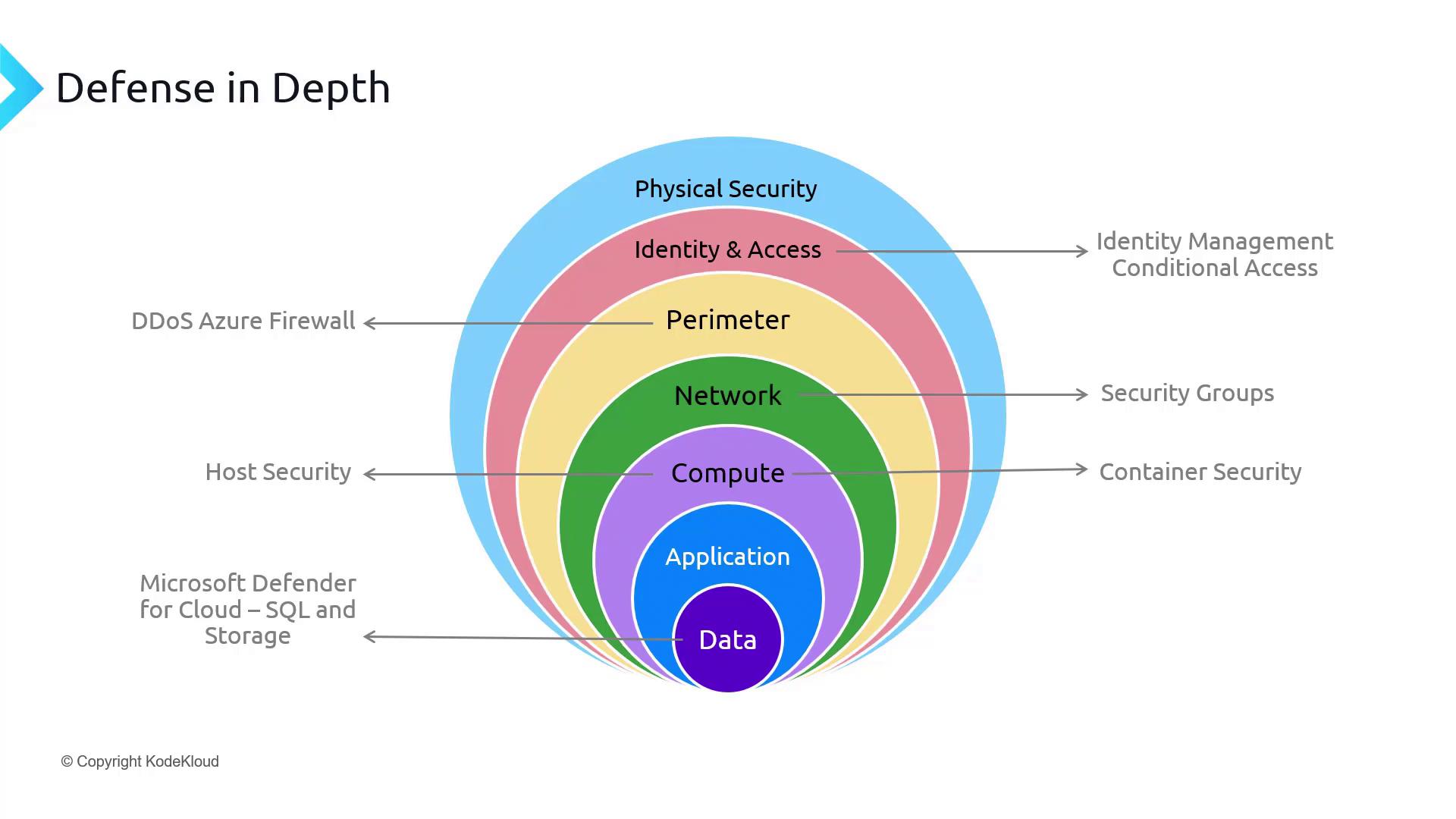
- Host Security: Pertains to Infrastructure as a Service (IaaS) solutions.
- Container Security: Relevant when using Azure Kubernetes Service (AKS), container apps, or container instances. For more details on AKS, refer to the Azure Kubernetes Service documentation.
Topics Covered
This module presents a comprehensive overview of host security best practices, including:- Endpoint protection
- Privileged access device strategy
- Privileged access workstations (PAW)
- Virtual machine templates
- Secure remote access management using Azure Bastion
- Update management configuration
- Disk encryption deployment
- Microsoft Defender for Cloud deployment and configuration (formerly known as Security Center)
- Securing Azure workloads using the Azure Security Benchmark
This guide is designed for IT professionals and security administrators seeking to enhance their understanding of host security within Azure environments.