Linux Professional Institute LPIC-1 Exam 101
System Architecture
Boot the System
Understanding the Linux boot process is essential for troubleshooting and optimizing system startup. This guide walks through each stage—from firmware to the init system—detailing BIOS/UEFI, the GRUB bootloader, kernel initialization with initramfs, and the init process.
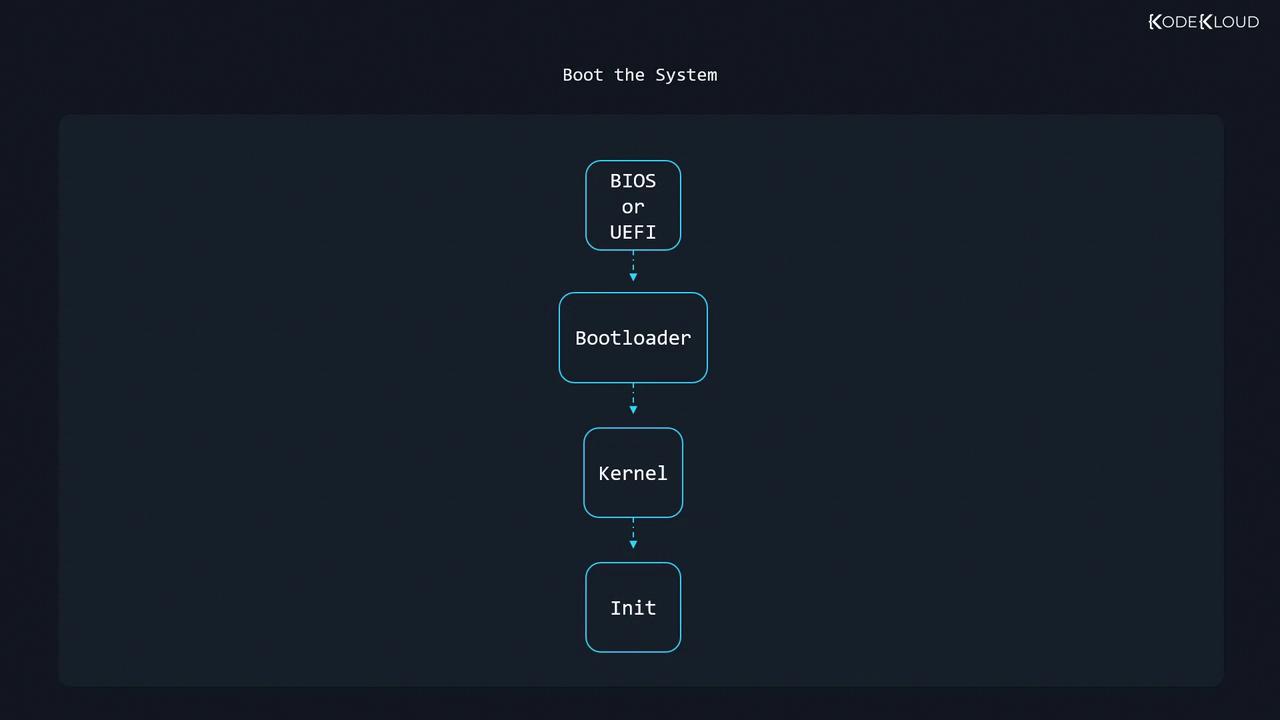
1. BIOS and the Master Boot Record (MBR)
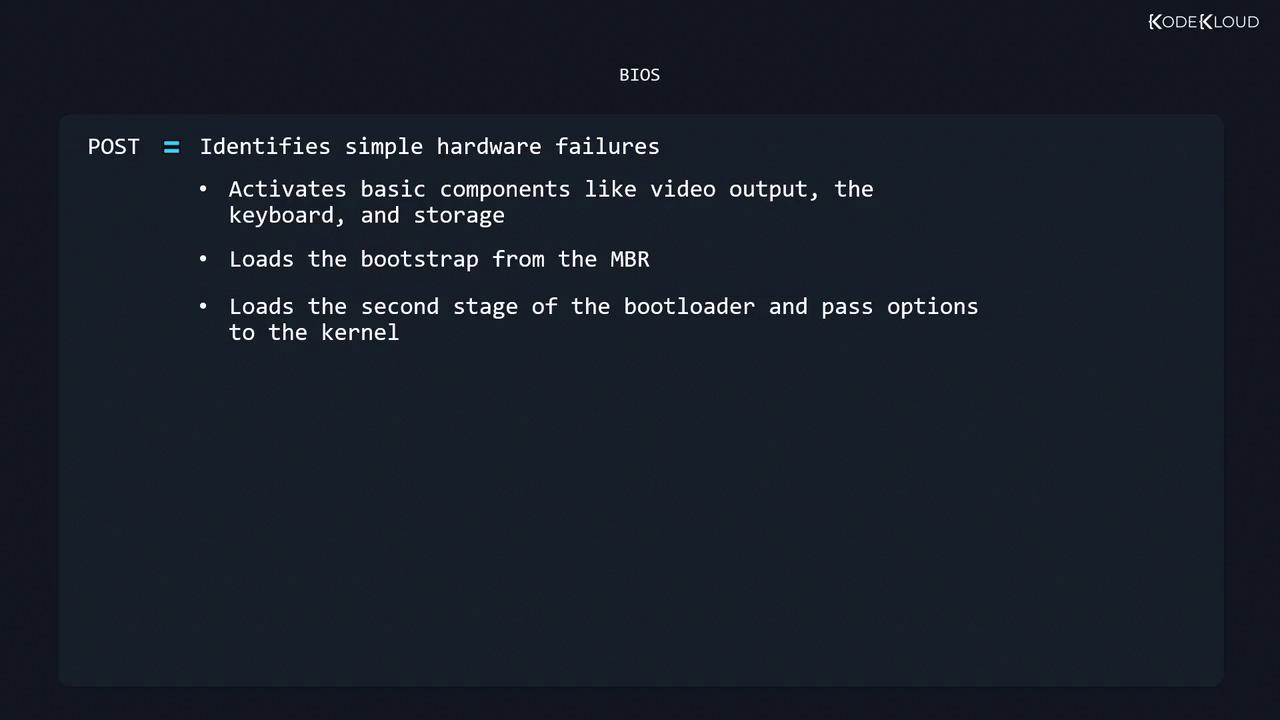
The Basic Input/Output System (BIOS) resides on a motherboard chip and executes immediately after power-on. It performs:
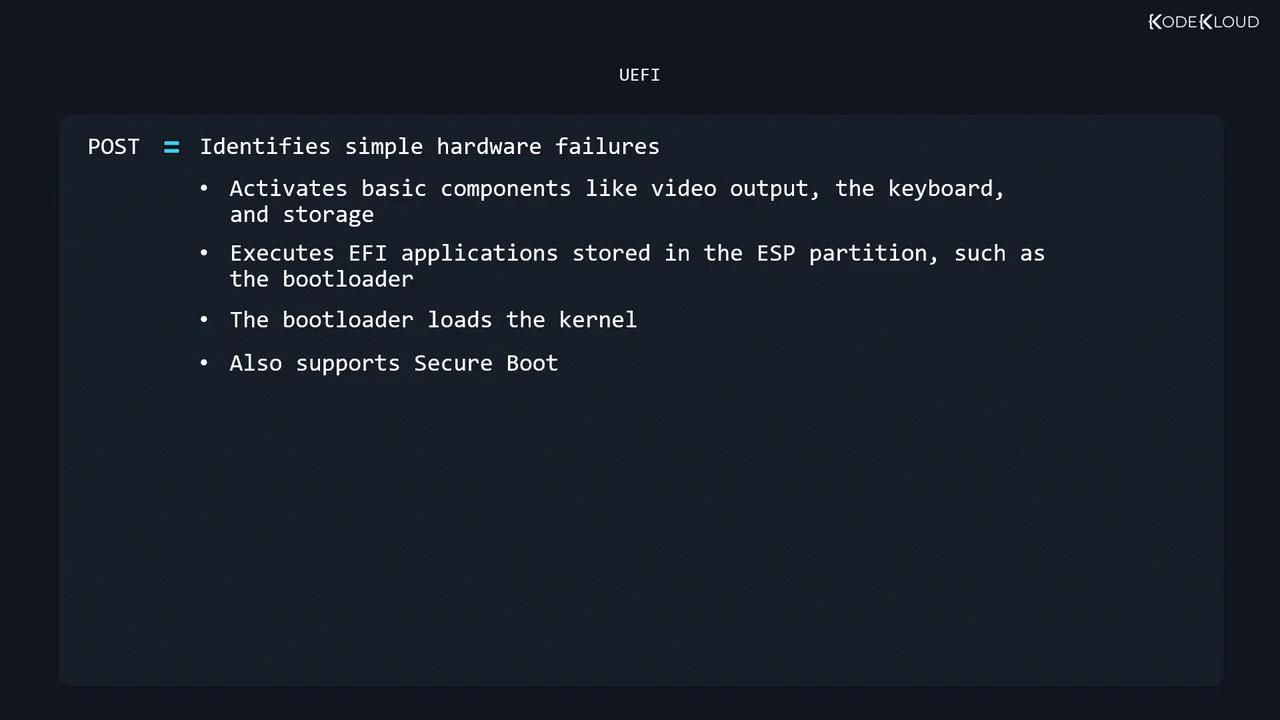
- Power-On Self-Test (POST): Verifies basic hardware (CPU, memory, etc.).
- Device Initialization: Activates video, keyboard, and storage controllers.
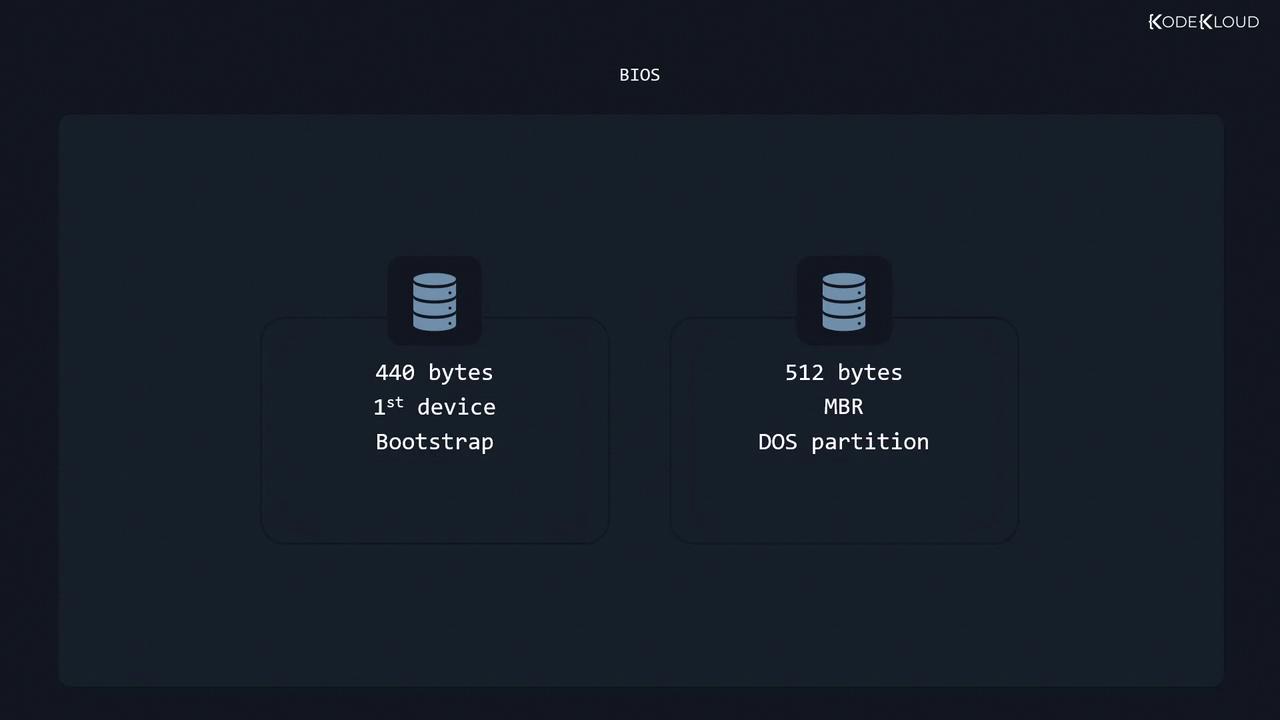
- MBR Read: Loads the first 512 bytes—the Master Boot Record—from the configured disk.
- Bootstrap Loader: Executes the first-stage bootloader (440 bytes), reads the partition table, then transfers control to the second stage to load the bootloader and kernel.
Note
The MBR format supports disks up to 2 TiB and allows a maximum of four primary partitions. Consider GPT for larger disks.
2. UEFI (Unified Extensible Firmware Interface)
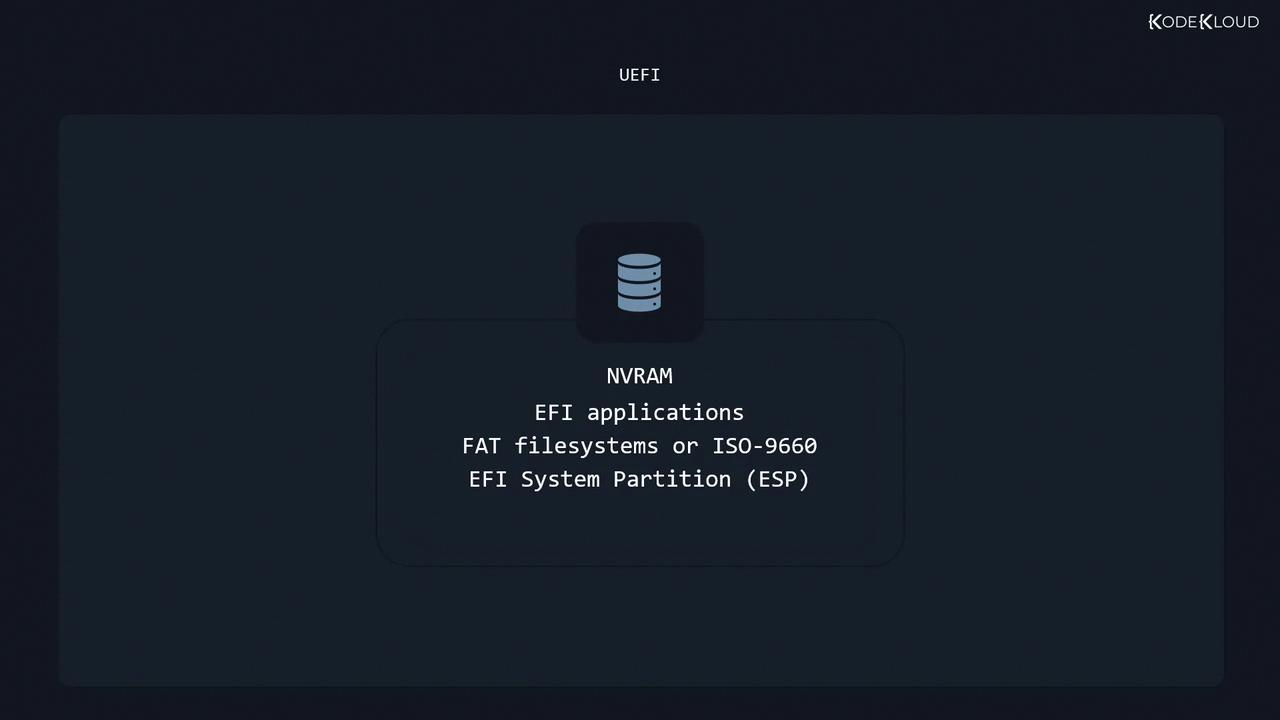
UEFI modernizes BIOS by using non-volatile memory (NVRAM) to locate EFI applications on an EFI System Partition (ESP). Key aspects:
- UEFI POST: Hardware diagnostics similar to BIOS.
- Component Activation: Initializes video, input, and storage.
- EFI Application: Loads the bootloader or OS selector from
/EFIon the ESP (FAT12/16/32 or ISO 9660). - Kernel Loading: Transfers control to the bootloader, which loads the Linux kernel.
UEFI’s Secure Boot verifies digital signatures, preventing unauthorized kernels and bootloaders.
Warning
Disabling Secure Boot is often required when installing unsigned or custom kernels. Ensure you understand the security implications.
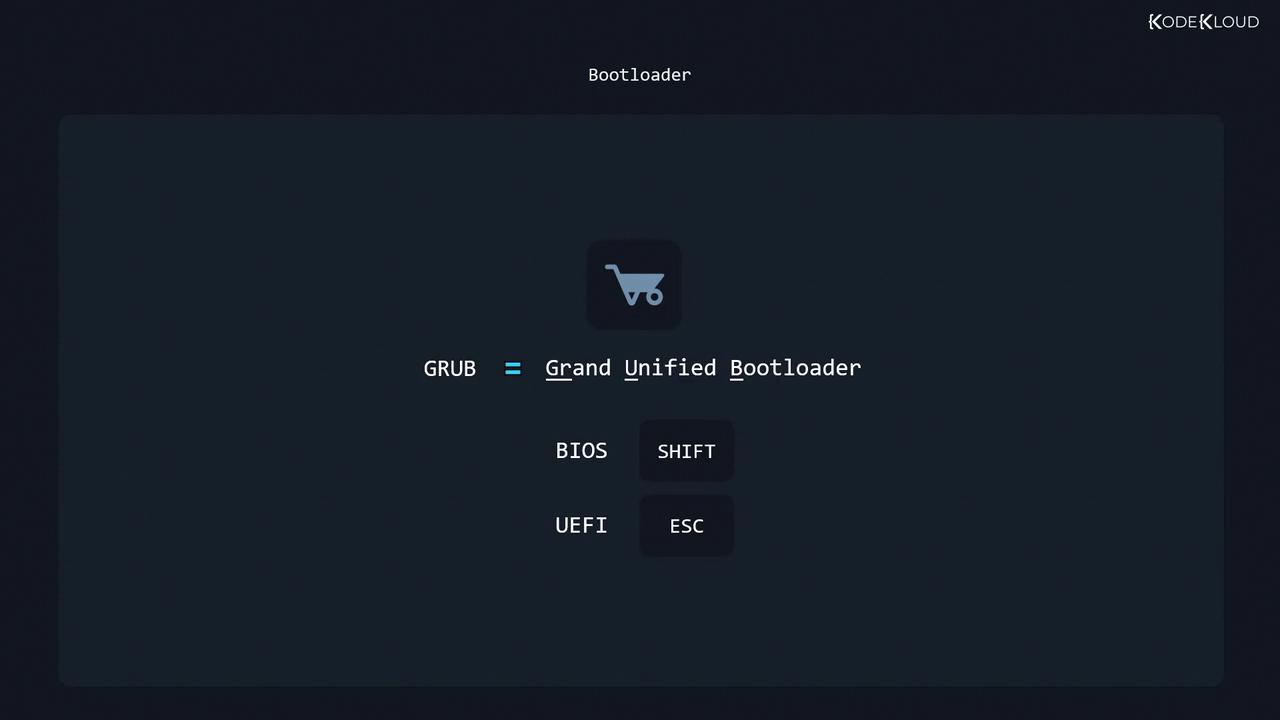
3. GRUB: The Grand Unified Bootloader
GRUB is the most common x86 bootloader for BIOS and UEFI systems. Press Shift (BIOS) or Esc (UEFI) to access the menu if it doesn’t appear.
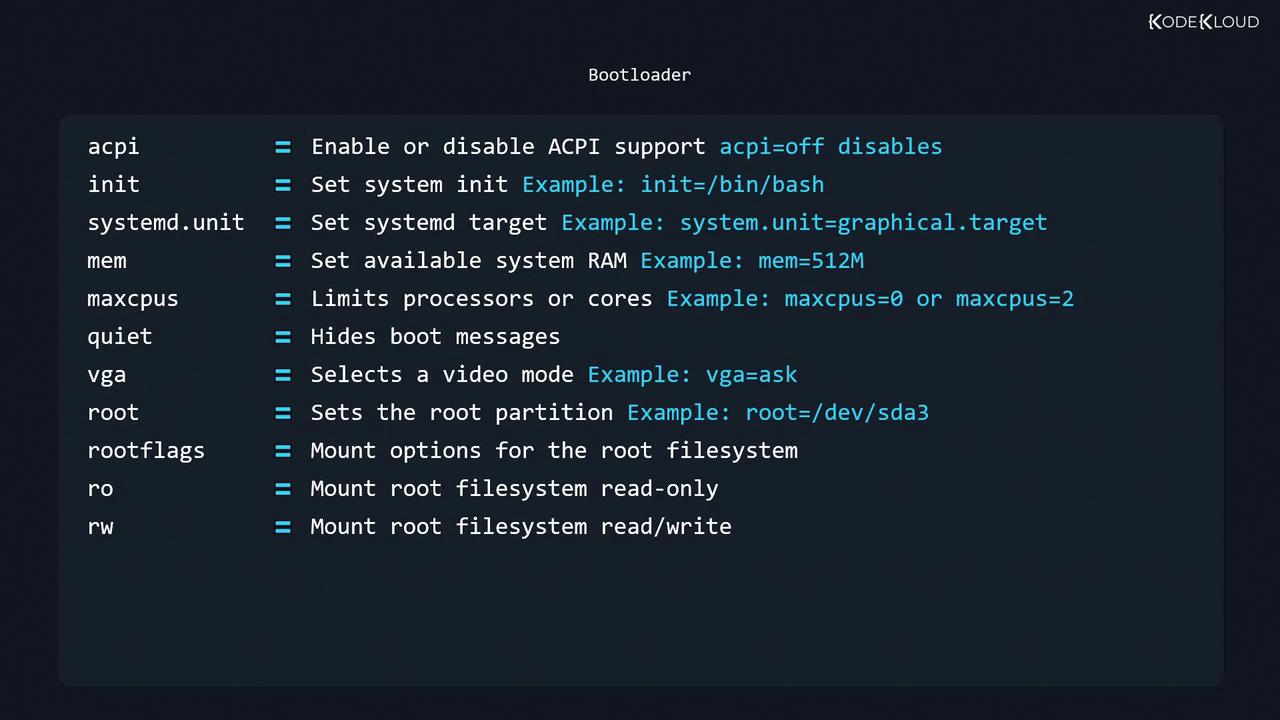
From GRUB, you can select kernels and pass parameters in option=value format:
| Parameter | Description |
|---|---|
acpi=off | Disable ACPI support |
init=/bin/bash | Boot directly to a Bash shell |
systemd.unit=multi-user.target | Set the systemd target (e.g., multi-user, graphical) |
mem=512M | Limit maximum RAM available |
maxcpus=2 | Restrict CPU cores |
quiet | Suppress most boot messages |
vga=ask | Prompt for video mode |
root=/dev/sda3 | Specify root filesystem partition |
rootflags=ro or rootflags=rw | Mount root filesystem read-only or read-write |
We’ll cover permanent GRUB configuration in a later lesson.
4. Kernel Initialization and initramfs
After GRUB loads the kernel:
- Kernel Startup: Initializes CPU, memory management, and drivers.
- initramfs Mount: Unpacks the initial RAM filesystem, which includes essential modules and tools.
- Real Root Mount: Switches to the actual root partition defined in
/etc/fstab. - Exec Init: The kernel runs:
exec /sbin/init
This launches the init system and frees the initramfs from memory.

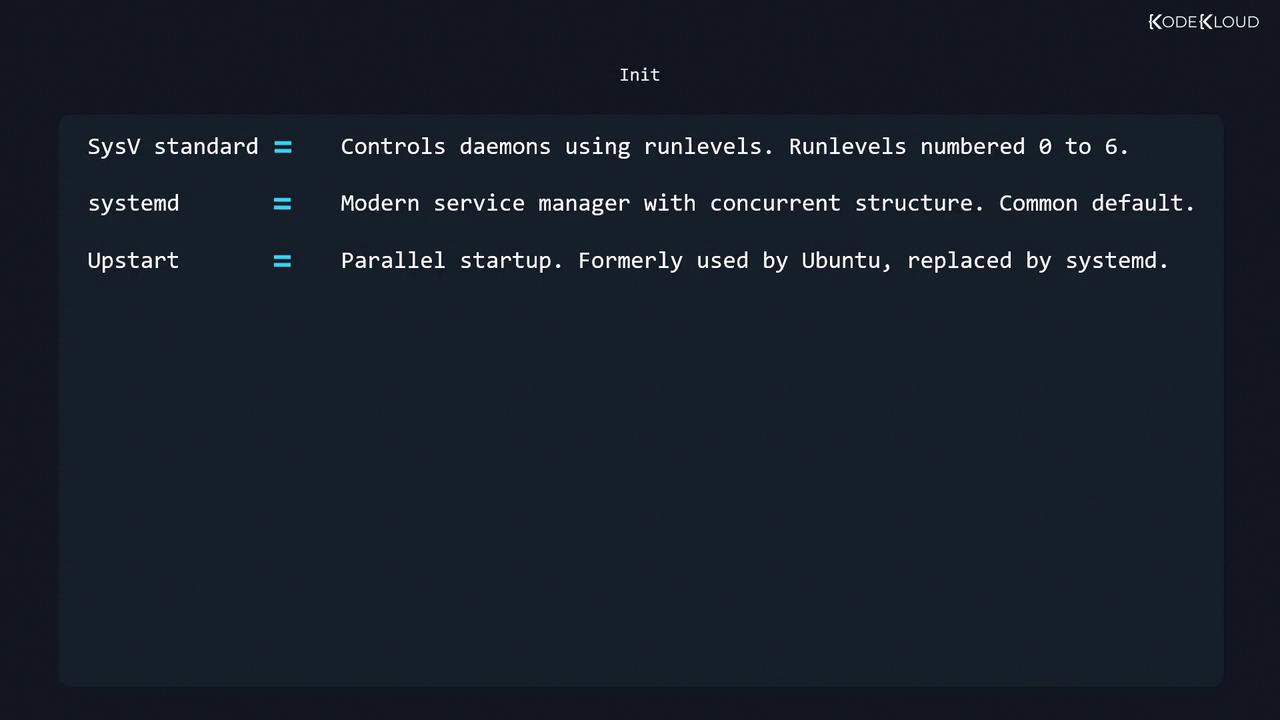
5. Init Systems: SysV, systemd, and Upstart
Linux distributions may use different init managers:
| Init System | Type | Key Features |
|---|---|---|
| SysV init | Runlevel-based | Sequential startup with scripts, runlevels 0–6 |
| systemd | Service manager | Parallel startup, socket/D-Bus activation, cgroups, dependency-based units |
| Upstart | Event-driven | Responds to system events for parallel service startup (legacy Ubuntu releases) |
Viewing and Analyzing Boot Messages
The kernel logs boot messages in a ring buffer. To inspect them:
dmesg | less
On systems with systemd, use journalctl:
List recorded boots:
journalctl --list-bootsView the current boot log (
boot 0):journalctl -b 0
To read logs from a different directory:
journalctl -D /var/log/other_directory
Links and References
- Linux Kernel Newbies – Boot Process
- GNU GRUB Manual
- systemd Documentation
- BIOS Basics on Wikipedia
- Unified Extensible Firmware Interface Forum
Watch Video
Watch video content