Microsoft Azure Security Technologies (AZ-500)
Microsoft Sentinel
Configure playbooks
Microsoft Sentinel offers robust automation capabilities through playbooks—automated response mechanisms built on Azure Logic Apps. These playbooks enable you to define procedures that trigger when specific conditions or alerts are met, significantly reducing the response time to cybersecurity threats. The benefits include faster threat response, consistent mitigation, reduction in manual tasks, and allowing security teams to concentrate on more complex issues.
What Are Playbooks?
A playbook in Microsoft Sentinel is essentially an automated process that eliminates the need for manual intervention by triggering predefined actions when an incident occurs. For example, a playbook can automatically notify relevant personnel, block suspicious IP addresses, or even reset a compromised user's password.
Key Benefit
Automating threat responses ensures that security incidents are managed quickly and uniformly, which is critical in today's fast-paced cybersecurity environment.
Navigating the Azure Portal
To configure playbooks, begin by accessing the Azure portal. On the portal's left-side navigation, locate the automation section at the bottom. This area provides access to playbooks, templates, and active playbooks, making it easier to set up and manage your automation workflows.
Below is an image that illustrates the Microsoft Azure interface for configuring playbooks in Microsoft Sentinel:
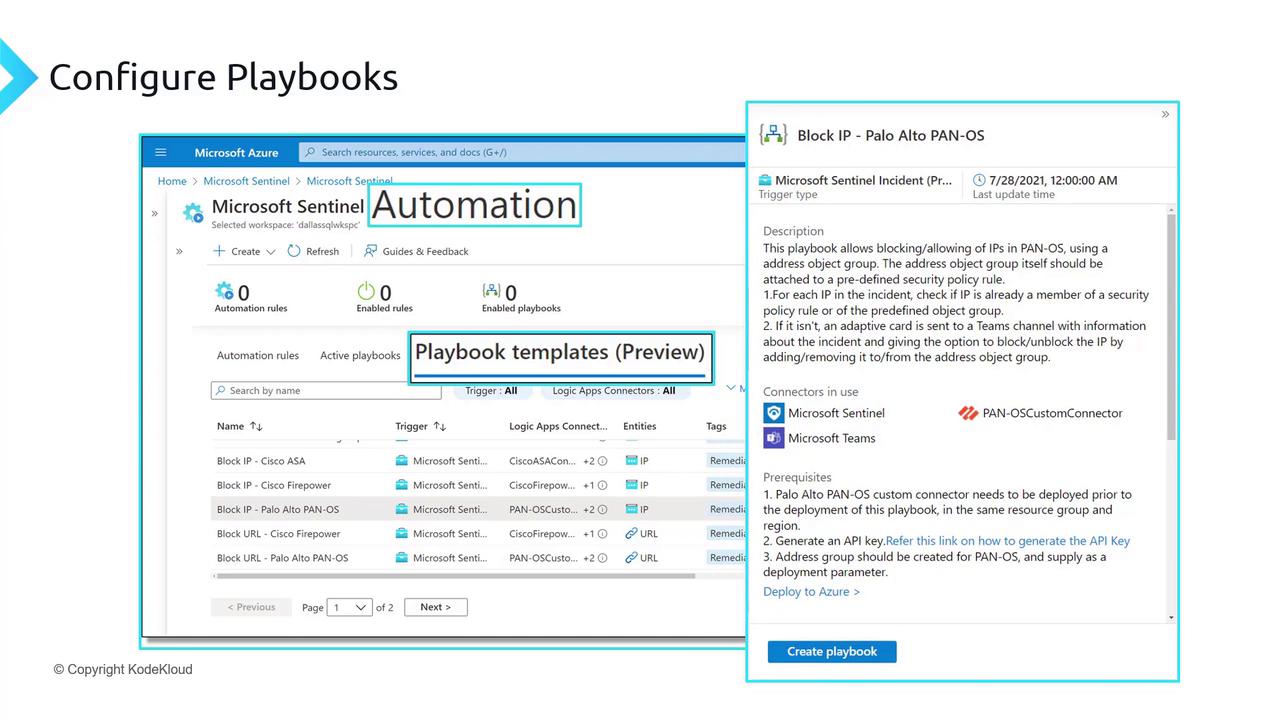
Exploring Playbook Templates
Within the automation section, you will find a variety of out-of-the-box playbook templates. A notable example is the "Notify incident owner in Microsoft Teams" playbook. This template assigns incidents to designated users and sends notifications directly through Microsoft Teams. For instance, if your incident is reassigned from a manager or the SOC team, the playbook will trigger a Teams notification to inform you of the new assignment.
Below is another image showing the Microsoft Sentinel Automation interface with a list of playbook templates that provide details about triggers, Logic App connectors, and associated entities:
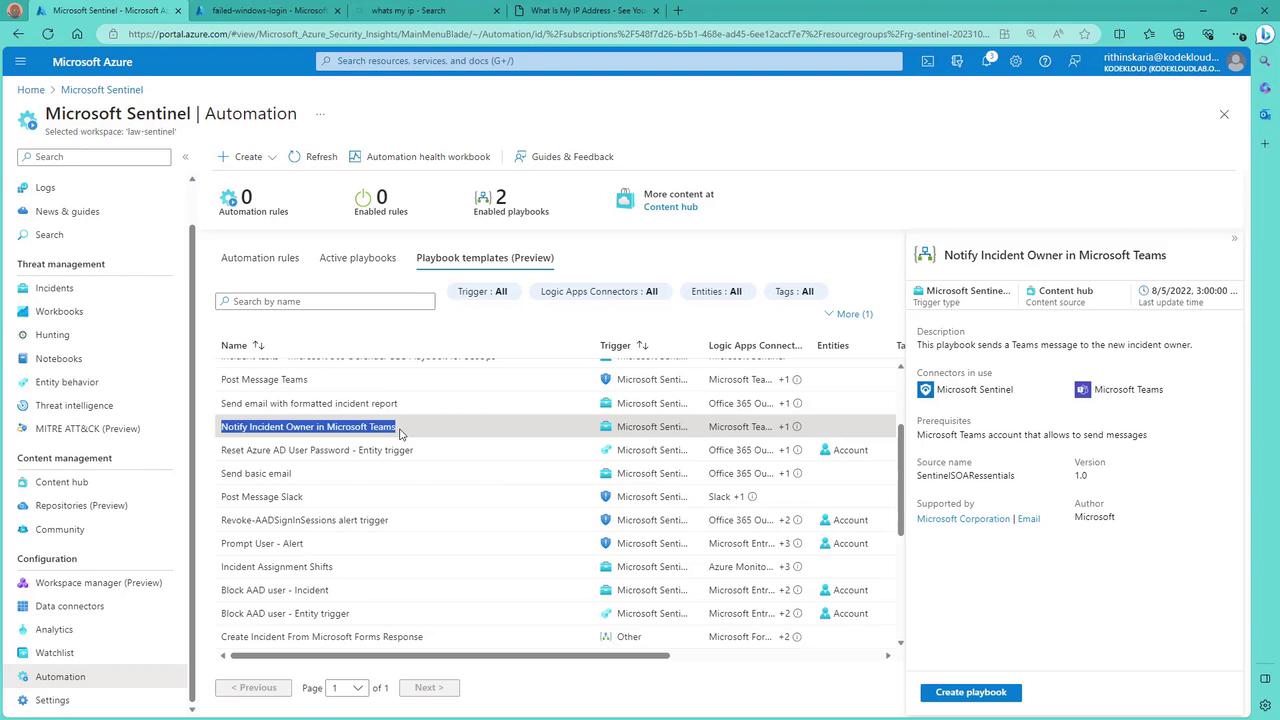
Additional Playbook Options
Microsoft Sentinel includes several other useful playbooks to address different security scenarios. For example:
- Reset Azure AD User Password: If you suspect a user's account is compromised or locked due to suspicious activity, you can automatically trigger this playbook to secure the account.
- Block AD User: In the event of excessive failed login attempts, this playbook disables the account to prevent potential security breaches.
Consider the image below that highlights the "Reset Azure AD User Password" playbook along with other templates available on the dashboard:
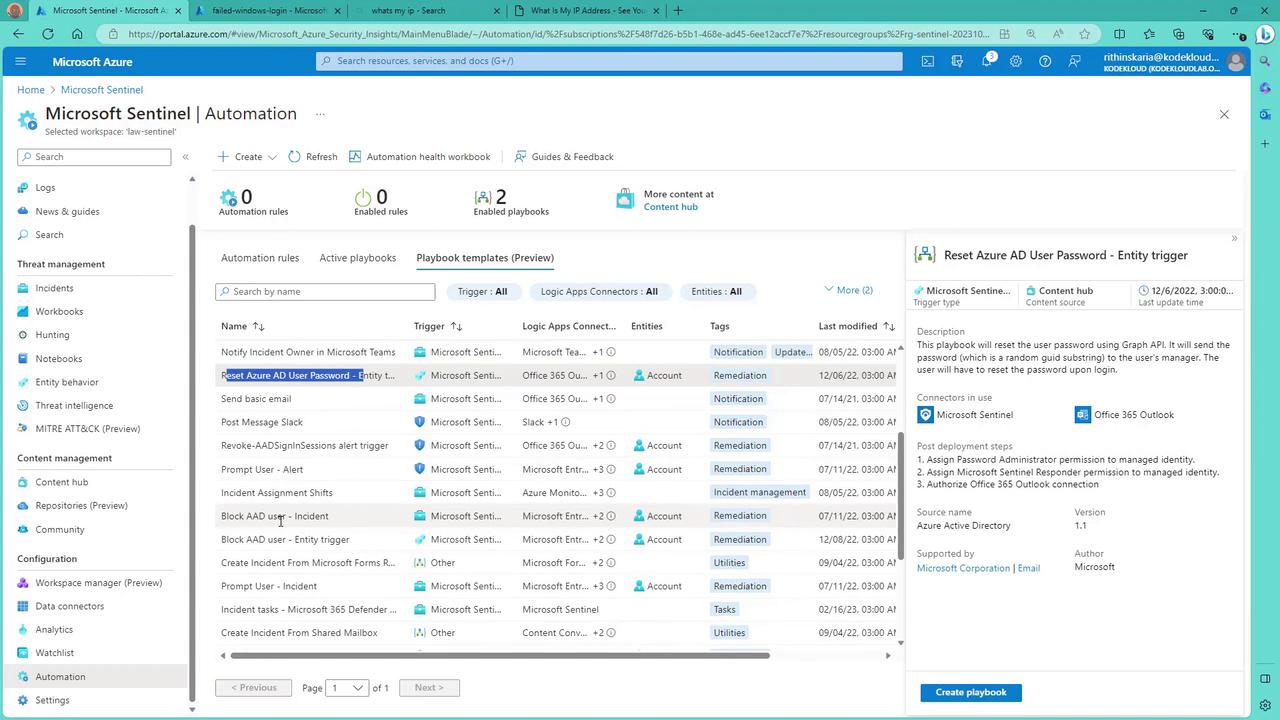
Other playbooks include notifying when an incident is reopened or closed, and posting messages to platforms such as Slack or Teams. Thanks to the extensive range of connectors available in Logic Apps, you are not limited solely to Microsoft services; integrations with Gmail, Google Suite, Slack, and many other platforms are also possible.
Advanced Automation
Leverage these automation capabilities to perform complex actions, such as executing ARM operations. For instance, if a virtual machine (VM) is under attack, you can configure a playbook to automatically shut down the VM to prevent further compromise.
Community and Customization
Remember, you are not limited to the standard templates provided by Microsoft Sentinel. A wealth of community-contributed playbook templates is available on GitHub and other repositories, offering enhanced flexibility and functionality to accommodate your unique security requirements.
With a comprehensive understanding of how to configure and utilize playbooks, you're now ready to dive into the final topic: hunting. Let's begin the hunt.
For further reading, consider exploring Microsoft Sentinel Documentation.
Watch Video
Watch video content