Key Aspects of Endpoint Protection
Antivirus and Anti-Malware
Azure Endpoint Protection employs state-of-the-art antivirus and anti-malware mechanisms to shield your systems from malicious software, including viruses and other forms of malware. Leveraging industry-leading threat intelligence and machine learning algorithms, the solution continuously scans your endpoints, promptly detects potential threats, and prevents unauthorized access and infections.Behavioral Analysis
In addition to traditional signature-based detection, the protection solution uses behavioral analysis to monitor application and process activities. By identifying anomalies and suspicious behavior, it effectively detects advanced threats that might bypass conventional security methods.Real-Time Threat Intelligence
Integration with Microsoft’s expansive threat intelligence network ensures that your endpoints receive real-time updates about emerging threats and vulnerabilities. This continuous updating process reinforces your defense systems with the latest threat definitions, fortifying your environment against evolving cyberattacks.Automated Remediation
When a threat is detected, Azure Endpoint Protection automatically initiates remediation procedures. The solution can quarantine or remove malicious files, block suspicious network connections, and execute other proactive measures to reduce the impact of security incidents. This rapid response minimizes downtime and lowers the risk of data breaches.Centralized Management
Centralized management is provided through a unified console that simplifies the administration of security policies across all endpoints. This approach ensures operational efficiency and consistent security measures throughout your organization.Integration with Microsoft Defender for Cloud
Azure Endpoint Protection seamlessly integrates with Microsoft Defender for Cloud (formerly Azure Security Center) to deliver comprehensive security insights. This integration not only quarantines malicious files but also updates threat intelligence to help prevent similar attacks. For instance, if a vulnerability is discovered and exploited, real-time updates facilitate prompt protective measures.For enhanced protection, always ensure that your Azure environment is integrated with Microsoft Defender for Cloud to benefit from its advanced threat detection and response capabilities.
Enabling Endpoint Protection in the Azure Portal
Follow these steps to enable endpoint protection using the Azure portal. Within the Azure portal, you will see various endpoint protection extensions. Options include Microsoft Anti-Malware, Trend Micro, and Symantec. Your choice will depend on your specific requirements—note that some options, such as Symantec or Trend Micro, may require a separate vendor subscription. While the Microsoft Anti-Malware solution is easy to install on Windows machines, Linux devices often require third-party solutions like Kaspersky, Trend Micro, or Symantec (typically subscription-based).Installing Microsoft Anti-Malware on a Windows Machine
- In your Windows virtual machine within the Azure portal, navigate to the “Extensions and Applications” section and click on “Add.”
- If Microsoft Anti-Malware is not immediately visible among the list of extensions, search for it using the “Load More” option.
- Select the Microsoft Anti-Malware extension by clicking on it, then choose “Next.”
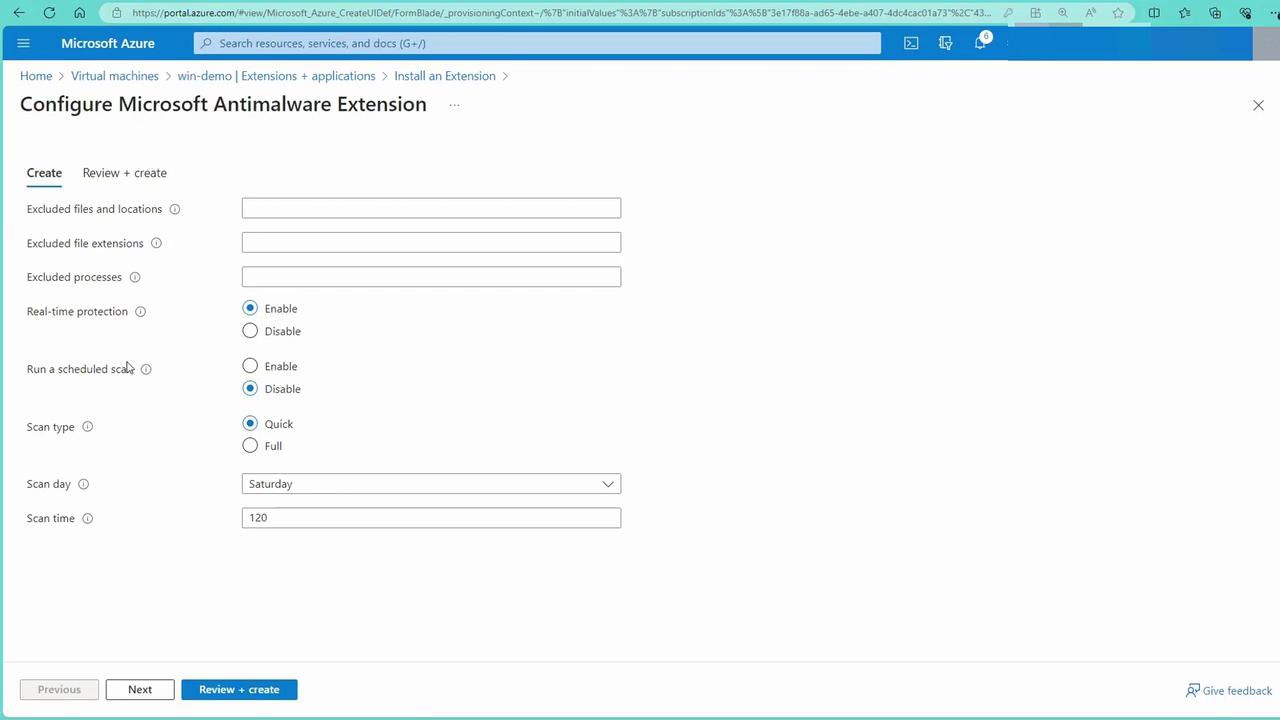
- Configure the extension settings—including exclusions, enabling real-time protection, scheduling scans (specify the scan day and time), and selecting the type of scan.
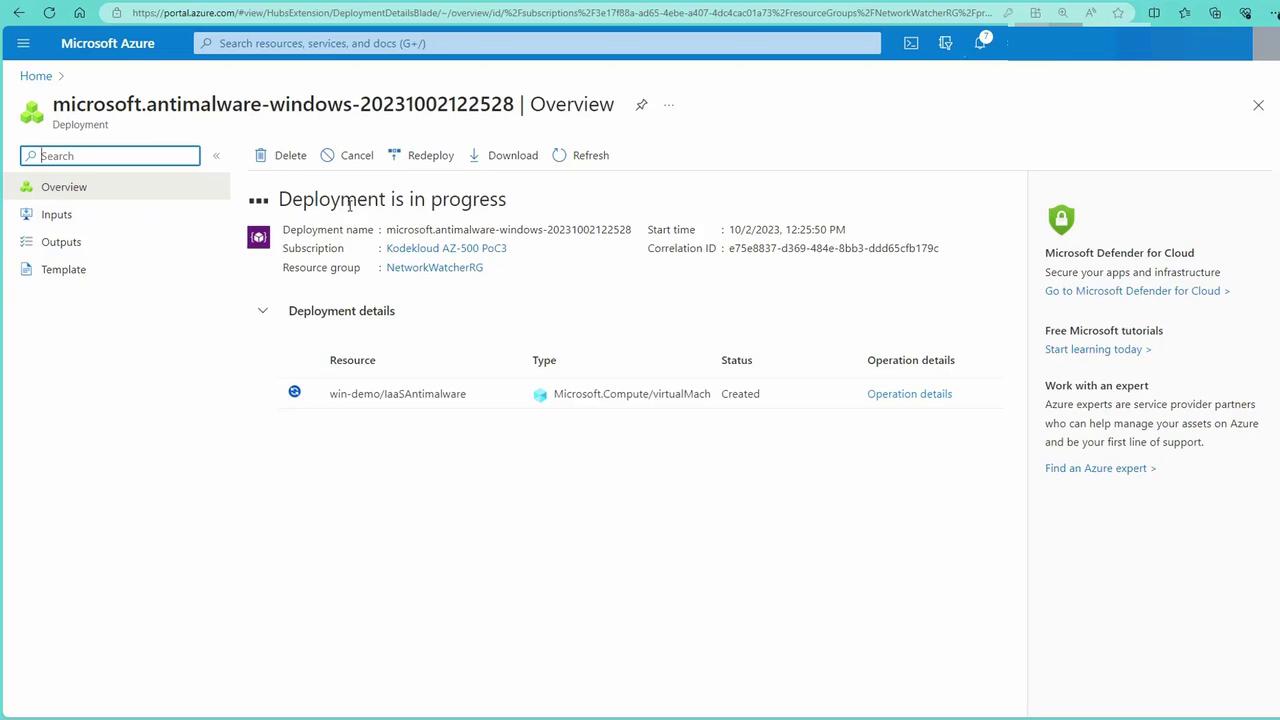
- Click on “Review and Create.” Once validation is complete, initiate the extension deployment.
Monitoring Endpoint Protection with Microsoft Defender for Cloud
Microsoft Defender for Cloud continuously analyzes your environment and provides actionable recommendations for endpoint protection. To view these insights, navigate to the “Recommendations” section and search for “endpoint” to identify any endpoints missing the necessary protection.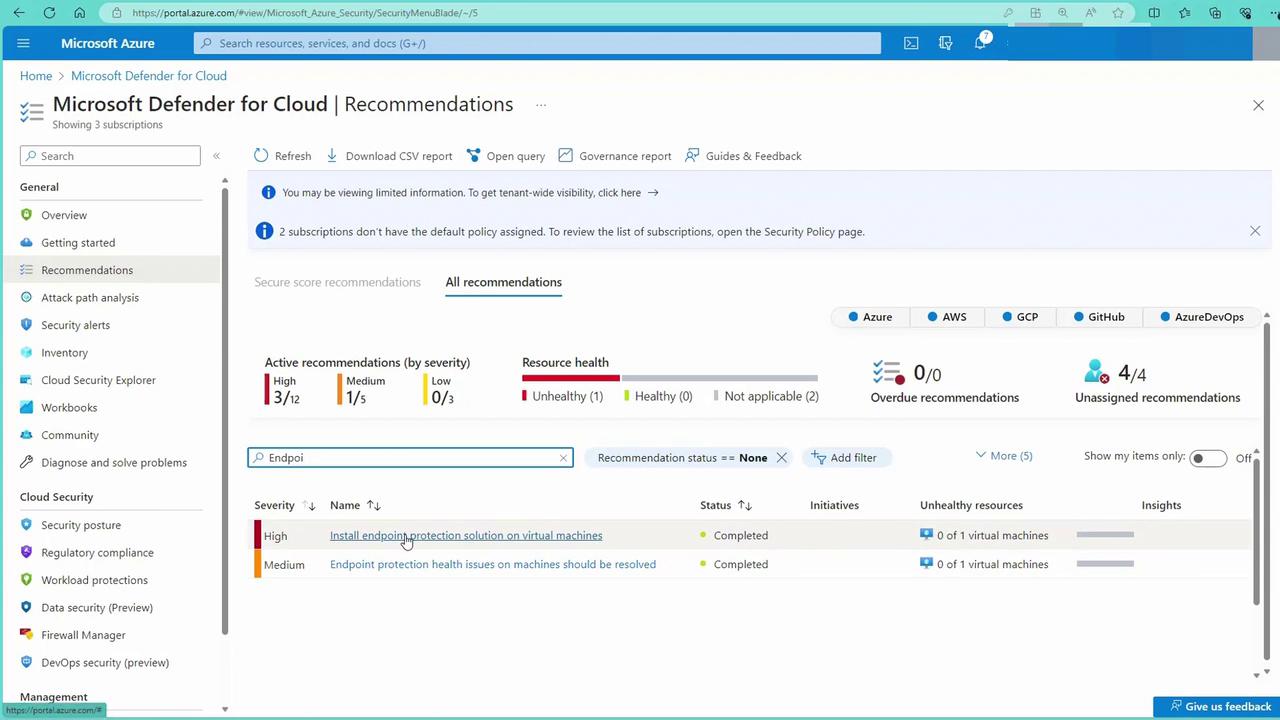
Verifying Deployment on a Windows Machine
Return to your virtual machine’s “Extensions and Applications” section to confirm that the IaaS Anti-malware extension has been successfully installed and is active.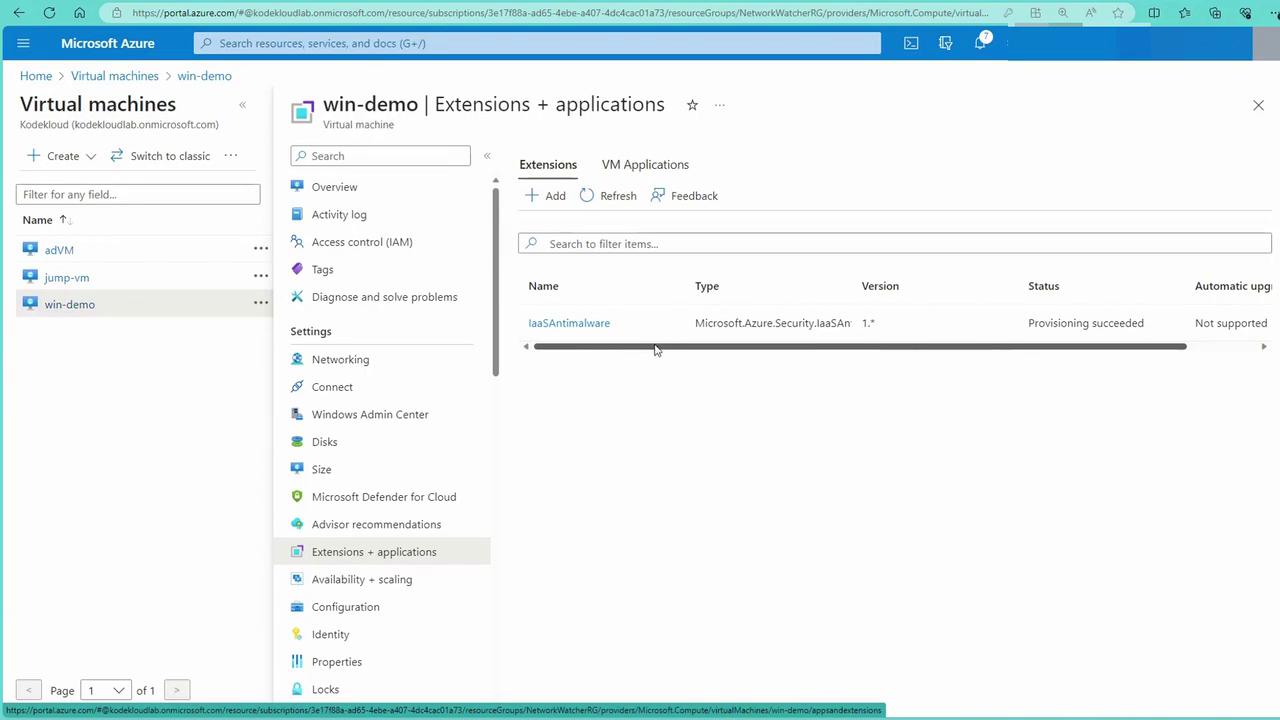
Third-Party Solutions for Linux Machines
For Linux endpoints, several third-party extensions provide robust protection. After clicking “Add” in the Extensions section, you’ll encounter options such as:- Symantec
- SentinelOne
- Kaspersky
- Rapid7 Insight Agent