Framework Overview
The Prevent-Detect-Respond framework in Microsoft Defender for Cloud consists of three core pillars:-
Prevent:
Mitigate risks by reducing vulnerabilities and minimizing the attack surface. Microsoft Defender for Cloud leverages security policies, secure score assessments, just-in-time access, and adaptive application controls to proactively prevent threats. -
Detect:
Early identification of malicious activities is crucial for interrupting breaches before they escalate. Defender for Cloud uses advanced threat protection (ATP), integrated threat intelligence, log analytics, and search capabilities to detect threats in real or near real time. -
Respond:
Once a security incident is detected, swift remediation is essential to minimize damage. Microsoft Defender for Cloud offers automated incident response, security alerts, and guided investigations to enable rapid, effective threat containment and recovery.
Core Features of Microsoft Defender for Cloud
Microsoft Defender for Cloud extends the capabilities of Security Center across both private and public cloud environments for unified security management and threat protection. Key features include:-
Broad Coverage:
Defender for Cloud secures a wide range of resources including servers, Kubernetes clusters, storage accounts, SQL databases, key vaults, and more. It supports workloads across on-premises environments, AWS, Azure, and GCP. -
Integration with Defender for Endpoint:
For enhanced server protection, this solution integrates seamlessly with Microsoft Defender for Endpoint, offering comprehensive endpoint detection and response (EDR) capabilities. -
Vulnerability Management:
Benefit from advanced vulnerability scanning for virtual machines and container registries, alongside continuous security assessments and policy enforcement across both on-premises and cloud workloads. -
Advanced Threat Protection:
By utilizing behavior analytics and machine learning, Defender for Cloud identifies sophisticated attacks—including zero-day exploits. Enhanced access and application controls help further minimize potential attack surfaces. -
Container and Application Security:
In addition to server security, Defender for Cloud delivers robust container security with real-time threat protection and vulnerability management. It also safeguards Azure services such as Resource Manager, DNS, Network Security, and Key Vault.
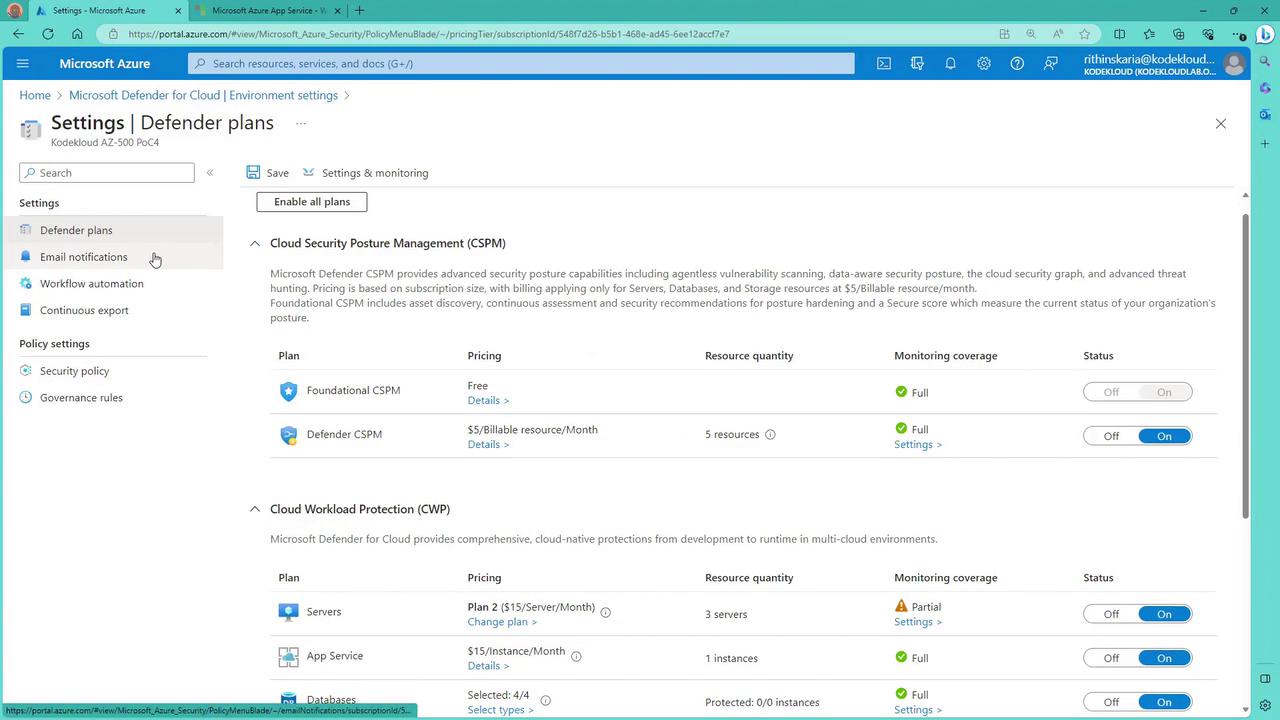
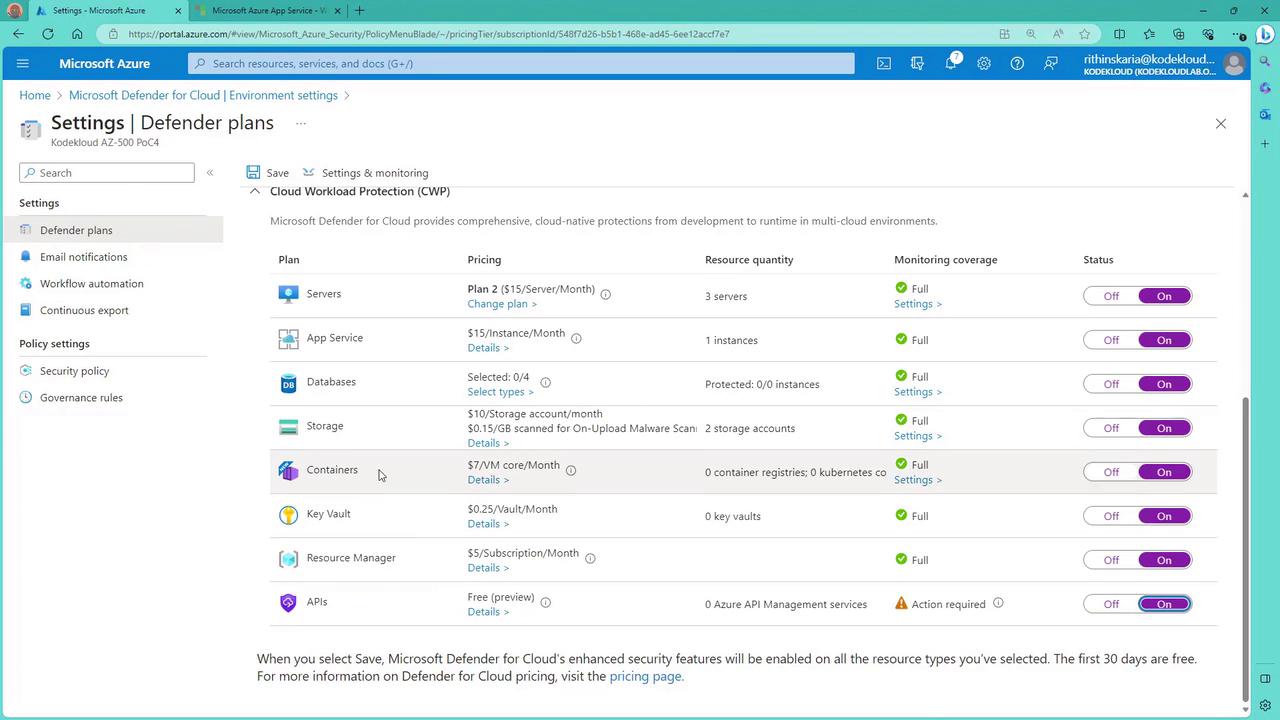
Licensing and Plans
Microsoft Defender for Cloud is available through various plans. Many features are offered at no extra cost, while advanced capabilities may require a subscription upgrade. These plans are enabled at the subscription level, meaning that whenever Defender for Cloud is activated, it secures all servers within that subscription rather than individual systems.Onboarding via the Azure Portal
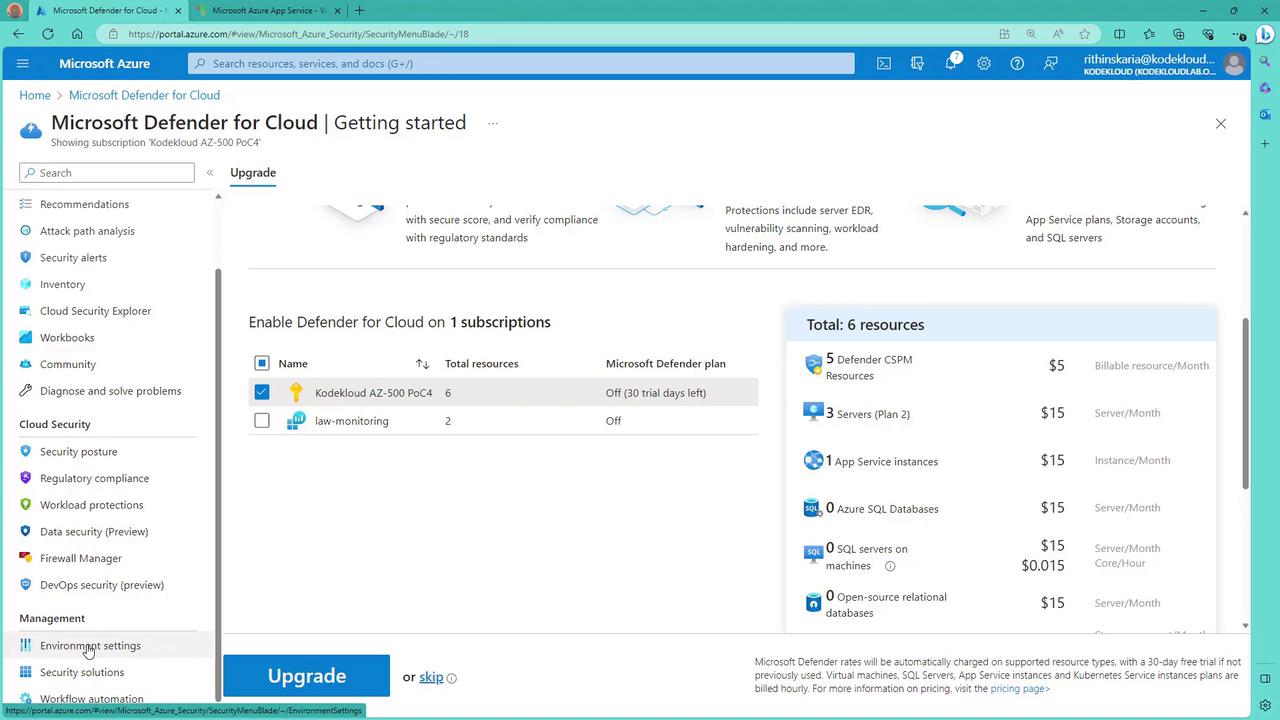
To onboard and configure Microsoft Defender for Cloud:- Log in to the Azure Portal.
- Navigate to the Microsoft Defender for Cloud section.
- If no plan is currently enabled, the portal displays a summary of six available resources that can be upgraded or activated. A 30-day free trial is available for many features.
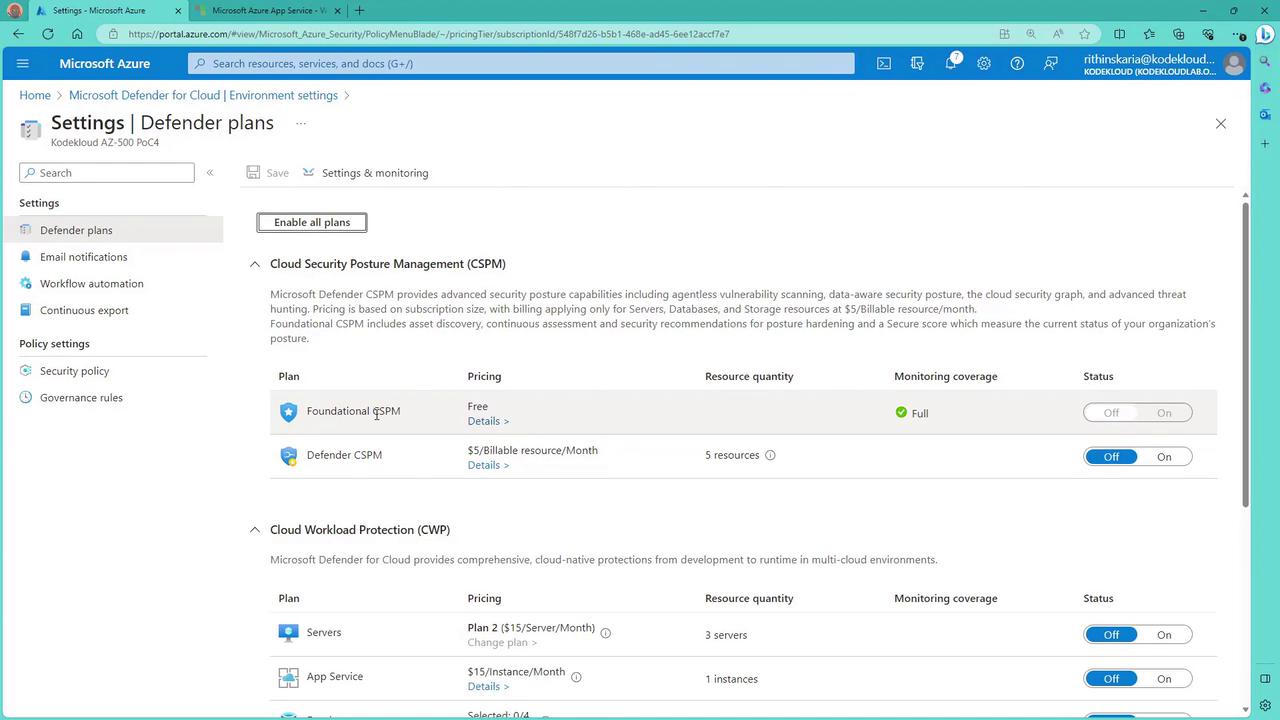
Configuring Server Plans
Within the Azure Portal, you can enable specific security plans for servers:-
Agentless Scanning:
Defender for Cloud provides agentless scanning for virtual machines, offering comprehensive assessments without the need to install an agent. Custom exclusions and parameters can be configured during setup. -
Log Analytics Agent and Custom Workspace:
By default, a Log Analytics Agent is installed automatically when a machine is created. You have the flexibility to change this configuration and link the machine to a custom workspace via the configuration settings.
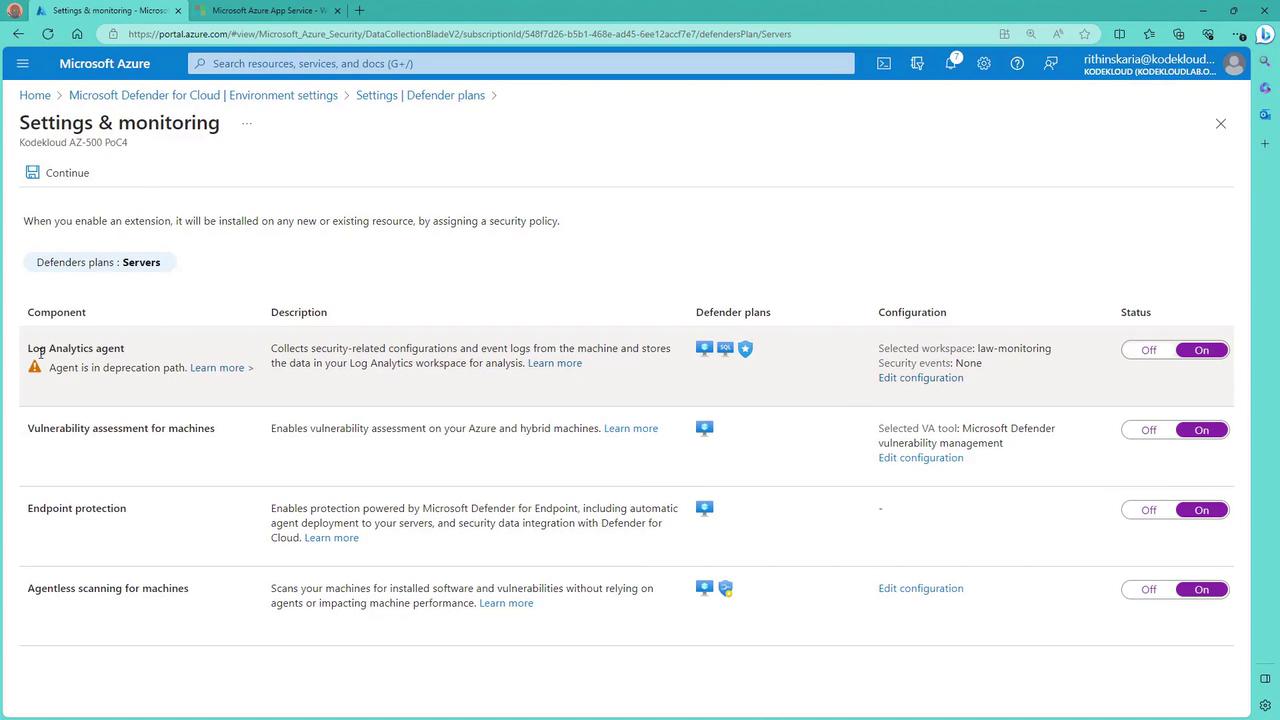
Additional Protection Options
-
Vulnerability Assessment Tools:
Defender for Cloud includes tools like Microsoft Defender for Endpoint (or Vulnerability Management) and also supports third-party solutions like Qualys Scanner for comprehensive vulnerability assessments. -
Endpoint Protection:
When enabled, endpoint protection onboards machines to Microsoft 365 Defender for Endpoint, facilitating agent deployment and enhanced security testing. -
Other Service Plans:
You can also activate plans for App Services and databases. For example, when securing SQL Server workloads, you may enable the Azure Monitoring Agent (currently in preview) as an alternative to the default Log Analytics agent.
Always verify the selected workspace in the settings and monitoring section to ensure that your data is routed to the intended workspace. Misconfigured workspaces can lead to data discrepancies in your monitoring reports.