HashiCorp Certified: Vault Operations Professional 2022
Create a working Vault server configuration given a scenario
Userpass Auth Method
The Userpass authentication method enables Vault clients to log in using a username and password stored in Vault itself. Since it doesn’t depend on an external identity provider, Userpass is perfect for quick labs, testing environments, and simple use cases where you need basic credential management without added complexity.
Warning
Userpass does not enforce password complexity, expiration, or rotation by default. For production workloads, consider integrating Vault with external identity providers or LDAP.
How It Works
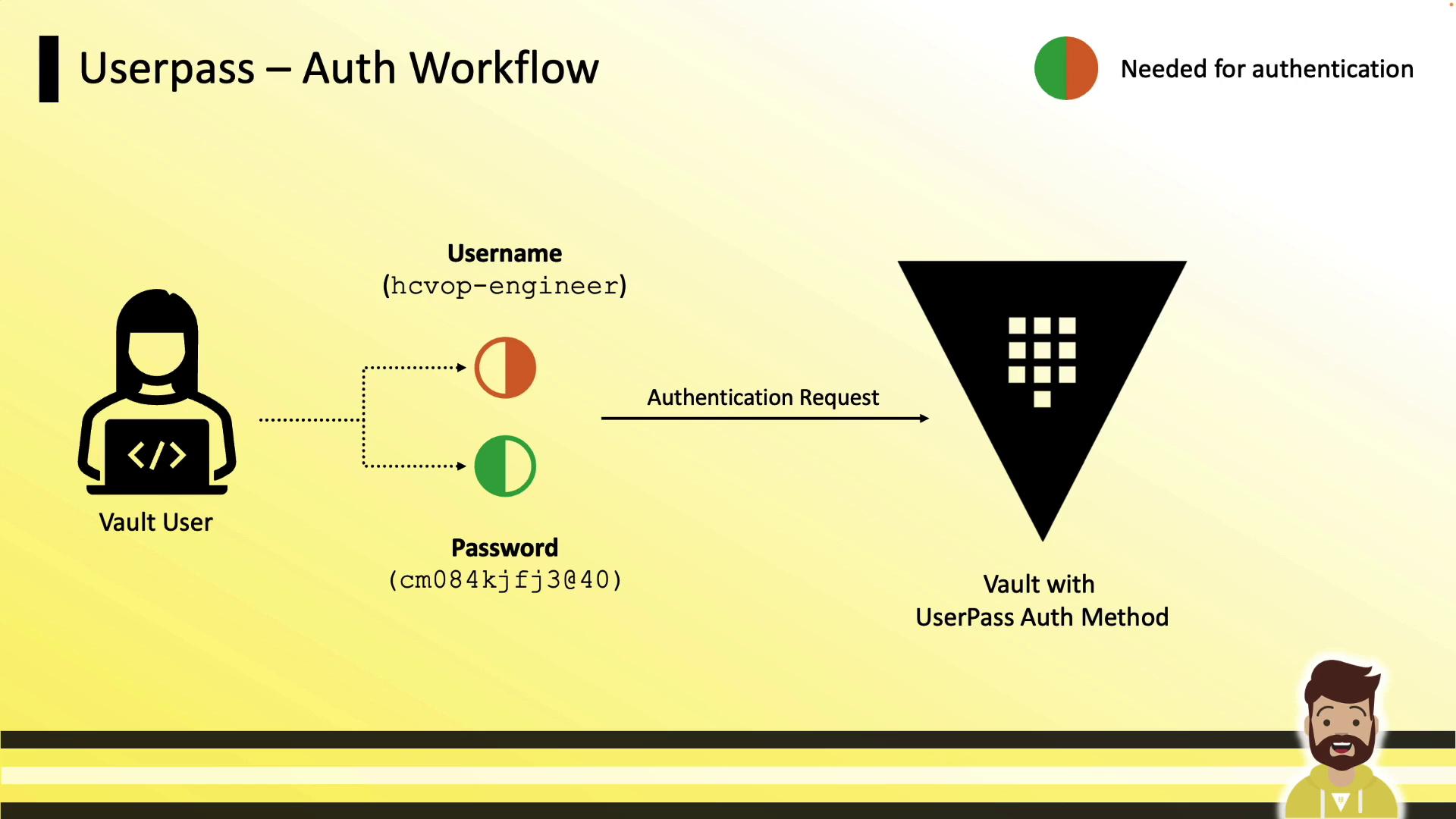
- User provides username (e.g.,
hcvop-engineer) and password. - Vault validates credentials and issues a token.
- The token is used to interact with Vault’s API and secrets engines.
Configuration Workflow
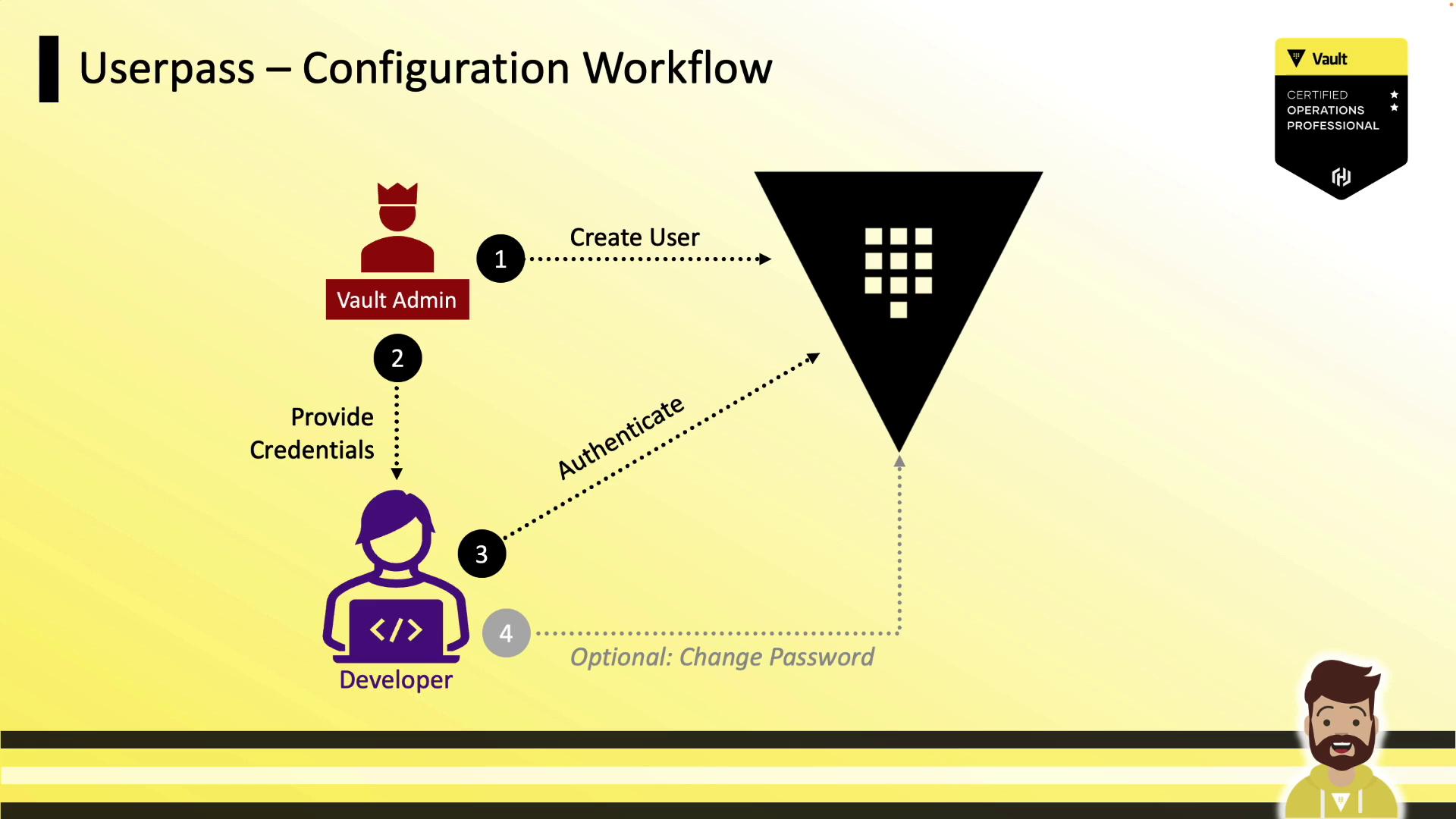
- Vault Admin enables the
userpassauth method. - Admin creates a user with policies and token settings.
- Admin hands off credentials to the Developer.
- Developer logs in and obtains a token.
- Developer may update their password if allowed by policy.
Enabling Userpass
# Enable at default path (userpass/)
vault auth enable userpass
# Or enable at custom path (e.g., vault-local/)
vault auth enable -path=vault-local userpass
Creating a User
Run vault write against the auth/userpass/users/<username> path:
vault write auth/userpass/users/hcvop-engineer \
password=cm084kjfj340 \
policies=engineering-policy \
token_ttl=15m \
token_max_ttl=8h
| Parameter | Description | Example |
|---|---|---|
| password | Initial user password | cm084kjfj340 |
| policies | Comma-separated Vault policies | engineering-policy |
| token_ttl | Time-to-live for issued tokens | 15m |
| token_max_ttl | Maximum time-to-live before renewal is disallowed | 8h |
Note
You can assign multiple policies (e.g., default,engineering-policy) or fine-tune token parameters per user.
Additional Token Configuration Options
| Option | Description | Example |
|---|---|---|
| token_type | Token type (default or batch) | token_type=batch |
| token_num_uses | Maximum number of uses for a token | token_num_uses=5 |
| token_bound_cidrs | CIDR list restricting token usage | token_bound_cidrs="10.1.16.0/16" |
| token_period | Duration for periodic tokens | token_period=1h |
Include these flags in the same vault write command when creating or updating a user.
Reading User Settings
Retrieve user configuration:
vault read auth/userpass/users/hcvop-engineer
Sample output:
Key Value
--- -----
policies [engineering-policy]
token_bound_cidrs []
token_explicit_max_ttl 0s
token_max_ttl 8h
token_ttl 15m
token_type default
Modifying User Configuration
To update a single attribute, re-run vault write with the changed flag:
vault write auth/userpass/users/hcvop-engineer token_type=batch
Only the specified setting (token_type) is updated; other attributes remain intact.
Authenticating with Userpass
vault login -method=userpass username=hcvop-engineer
# Prompts for password (hidden)
Successful authentication returns:
- Token
- Duration (TTL)
- Renewable flag
- Attached policies
Your CLI automatically caches the token for subsequent commands.
Password Rotation
Grant users the ability to update their own password by adding this to their policy:
path "auth/userpass/users/{{identity.entity.aliases.userpass.username}}/password" {
capabilities = ["update"]
}
Then users can run:
vault write auth/userpass/users/hcvop-engineer/password password=xmeij9dk20je
This enables self-service rotation without exposing credentials to admins.
Best Practices and Considerations
- Regularly revoke or delete user entries when access is no longer required.
- Implement an external password policy (complexity, expiry) via automation or scripts.
- For enterprise use, prefer OIDC, LDAP, or Kerberos auth methods to centralize identity management.
Links and References
Watch Video
Watch video content