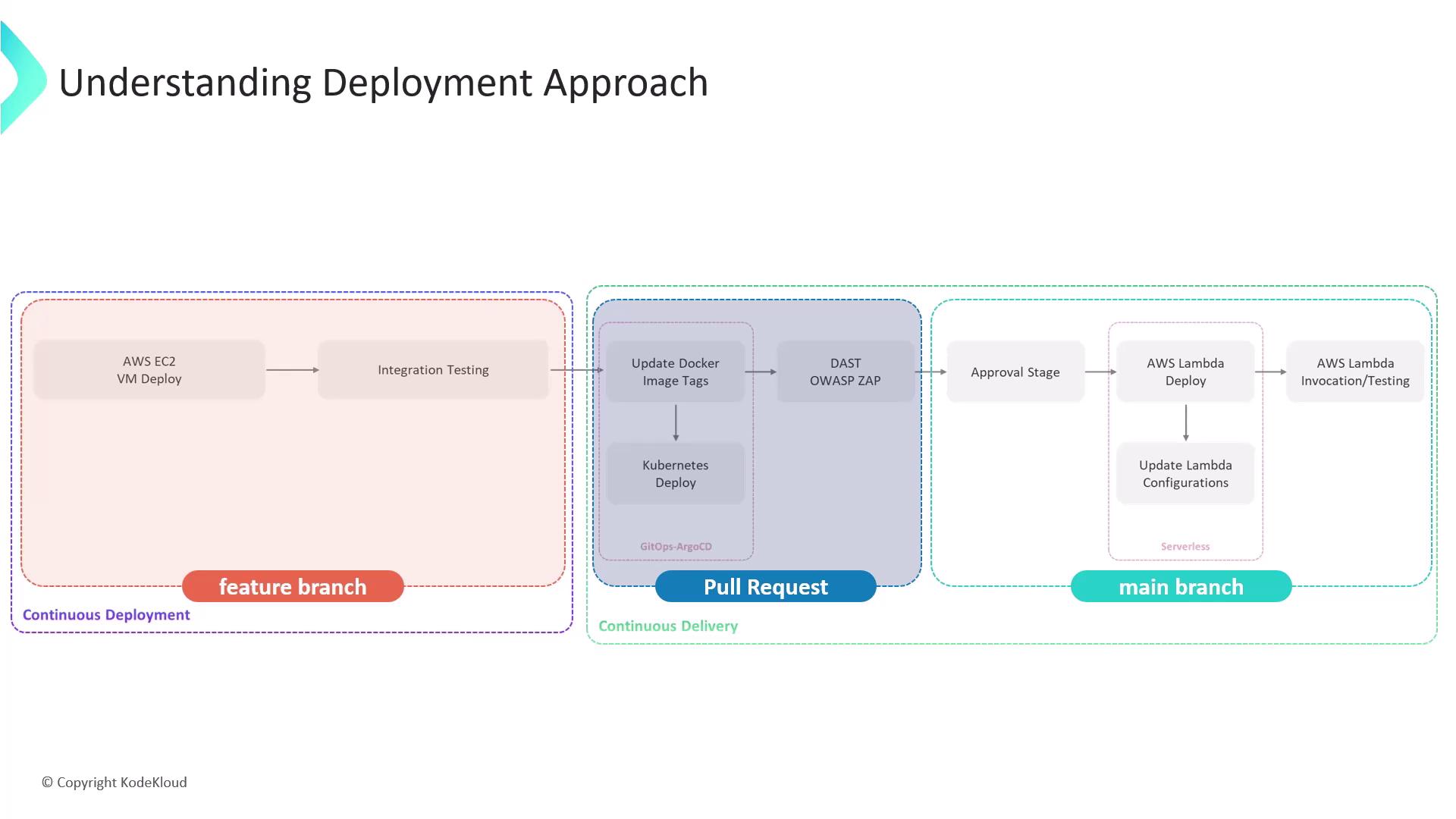
- Deployed an AWS EC2 VM
- Conducted integration testing
- Created a pull request
- Deployed the application to Kubernetes using GitOps with Argo CD
- Executed OWASP ZAP security tests
- The
whencondition ensures this stage only runs on the main branch. - A one-day
timeoutprovides ample time for the admin to approve. - The
inputstep presents a confirmation message with a custom OK button. - The
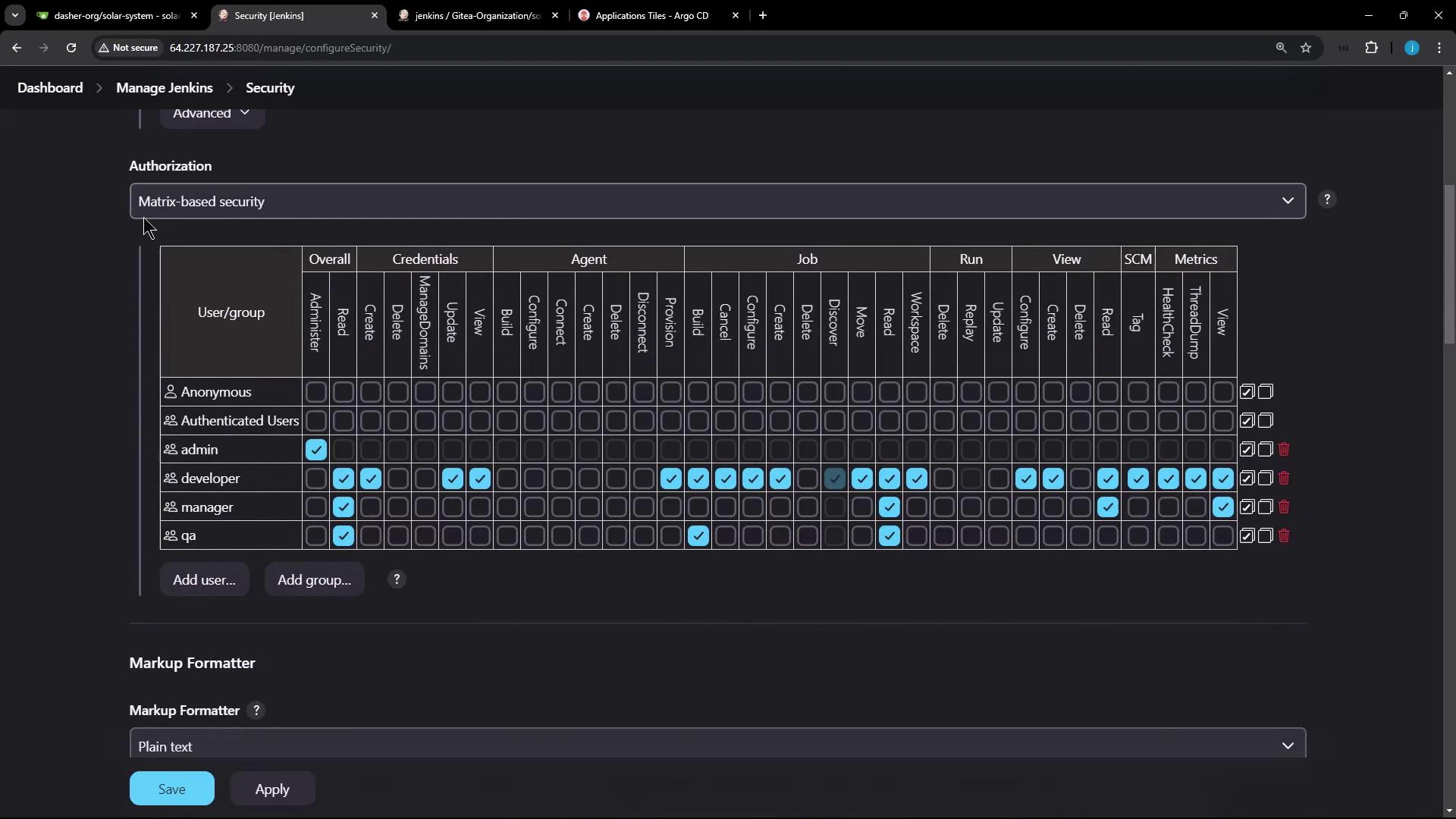
submitterparameter restricts approval to those belonging to the admin group.
submitter field, as shown in the snippet below generated by Jenkins’ Declarative Directive Generator:
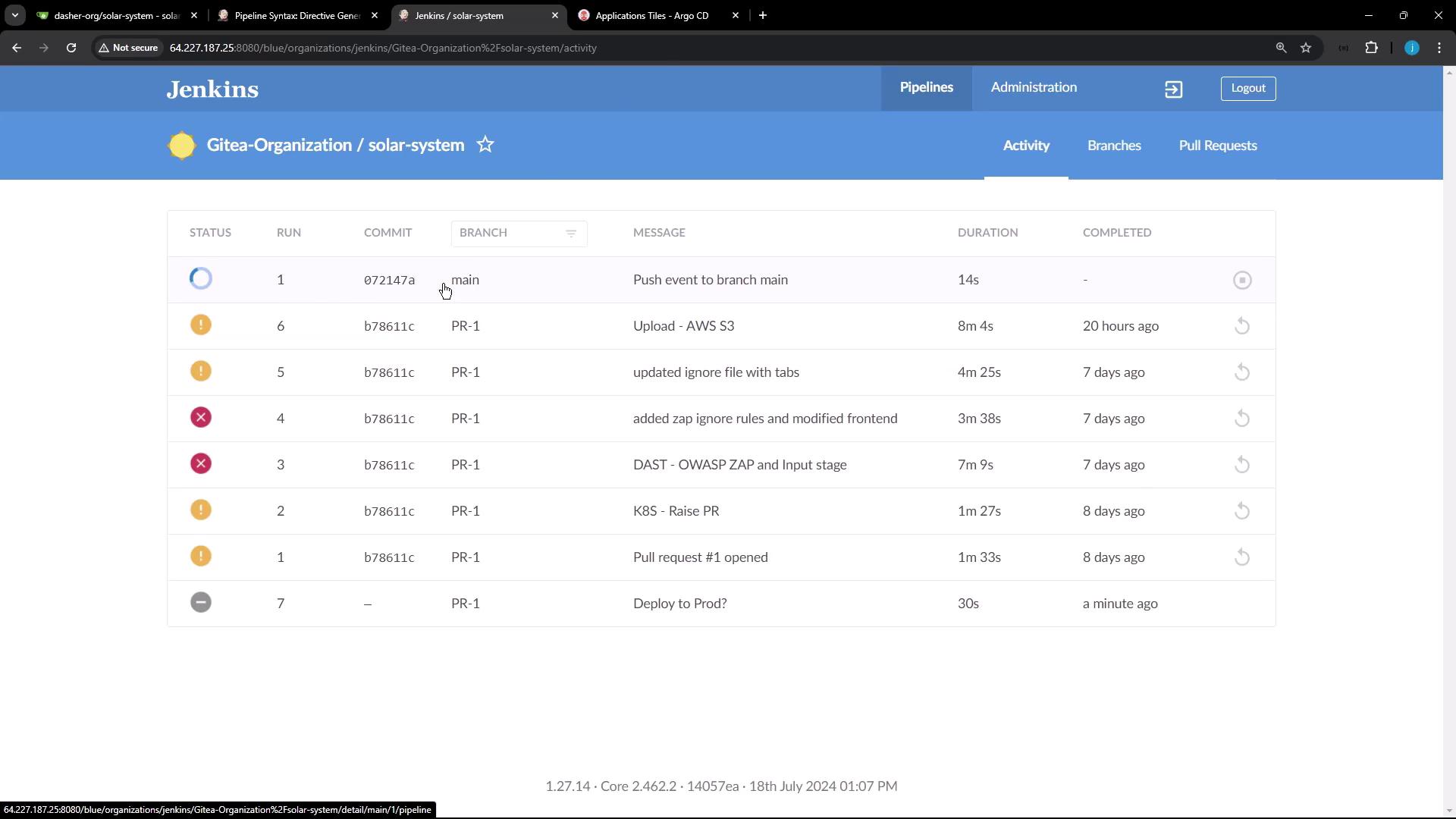
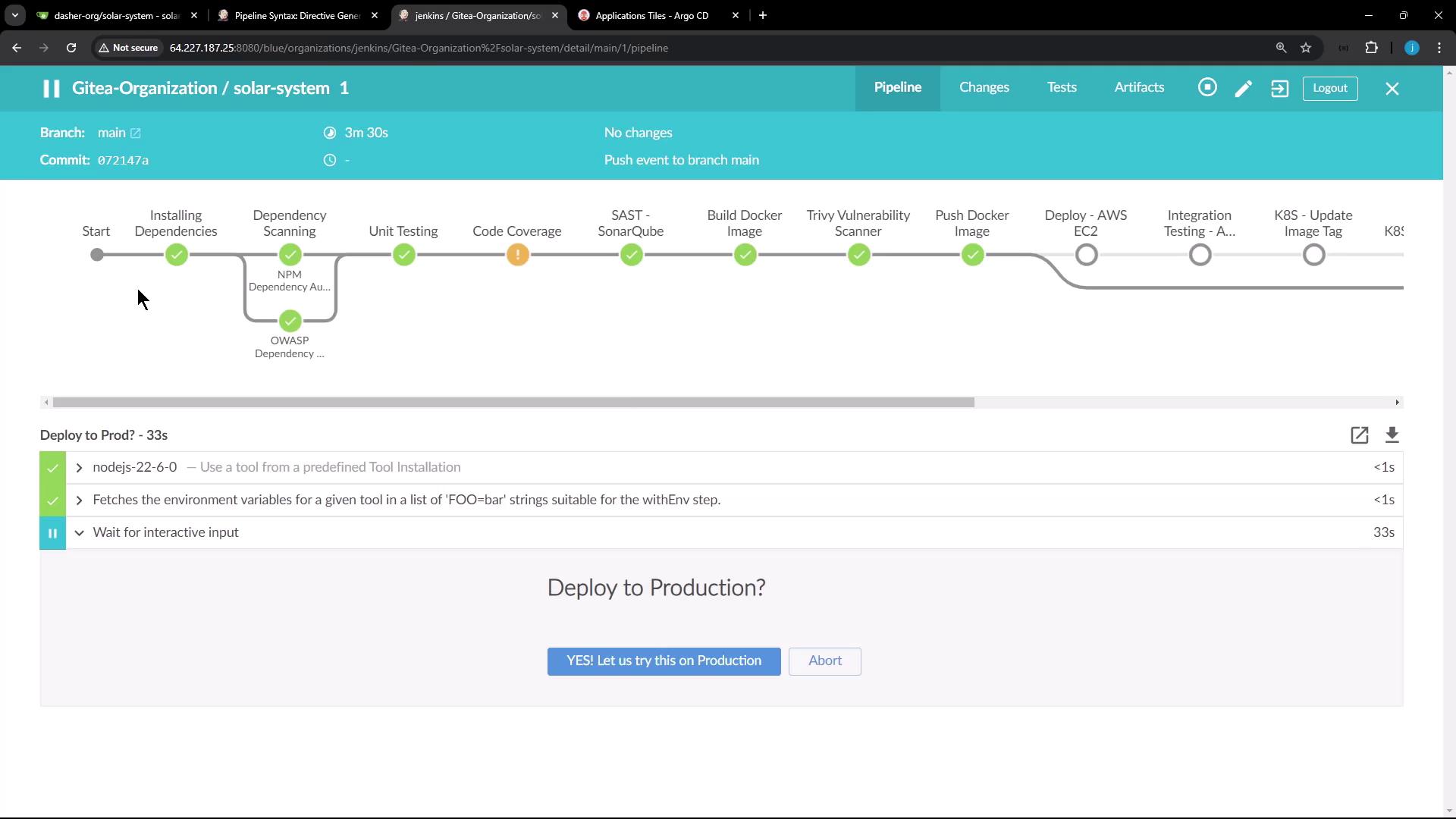
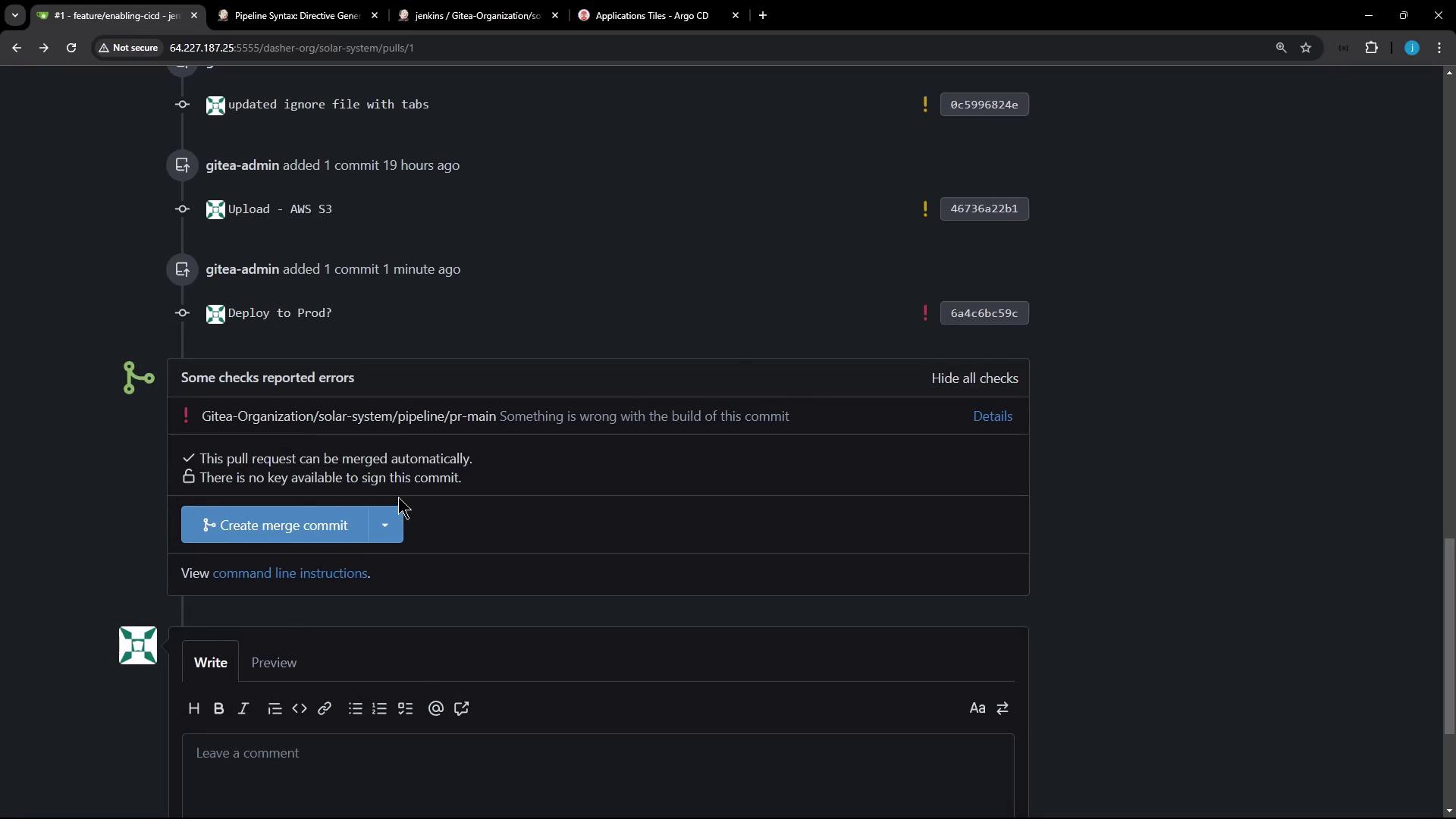
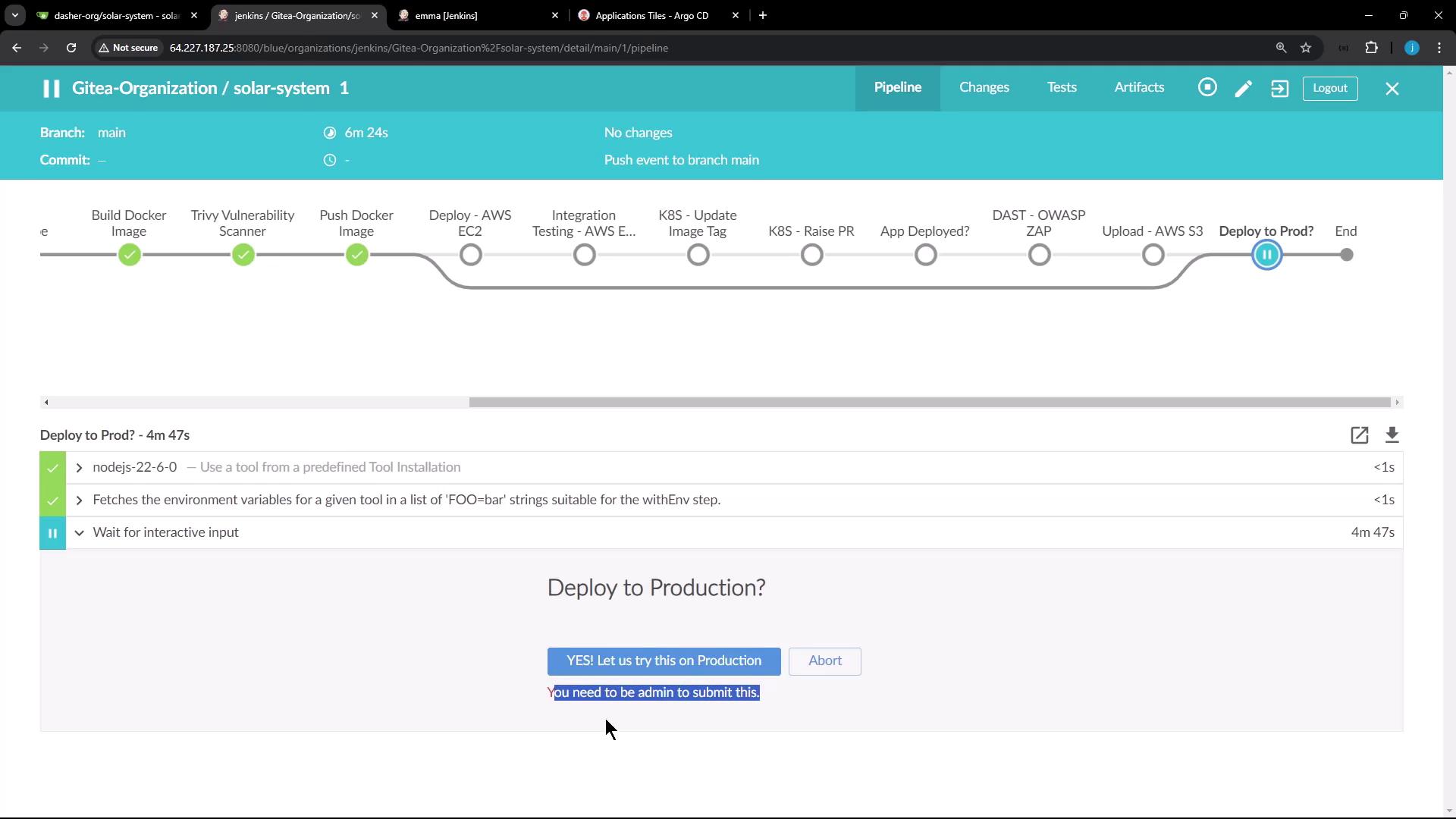
- When logged in as an admin, the deploy-to-production stage accepts the input and the build proceeds.
- If a non-admin user (e.g., EMA from the developer group) attempts to approve the stage, Jenkins denies the action. Developer group permissions are set to overall read-only based on the matrix-based security configuration.