Traditional vs. Modern Build Processes
Historically, deploying an application involved writing code, compiling it into a binary (for example, a Java JAR file), and then running that binary on the target system. Over time, developers began using Dockerfiles to build container images and deploy containers. Despite the surge in popularity of container images, there is still a strong need for a build process that generates conventional artifacts. The custom image builder fulfills this need by integrating build process logic into a minimal base image.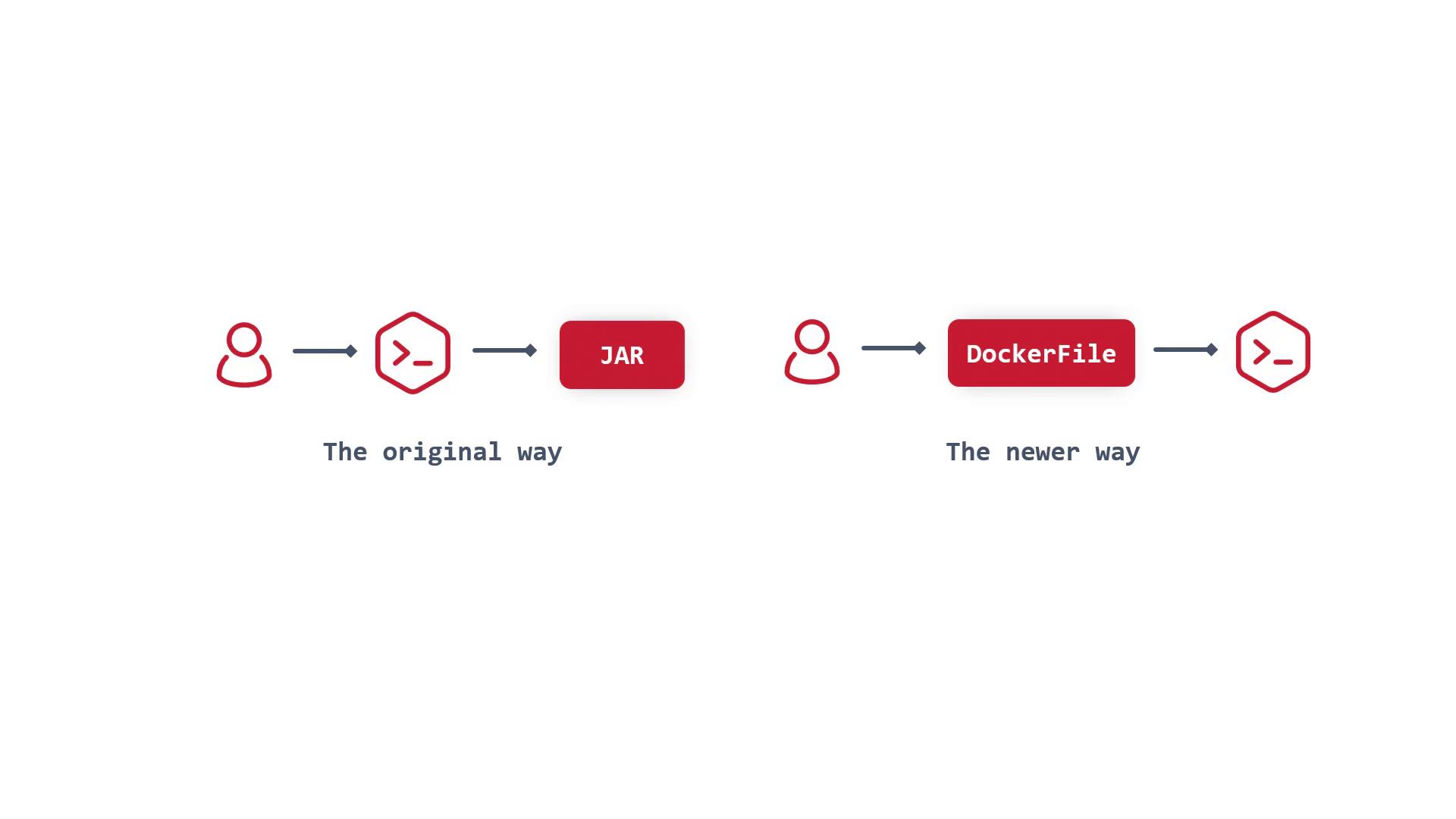
Key Components of the Custom Builder
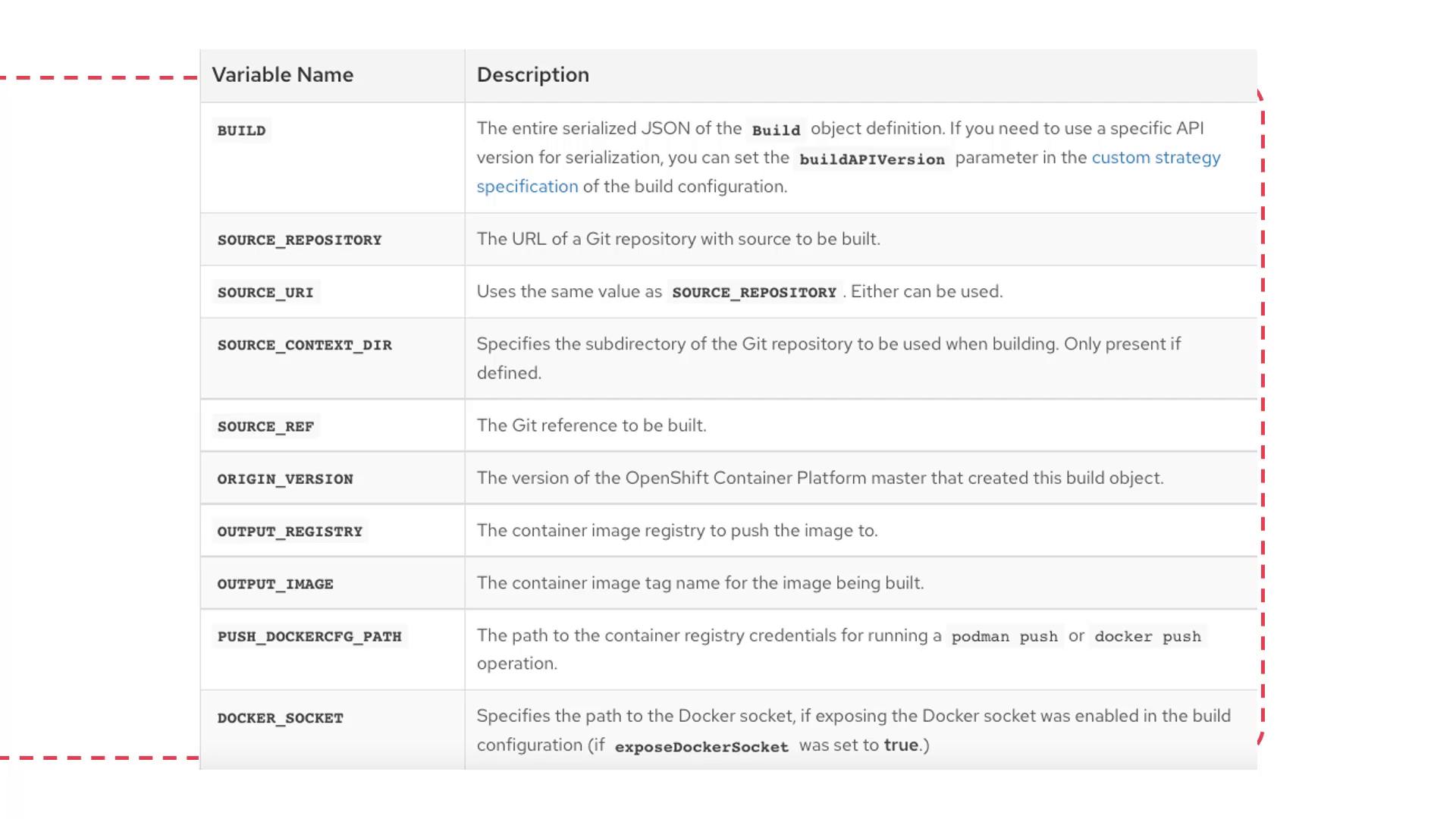
Even when using a pre-built container image, several runtime components are necessary to ensure a successful build process:- The build process logic itself.
- The source repository containing the application code.
- The specific directory within the repository where the build should execute.
- The source reference (branch, tag, or commit).
- The target version of OpenShift upon which the build is based.
- The output destination where the resulting container image will be deployed.
- The designated image name or tag.
- Any credentials needed to interact with the container registry.
- Access to the Docker socket for the runtime environment.
Specifying the correct directory and configuration parameters ensures that your build process targets the correct code segment and produces the desired artifacts.
Integrating with CI/CD Pipelines
The custom builder image consolidates all these parameters into one cohesive process. This integration not only simplifies the generation of build artifacts but also makes it easy to incorporate into larger CI/CD pipelines. The result is an automated and efficient build and deployment process tailored for modern development workflows.