Architecture Overview
Azure Container Instances enable you to run containers within a virtual network for secure communication with both internal and external workloads. At the heart of the deployment is the virtual network, which hosts the container environment managed by Microsoft. As an administrator, you simply provide the container image; Azure automatically retrieves it from a repository and provisions it with the necessary resources. Inside the container host, your application and its dependencies run isolated from the underlying infrastructure. By eliminating the need to manage virtual machines or container runtimes (e.g., Docker), ACI ensures a rapid and straightforward deployment process. The container application is typically set to listen on port 80, making it accessible via a public IP address. In summary, ACI provides an efficient, managed solution for deploying containerized applications securely and with minimal overhead.Benefits of Azure Container Instances
Faster Startup
Containers in ACI are agile and lightweight, starting in just a few seconds compared to minutes for traditional virtual machines. This rapid startup ensures high application availability and a seamless user experience.Internet-Facing Applications
ACI supports the assignment of public IP addresses and DNS labels, making it an excellent choice for hosting internet-facing applications while ensuring robust security.Isolation and Security
Each container operates in an isolated environment, even when hosted on the same physical machine. This isolation enhances security and minimizes risks such as container breakouts. With Microsoft managing the infrastructure, vulnerabilities related to container runtimes are significantly reduced.Scalability and Flexibility
ACI allows you to customize resource allocations by specifying the number of CPUs, memory, and even GPU support as needed. This level of scalability is perfect for dynamic workloads across various application types.Persistent Storage
While container storage is generally ephemeral, Azure provides options like Azure Files and Azure Disk to secure persistent storage, ensuring that important data remains intact even after container restarts.Seamless Integration
ACI seamlessly integrates with your existing network infrastructure by deploying containers into virtual networks. The service supports both Windows and Linux-based containers, making it versatile for a variety of applications.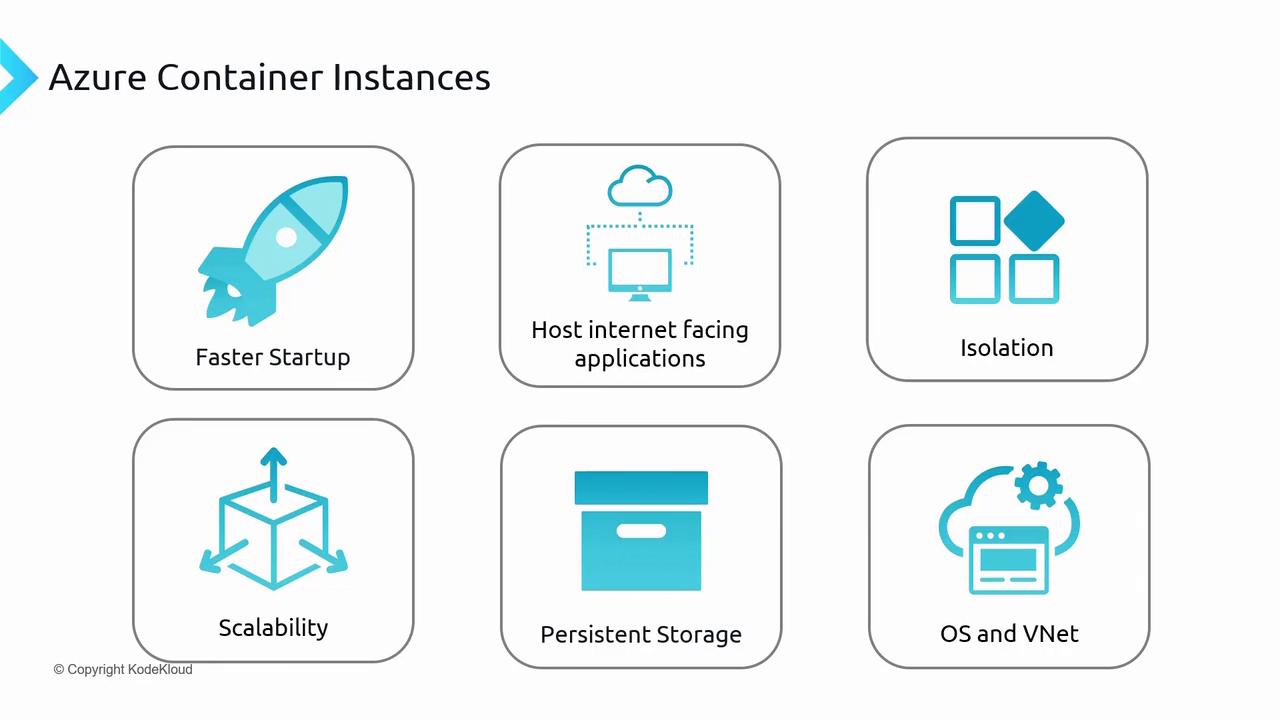
Security Considerations in ACI
When exposing container applications to the internet, it is essential to address various security threats:-
DDoS Attacks:
Exposure to the internet increases the potential for DDoS attacks. Enabling Azure’s DDoS Protection plan is a recommended mitigation measure. -
Poisoned Images:
To avoid malicious container images, utilize the Azure Container Registry (ACR) for image storage and management. ACR, combined with Microsoft Defender for Cloud, scans images for vulnerabilities. Additionally, enabling Content Trust ensures that only signed, trusted images are deployed. -
Container Breakout:
Although the risk is reduced by isolation, the potential for container breakout exists. Azure’s managed infrastructure includes multiple security measures to further minimize this risk. -
Kernel Exploits and Compromised Secrets:
Sharing the same OS kernel can expose containers to kernel-level vulnerabilities. Azure proactively monitors and updates the container host to protect against such exploits. For sensitive information like API keys or database credentials, Azure Key Vault provides secure management. With Managed Identity, containers can safely access secrets from the Key Vault without exposing them in the application configuration.
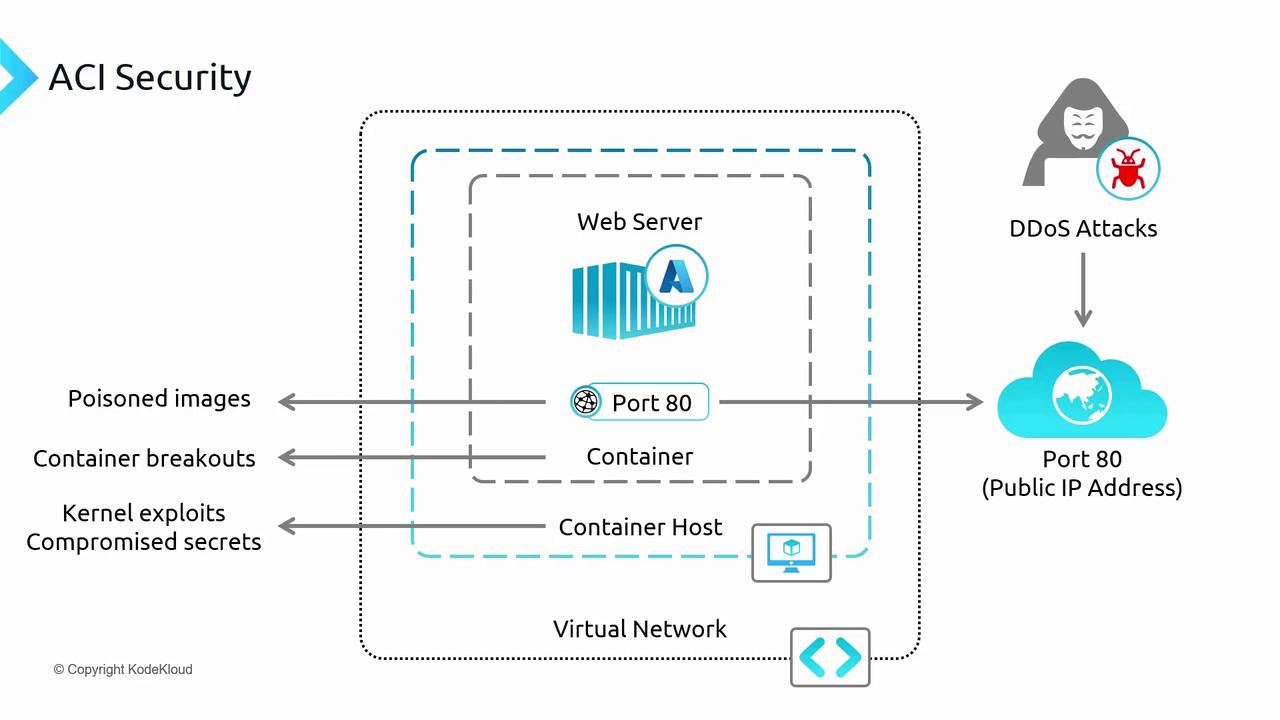
Implementing the recommended security practices will help you maintain secure container deployments while enjoying the benefits of a managed service.
Deploying an Azure Container Instance via the Azure Portal
Follow these steps to deploy a container instance using the Azure Portal:-
Access Container Instances:
In the Azure Portal, use the search bar to find “container instances” and select the service. -
Initiate a New Deployment:
Click on “Create” to start a new container instance setup. -
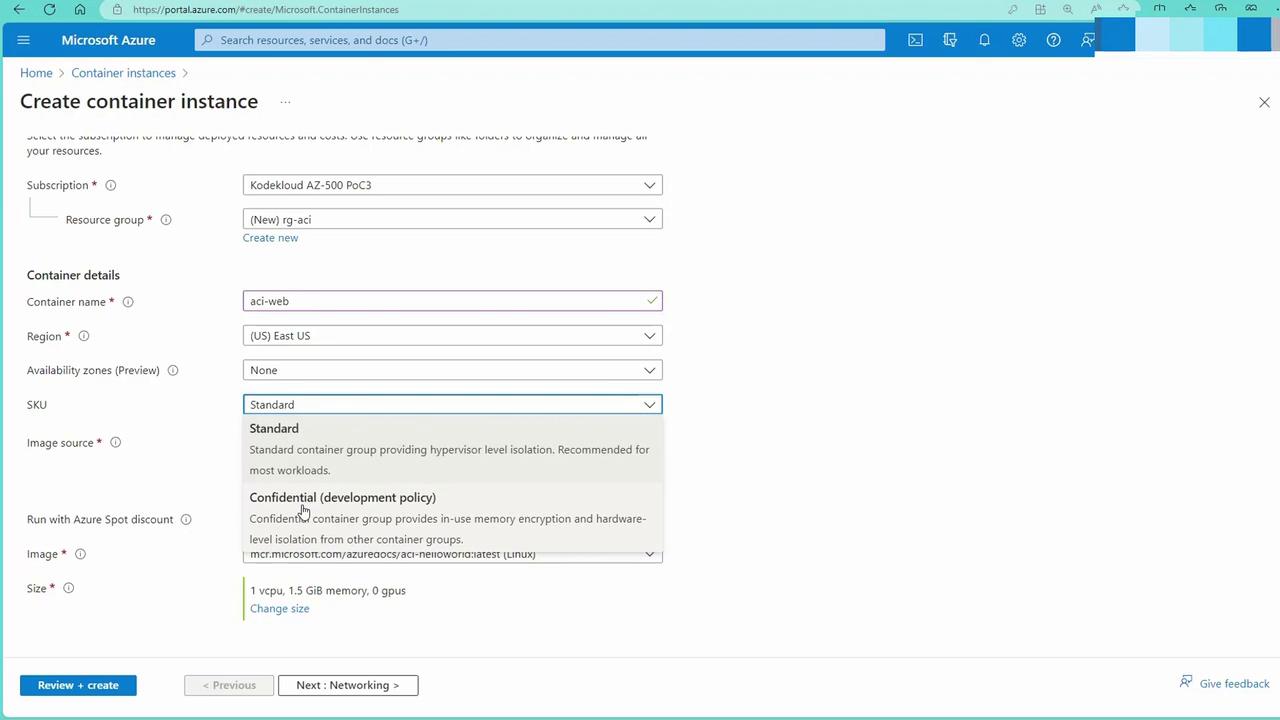
Configure Basic Settings:
- Create a new resource group (e.g., RGACI) or select an existing one.
- Specify a name for your container instance (e.g., ACI Web).
-
Container Details:
Choose the container image source. Options include kickstart images available in Azure, images from the Azure Container Registry, or from repositories like Docker Hub. For demonstration, select the Nginx image. -
Operating System:
Select the appropriate OS (Linux or Windows) based on your application requirements. -
Size and Scaling:
Configure the container’s resources by choosing the desired number of CPUs and memory. ACI provides custom size options ranging from 1 to 8 cores and 1 to 32 GB of memory. GPU support is also available if needed.
-
Set Up Networking:
- Choose the networking type (public, private, or none).
- Configure the DNS label to expose your application over the internet.
- Designate the necessary ports (e.g., port 80 for Nginx).
-
Restart Policy:
Set the restart policy for the container (default is “on failure”). -
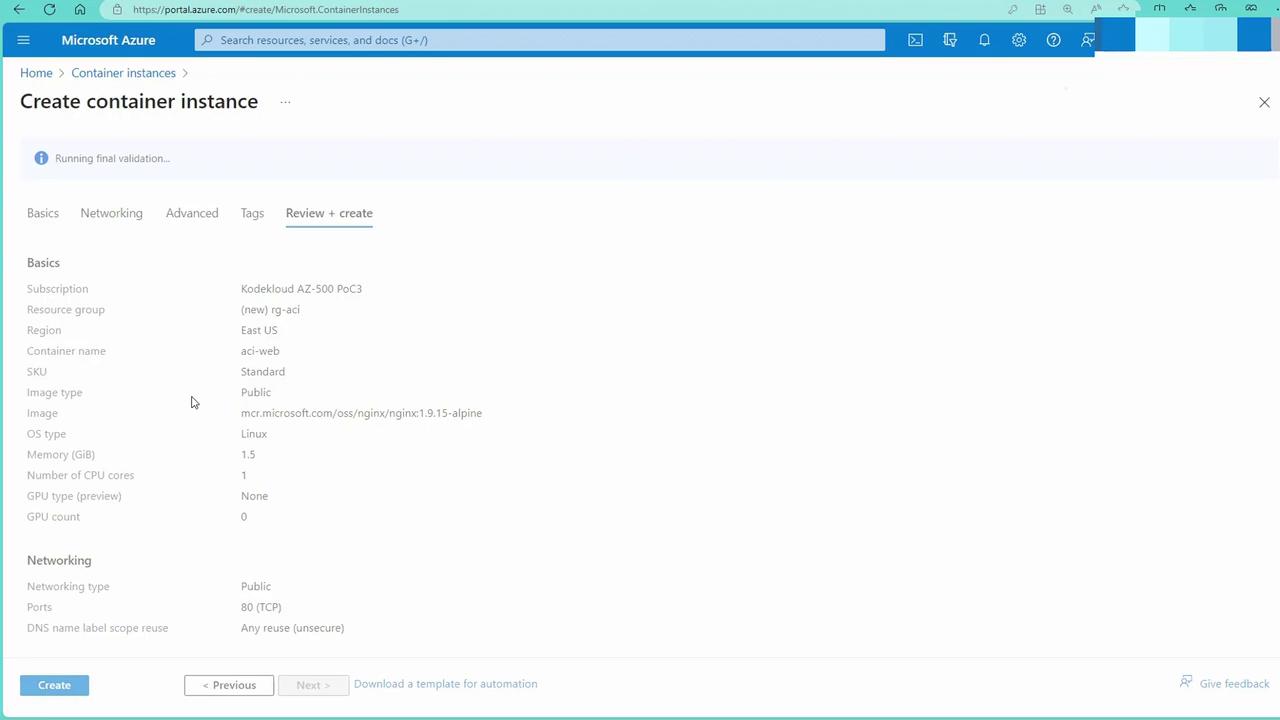
Review and Create:
Review your configuration settings and click “Create” to deploy the container instance. Typically, the deployment completes in under a minute.
Exploring Container Apps
While ACI is ideal for simple container deployments—often utilized in Kubernetes-related tasks—Azure also offers Container Apps for more complex, multi-container solutions. Container Apps provide advanced scaling, integration with services like Application Gateway and Azure Front Door, and seamless Kubernetes integration. Microsoft recommends transitioning to Container Apps when running complex deployments, although ACI remains a practical choice for straightforward scenarios.
Verifying the Deployment
After deploying your container instance, verify its status in the Azure Portal:- Navigate to the “Containers” section to check that your container is running.
- Open the terminal interface under the “Connect” tab for real-time management.
- For example, if you deployed an Nginx container, copy the public IP address from the overview page, paste it into your browser, and you should see the “Welcome to NGINX” page.