Azure Activity Logs are enabled by default with no additional setup required. They retain data for up to 90 days within the portal. For organizations needing longer retention periods (e.g., 180 days for compliance), logs can be exported to a storage account or sent to a Log Analytics workspace.
Querying Activity Logs
You can query Activity Logs directly from the Azure portal. The portal offers several filtering options including:- Subscription
- Timespan
- Severity
- Resource group
- Resource
- Initiating user
- Keyword search
Position of Activity Logs in the Azure Resource Stack
Activity Logs sit above the Azure infrastructure but below the host virtual machine and guest operating system layers. This means that internal events within a guest OS (for example, Windows events) are not captured in the Activity Logs. Instead, these logs record operations that directly interact with Azure’s infrastructure.Viewing Metrics and Activity Logs in the Azure Portal
In the Azure portal, you can access both operational metrics and activity logs for your resources. For instance, when you navigate to a virtual machine and select the “Monitoring” section, you can view platform metrics. Clicking on “See all metrics” opens the Metrics Explorer, where you can compare metrics like CPU usage and available memory.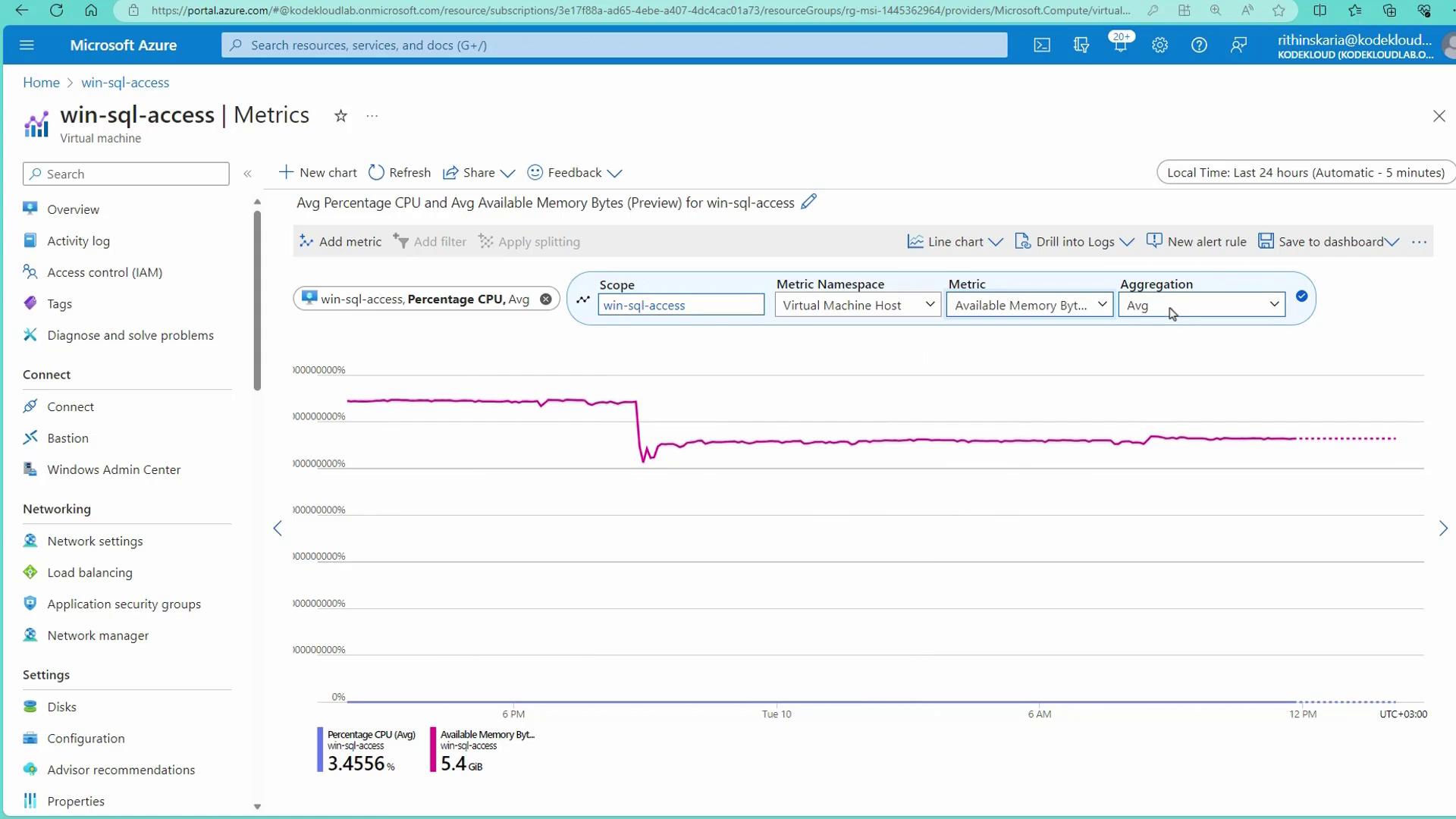
Event Categories
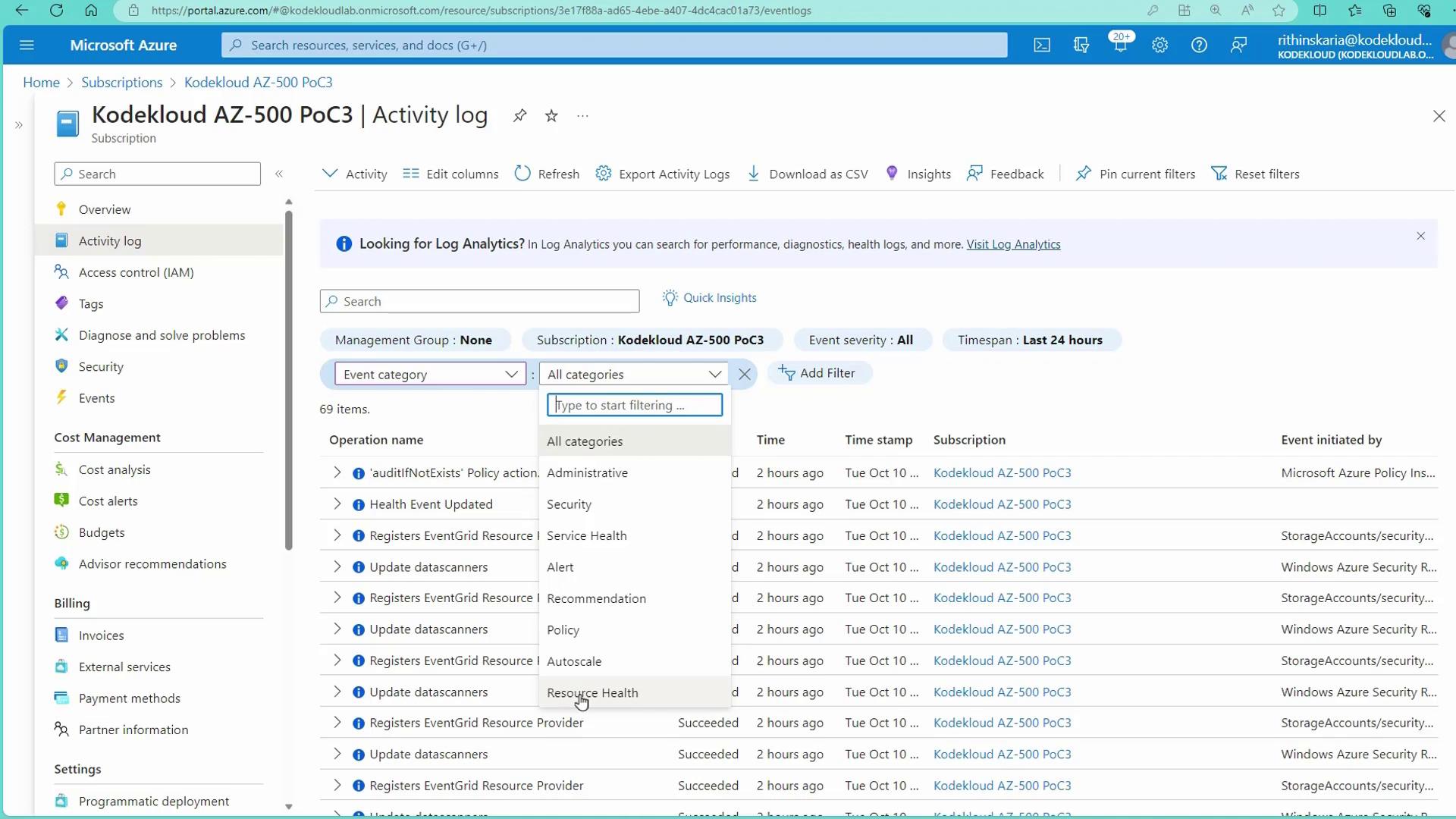
Azure Activity Logs categorize events into several types:| Category | Description |
|---|---|
| Administrative | Actions performed by users, service principals, or accounts. |
| Security | Alerts from Microsoft Defender for Cloud. |
| Service Health | Information on Azure service health. |
| Recommendation | Suggestions from Microsoft Azure Advisor. |
| Policy | Policy-related actions (e.g., deny, audit, or deploy if not exists). |
| Auto Scale | Activities related to auto scaling. |
| Resource Health | Events pertaining to the health of specific resources. |
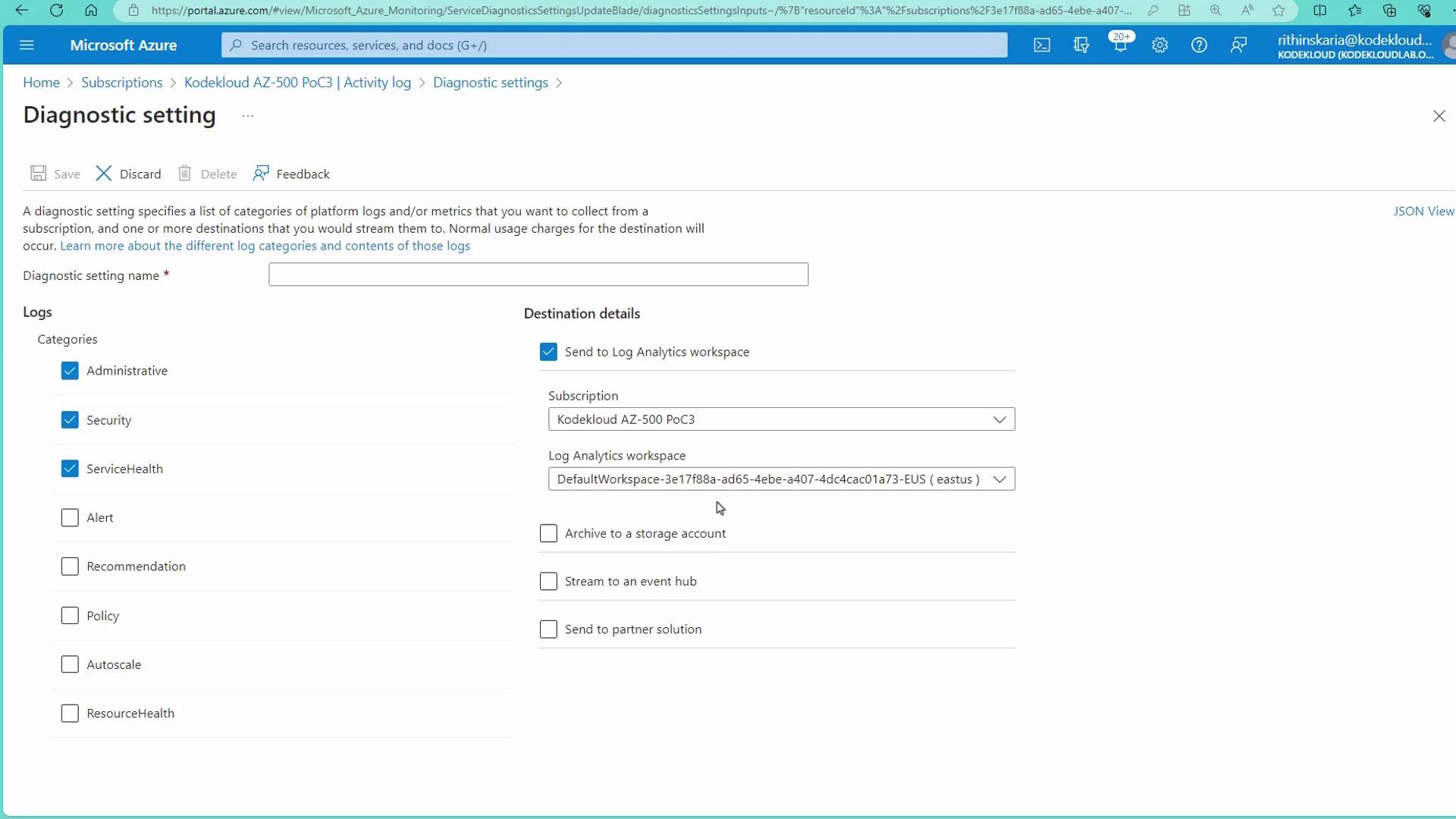
Working with Azure Monitor Alerts
Azure Monitor Alerts complement Activity Logs by enabling proactive surveillance of resource events. The diagram below summarizes the integration of Activity Logs with alerting, auditing, retention, and querying across various resource types (both compute and non-compute):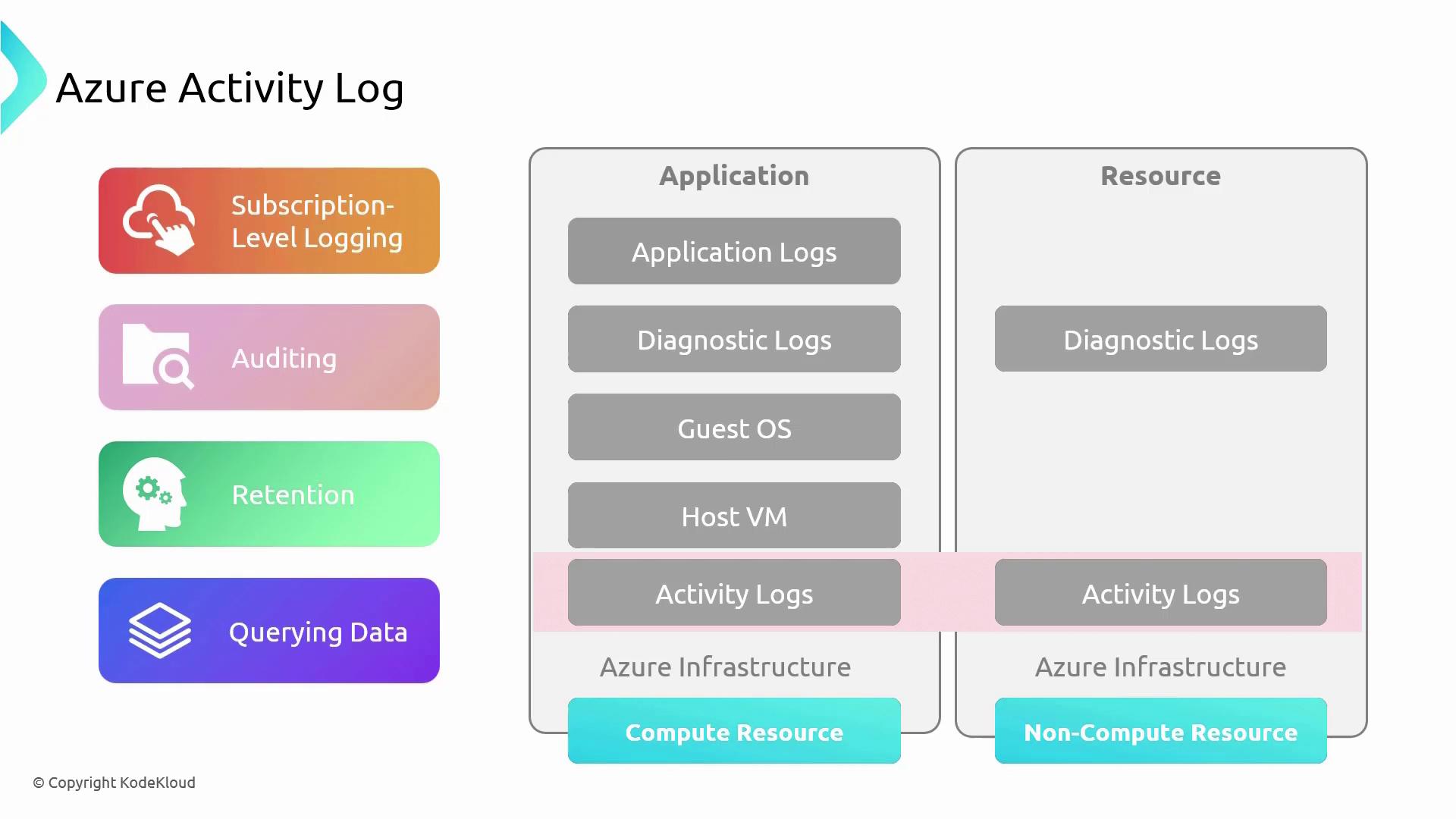
This integrated approach enhances your ability to track and manage resource operations effectively across your entire subscription.