HashiCorp Certified: Vault Operations Professional 2022
Employ the Vault Security Model
Secure Introduction of Vault Clients
In this guide, we explore methods to securely introduce Vault clients, ensuring that your applications obtain secrets without exposing initial credentials. We’ll cover the concept of Secret Zero, security goals, and multiple introduction patterns using trusted platforms and orchestrators.
Secret Zero
Secret Zero is the initial secret an application needs to authenticate and retrieve further secrets. Examples from everyday tools include 1Password or LastPass, where a master password or biometric unlock grants access to stored credentials. In HashiCorp Vault, Secret Zero can be an auth method’s credentials or a Vault token.
Because Secret Zero unlocks access to dynamic secrets—database passwords, API keys, TLS certificates—it must be introduced at the last possible moment and never embedded in code or repositories.

Secure Introduction Goals
Use the following best practices to minimize risk when introducing Vault clients:
| Goal | Benefit |
|---|---|
| Unique credentials per instance | Granular revocation and auditing |
| Limit exposure of compromised credentials | Reduces blast radius with short-lived credentials |
| No hard-coded credentials | Prevents accidental leaks in repositories |
| Reduce TTLs and use dynamic credentials | Ensures temporary access and automatic expiration |
| Runtime distribution only | Keeps secrets out of code and build artifacts |
| Trusted platform identity verification | Leverages cloud or Kubernetes identities for auth |
| Trusted orchestrator for secret injection | Automates secure provisioning in CI/CD and infrastructure |
1. Unique Credentials per Instance
Assign each application instance its own credentials to enable individual revocation and precise auditing.
2. Limit Exposure of Compromised Credentials
Use short-lived credentials; if one is compromised, you can revoke its lease or token without impacting others.
3. No Hard-Coded Credentials
Authenticate at runtime instead of embedding secrets in code.
Warning
Never commit static credentials or SecretID values into version control.
4. Reduce TTLs and Use Dynamic Credentials
Favor dynamic credentials (e.g., database users, cloud provider tokens) with minimal TTLs to limit exposure.
5. Runtime Distribution Only
Inject secrets into applications only during startup or execution, never bake them into container images or binaries.
6. Trusted Platform Identity Verification
Leverage platform-specific identity sources for authentication:
- AWS IAM
- Azure MSI
- GCP metadata server
- Kubernetes ServiceAccount tokens
7. Trusted Orchestrator Injection
Use CI/CD tools or infrastructure-as-code platforms authenticated to Vault to generate and inject per-application secrets.
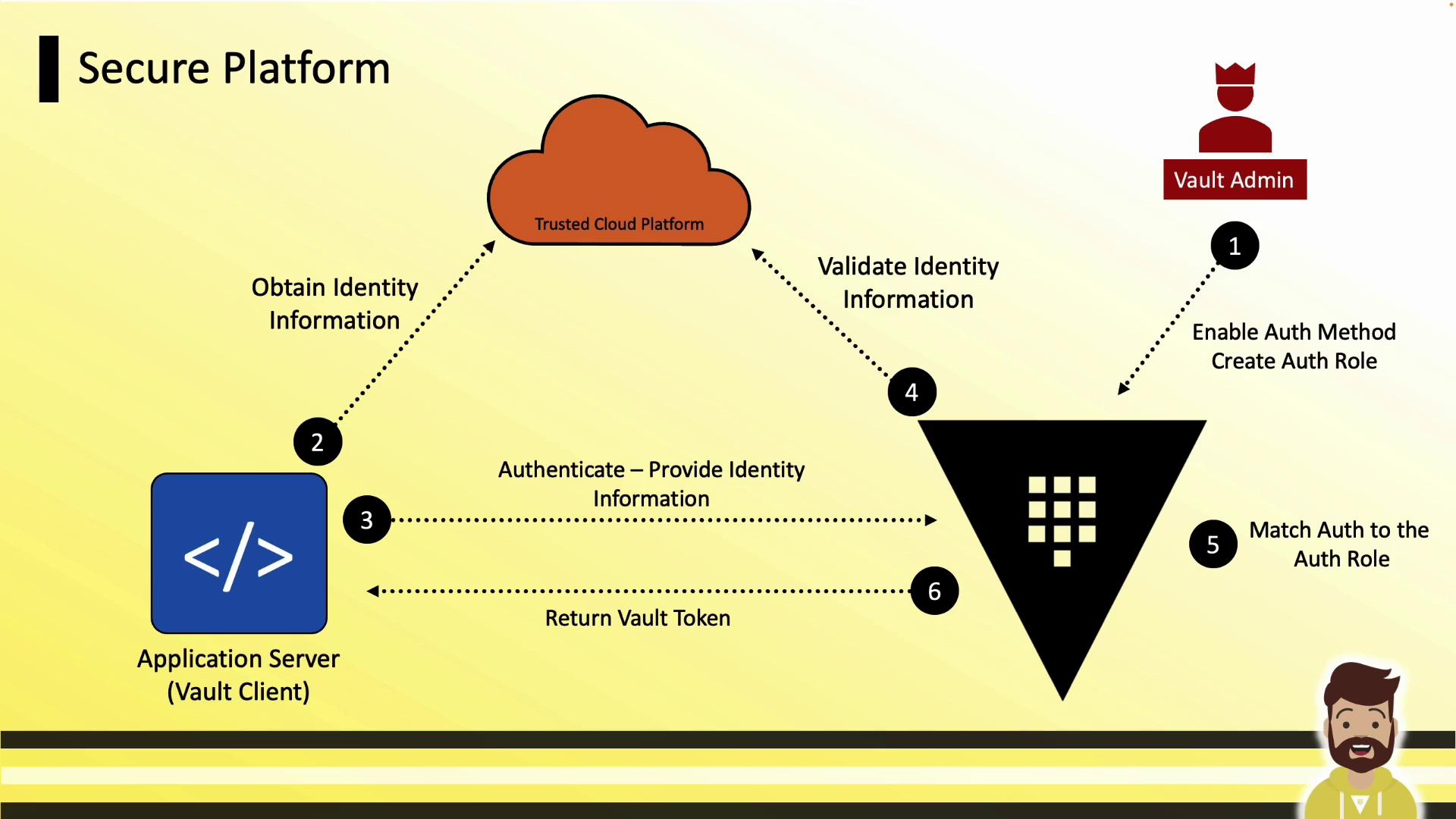
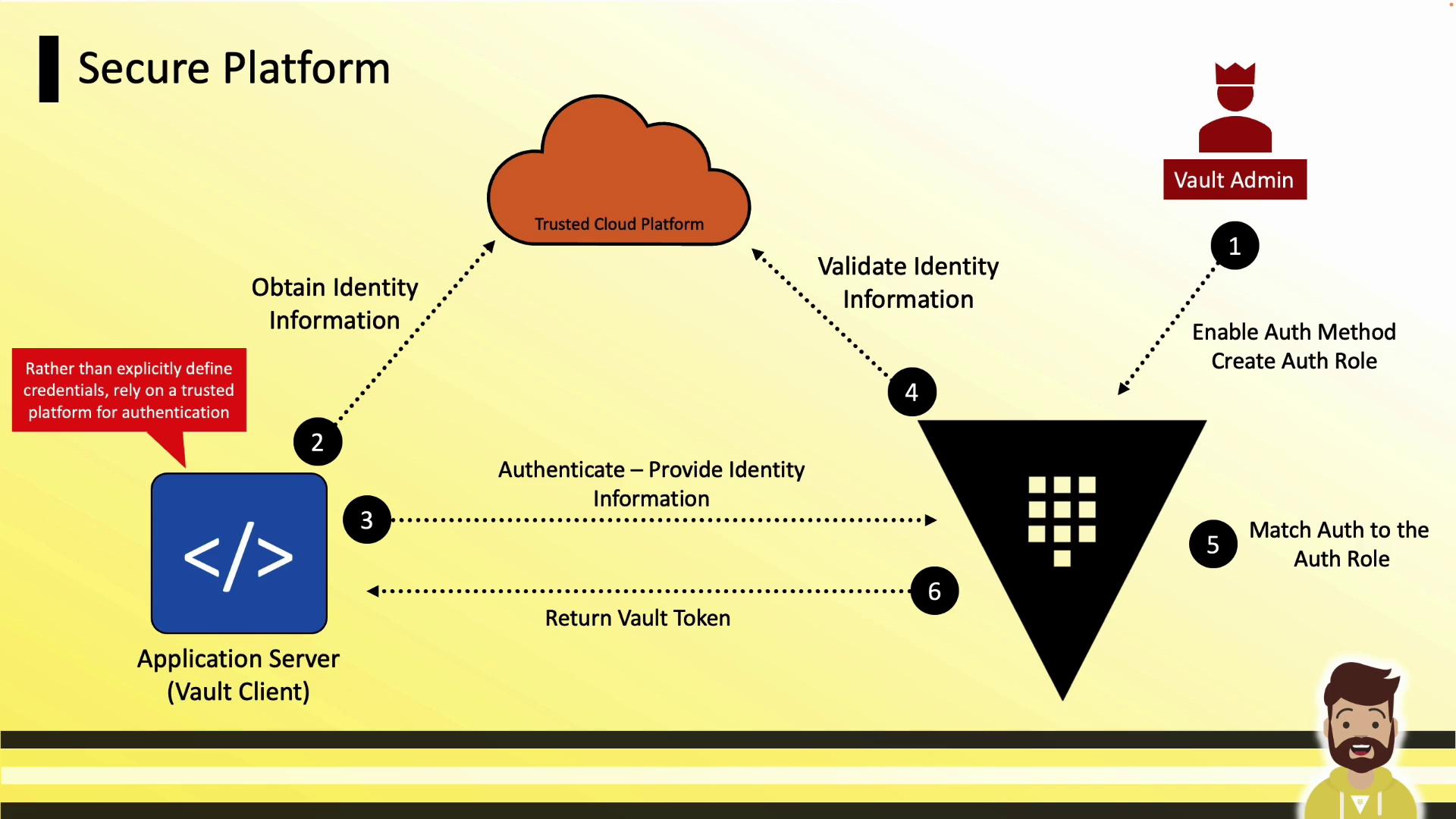
Secure Platform Authentication
Applications running on trusted platforms (AWS, Azure, GCP, Kubernetes) can authenticate to Vault using metadata services.
Authentication Flow
- Vault admin enables a platform auth method and defines a role.
- The application retrieves its instance identity (e.g., metadata service).
- It presents this identity data to Vault.
- Vault validates the data with the cloud provider.
- On success, Vault issues a short-lived token.
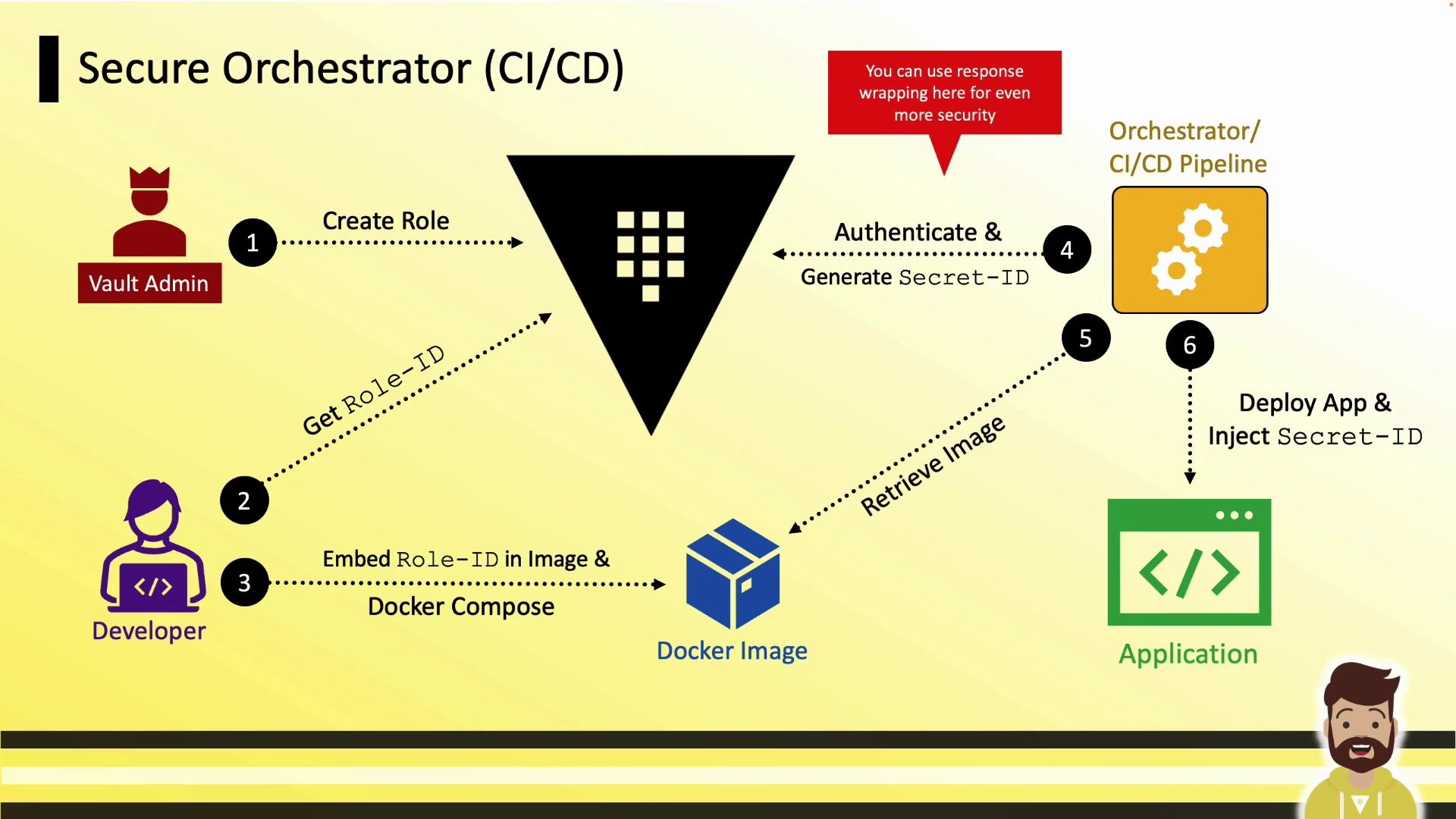
Secure Orchestrator: CI/CD Pipeline
A CI/CD pipeline can act as a trusted orchestrator to generate and inject secrets at deployment time.
Pipeline Steps
- Vault admin creates an AppRole for the application.
- Developer retrieves the RoleID and bakes it into the application image.
- During deployment, the pipeline authenticates to Vault and requests a SecretID.
- The pipeline deploys the application and injects the SecretID at runtime.
- The application combines RoleID and SecretID to authenticate and retrieve secrets.
Note
For stronger protection, enable response wrapping so that only the intended application can unwrap the SecretID.
Secure Orchestrator: Terraform
Use Terraform to provision infrastructure and request Vault credentials without storing secrets in code.
Provisioning Flow
- Terraform provisions new workloads.
- It requests an AppRole SecretID from Vault.
- Terraform injects the SecretID into the workload at deployment time.
- The application authenticates using its RoleID and the injected SecretID.
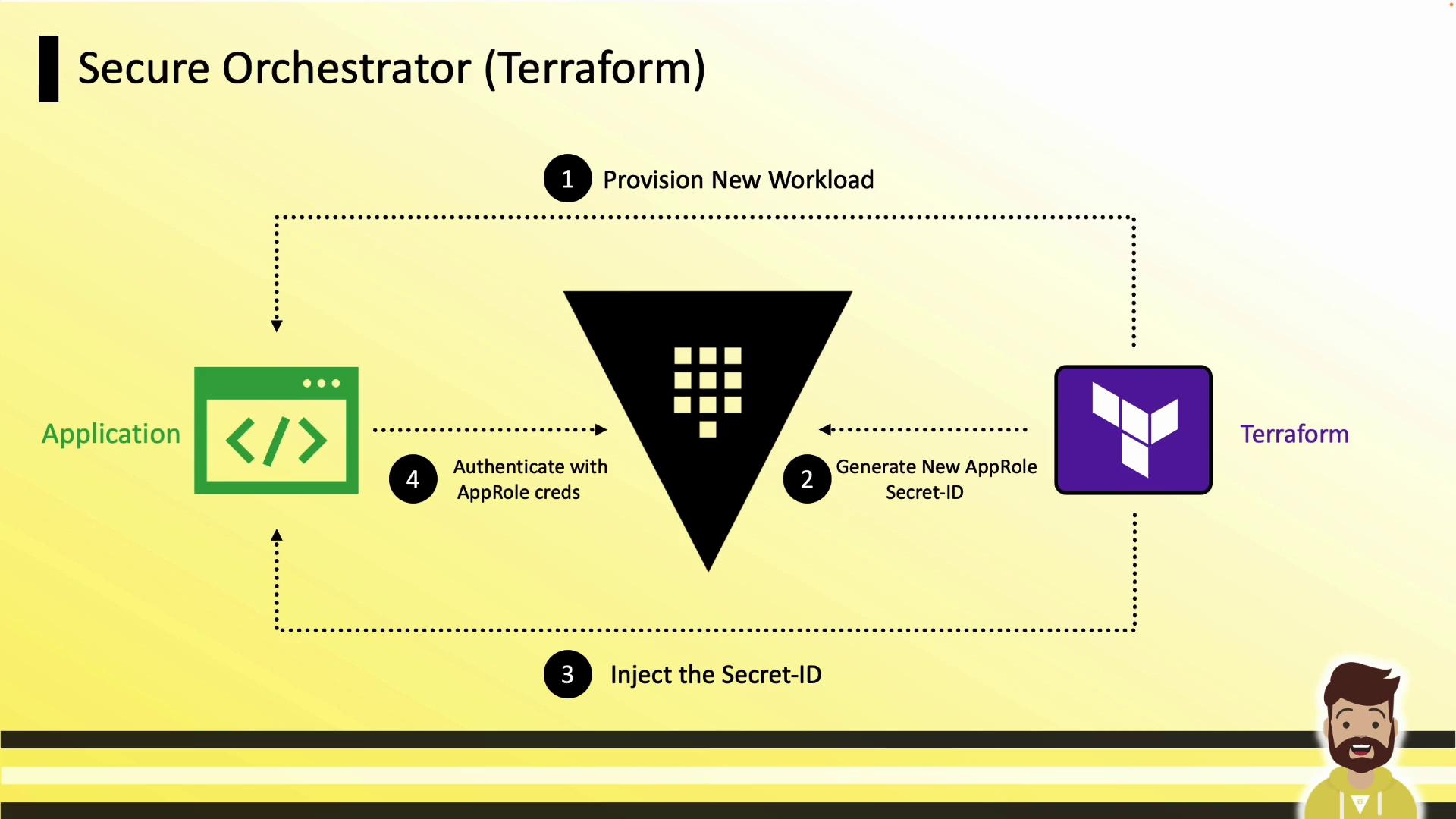
The SecretID is never stored in your Terraform code repository—only the provisioning logic is.
Vault Agent Auto-Auth
Vault Agent can manage authentication and token renewal for your application, reducing operational overhead.
Auto-Auth Steps
- Install Vault Agent on the application server.
- Configure the Auto-Auth stanza with your chosen auth method.
- Vault Agent authenticates to Vault and obtains a client token.
- The agent writes the client token to a local file.
- The application reads the token file for API requests to Vault.
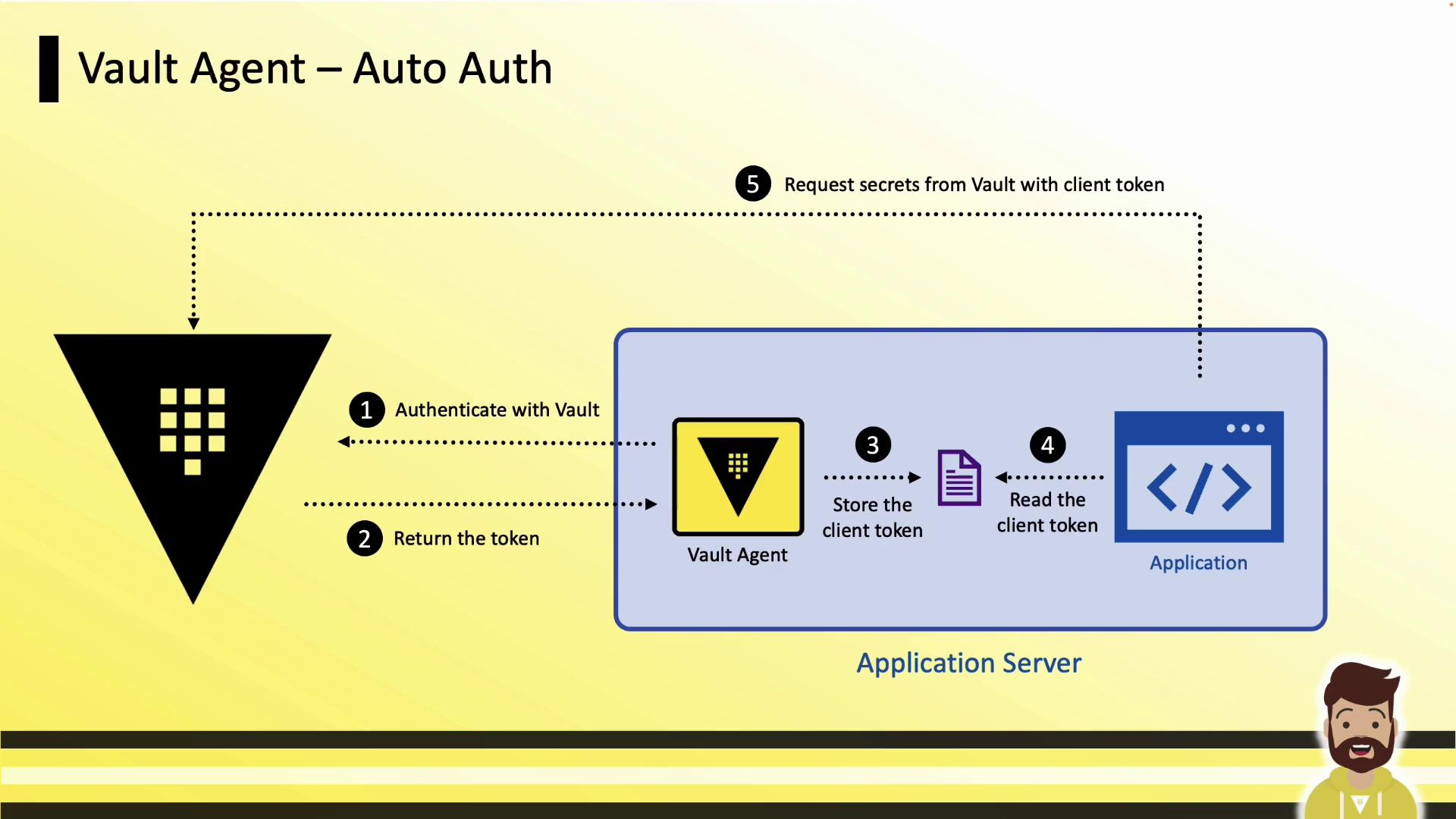
Vault Agent ensures applications never handle raw credentials directly and transparently renews tokens as needed.
Links and References
- AWS IAM documentation
- Azure Managed Identities
- GCP Metadata Server
- Kubernetes ServiceAccount Tokens
- Jenkins
- Azure DevOps
- Terraform
- HashiCorp Vault Documentation
Watch Video
Watch video content