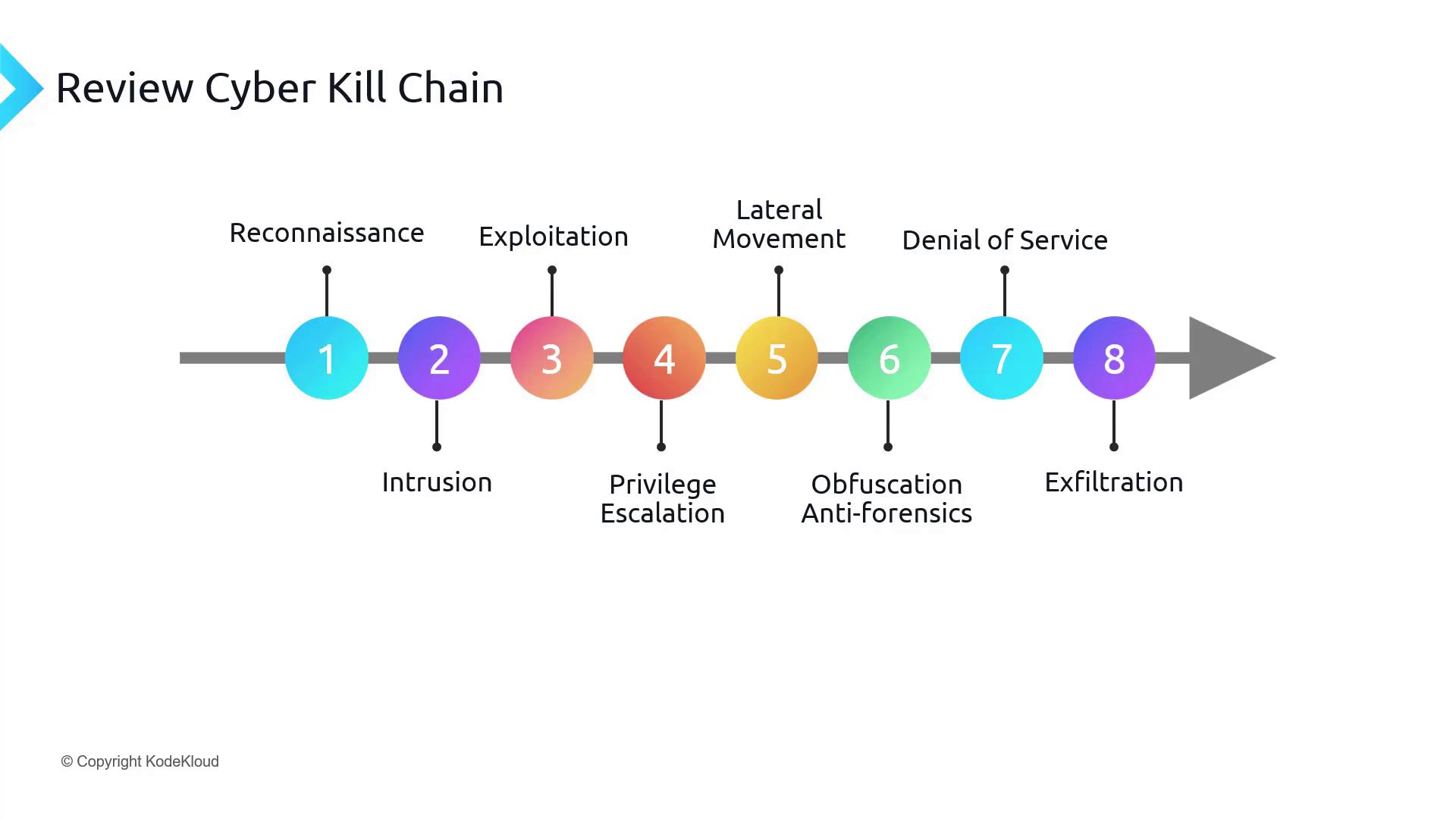
Stages of the Cyber Attack Lifecycle
-
Reconnaissance
The attacker gathers intelligence about the target, identifying vulnerabilities and potential entry points. -
Intrusion
The attacker penetrates the target’s defenses to establish an initial foothold within the environment. -
Exploitation
With the collected intelligence and initial access, the attacker further compromises the system. -
Privilege Escalation
The attacker increases their level of access, enabling control over additional resources and sensitive data. -
Lateral Movement
Once initial access is secured, the attacker moves laterally within the network in search of valuable assets. -
Obfuscation and Antiforensics
The attacker conceals their activities to hinder detection and complicate forensic efforts. -
Denial of Service (DoS)
To divert attention or disrupt operations, the attacker may launch a DoS attack affecting system availability. -
Exfiltration
In the final phase, the attacker extracts valuable data from the compromised system.
Understanding each phase of the Cyber Kill Chain is essential for building effective defense strategies. By identifying and monitoring these stages, organizations can detect early signs of intrusion and prevent further compromise.