OpenShift 4
Openshift Security
SCC Overview
Security in the Kubernetes ecosystem is often overlooked, even though it plays a crucial role in maintaining a reliable and secure environment. In many organizations, a significant disparity exists between the number of developers and dedicated security engineers. In some cases, there may not even be a dedicated security team at all.
A recent Red Hat State of Kubernetes and Container Security report revealed that nearly 70% of security issues are caused by misconfigurations, while 27% stem from runtime security incidents. These alarming statistics highlight the critical need to address security challenges effectively.
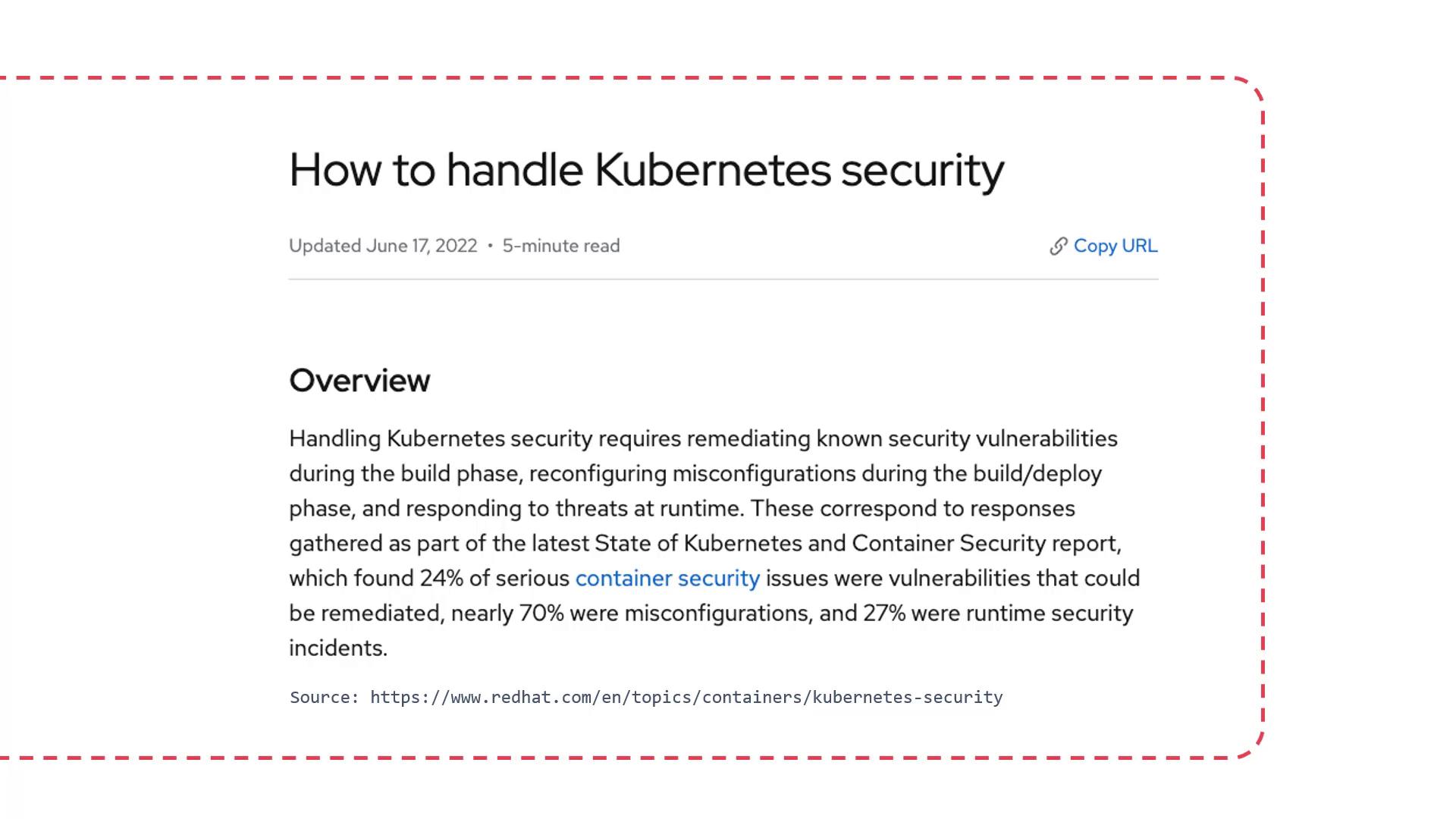
What are Security Context Constraints (SCC)?
Security Context Constraints (SCC) provide a robust mechanism for controlling pod permissions. Think of SCC as the access control system for pods—it defines what a pod is allowed to do, which resources it can access, and its overall security credentials. While Role-Based Access Control (RBAC) manages user permissions, SCC focuses on system-level security, including integrations with third-party applications. Moreover, SCC leverages native Linux capabilities, such as SELinux, enabling you to apply familiar policies directly to your pods.

Key Information
SCC not only enhances security by limiting pod actions but also complements other controls like RBAC and network policies, creating a layered defense strategy.
SCC vs. Network Policy
Both SCC and network policies are vital for Kubernetes security, yet they focus on different aspects:
Network Policies: These are designed to manage inbound and outbound traffic at the network level, considering factors like IP addresses, ports, and the OSI model. Their primary focus is regulating communication between pods and external entities.
Security Context Constraints (SCC): These govern privileges and access control from an application and system perspective. SCC ensures that a pod operates within defined restrictions regarding system-level permissions and resources.
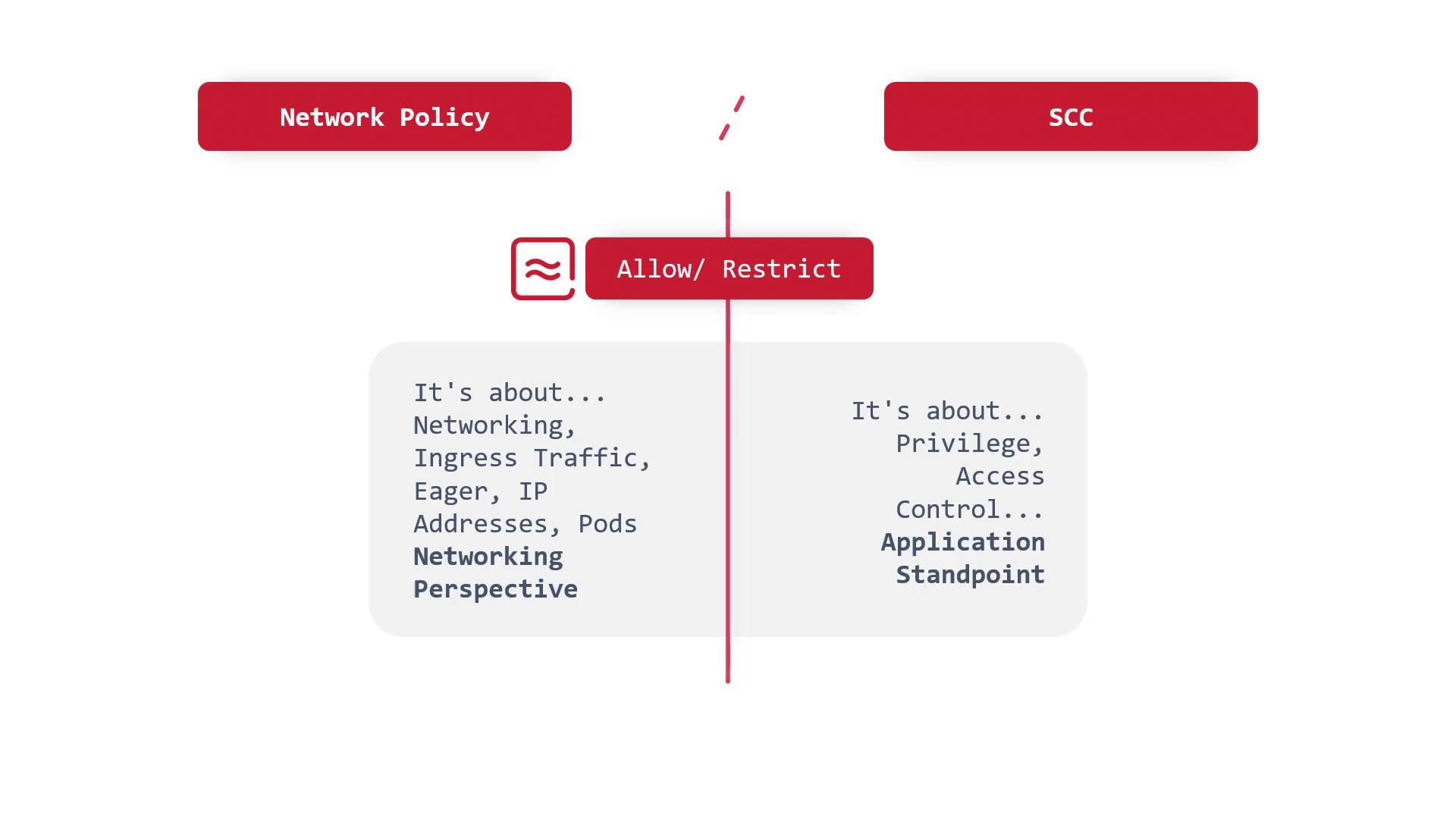
Both tools work in tandem to enforce robust security policies, ensuring that pods adhere to their minimum required permissions.
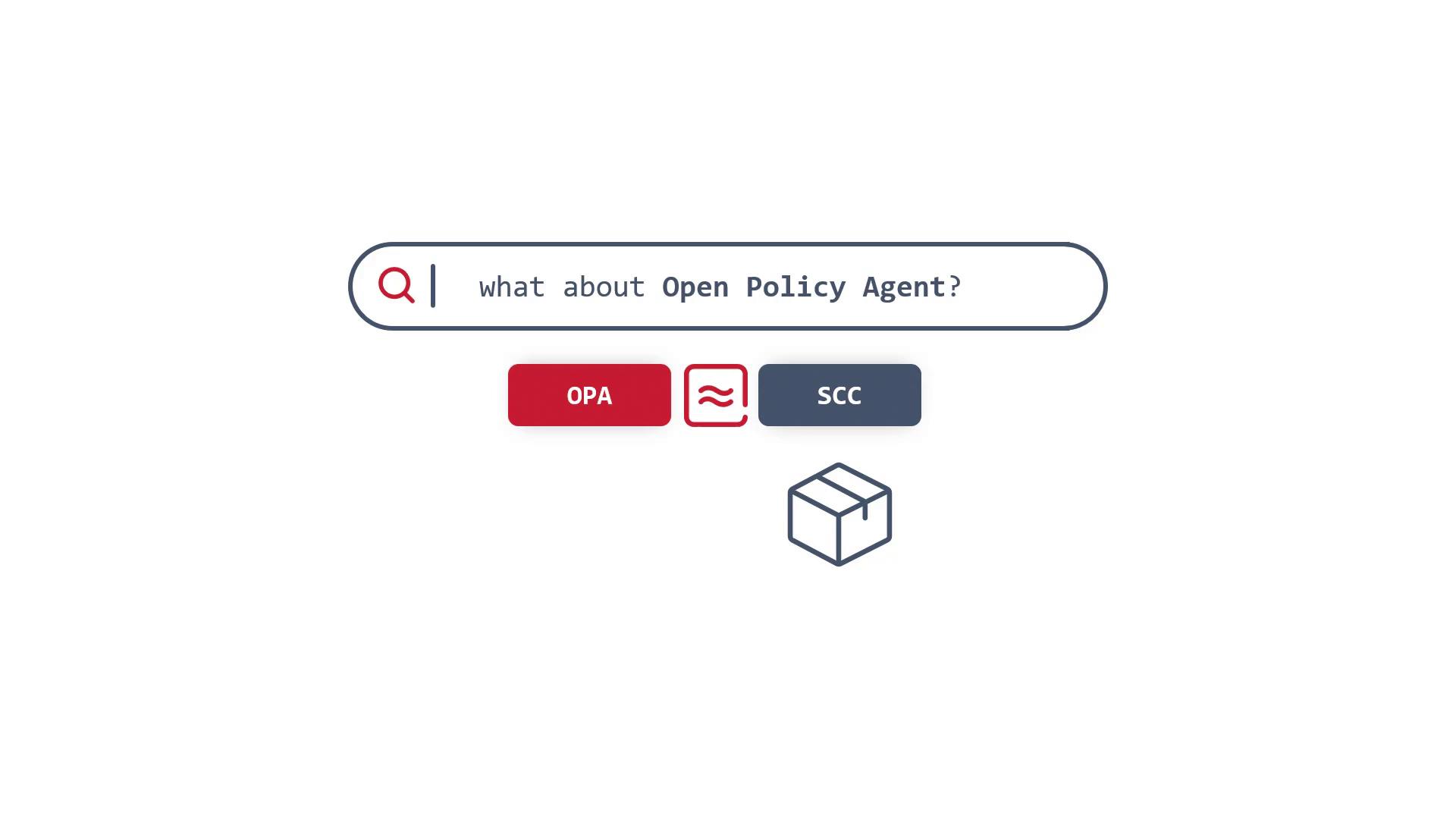
SCC and Open Policy Agent (OPA)
Although SCC is integrated into the Kubernetes system, there are similar tools such as Open Policy Agent (OPA) that extend security capabilities. OPA allows for advanced policy enforcement, but SCC serves as a strong first layer of defense, establishing fundamental access controls and aiding in early identification of security vulnerabilities.
Leveraging Linux Native Security Features
One practical approach to enhancing security is by using Linux native features such as AppArmor—a security module within the Linux kernel. AppArmor helps in restricting container access to resources by controlling file permissions and network access for specific applications. Note that AppArmor is specific to Linux environments, and its implementation may vary on Windows worker nodes.
Practical Examples of Security Context in Kubernetes
The OWASP Top 10 for Kubernetes project, building on insights from reports like Red Hat’s, emphasizes the importance of setting secure contexts for workloads. Defined security contexts help establish a strong security posture by ensuring that containers operate with the minimum required privileges.
Below are consolidated examples of applying security contexts using YAML:
Example 1: Setting Run-As User and Group
This example demonstrates how to configure a pod’s security context by assigning specific user and group IDs:
apiVersion: v1
kind: Pod
metadata:
name: root-user
spec:
containers:
- name: example-container
image: example-image
securityContext:
runAsUser: 0 # Run as root user
runAsGroup: 5554 # Set a specific group for non-root operations
Example 2: Configuring a Read-Only Filesystem
Enforcing a read-only filesystem is a common security measure that prevents modifications to the container’s root filesystem:
apiVersion: v1
kind: Pod
metadata:
name: read-only-fs
spec:
containers:
- name: readonly-container
image: example-image
securityContext:
readOnlyRootFilesystem: true # Define the root filesystem as read-only
Example 3: Managing Privileged Containers
For containers that require elevated privileges, it’s essential to clearly define security policies. The example below shows how to enable privileged mode:
apiVersion: v1
kind: Pod
metadata:
name: privileged-pod
spec:
containers:
- name: privileged-container
image: example-image
securityContext:
privileged: true # Grant privileged access
# To restrict privileges, you would set:
# privileged: false
Demo: Putting Security Contexts into Action
The following examples demonstrate practical implementations of security contexts, focusing on a read-only filesystem and privileged mode settings.
apiVersion: v1
kind: Pod
metadata:
name: demo-read-only-fs
spec:
containers:
- name: demo-container
image: example-image
securityContext:
readOnlyRootFilesystem: true
apiVersion: v1
kind: Pod
metadata:
name: demo-privileged-pod
spec:
containers:
- name: demo-container
image: example-image
securityContext:
privileged: true # Container runs with elevated privileges
These examples underscore the importance of defining clear and precise security contexts to mitigate vulnerabilities and ensure that Kubernetes workloads operate with the minimum necessary permissions.
By combining SCC with network policies and native Linux security features, you can build a robust security framework, significantly strengthening your Kubernetes environment.
For further reading, visit Kubernetes Documentation or explore more about Linux Security Modules.
Watch Video
Watch video content