Microsoft Azure Security Technologies (AZ-500)
Secure Azure solution with Azure Active Directory
Deploy Azure AD DS
In this guide, you'll learn how to deploy Azure AD Domain Services using the Azure portal. The walkthrough covers configuring the service, setting up network integration, and joining a Windows Server VM to the domain. Follow along with the step-by-step instructions and accompanying screenshots.
1. Launching Azure AD Domain Services in the Azure Portal
Begin by logging into your Azure portal and searching for "Azure AD Domain Services." This will locate the service along with accompanying documentation and related services.
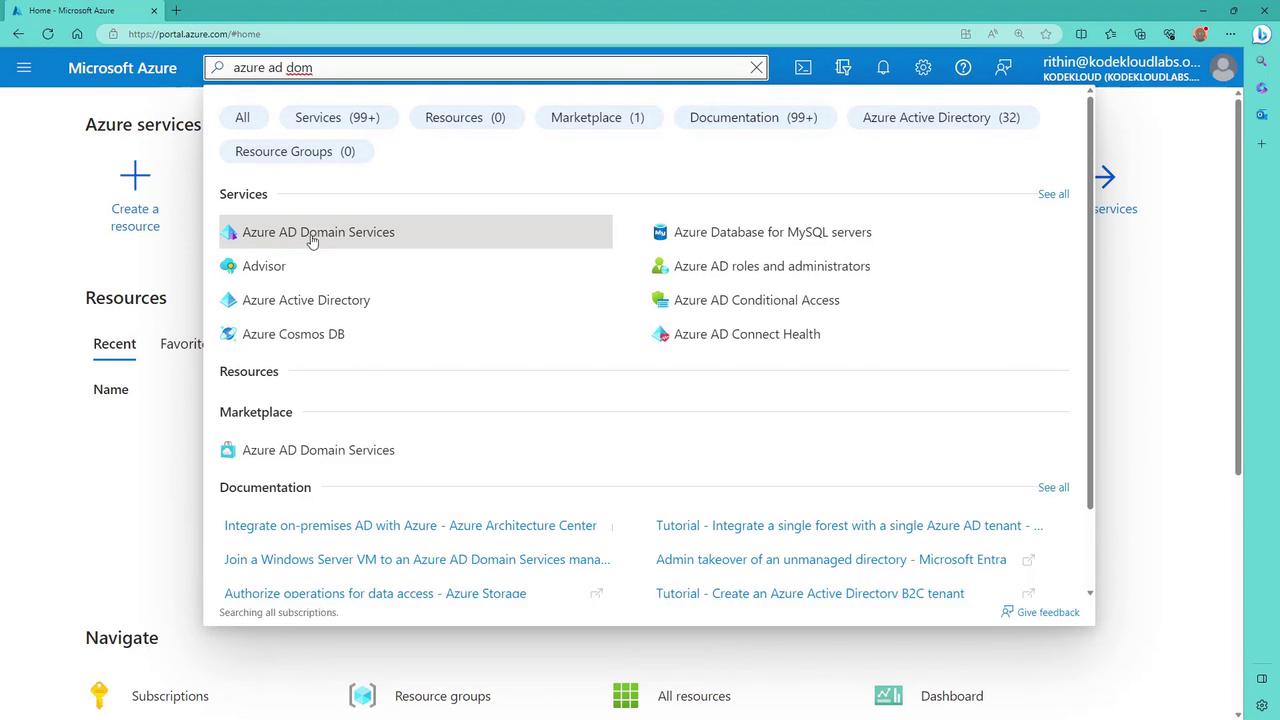
2. Creating the Azure AD Domain Services Resource
To deploy the service, you must first create an Azure AD Domain Services resource. Start with a resource group (for instance, name it “RG”) and specify a DNS name. For seamless integration with your existing Azure AD, use your default Azure AD DNS name to maintain a consistent domain across services.
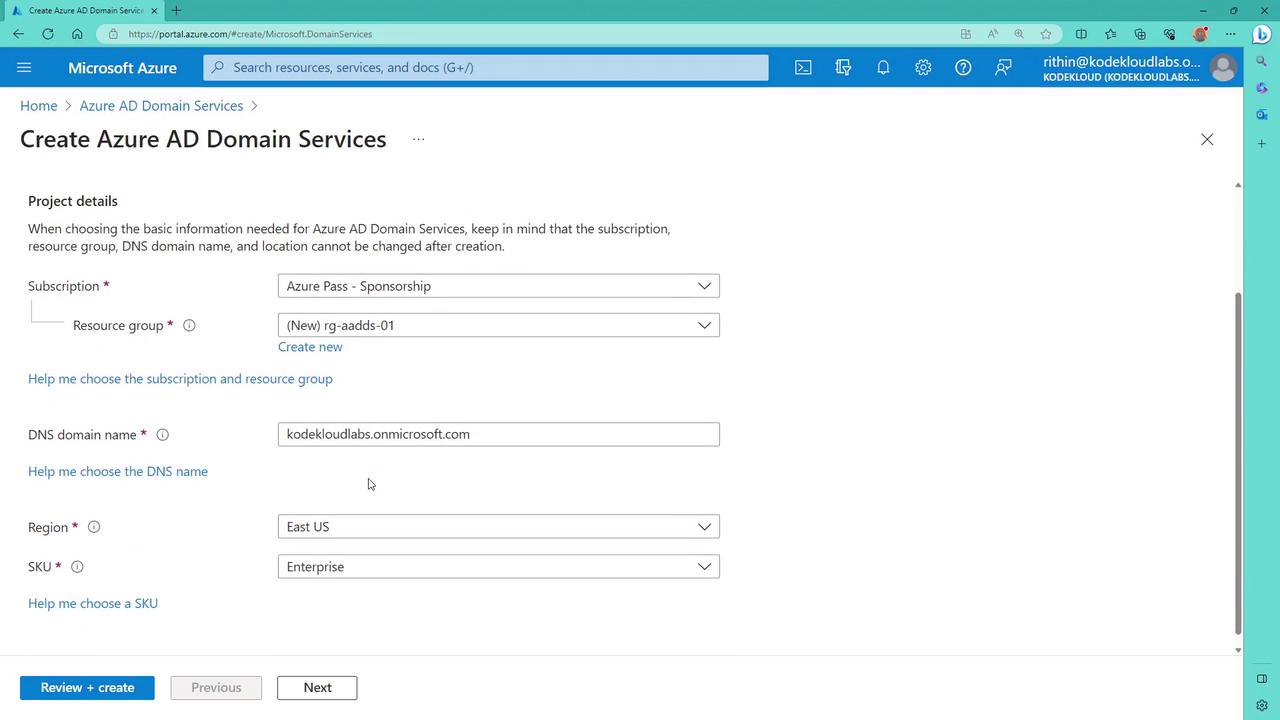
3. Configuring Region, SKU, and Pricing
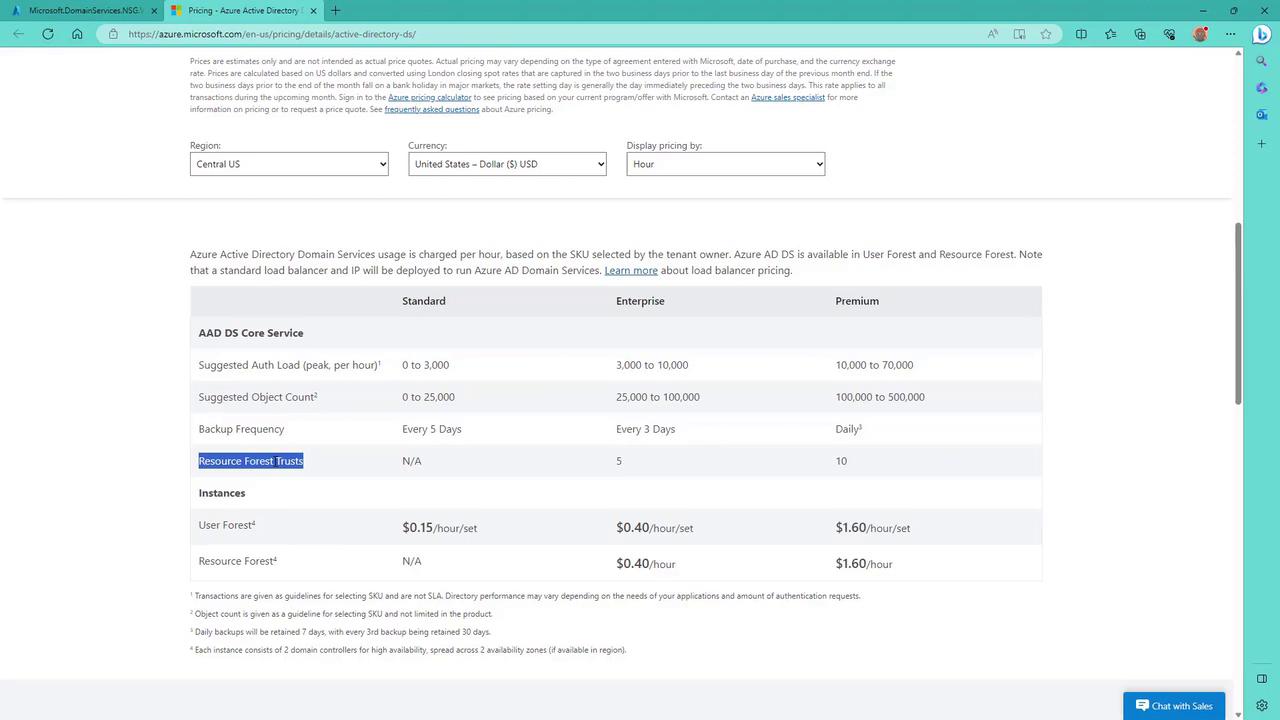
Select your preferred region (e.g., East US) and choose an appropriate SKU from enterprise, standard, or premium. If you're uncertain which SKU best meets your requirements, click on "help me choose a SKU" for a detailed review of factors like object count, authentication load per hour, backup frequency, and additional features such as forest trust capabilities.
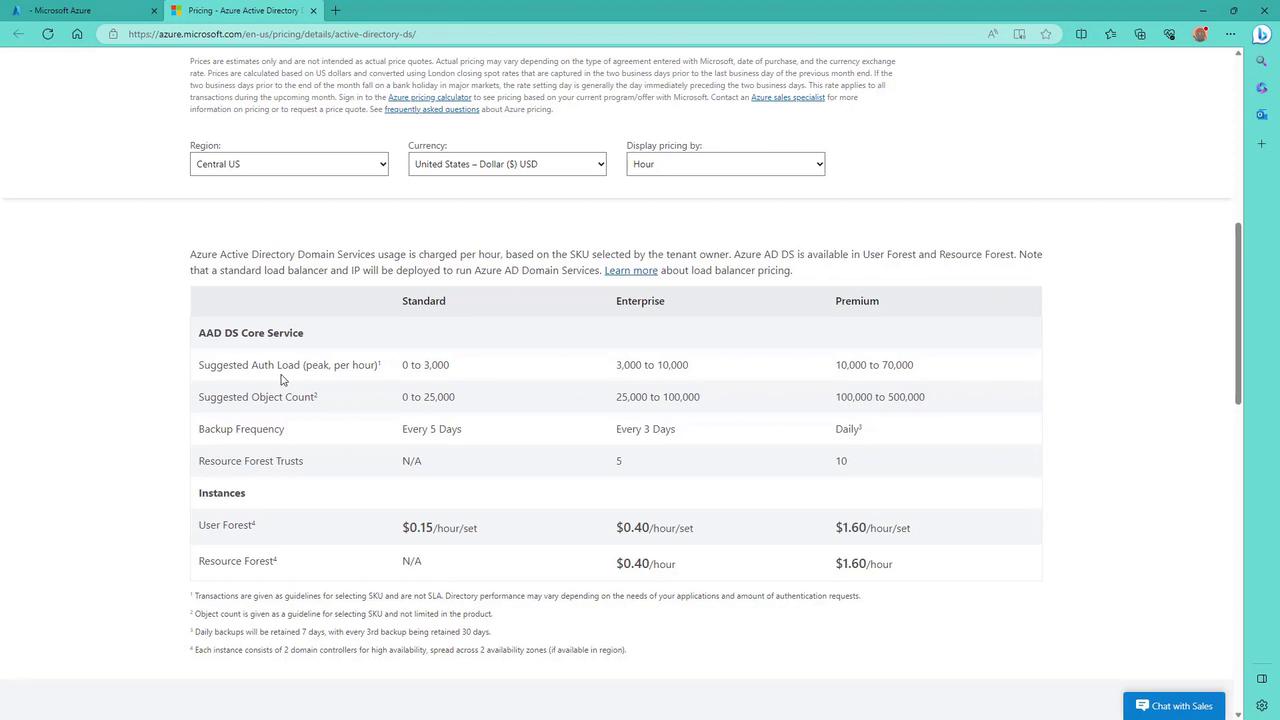
Tip
For a development deployment, the Standard SKU is used. Always analyze your production requirements before choosing a higher SKU level.
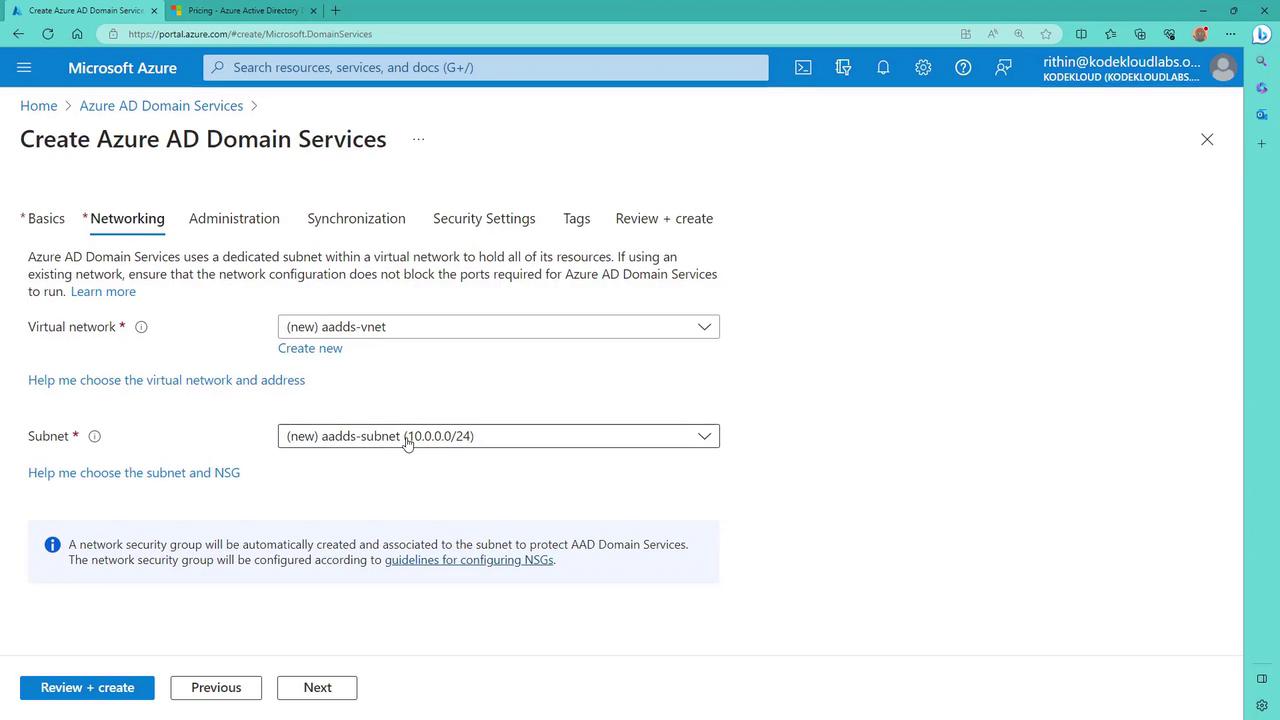
4. Setting Up the Virtual Network
Azure AD Domain Services is deployed into a virtual network. In a new subscription, Azure will automatically propose a virtual network with an address range that avoids conflicts with other networks.
5. Configuring Domain Administration
Manage domain controller administrators by adding users or groups to the Azure AD group named "AADDC administrators." Global administrators can also opt to receive alerts via notifications. To manage permissions, click "manage group membership" and add the required users.
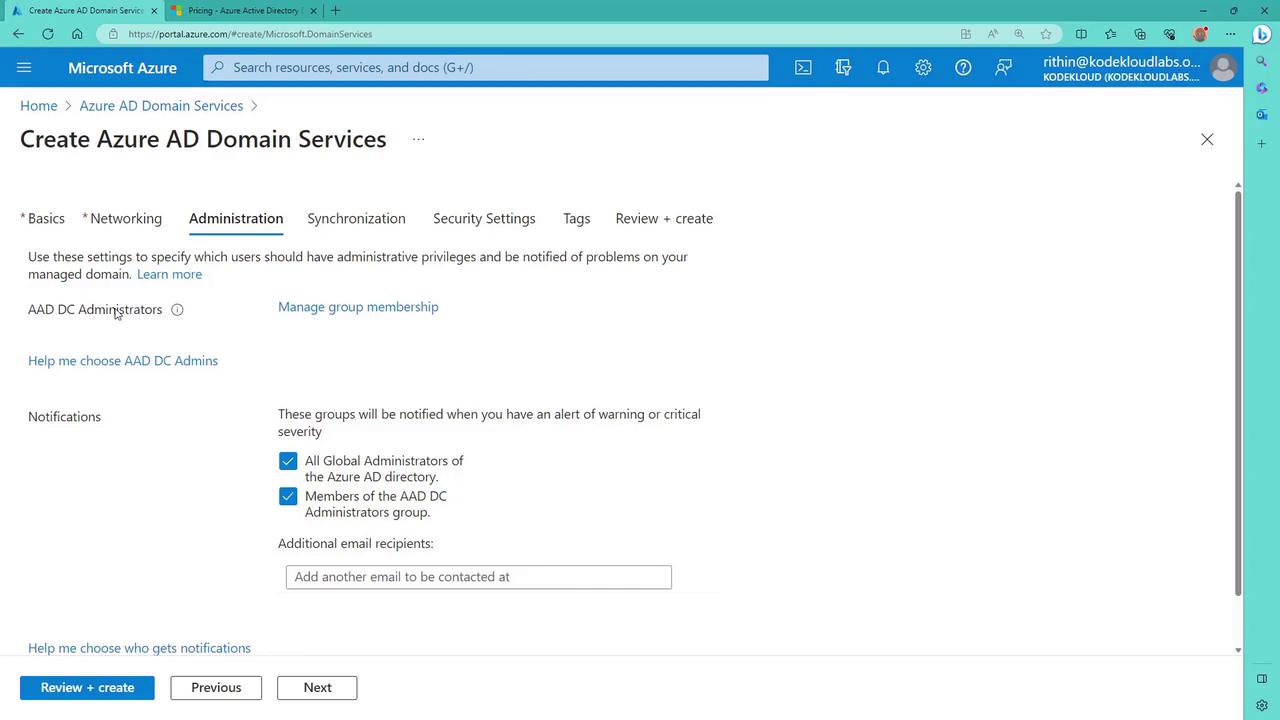
For example, add your name to the group:
6. Configuring Synchronization Settings
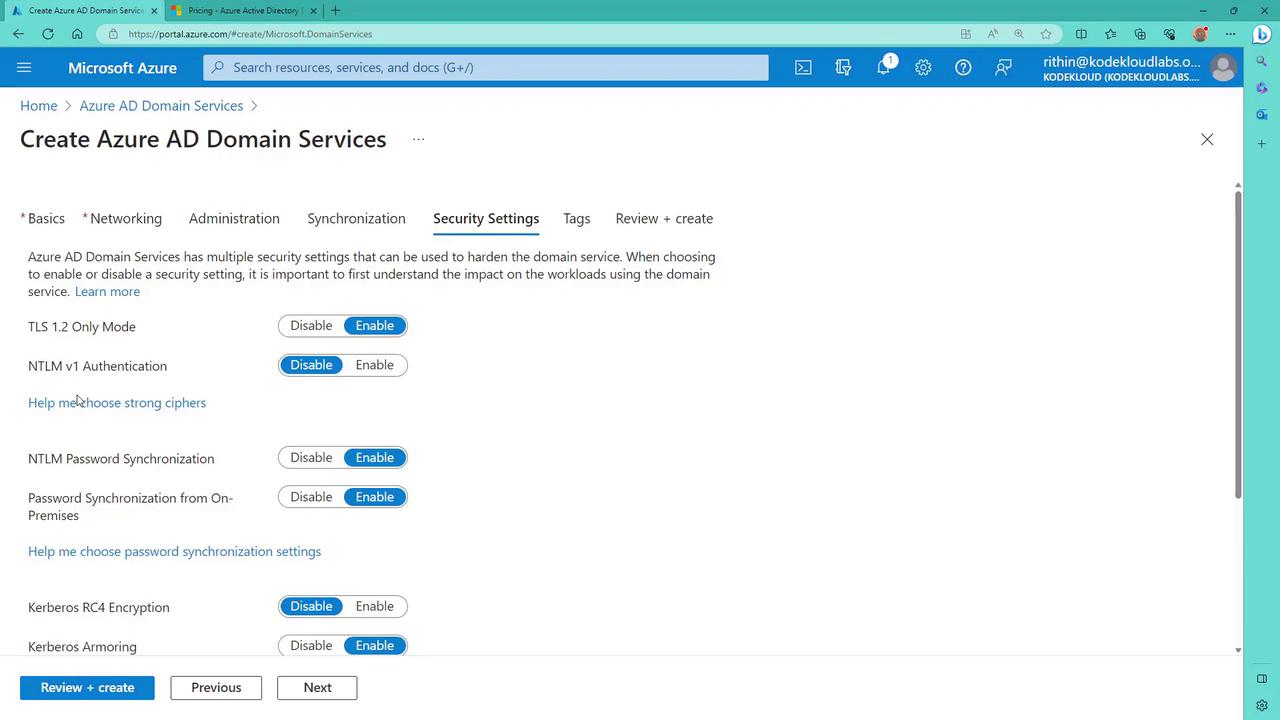
Navigate to the Synchronization tab and select a synchronization type of "all" to ensure that every identity from Azure AD is synchronized. Additional options (such as TLS mode, NTLM v1, password synchronization, Kerberos, and LDAP) are available to meet specific security and operational needs.

7. Reviewing Settings and Finalizing Deployment
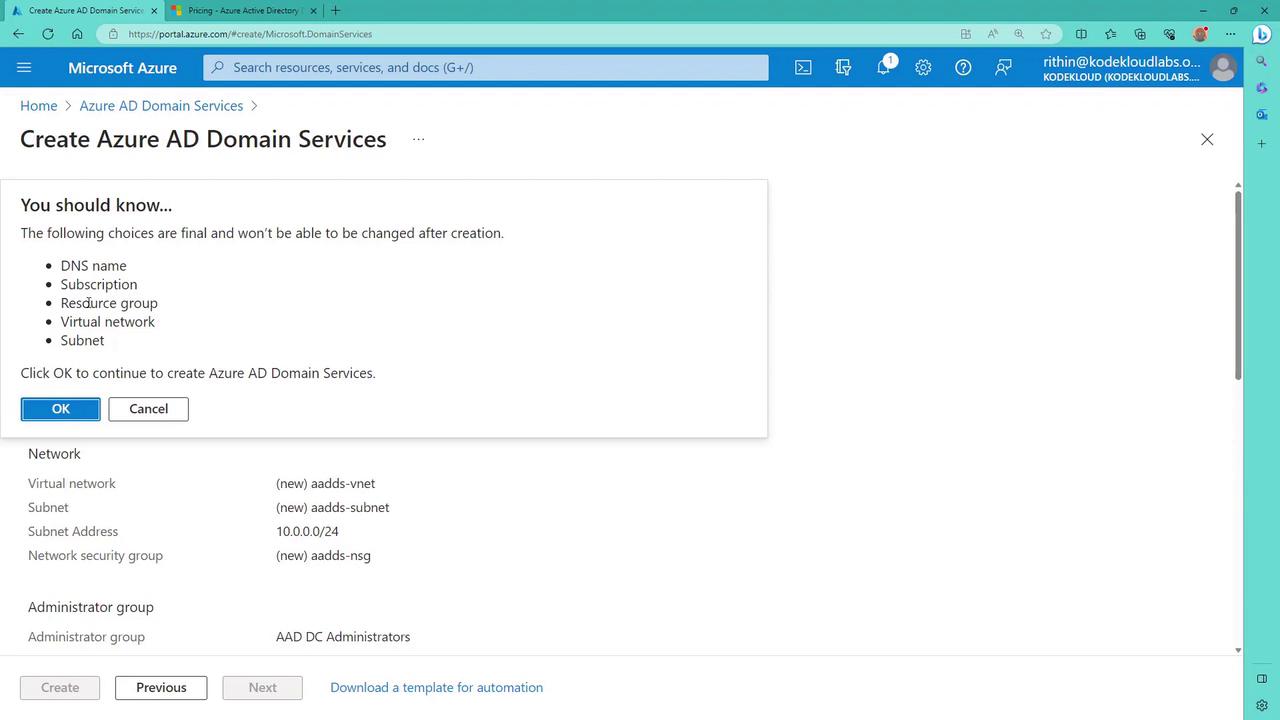
After configuring all settings, click on "Review + Create" and then "Create" once validation passes.
Important
A warning will appear indicating that your configuration choices are final and cannot be modified after deployment. Accept the warning by clicking "OK."
Once confirmed, wait while the service is deployed. During this time, you may review documentation on trust relationships. Note that while full two-way trust is unsupported with Azure AD Domain Services, you can implement a one-way outbound trust (typically with on-premises environments) to enable authentication for users and applications.
8. Preparing a Virtual Machine for Domain Join
While the domain service is deploying, create a virtual machine (VM) that will join the domain. For this demonstration, set up a separate resource group (e.g., “RG workloads”) to host workload VMs. Deploy a Windows Server 2019 Datacenter VM with the necessary credentials, ensuring the RDP port is open for remote access.
After deployment, verify the status of Azure AD Domain Services from the Azure portal.
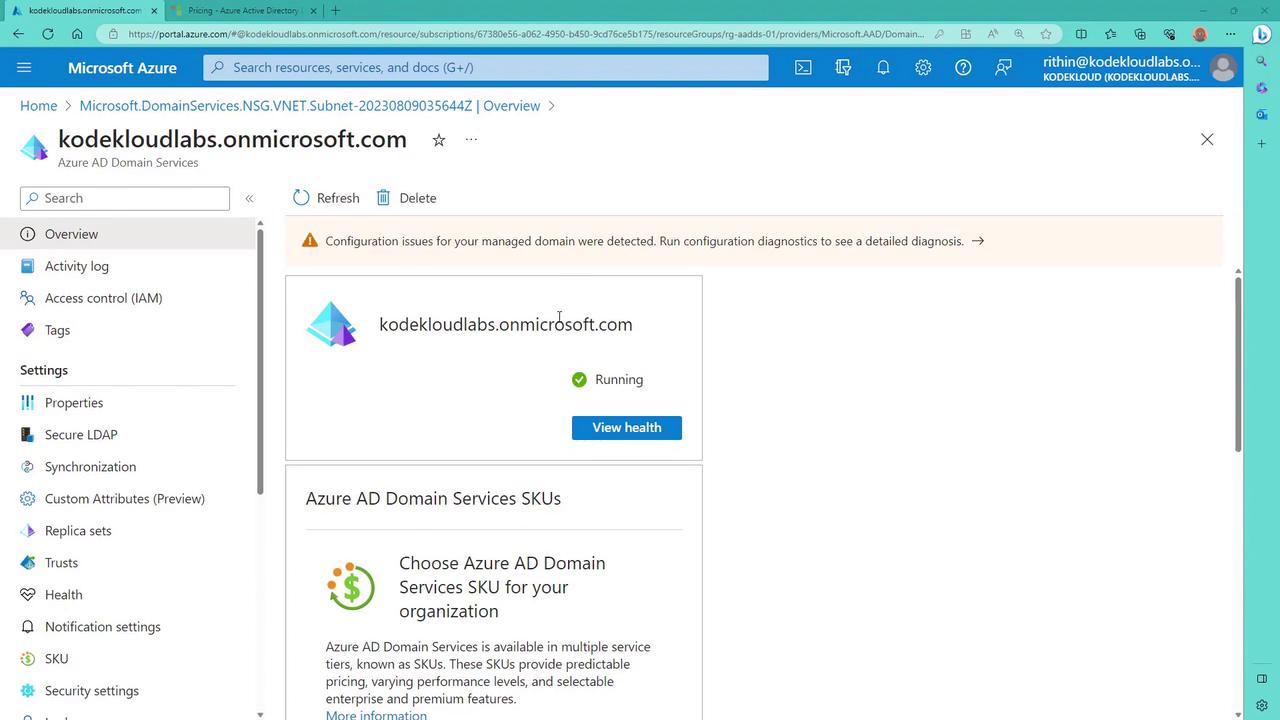
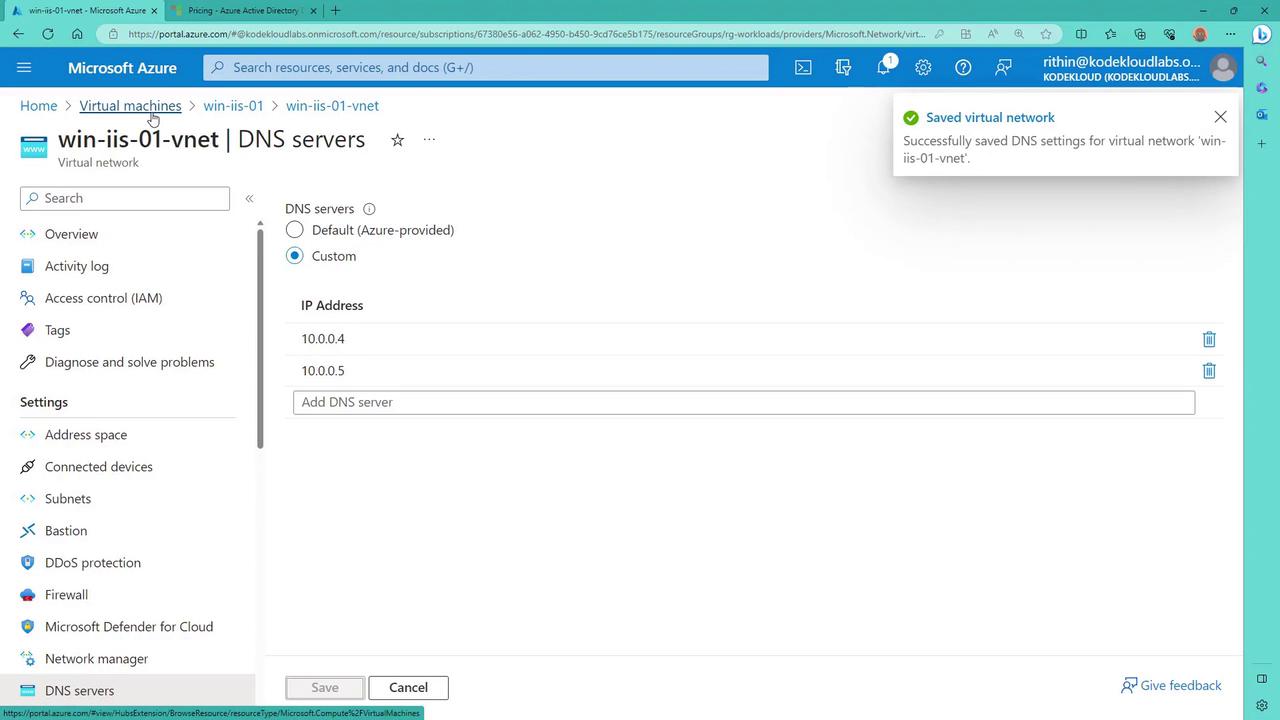
9. Updating DNS Settings on the Virtual Machine
If you encounter a warning regarding DNS records, click on it to review detailed network analysis. This warning indicates that you need to update the virtual network's DNS servers with the domain controllers’ IP addresses to allow domain join operations.
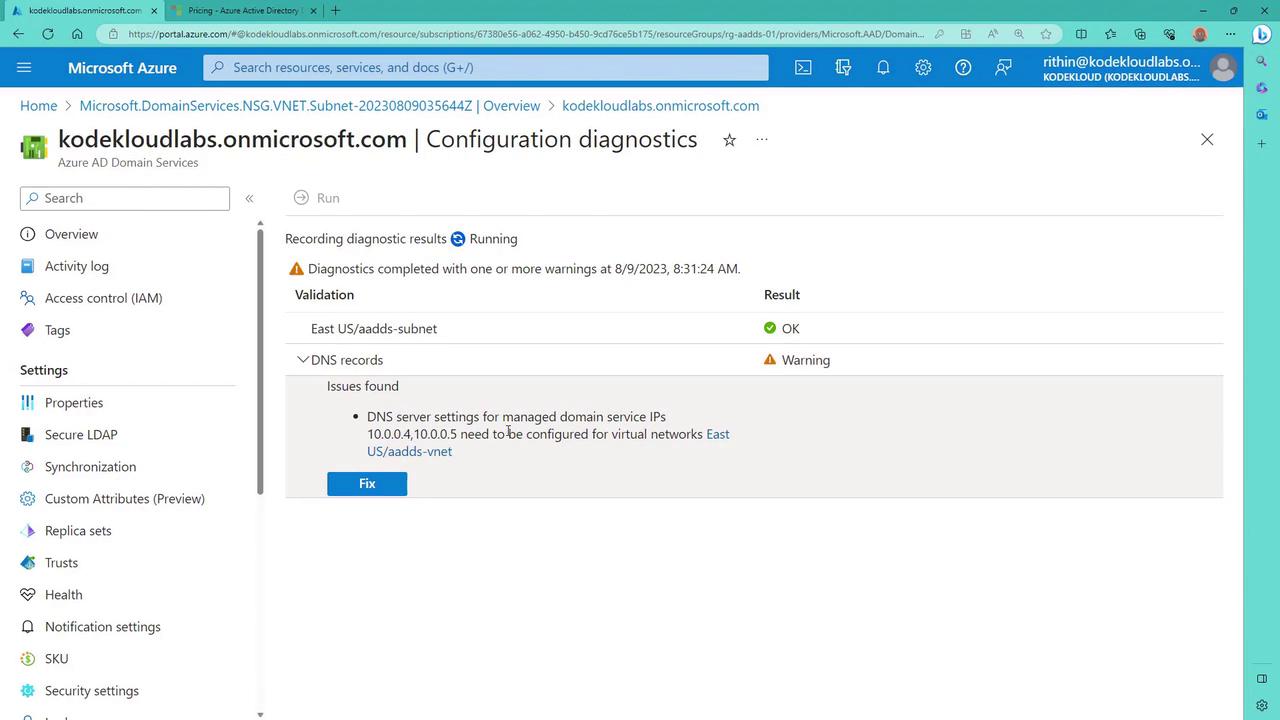
Examine the underlying network configuration via the virtual network diagram. This diagram displays two network interfaces for the domain controllers that must be added as DNS servers.
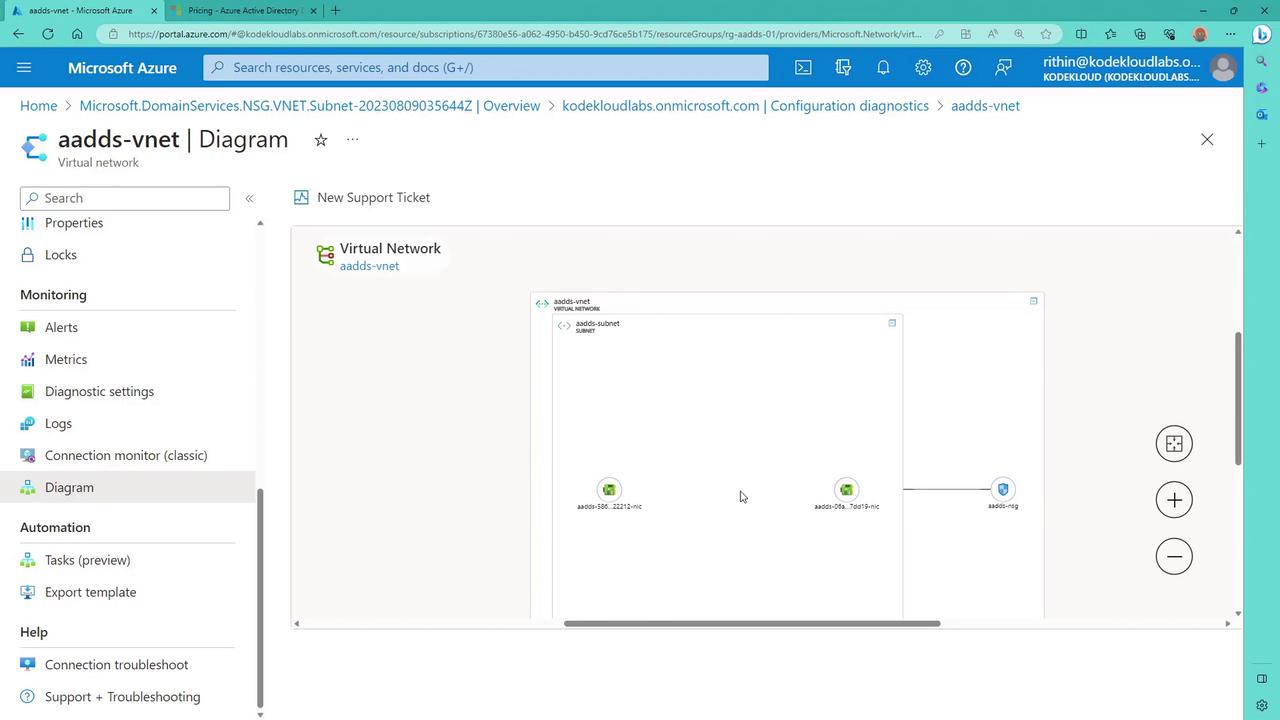
Next, update the DNS settings of your target VM by following these steps:
- Navigate to the VM's Networking settings.
- Change the DNS configuration from Default to "Custom."
- Enter the IP addresses of the domain controllers (or Azure AD Domain Services).
- Save the changes. Note that the VM will restart to apply the updated DNS settings.
After the VM restarts, confirm the updated DNS settings by running the following command in Command Prompt or PowerShell:
PS C:\Users\winuser> ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . : win-iis-01
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : reddog.microsoft.com
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . : reddog.microsoft.com
Description . . . . . . . . . . . : Microsoft Hyper-V Network Adapter
Physical Address. . . . . . . . . : 00-22-48-1F-8C-A9
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::407b:4401:e11:ce%4(Preferred)
IPv4 Address. . . . . . . . . . . : 10.1.0.4(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Wednesday, August 9, 2023 5:34:21 AM
Lease Expires . . . . . . . . . . : Saturday, September 15, 2159 12:08:43 PM
Default Gateway . . . . . . . . . : 10.1.0.1
DHCP Server . . . . . . . . . . . : 168.63.129.16
DHCPv6 IAID . . . . . . . . . . . : 100672072
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-2C-64-65-CA-00-22-48-1F-8C-A9
DNS Servers . . . . . . . . . . . : 10.0.0.4
10.0.0.5
NetBIOS over Tcpip. . . . . . . . . : Enabled
After verifying the updated configuration with tools such as NSLookup or a ping test (e.g., ping 10.0.0.4), proceed to establish connectivity between the networks if needed.
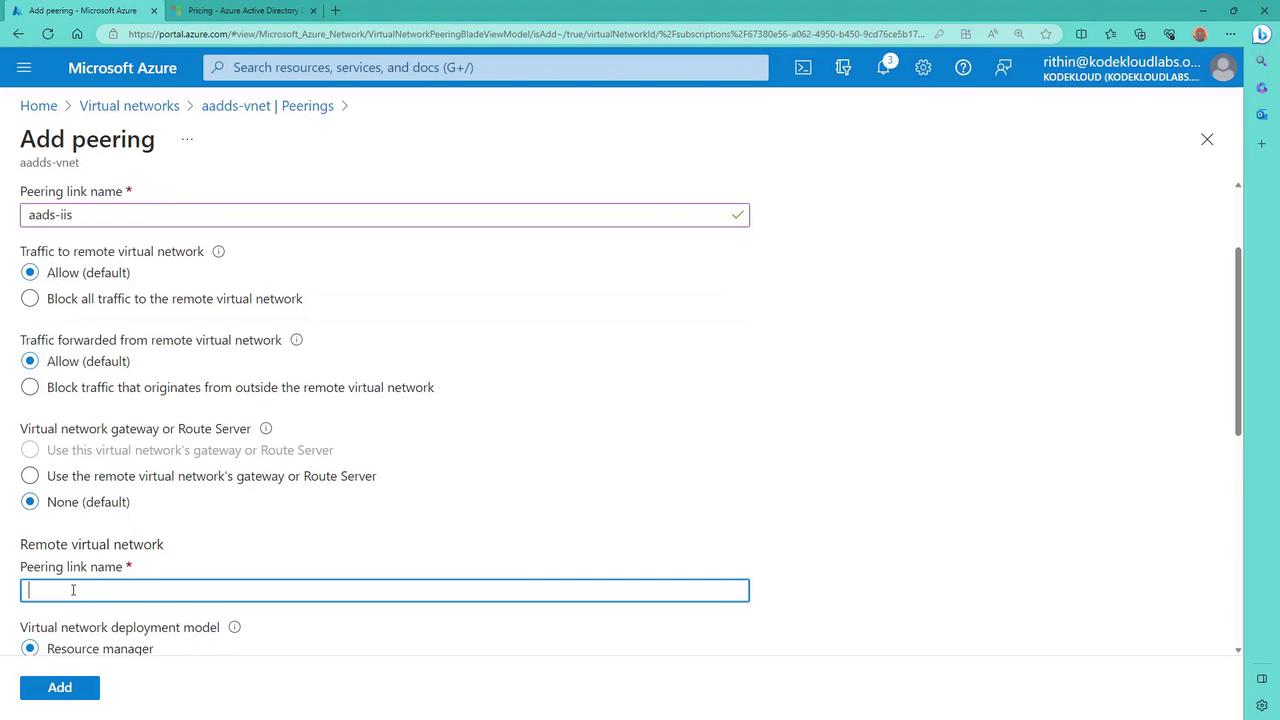
10. Configuring Virtual Network Peering
If the ping test initially shows timeouts, establish connectivity between the virtual network hosting your VM and the virtual network containing Azure AD Domain Services by creating a peering connection:
- Navigate to the virtual network that hosts Azure AD Domain Services.
- Click "Add peering" and configure it (for example, name it "AAD to IAS"), ensuring that inbound and outbound traffic is allowed.
- Select the IaaS network as the remote network and click "Add."
With peering in place, the networks can communicate. Confirm this by running the ping command again:
PS C:\Users\winuser> ping 10.0.0.4
Pinging 10.0.0.4 with 32 bytes of data:
Reply from 10.0.0.4: bytes=32 time=<ms TTL=128
Reply from 10.0.0.4: bytes=32 time=<ms TTL=128
Reply from 10.0.0.4: bytes=32 time=<ms TTL=128
Ping statistics for 10.0.0.4:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 8ms, Average = 3ms
11. Joining the Virtual Machine to the Domain
Once network connectivity is confirmed, join the VM to the domain:
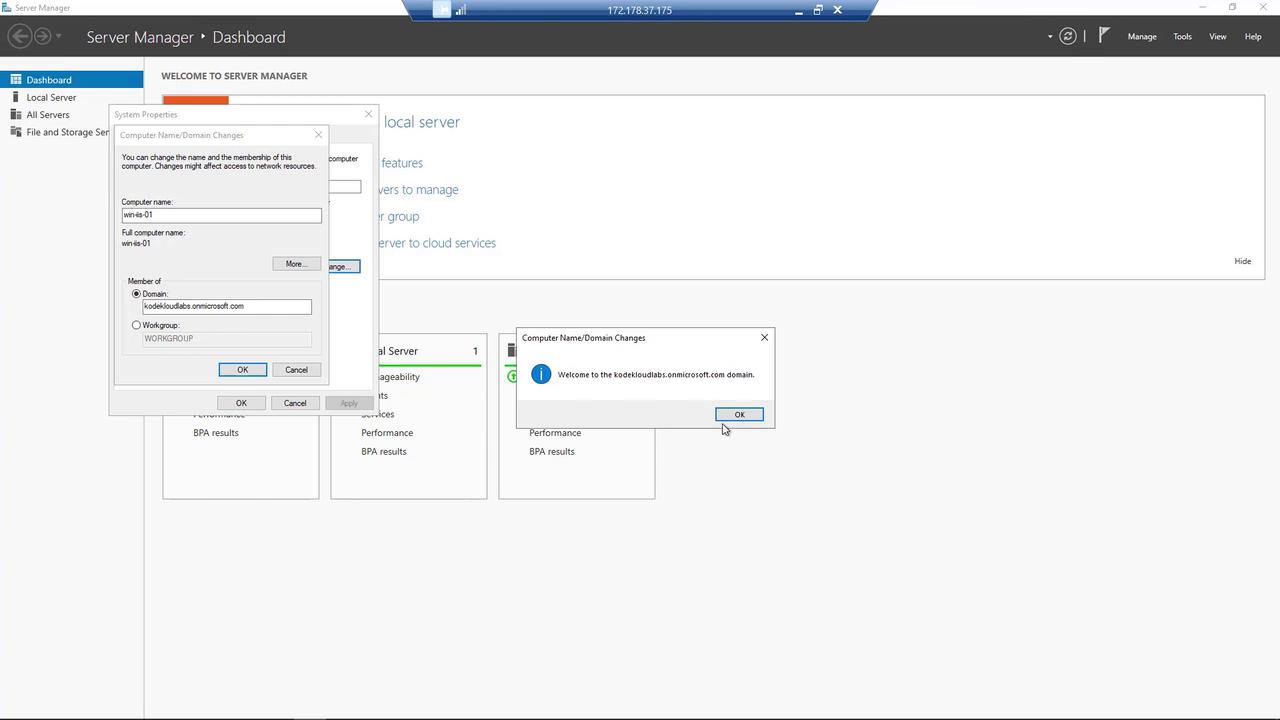
- Open System Properties or use the “Change settings” option in the System control panel.
- Set the computer name to match the domain name provided in the Azure portal.
Password Synchronization
If your domain administrative password hasn’t synchronized yet, you might encounter authentication issues. In such cases, use the self-service password reset (SSPR) portal at https://aka.ms/SSPR to reset your password. Note that synchronization may take 10 to 15 minutes.
After you successfully join the domain, restart the computer to finalize the process.
12. Managing Domain Services with RSAT
After the VM has joined the domain, log in using domain administrator credentials (local accounts will not display Active Directory objects). Install the Remote Server Administration Tools (RSAT) to manage Active Directory Domain Services:
- Open Server Manager.
- Add roles and features.
- Include the RSAT tools such as DNS Server Tools.
Once RSAT is installed, open the Active Directory Administrative Center to view and manage domain objects such as users and groups.
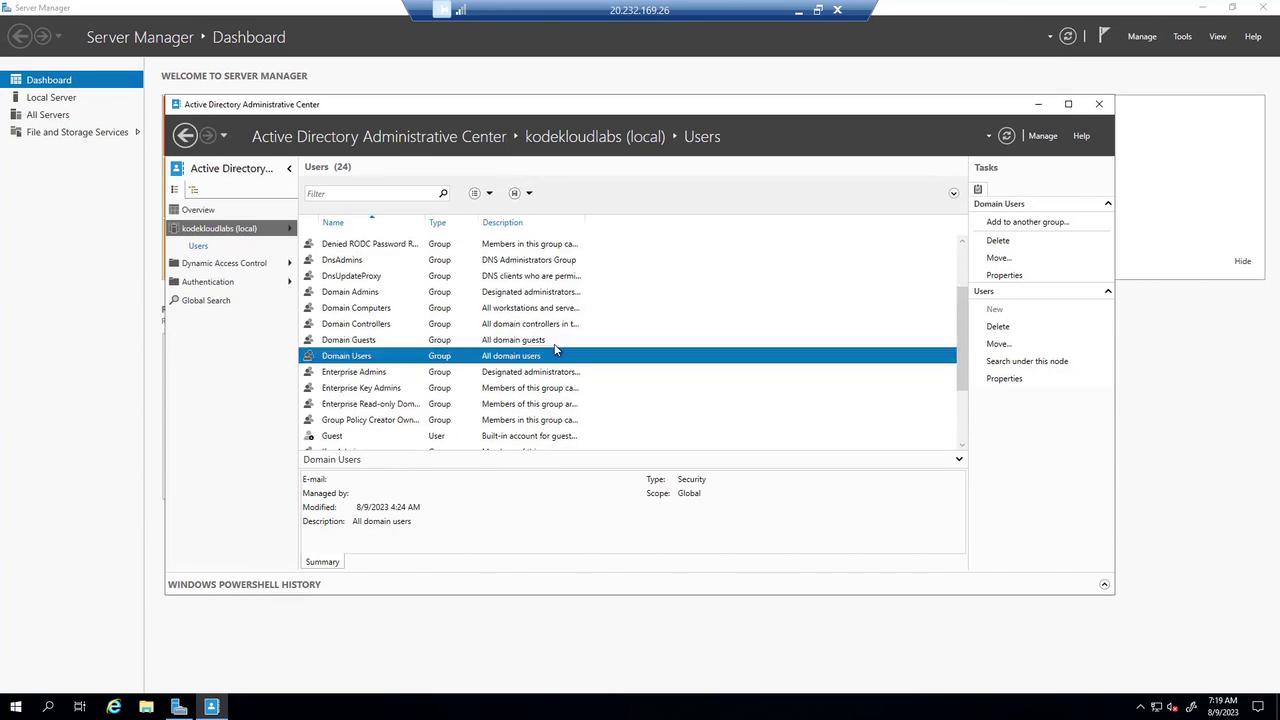
Additionally, use DNS Manager to monitor your forward lookup zones and manage DNS records for your domain, ensuring that both the IIS server and management VM (which are domain-joined) are operating correctly.
Conclusion
This guide demonstrated how to deploy Azure AD Domain Services using the Azure portal, configure virtual networks with peering, join a Windows Server VM to the domain, and manage Active Directory objects with RSAT. While Azure AD Domain Services offers many on-premises-like features, be aware that some advanced configurations and trust relationships have limitations.
Thank you for reading this comprehensive walkthrough on deploying Azure AD Domain Services. For additional information, refer to the official Azure Documentation.
Watch Video
Watch video content