[Updated] AZ-104: Microsoft Azure Administrator
Administer Governance and Compliance
Azure Resource Locks
Imagine working late while deploying updates to your Azure environment. A single moment of distraction could lead to running a script without a proper double-check, causing your crucial DNS domain to be deleted. Azure Resource Locks act as a safeguard, preventing accidental modifications or deletions and ensuring that a small mistake doesn’t result in irreversible damage.
In this article, we explore how resource locks protect your Azure environment from unintentional changes.
What Are Resource Locks?
Resource locks are a critical feature designed to protect your Azure resources from unintended modifications. Think of them as a safety cover on a switch—ensuring that nothing is toggled accidentally. When enabled, these locks keep your resources unchanged during routine maintenance or while scripts are running.
Azure allows you to apply locks at various scopes:
- Subscription
- Resource Group
- Individual Resource
Once a lock is applied at a particular scope, it is automatically inherited by all underlying resources. For instance, applying a lock at the resource group level means every resource within that group is protected.
Types of Resource Locks
Azure provides two primary types of resource locks:
Read-Only Locks
A read-only lock lets you view a resource without modifying or deleting it, much like placing valuable items in a display case—you can admire them but not alter them.Delete Locks
A delete lock allows modifications but prevents the complete removal of a resource. This is akin to writing with a pencil that does not have an eraser—you can adjust details, but the resource itself remains undeletable.
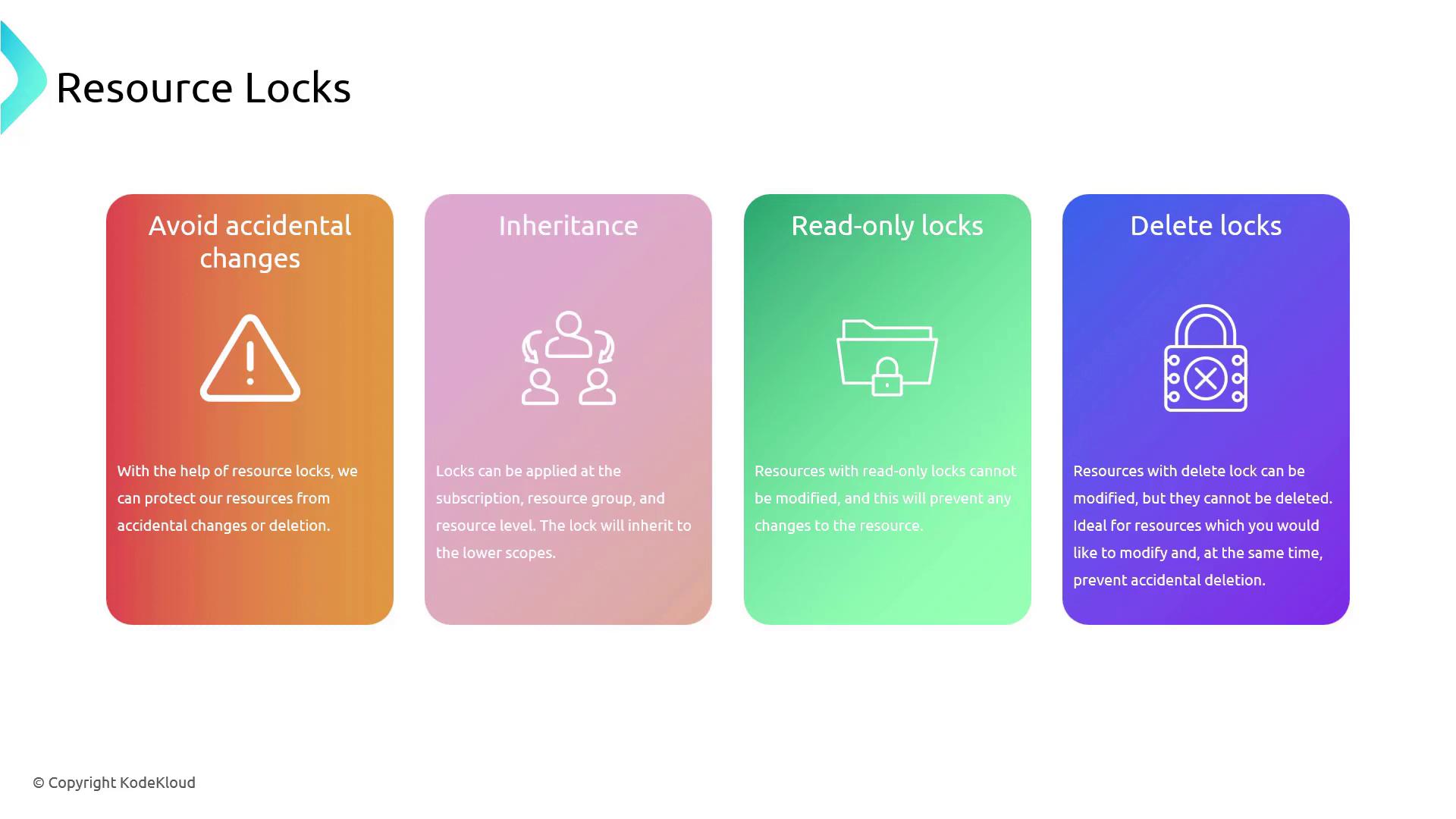
The following infographic illustrates the benefits of Azure Resource Locks, highlighting the prevention of accidental changes, inheritance across resources, and the flexibility to operate in both read-only and delete modes.
Implementing Resource Locks in the Azure Portal
Follow these steps to implement resource locks using the Azure portal:
Navigate to the Resource Groups Section
Open the Azure portal and locate the Resource Group that contains the resource you wish to protect. For example, select a Resource Group that holds an automation account.Select the Resource
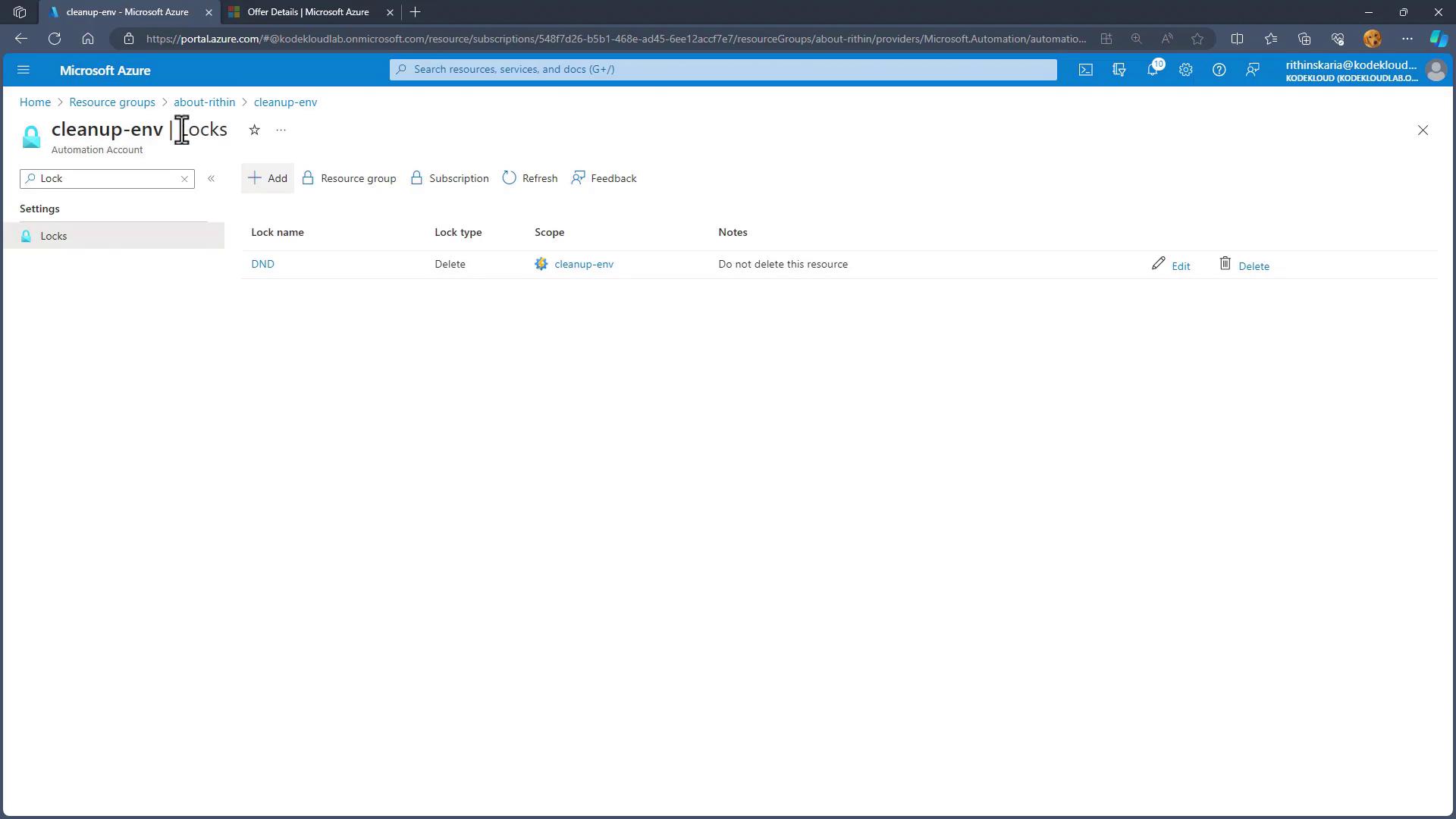
Within your chosen Resource Group, open the automation account. In the left-hand menu, click on the "Locks" option.Add a Delete Lock
- Click on Add lock.
- Provide a name (e.g., "DND" for "Do Not Delete").
- Set the lock type to Delete.
- Optionally, add a note for other users.
- Click Save.
After saving, the delete lock becomes active. If you navigate back to the Overview blade for the resource and attempt to delete it, an error message will confirm that deletion is blocked due to the active lock.
Even though the delete lock stops resource removal, you can still modify aspects of the resource. For instance, you can update runbooks within the automation account without any issues.
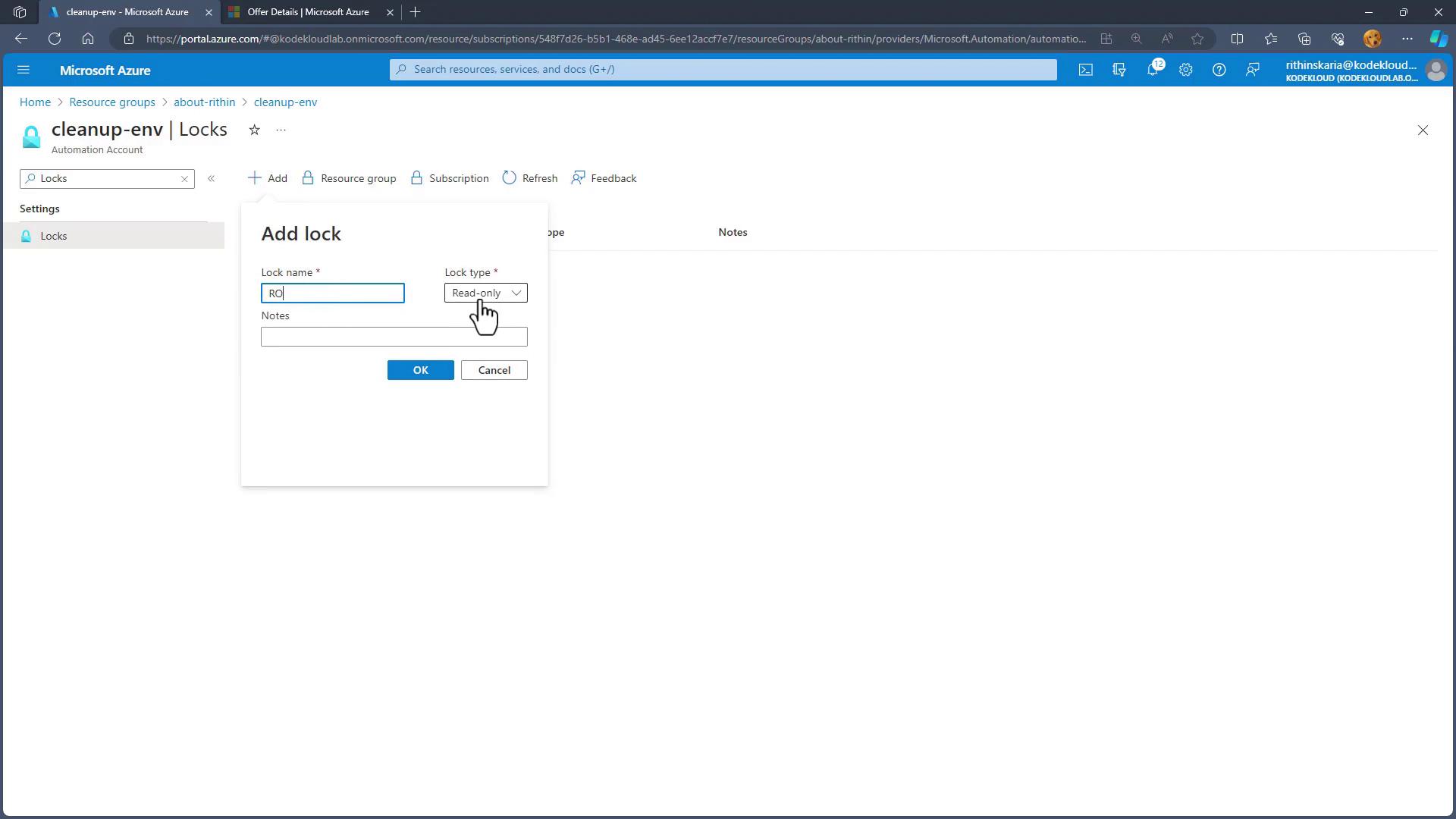
- Switching to a Read-Only Lock
- Return to the "Locks" section in the automation account.
- Remove the existing delete lock.
- Add a new lock, setting the type to Read-only.
- Name it "RO" and include any notes or descriptions.
- Click Save.
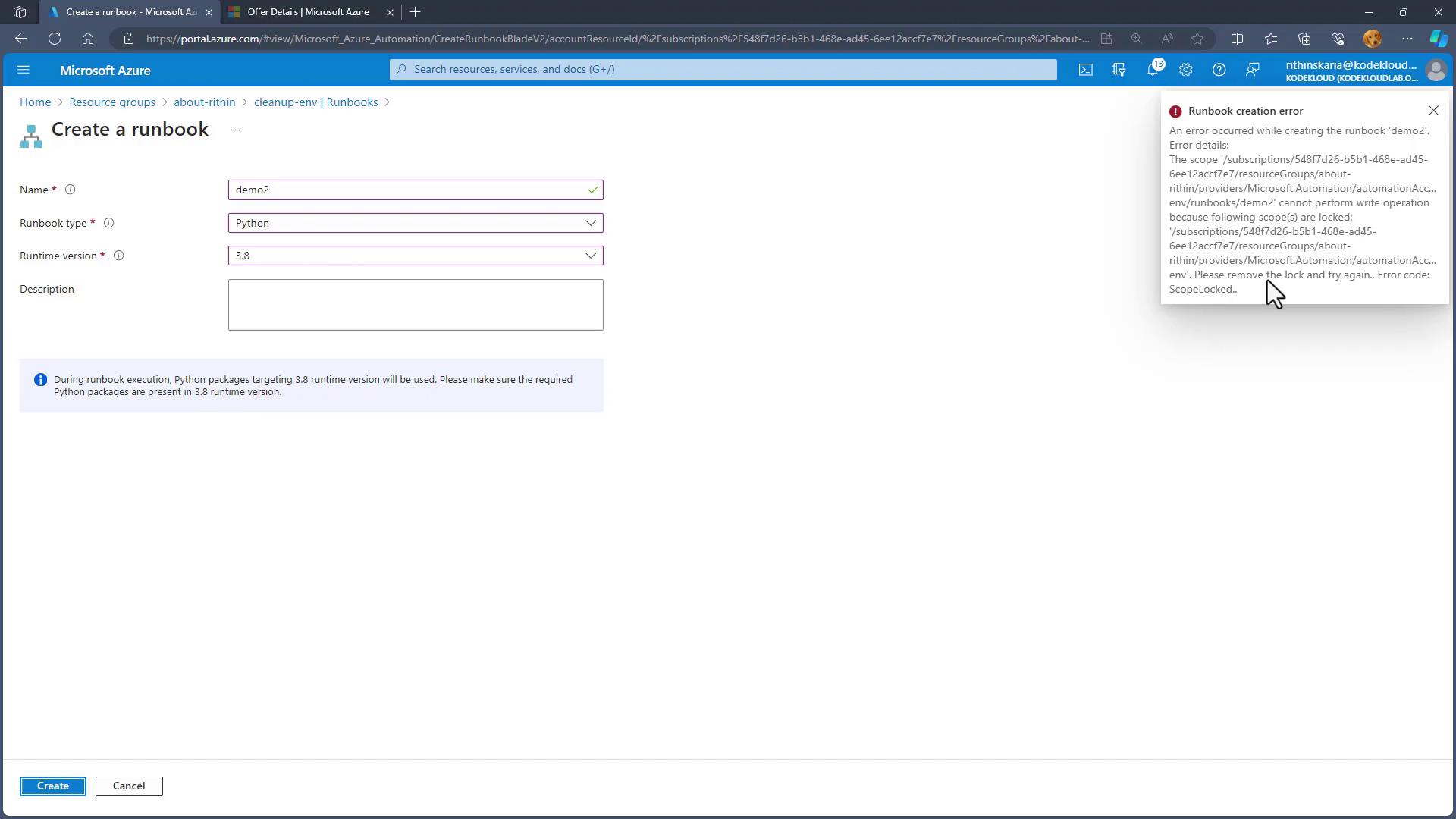
With the read-only lock in place, attempts to create a new resource—such as a Python runbook (version 3.8) named "demo2"—will result in an error message indicating that the scope is locked. This clearly demonstrates the difference in behavior between a read-only lock and a delete lock.
Applying Locks at the Resource Group Level
From the Resource Groups view, you can inspect any locks applied at that level. The locking mechanism works similarly at the subscription level, where every resource within the subscription inherits the lock.
To further enhance protection, you can add an additional lock at the resource group level. For instance, add a delete lock named "RG lock" (or any custom name) to the Resource Group.
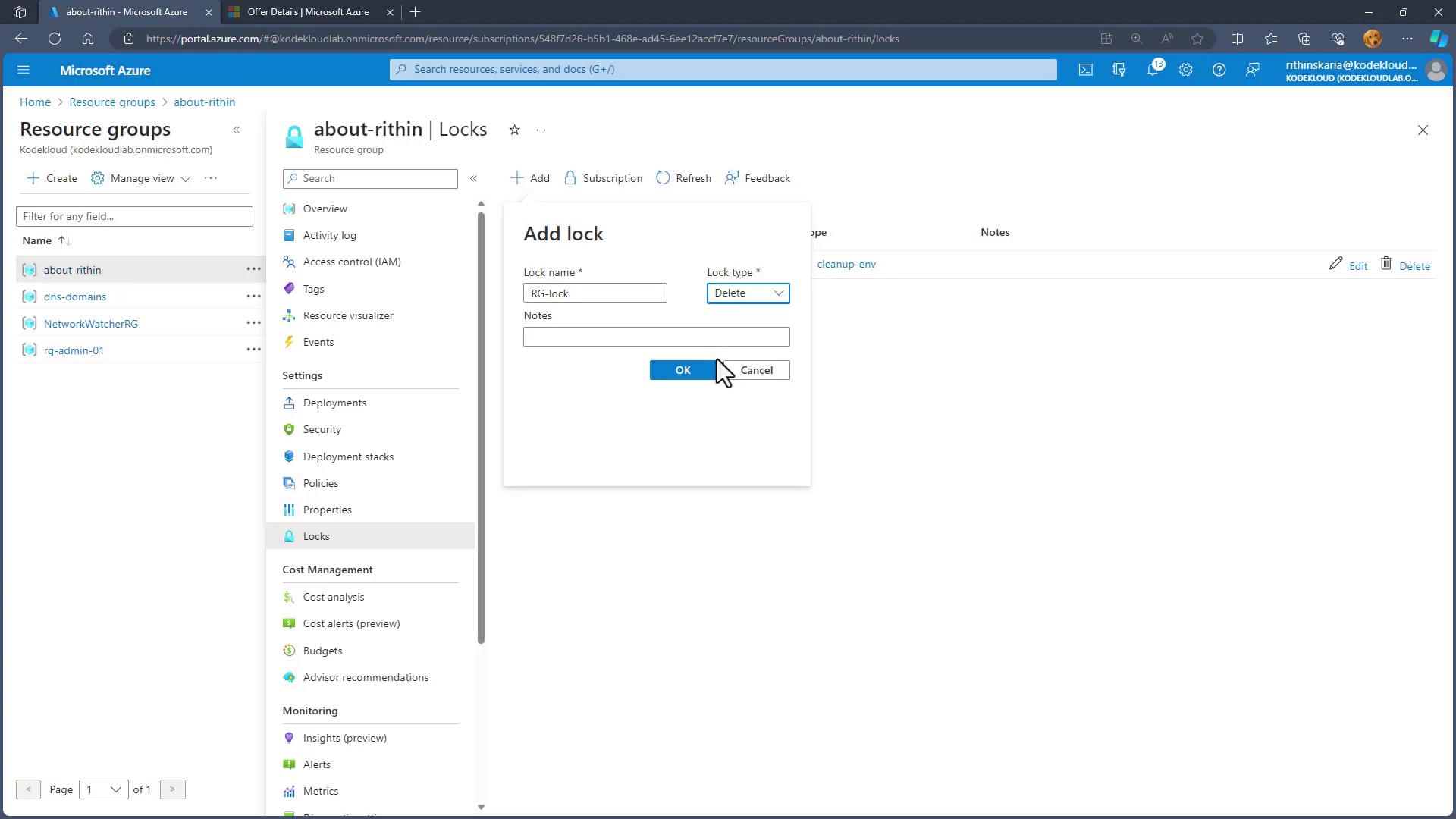
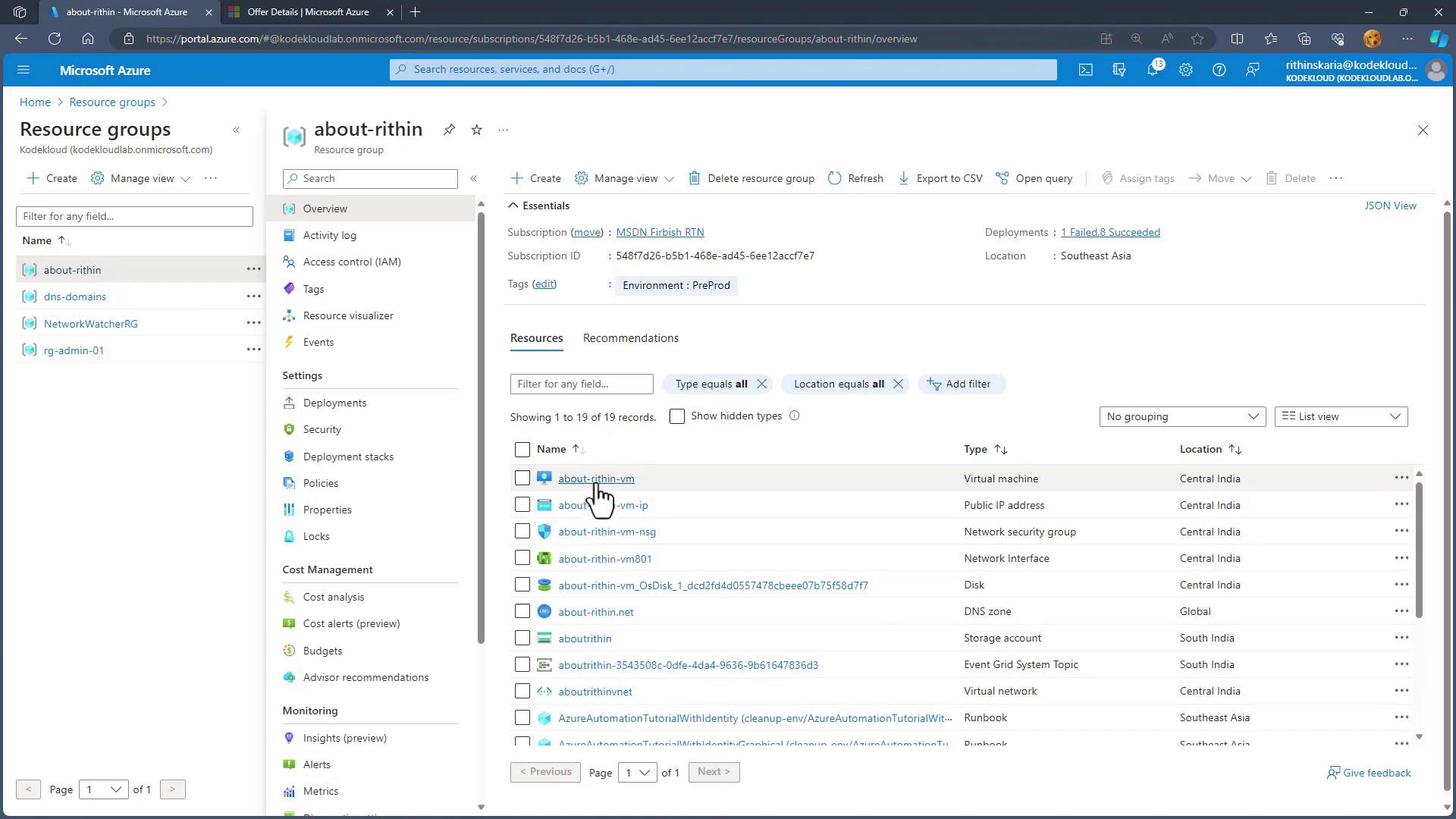
After saving this lock, all resources within the Resource Group—such as virtual machines (VMs), storage accounts, and network interfaces—are protected. Attempting to delete a VM along with its associated resources (disk, network interface, etc.) will fail due to the active lock.
Important Note
Remember, to make any change to a resource that is locked, you must first remove the active lock, perform the necessary updates, and then reapply the lock to maintain continuous protection.
Conclusion
Azure Resource Locks are a powerful tool that safeguards your cloud environment against accidental modifications or deletions. By strategically applying read-only or delete locks, you add an essential layer of protection to your resources. This ensures that routine maintenance or inadvertent script executions do not lead to critical mistakes.
Next, we will delve into strategies for managing costs in your Azure subscription, providing further insights for maintaining a secure and efficient cloud environment.
Watch Video
Watch video content