Why Early Detection Matters
It might seem that once an attacker breaches your perimeter, the damage is done. However, just as banks now send instant alerts for credit card transactions to limit fraud, rapid detection in Kubernetes prevents lateral movement and stops attackers before they can escalate privileges or exfiltrate data.Real-World Analogy: Credit Card Alerts
Imagine your debit card is stolen. In the past, you might not notice fraudulent withdrawals until reviewing your statement days later. Today, banks send instant notifications, allow you to revert unauthorized transactions, and let you set spending limits:- Instant alerts tell you when and where the breach happened.
- Automated workflows can isolate or replace affected pods.
- Policy limits (e.g., resource quotas, network policies) contain the impact.
Detecting Breaches in Kubernetes
Once a container is breached, rapid detection prevents further spread: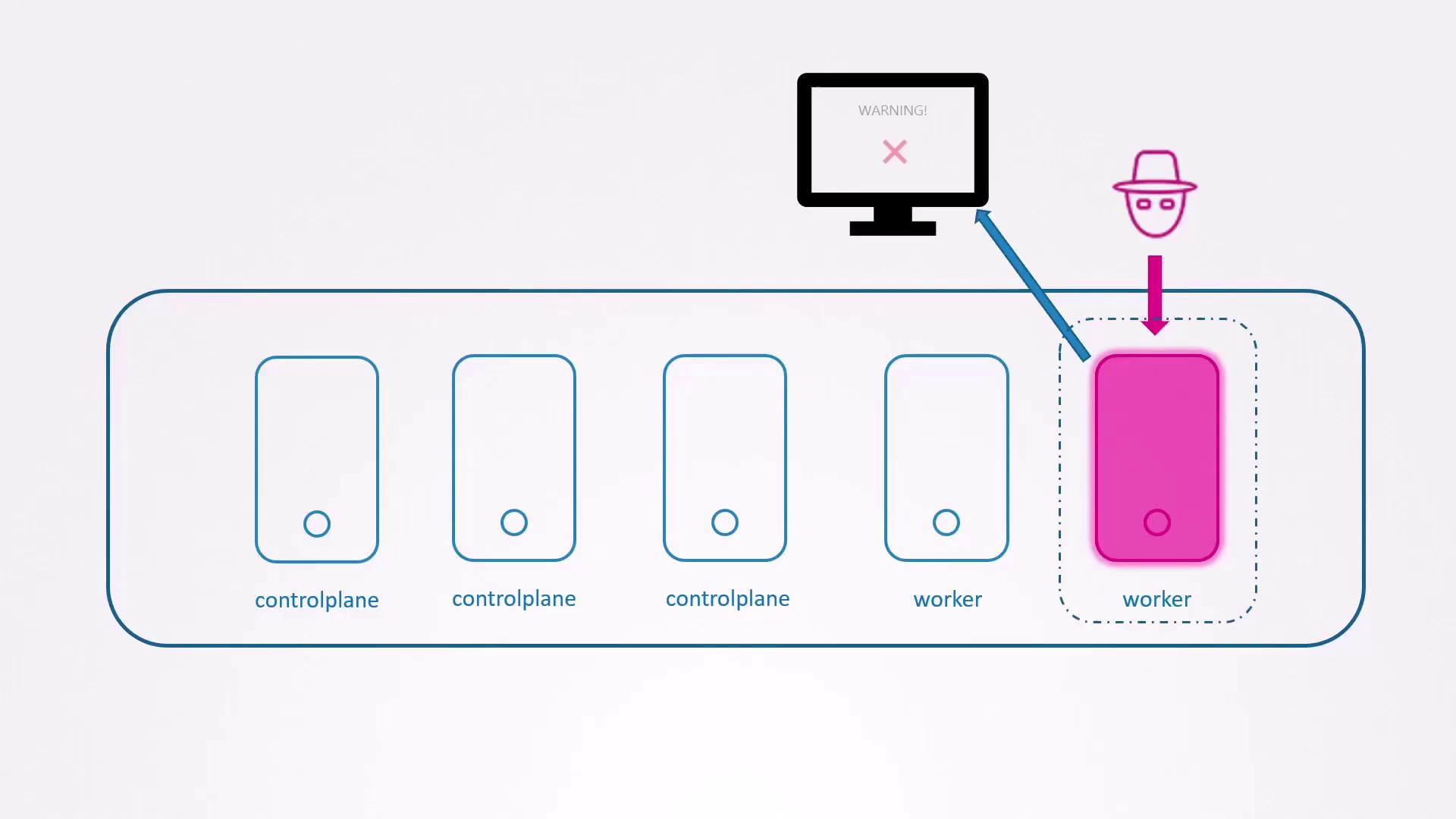
Introducing Falco
Falco is an open-source runtime security project by Sysdig. It hooks into the Linux kernel to capture syscalls from containers and applies rules to detect: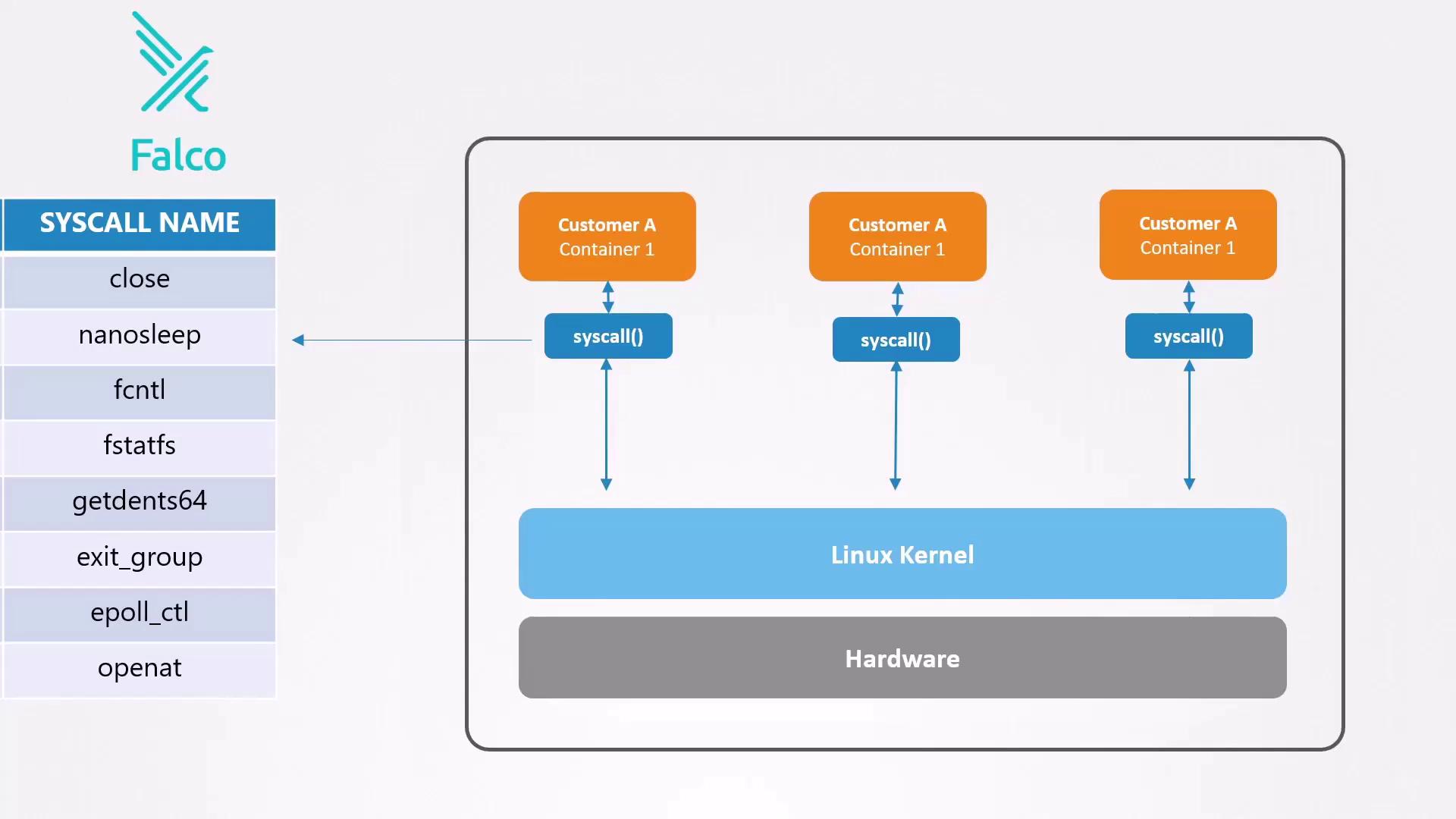
- Unexpected shell access inside a container
- Reading sensitive files like
/etc/shadow - Deleting or truncating logs to cover tracks
Falco requires privileged permissions to monitor syscalls. Make sure to deploy it with appropriate security contexts and RBAC settings.
Common Indicators of Compromise
| Suspicious Activity | Description |
|---|---|
| Unexpected shell in container | kubectl exec -ti <pod> -- bash opens an interactive shell |
| Accessing password hashes | cat /etc/shadow |
| Deleting or truncating audit logs | > /opt/logs/audit.log |
Suppressing Falco alerts for critical rules can blind you to real threats. Tune rules carefully rather than disabling them.