Microsoft Azure Security Technologies (AZ-500)
App Security
Introduction
Welcome back to our application security module. In this article, we explore critical aspects of application security as part of a comprehensive defense-in-depth strategy. Our lessons have progressively covered various security layers, including physical security, identity and access management, perimeter security, network security, compute security (such as host and container security), and now, application security.
Below is the defense-in-depth diagram illustrating these multiple layers:
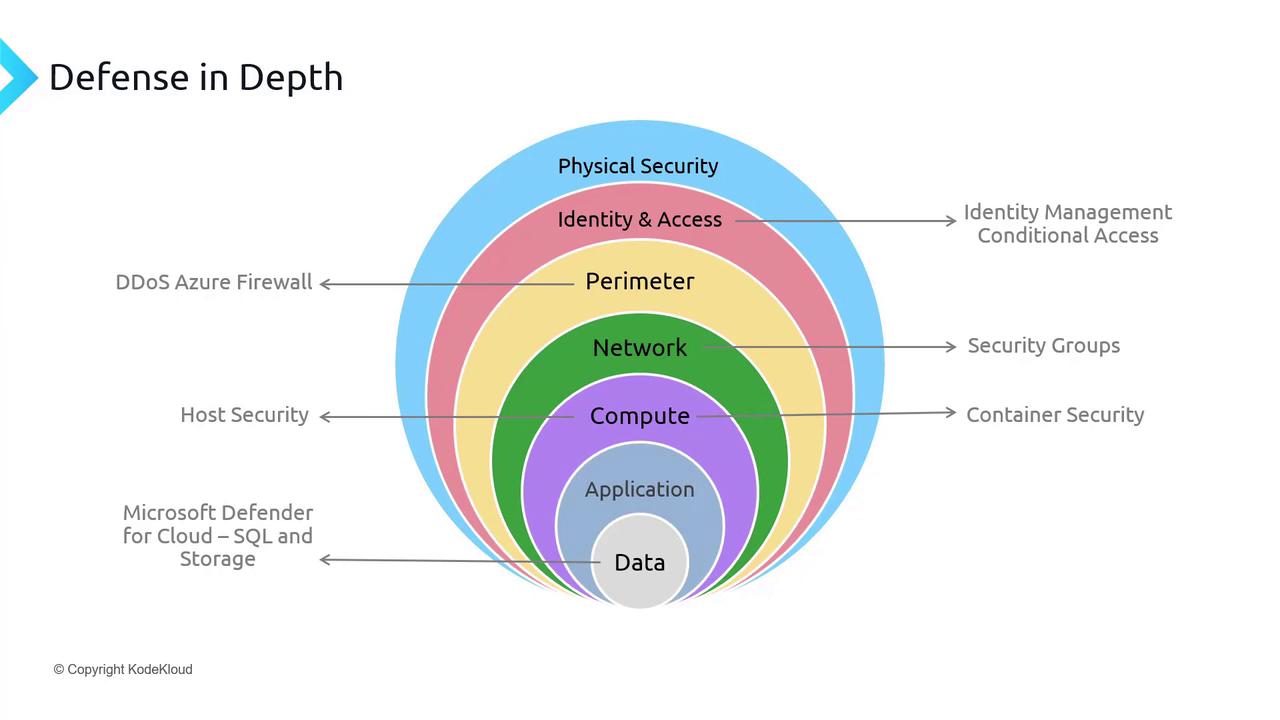
A key element within application security is the Key Vault. In this module, we will delve into several essential topics, including:
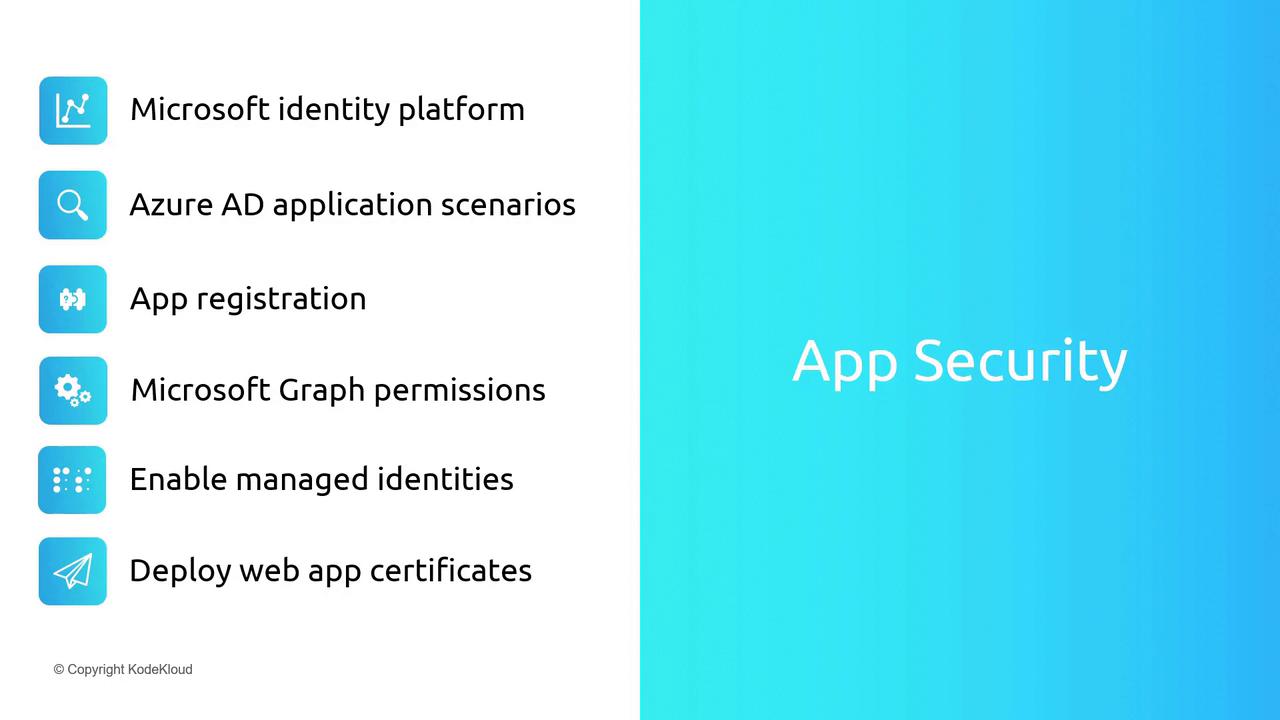
- Microsoft Identity Platform
- Azure AD Application Scenarios
- App Registration (with a focus on service principals, as briefly introduced in our previous lesson)
- Microsoft Graph Permissions
- Enabling Managed Identities
- Deploying Web App Certificates (with an emphasis on securing AMP services)
The diagram below outlines the primary topics we will cover:
Note
For a detailed understanding of these topics, consider reviewing related articles on Microsoft Identity Platform and Azure AD Application Scenarios.
This overview concludes our introduction to application security. Let's begin by exploring the Microsoft Identity Platform in depth.
Watch Video
Watch video content