Microsoft Azure Security Technologies (AZ-500)
Database Security
Introduction
Welcome to this lesson on database security, where we dive into a comprehensive defense-in-depth strategy tailored to protect your data assets.
In today's article, we begin by reviewing a multi-layered security strategy that starts with physical security—managed by Microsoft—and extends into several additional layers of protection. These layers include identity and access management, perimeter security, network security, host security, container security, and application security. Having already covered storage and data security, we now turn our focus to databases, a critical component in maintaining robust data protection.
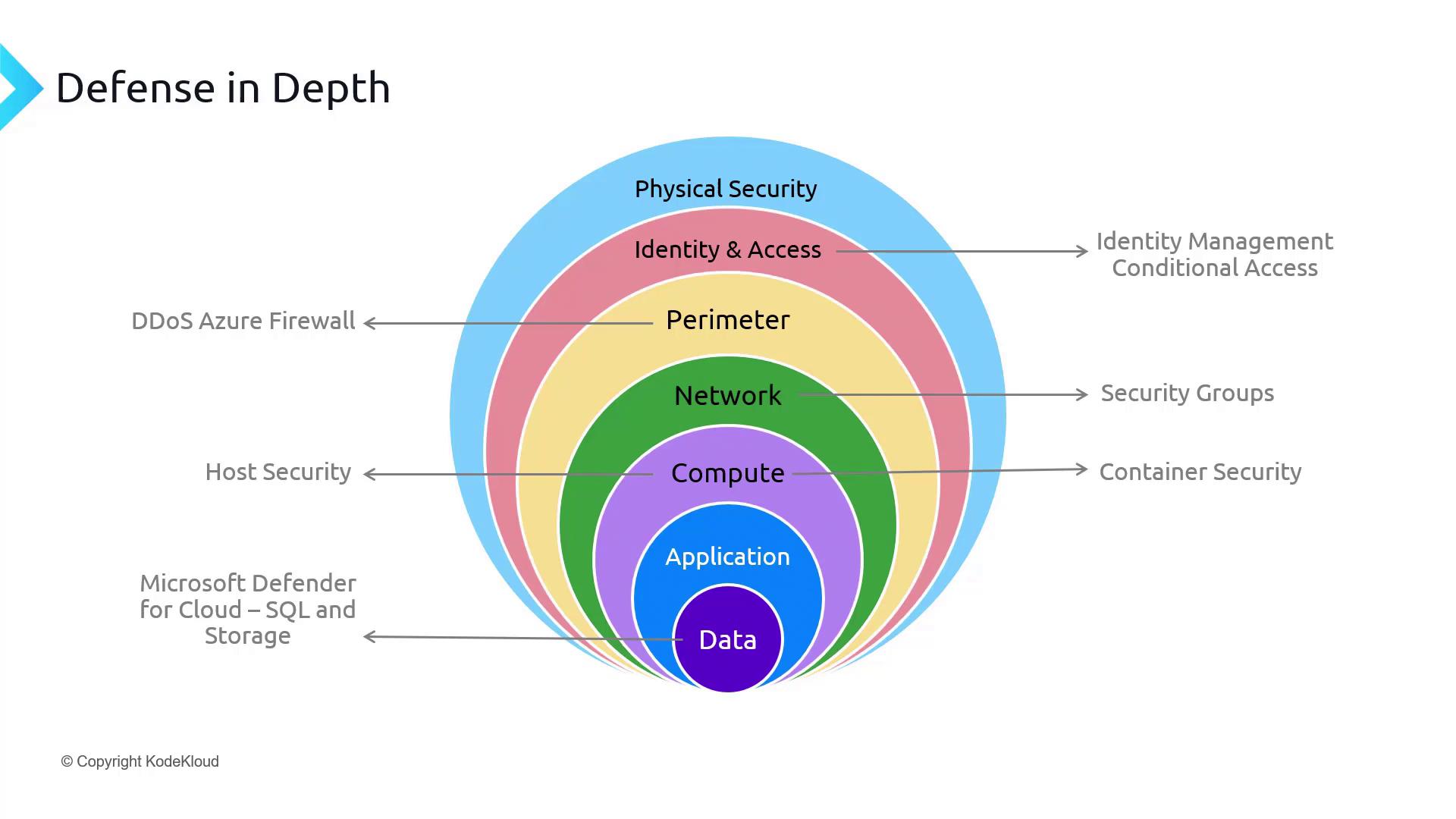
Note
This layered security approach not only safeguards your data but also helps you meet various compliance and regulatory requirements.
Following our introduction to database security, we will explore key topics including monitoring, Defender for Cloud, and Sentinel. Our discussion will cover in-depth strategies for securing SQL databases. The main topics include:
- Enabling SQL Database authentication
- Configuring SQL Database firewalls
- Implementing monitoring and auditing
- Utilizing data discovery and classification techniques
- Performing vulnerability assessments
- Leveraging Defender for SQL
- Applying dynamic data masking
- Implementing Transparent Data Encryption (TDE)
- Using Always Encrypted along with its features and implementation strategies
Let’s get started by exploring how to implement SQL authentication as the first step towards a secure database environment.
For more insights into database security and related technologies, continue reading and refer to our additional documentation and external resources, such as Kubernetes Basics.
Watch Video
Watch video content