Microsoft Azure Security Technologies (AZ-500)
Microsoft Defender for Cloud
Configure Defender for Cloud policies
This guide explains how to configure Defender for Cloud policies in Azure to monitor and enforce security compliance. Defender for Cloud allows you to assign various policies—such as the Azure Security Benchmark—and continuously assess your Azure resources against these standards.
Overview of the Azure Security Benchmark
The Azure Security Benchmark provides a comprehensive roadmap for implementing robust security controls. It aligns with multiple compliance frameworks and regulatory requirements including PCI DSS, HIPAA, and GDPR. Integrated directly with Microsoft Defender for Cloud, the benchmark evaluates your resource configurations and offers remediation recommendations based on periodic assessments.
Tip
By assigning the Azure Security Benchmark, you not only secure your environment but also receive targeted recommendations to improve your overall security posture.
How Defender for Cloud Works
Once the required policies are assigned, Defender for Cloud evaluates your Azure resources, checking them against the defined requirements. It then reports on compliance levels and provides clear remediation recommendations. Additional policy initiatives, including PCI or HIPAA, can be incorporated as needed to further tailor your security strategy.
Navigating the Azure Portal
To see these policies in action, follow these steps in the Azure portal:
- Open the portal and navigate to Microsoft Defender for Cloud.
- Enter the environment settings where you enable security plans.
- Click on Edit settings to access the security policies view.
At this point, you might notice that the default initiative is not assigned yet. To deploy it, click on Assign policy to add the Microsoft Cloud Security Benchmark initiative.
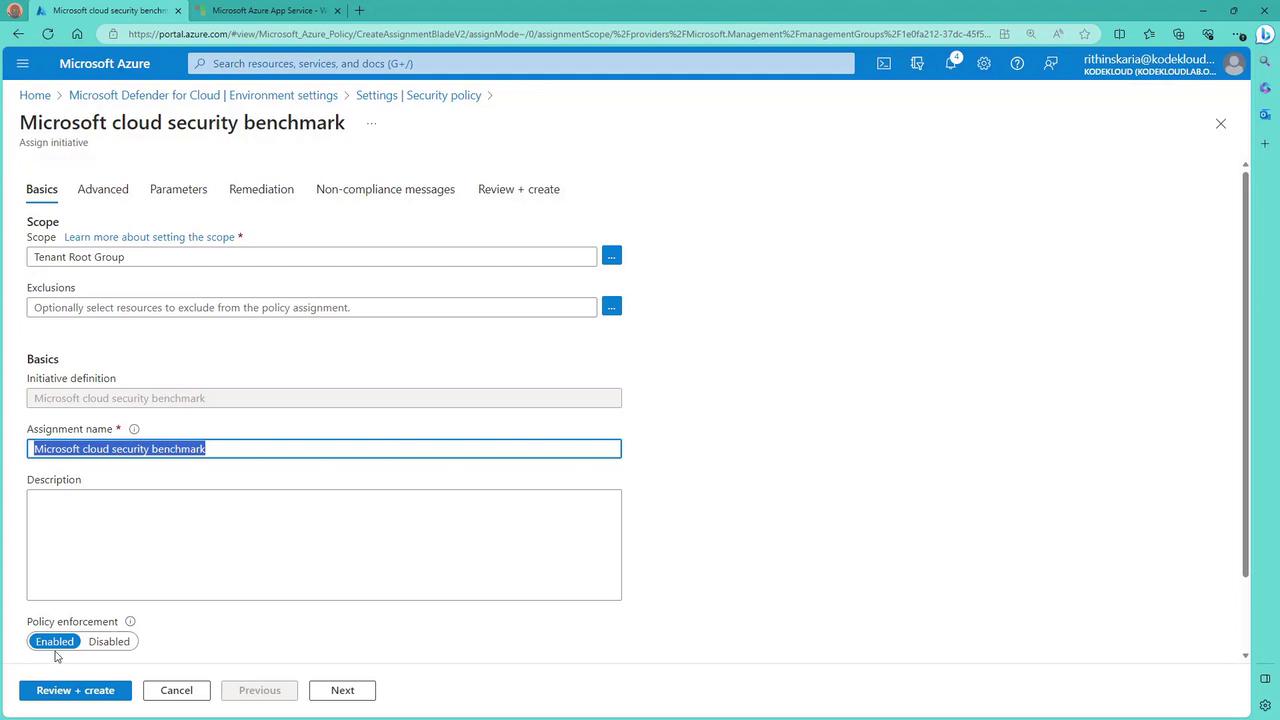
This initiative comprises 210 audit policies, out of which 12 are disabled by default. The comprehensive security recommendations you see for your environment are based on this evaluation.
Adding Additional Regulatory Standards
If you want to include additional standards such as PCI DSS, you can easily do so:
- Locate the PCI DSS standard in the list.
- Click the Add button next to it.
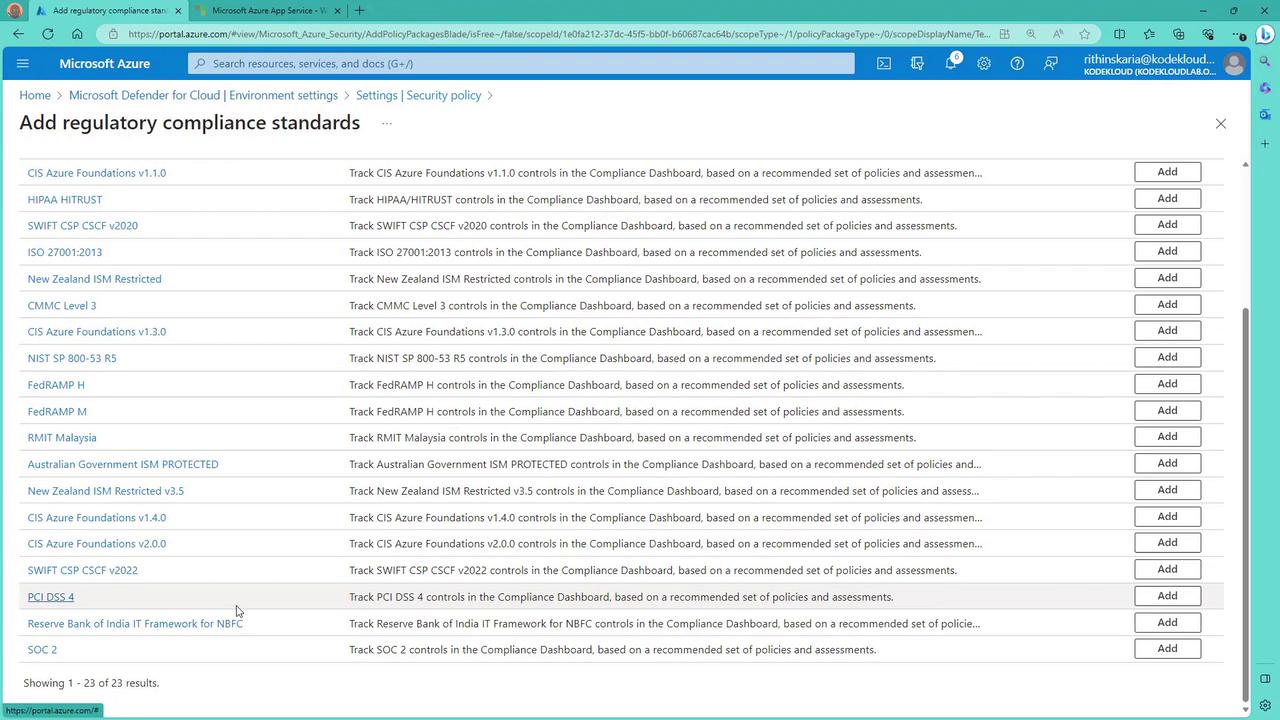
This action opens the policy assignment blade for the selected standard. Once added, the initiative will evaluate your Azure resources against its specific compliance criteria, highlighting any gaps and providing actionable remediation steps.
Next Steps
The following sections will delve deeper into the remediation recommendations generated by these policies and provide guidance on how to address compliance issues effectively.
Summary
By configuring Defender for Cloud policies, you create a proactive security environment for your Azure resources. Using initiatives like the Microsoft Cloud Security Benchmark, you receive continuous assessments and targeted recommendations, ensuring that your security posture meets industry best practices and regulatory requirements.
For more information on Azure Security and compliance, visit Microsoft Defender for Cloud Documentation.
Watch Video
Watch video content