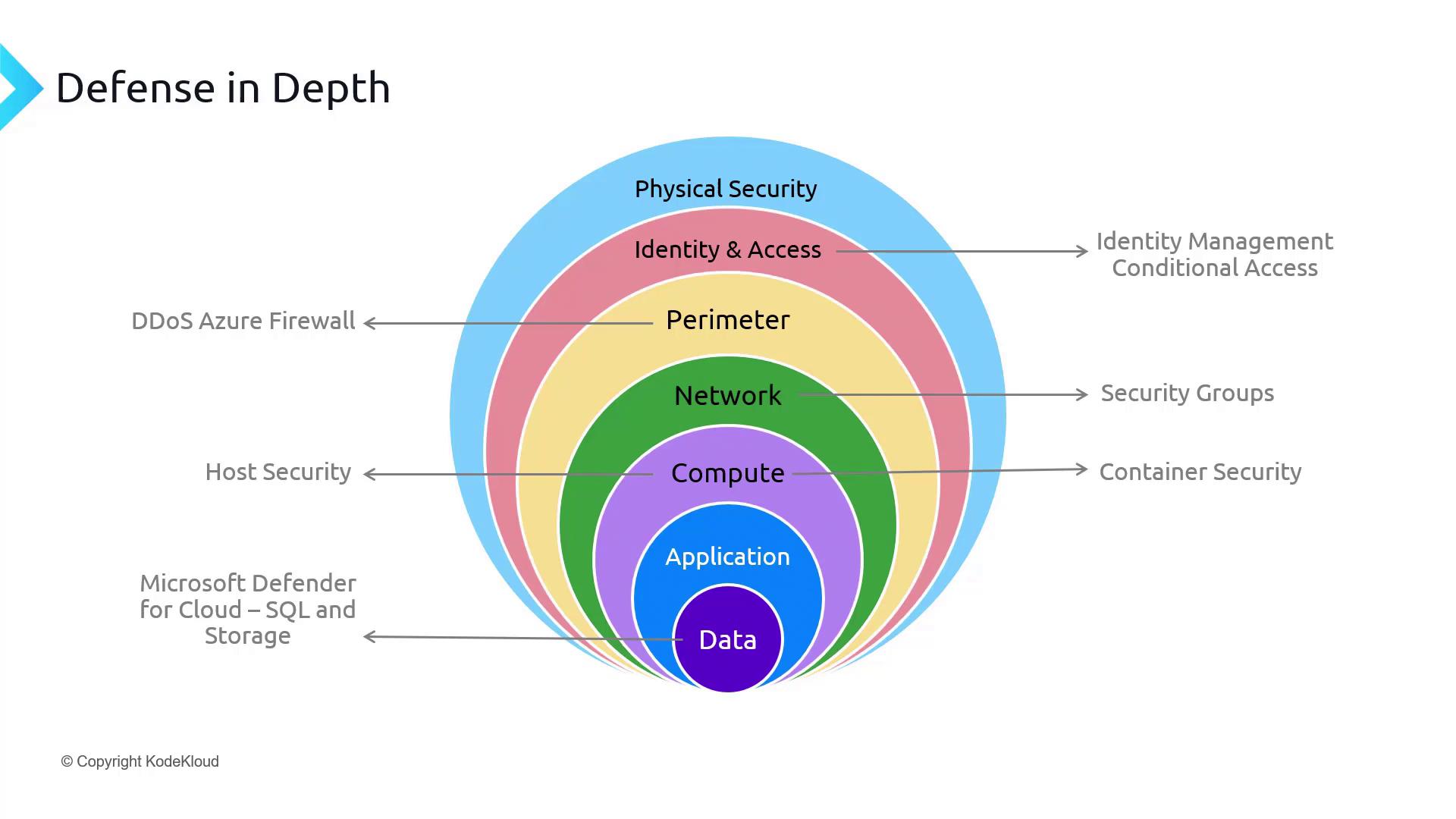
Securing the Core: Data
Data is the central element of any robust security posture. This section details effective methods to protect data stored in Azure Storage and Azure SQL services. By implementing these security practices, you can ensure that your data remains secure at all times.Key Topics in Storage Security
The following topics outline our approach to ensuring storage security:- Defining Data Sovereignty: Understand the legal and regulatory implications of data location.
- Configuring Azure Storage Access: Follow best practices to securely manage access to your storage solutions.
- Deploying Shared Access Signatures (SAS): Use time-bound tokens to control and limit access to your resources.
- Managing Azure AD Storage Authentication: Enhance security by leveraging Azure Active Directory for authenticating storage access.
- Implementing Storage Service Encryption: Protect your data at rest by ensuring full encryption.
- Configuring Blob Data Retention Policies: Manage the lifecycle of your blob data through customized retention strategies.
- Configuring Azure File Authentication: Secure your file shares by enforcing robust authentication methods.
- Enabling the Secure Transfer Required Property: Force encrypted data transfers to safeguard your data in transit.
For additional insights on Azure security best practices, visit the Azure Security Documentation.