AWS Certified SysOps Administrator - Associate
Domain 4 Security and Compliance
AWS Config Overview
Welcome to this comprehensive lesson on AWS Config. In this article, you'll learn how AWS Config provides detailed visibility into your AWS resources, offers robust auditing capabilities, and integrates seamlessly with other AWS services to maintain compliance.
AWS Config does not perform configuration tasks itself. Instead, it continuously records configuration changes across your AWS resources, allowing you to review what was configured and how it changed over time.
![]()
Unlike CloudTrail—which logs all API calls—AWS Config focuses on tracking resource configuration changes according to your defined rules. This focused capability is essential for auditing, compliance checks, and ensuring that your resources adhere to your security policies.
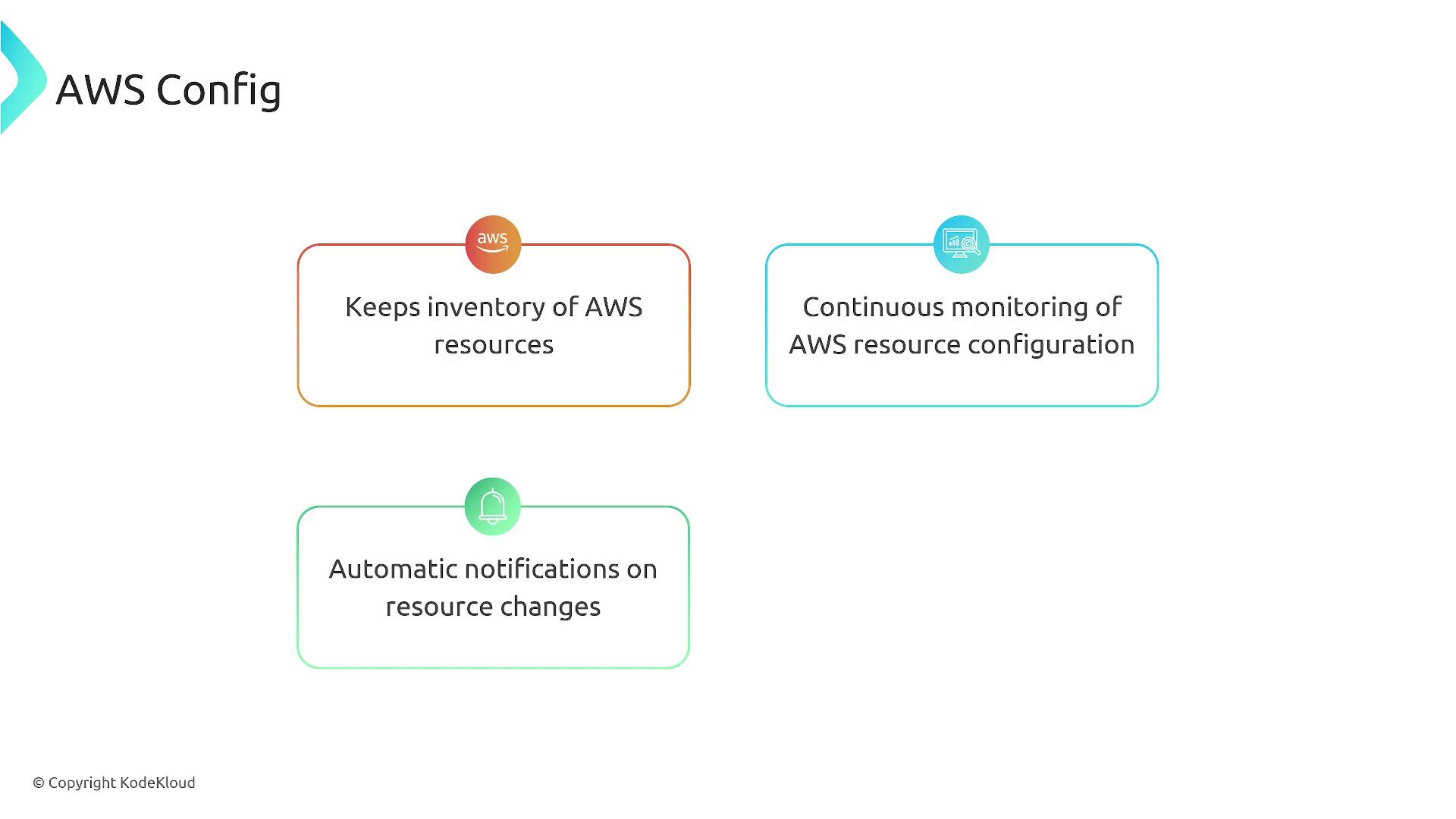
Key functions of AWS Config include:
- Maintaining a historical version of your service settings.
- Keeping an inventory of all AWS resources.
- Continuously monitoring resources for changes.
- Notifying you or triggering automated responses (e.g., via AWS Lambda) when a configuration rule is violated.
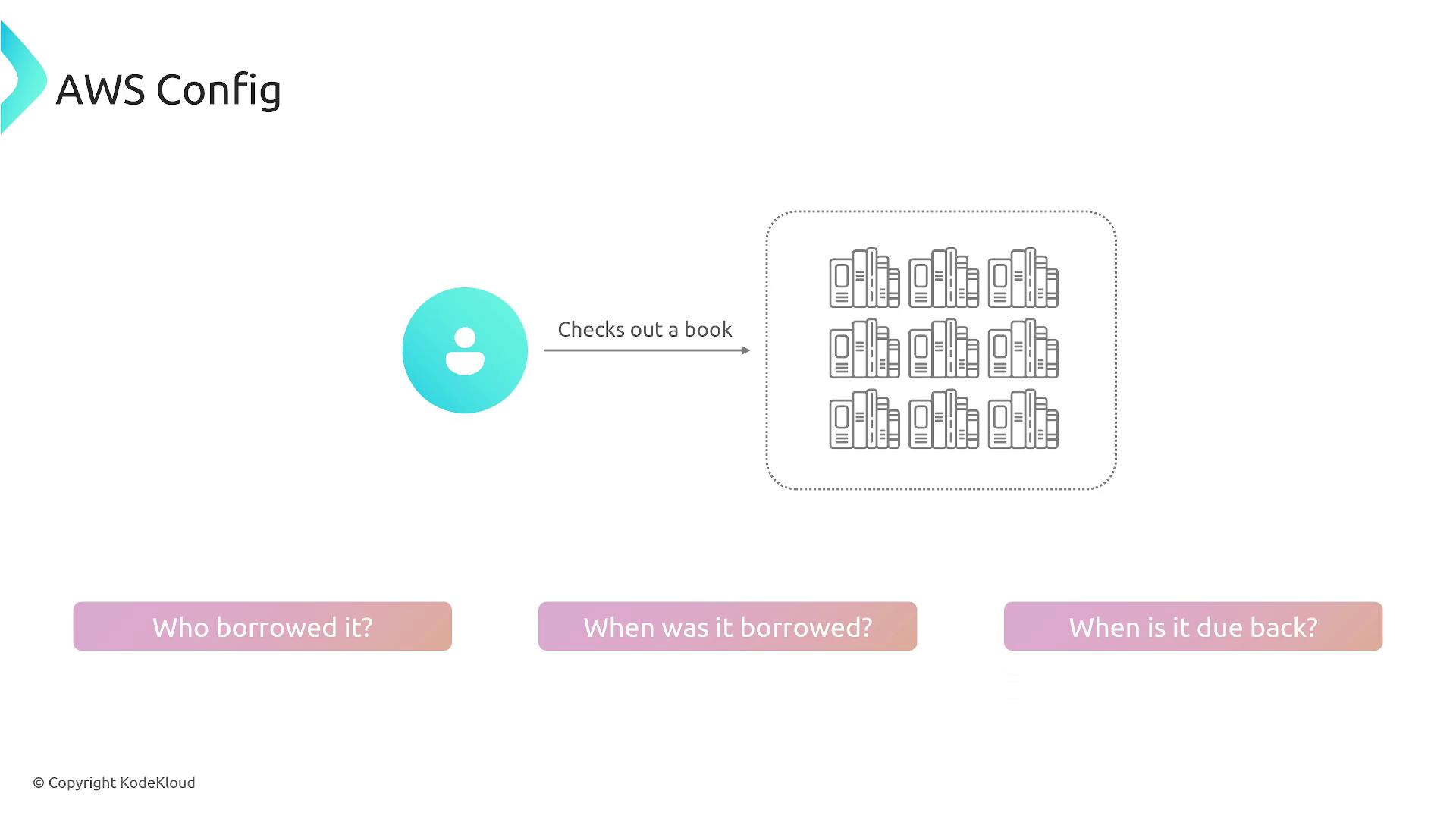
Think of AWS Config as a library catalog that tracks and records every item and its changes. It answers critical questions such as: "What changed?", "Who made the change?", "When did it change?" and "Where was the change applied?" This historical tracking is vital for conducting audits, generating compliance reports, and triggering remediation actions.
For example, consider a library where a book is checked out—the librarian tracks who borrowed it, when it was borrowed, and when it is due back. Similarly, AWS Config logs who modified configurations, what was changed, and when the changes occurred.
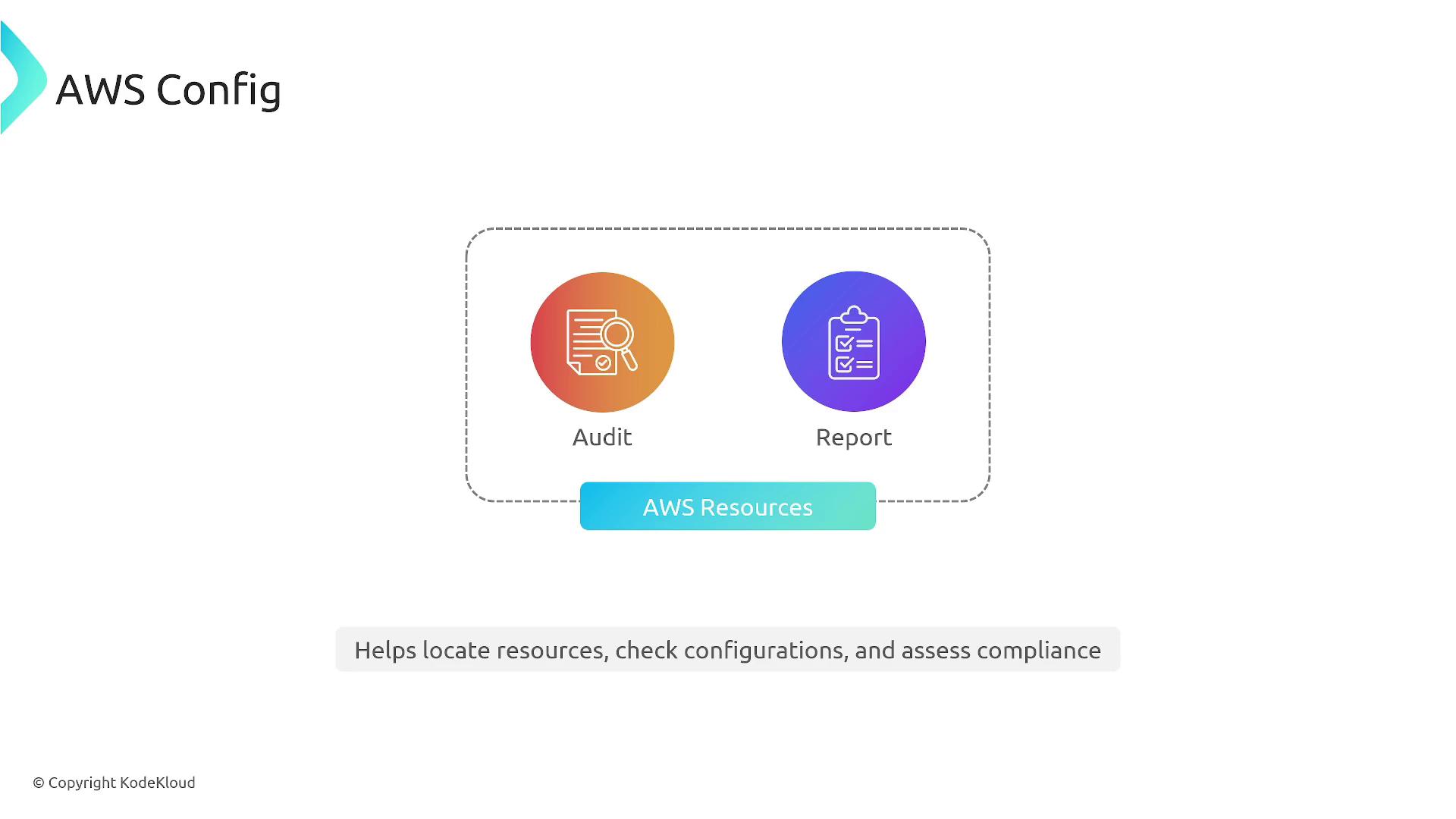
This service supports auditing for almost every AWS service—whether it’s EC2 instances, S3 buckets, or additional resources—helping you ensure consistent compliance with your baseline policies.
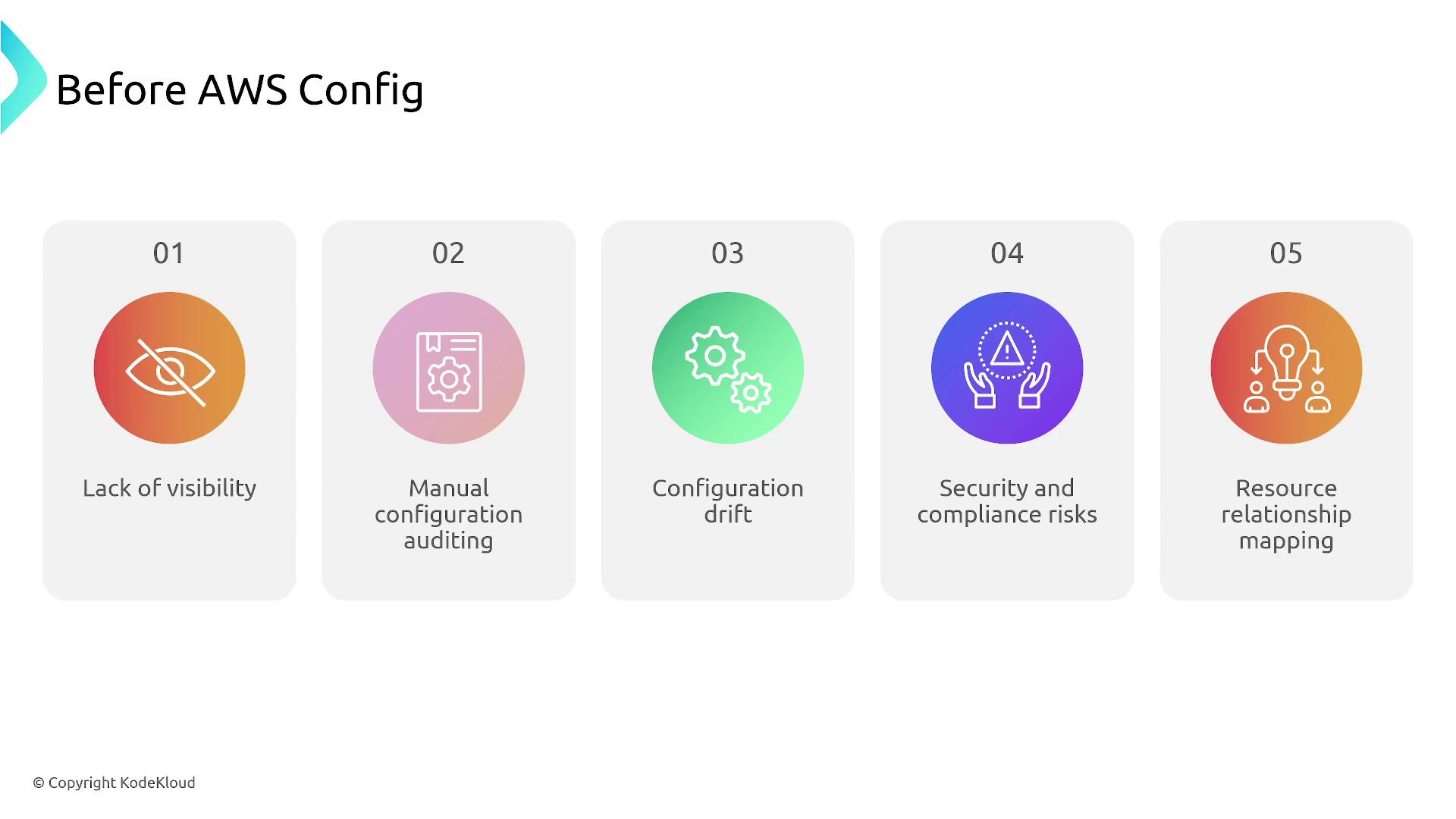
Without AWS Config, gaining visibility into environment changes becomes challenging. Manual audits are time-consuming, configuration drift can go unnoticed, and significant compliance issues may arise, increasing security risks. AWS Config addresses these challenges by mapping resource relationships and accurately tracking changes.
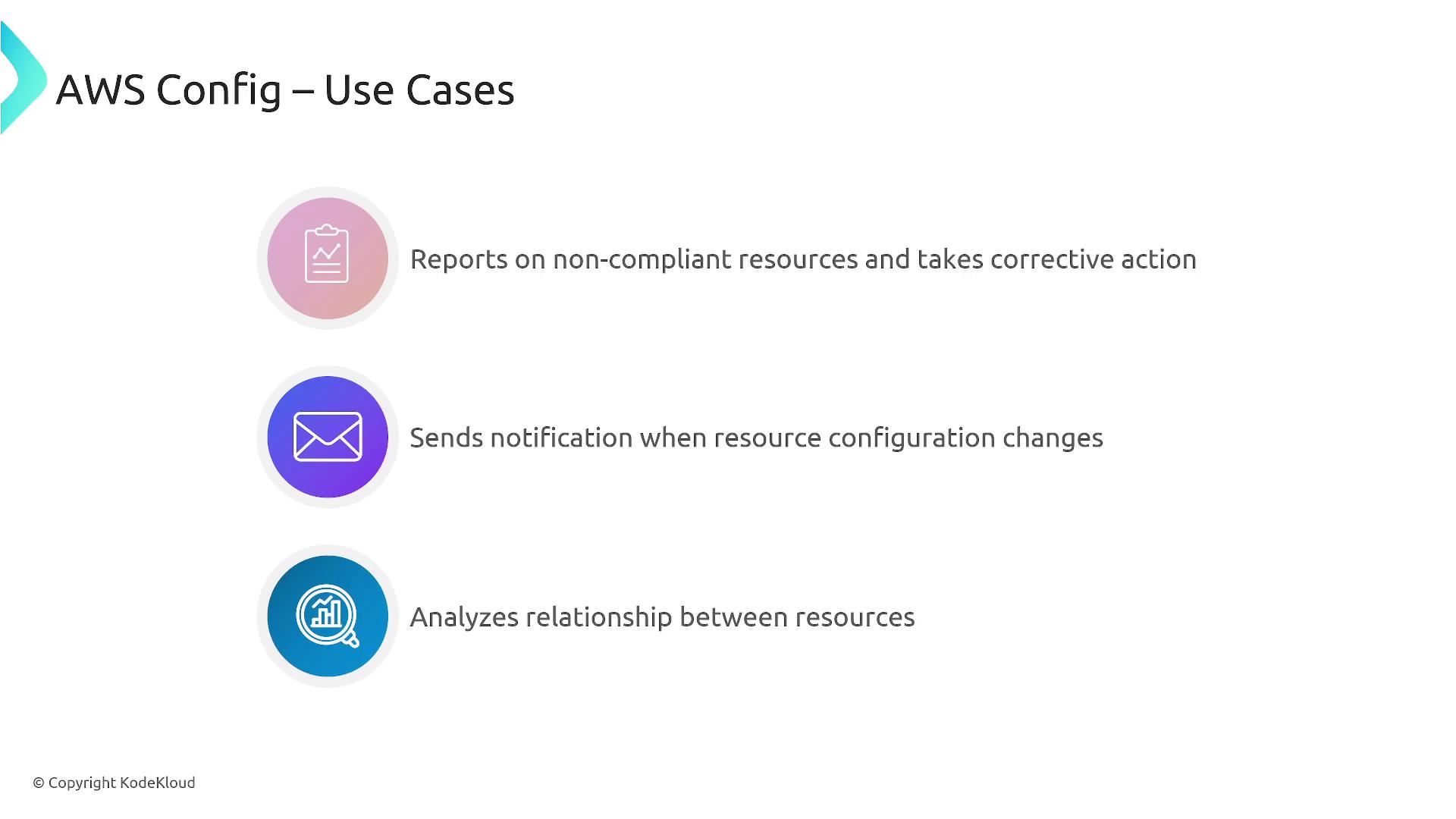
AWS Config is primarily used for inventory tracking, continuous monitoring, and auditing. It reports on non-compliant resources and can trigger notifications or remediation actions when policies are not met. Additionally, it maintains relationships between resources, illustrating the upstream impact of any configuration changes.
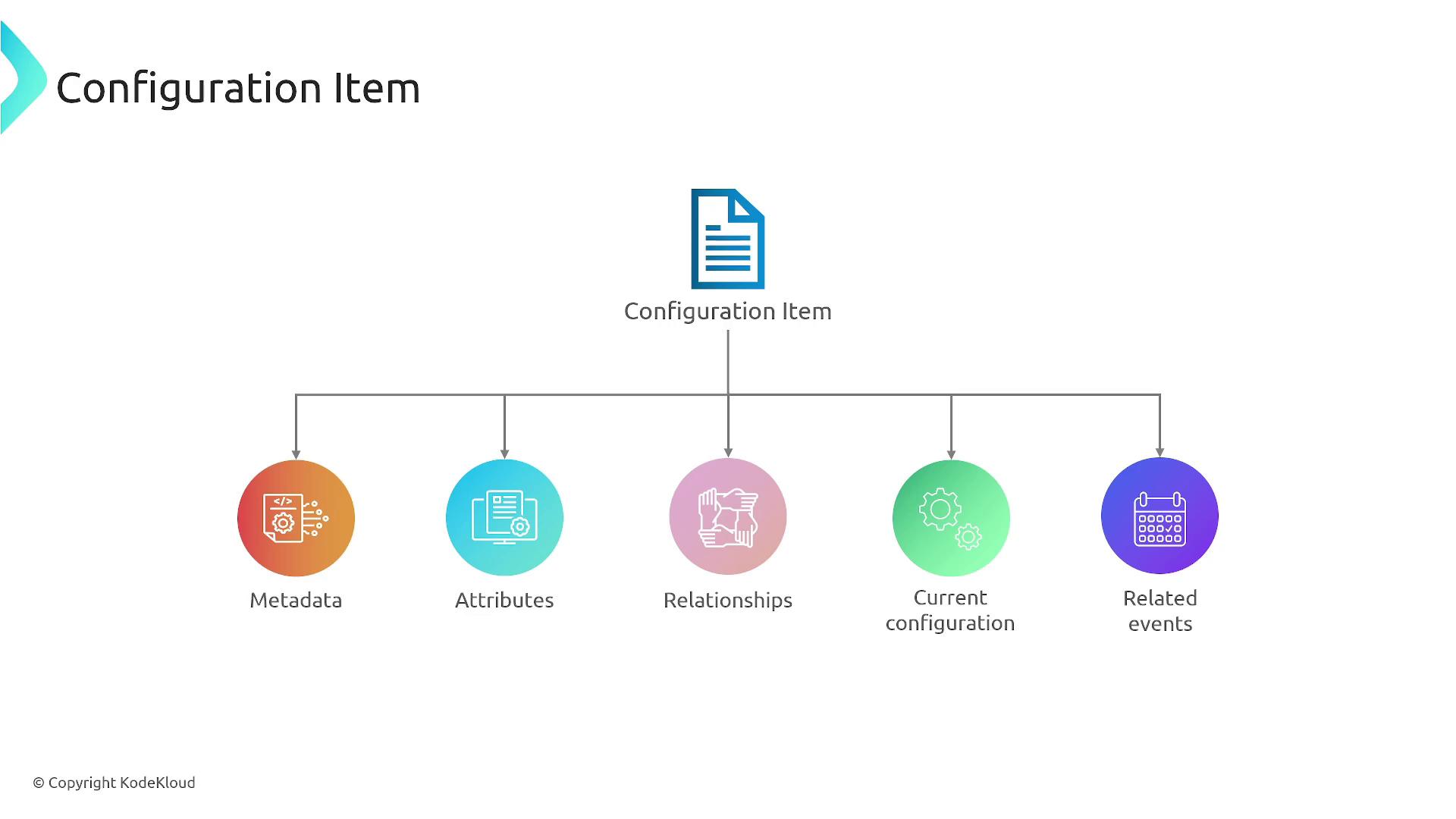
Each configuration item in AWS Config represents a snapshot of a resource’s metadata, attributes, relationships (for example, S3 buckets associated with Lambda functions), its current configuration, and related API events. AWS collectively refers to these snapshots as "resources."
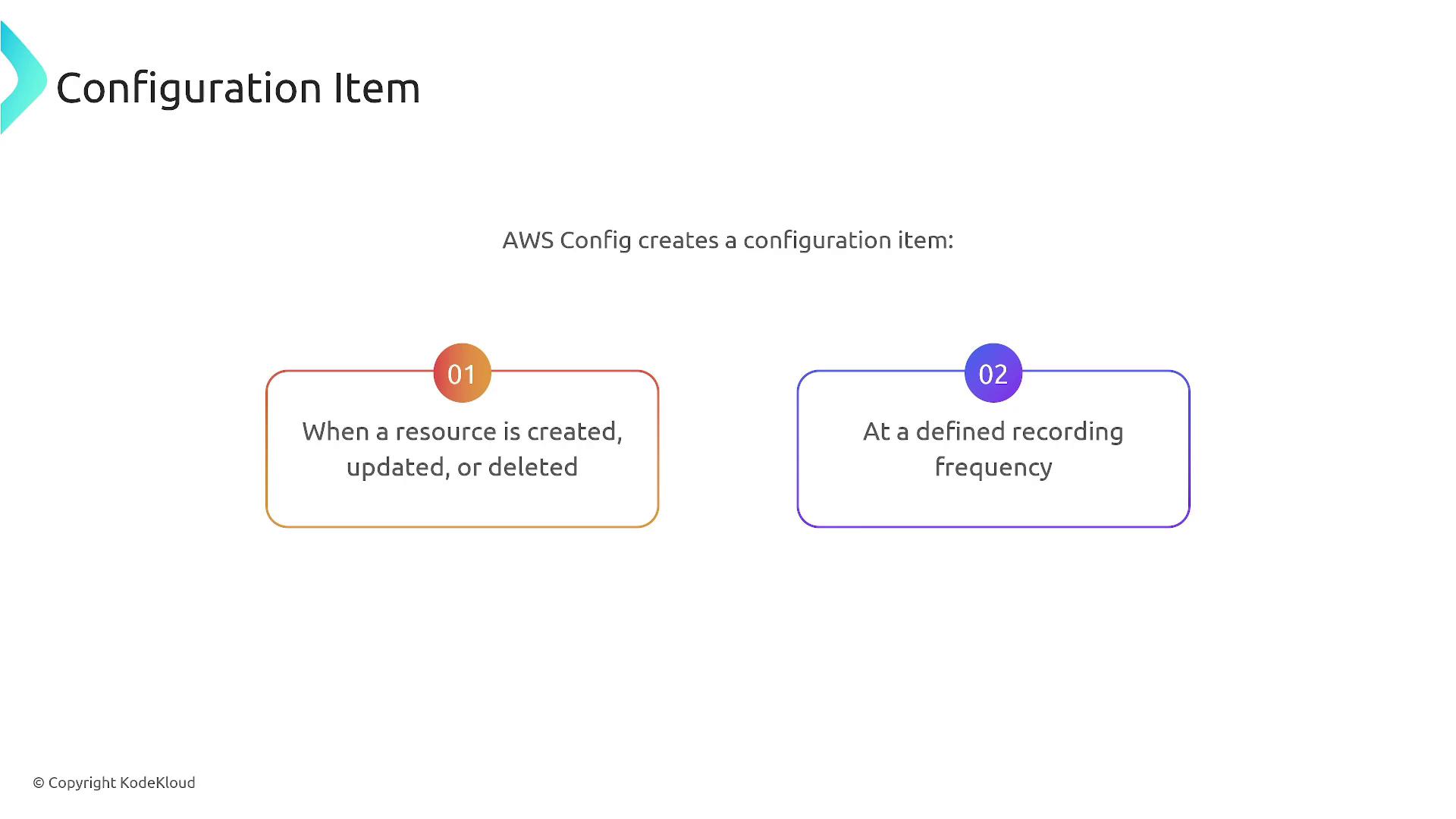
AWS Config automatically creates a configuration item whenever a resource is created, updated, or deleted. You can set the recording frequency to trigger on every change, every 10 minutes, hourly, or daily—depending on your resource sensitivity.
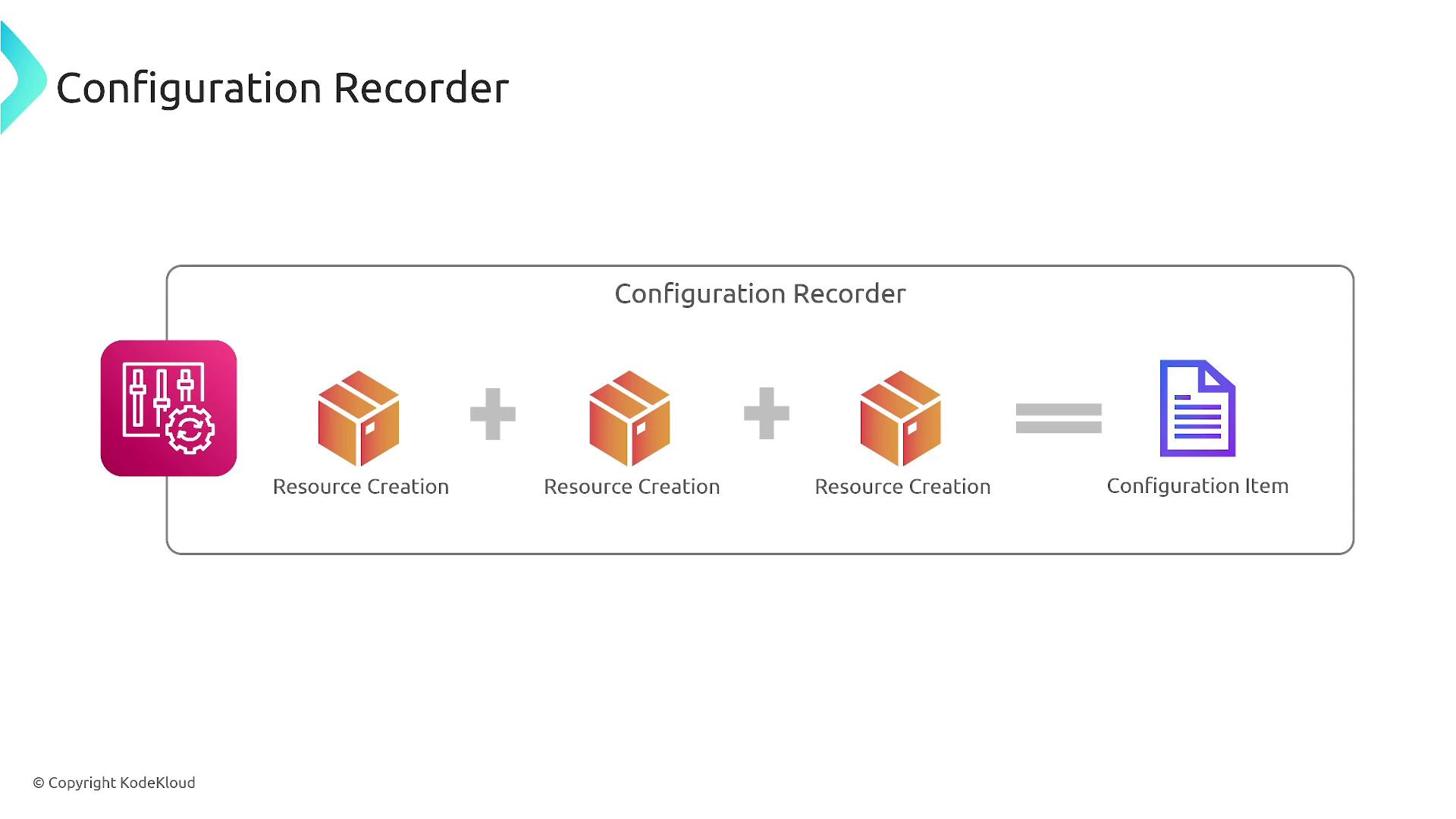
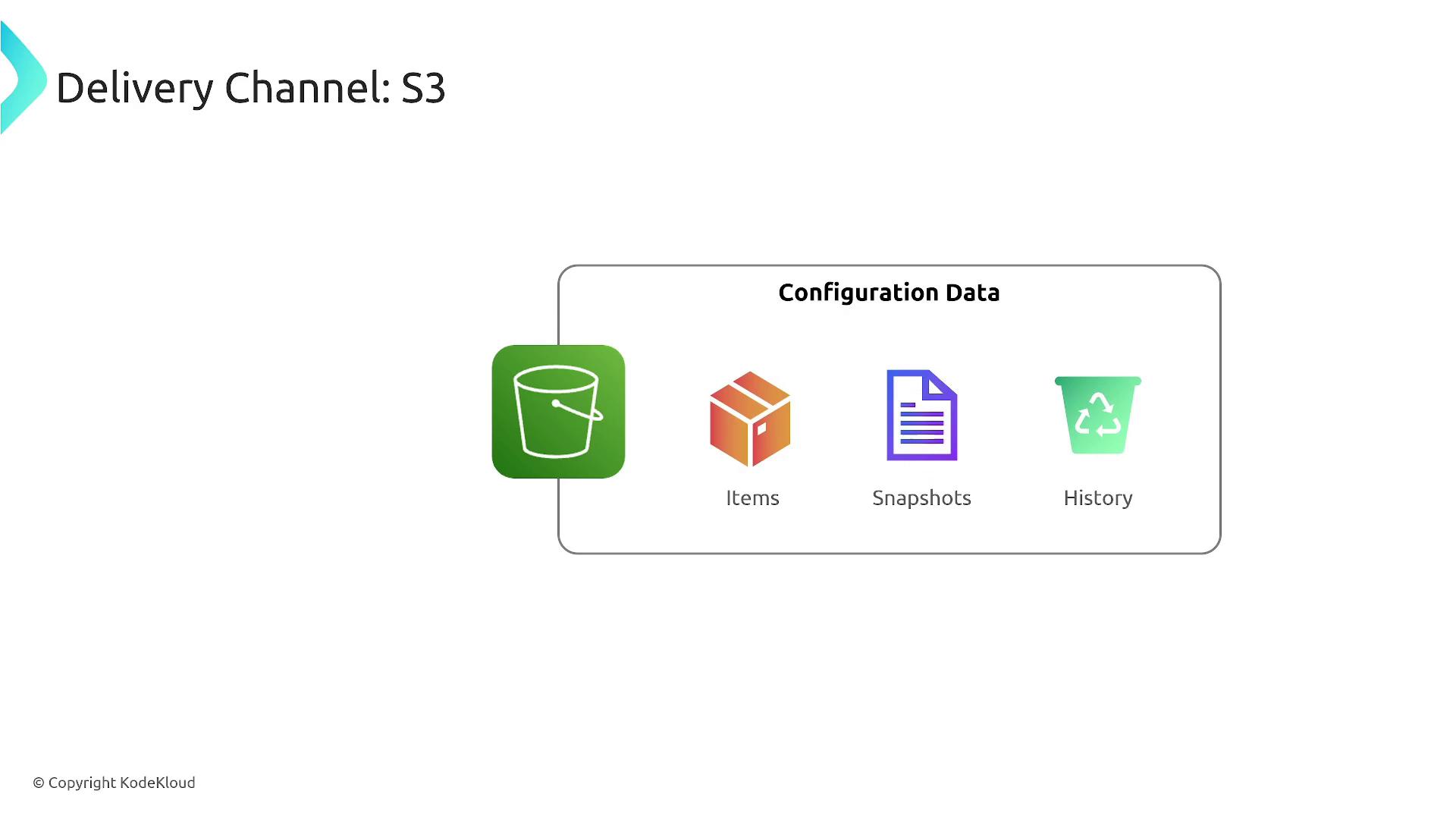
The historical collection of these items, known as configuration history, provides valuable context regarding how a resource evolves over time. This data is stored in an S3 bucket, where records are grouped by creation, updates, and deletions.
![]()
AWS Config delivers configuration data to various destinations:
- Storing data in an S3 bucket.
- Publishing notifications through SNS.
- Triggering AWS Lambda functions for automated remediation.
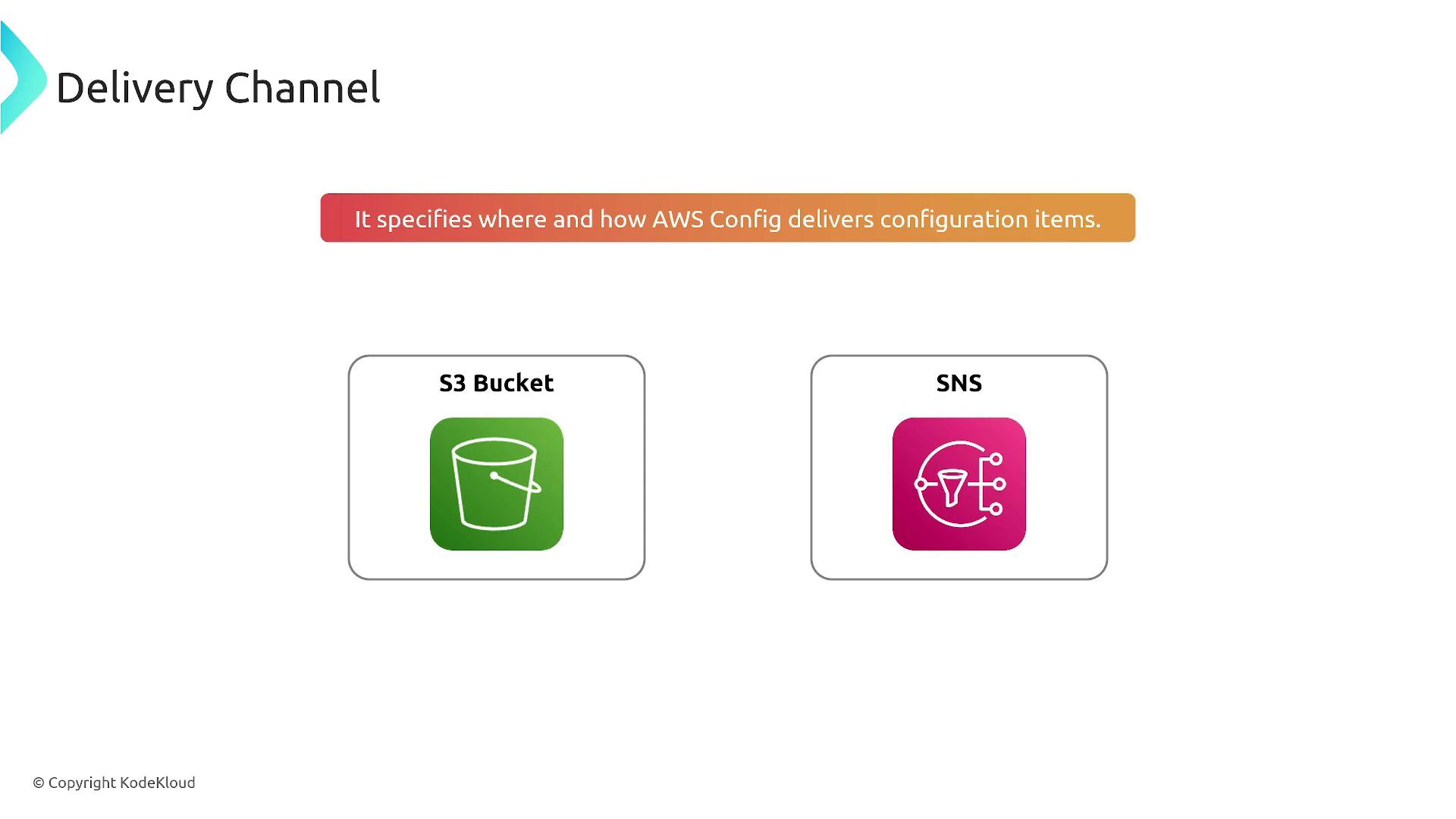
For example, if you choose S3 as your storage destination, ensure that AWS Config has the necessary permissions to access the bucket. Alternatively, using SNS allows subscribers to receive emails or text messages, and even trigger Lambda functions.
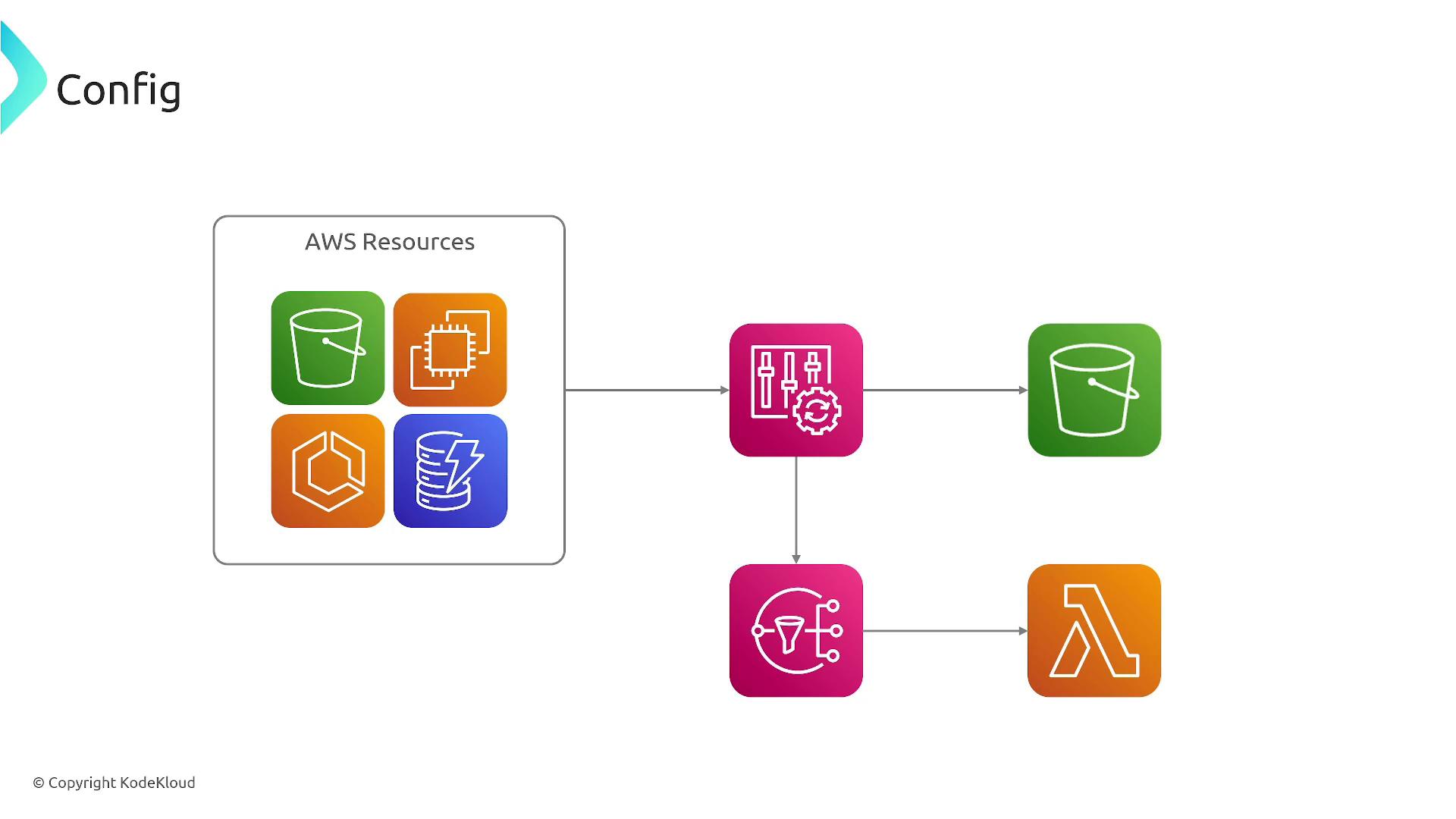
In this example, AWS Config monitors services such as S3, EC2, ECS, and DynamoDB for configuration changes. When a change is detected, it records the change, triggers remediation actions, and sends notifications concurrently.
AWS Config Rules and Evaluations
AWS Config rules help determine whether a configuration complies with specific requirements. For instance, one rule might verify that an Application Load Balancer (ALB) redirects HTTP traffic to HTTPS. This detective rule monitors configurations and alerts you if non-compliance is detected without automatically remediating the condition.
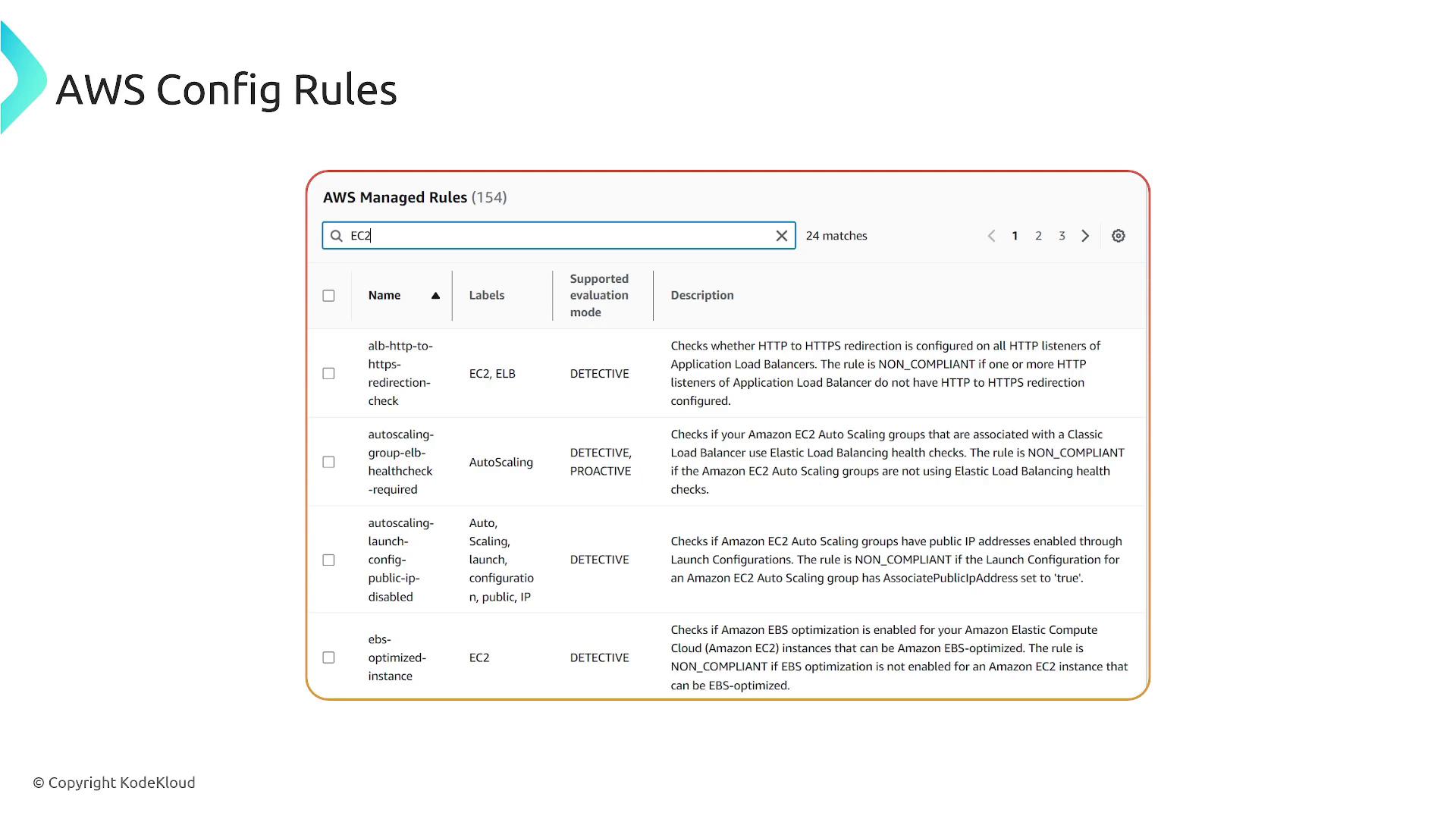
Another rule might ensure that EC2 Auto Scaling groups tied to a Classic Load Balancer are using appropriate health checks. This proactive rule not only detects non-compliant states but can also trigger notifications or remediation actions upon violations.
Compliance is clearly indicated: for example, an EC2 volume that is not encrypted might be marked as "non-compliant," whereas an encrypted volume is shown as "compliant."
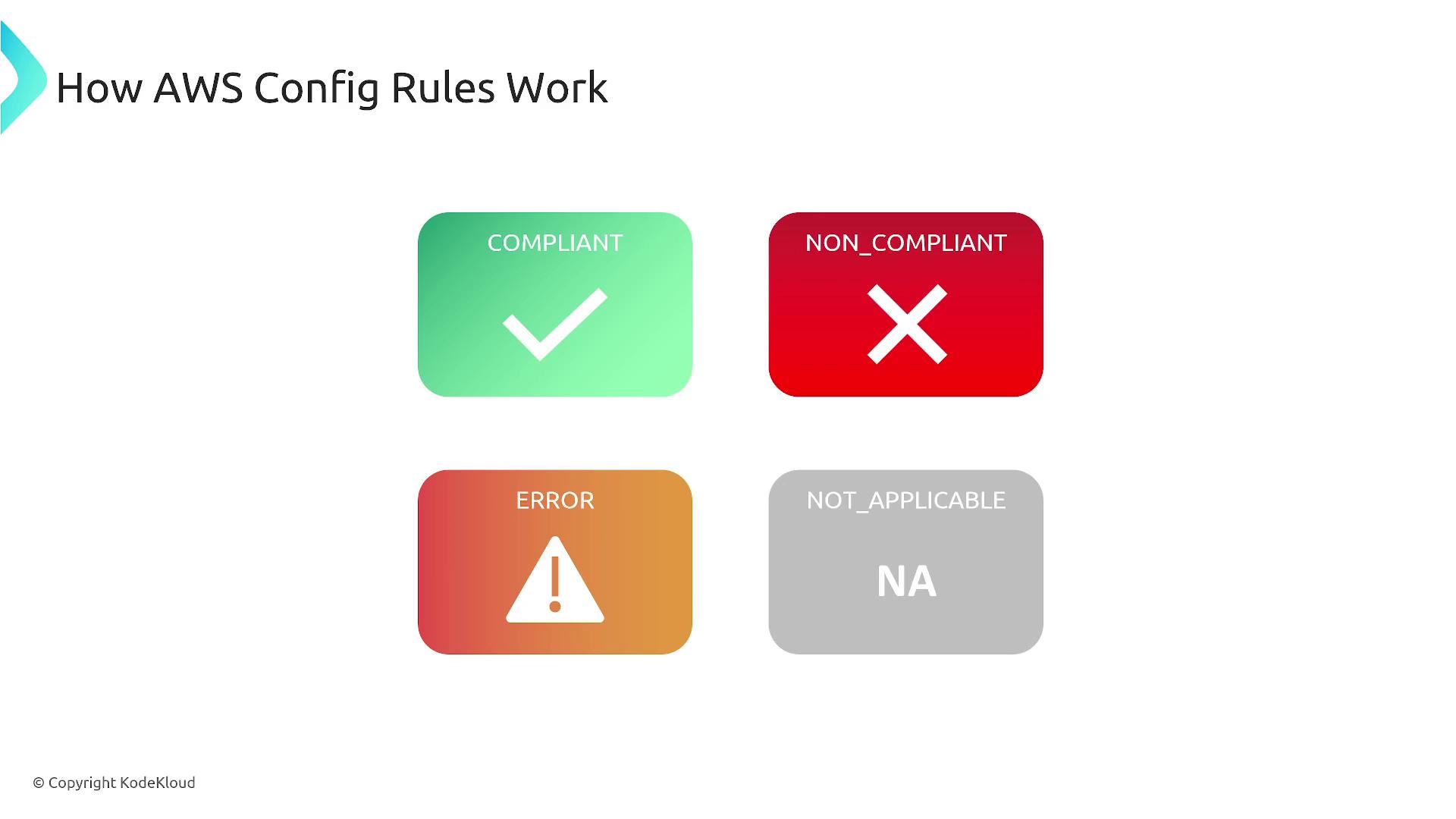
There are two primary evaluation modes in AWS Config:
Proactive Evaluation:
Checks configuration changes before they are applied. For example, if there is an attempt to open a port on an EC2 instance, this mode can block the change before it is committed.Detective Evaluation:
Monitors and assesses changes after they occur, identifying non-compliant configurations without preventing the change.
AWS Config also uses different trigger types to determine when a rule is evaluated:
- Configuration Changes Trigger: Evaluation occurs immediately after a configuration change.
- Periodic Trigger: Evaluations are performed at regular, configured intervals.
- Hybrid Trigger: Combines immediate evaluations with periodic checks.

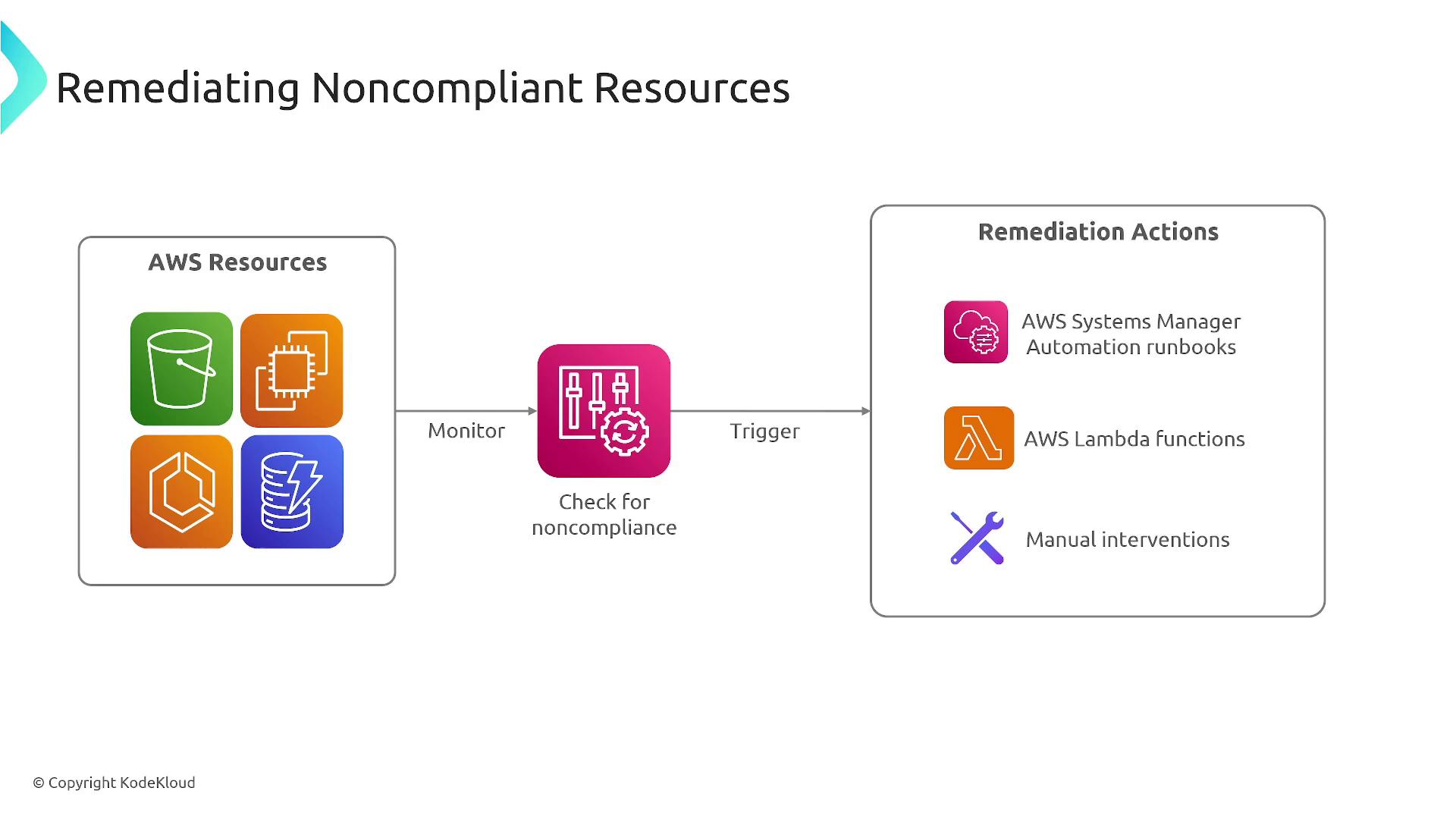
Remediation Options
AWS Config goes beyond monitoring by also triggering remediation actions to address non-compliant changes. These actions may include:
- Activating AWS Systems Manager.
- Triggering an AWS Lambda function.
- Sending notifications to prompt manual intervention.
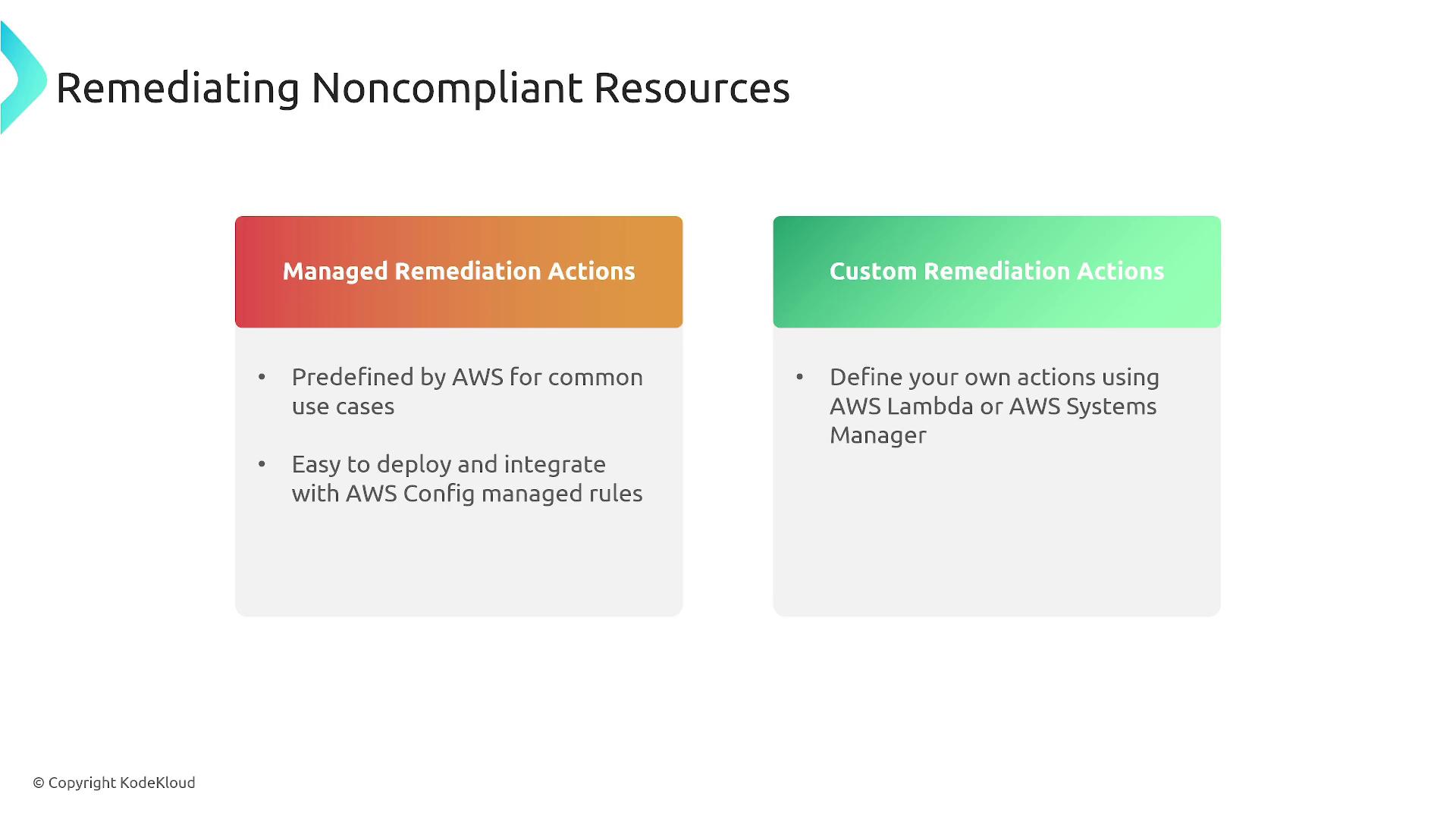
Predefined rules can automate remediation, or you can define custom actions using AWS Lambda or Systems Manager documents. This automation minimizes risks by rapidly correcting non-compliant configurations.
Conformance Packs and Aggregation
AWS Config also provides conformance packs—collections of pre-packaged AWS Config rules and remediation actions that can be deployed as one package. You can apply these packs across an entire account, a region, or even an AWS Organizations unit. Conformance packs are typically created using YAML templates and managed via Systems Manager documents.

Another key feature is the AWS Config Aggregator. This tool centralizes configuration data across multiple accounts, regions, and organizational units. It aggregates information on resource configurations and their compliance, offering a unified view that is invaluable for large-scale governance.
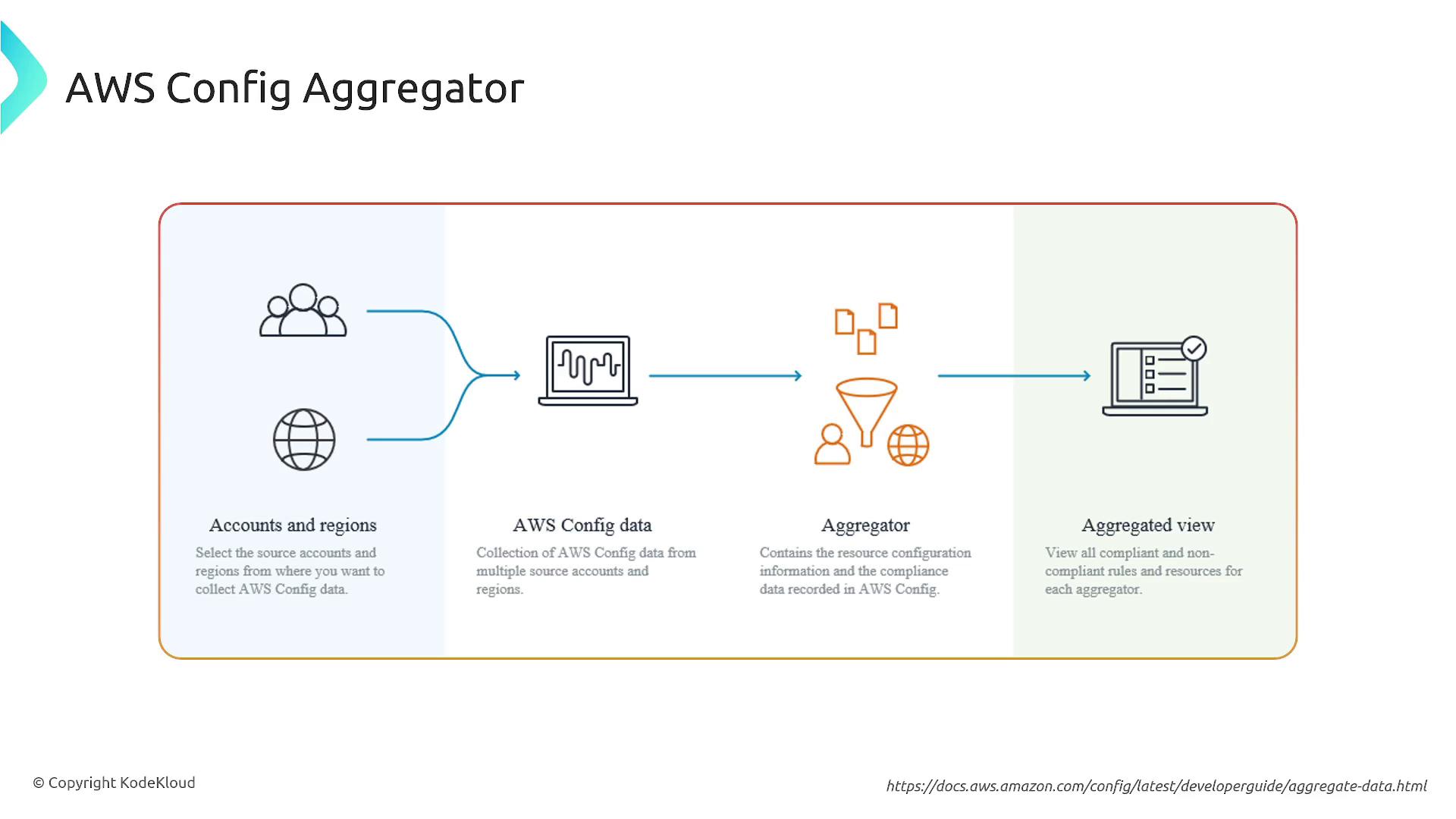
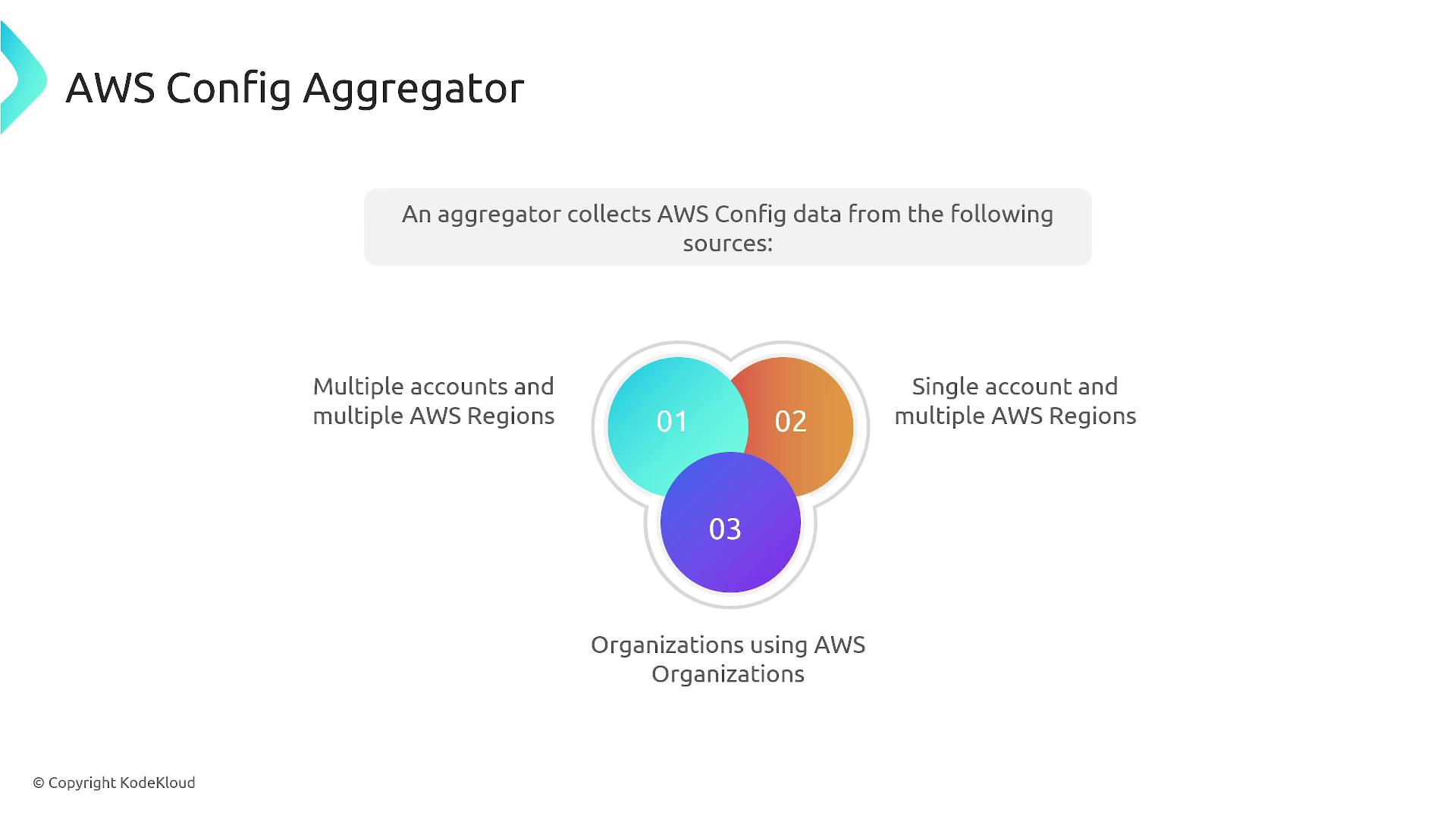
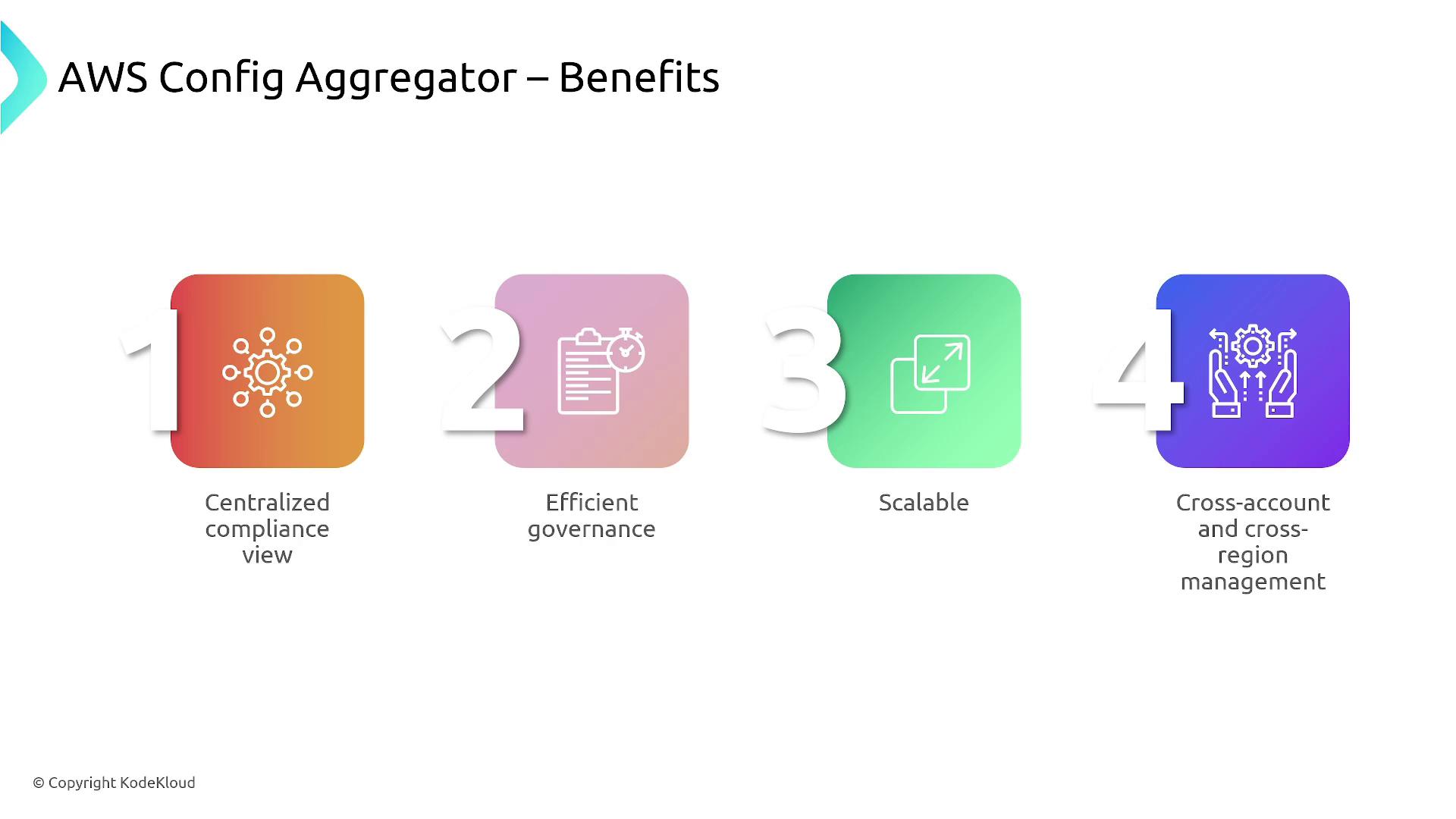
The aggregator provides a comprehensive view of your resources and their compliance status, making it easier to monitor non-compliant assets and manage overall compliance.
Summary
AWS Config is an essential service for tracking AWS resource configurations, auditing changes, and ensuring compliance. Its ability to detect non-compliant changes—whether proactively or retrospectively—automate remediation actions, and aggregate data across multiple accounts makes it a vital tool for managing large-scale environments.
By understanding the differences between proactive and detective evaluation modes, the various trigger types, and available remediation options, you are now better equipped to implement and manage configuration compliance within your AWS environments.
Note
Leveraging AWS Config not only helps in maintaining compliance but also simplifies the process of auditing and governance in dynamic cloud environments.
This concludes our lesson on AWS Config. Happy configuring!
Watch Video
Watch video content