AWS Certified SysOps Administrator - Associate
Domain 4 Security and Compliance
Security Hub Overview
Welcome to this lesson on AWS Security Hub. In this guide, you will learn how Security Hub centralizes security findings across your AWS environment, acting as a comprehensive cloud security posture management system. It aggregates findings from both AWS native services and third-party tools, giving you a unified view of your cloud security across multiple accounts and regions.

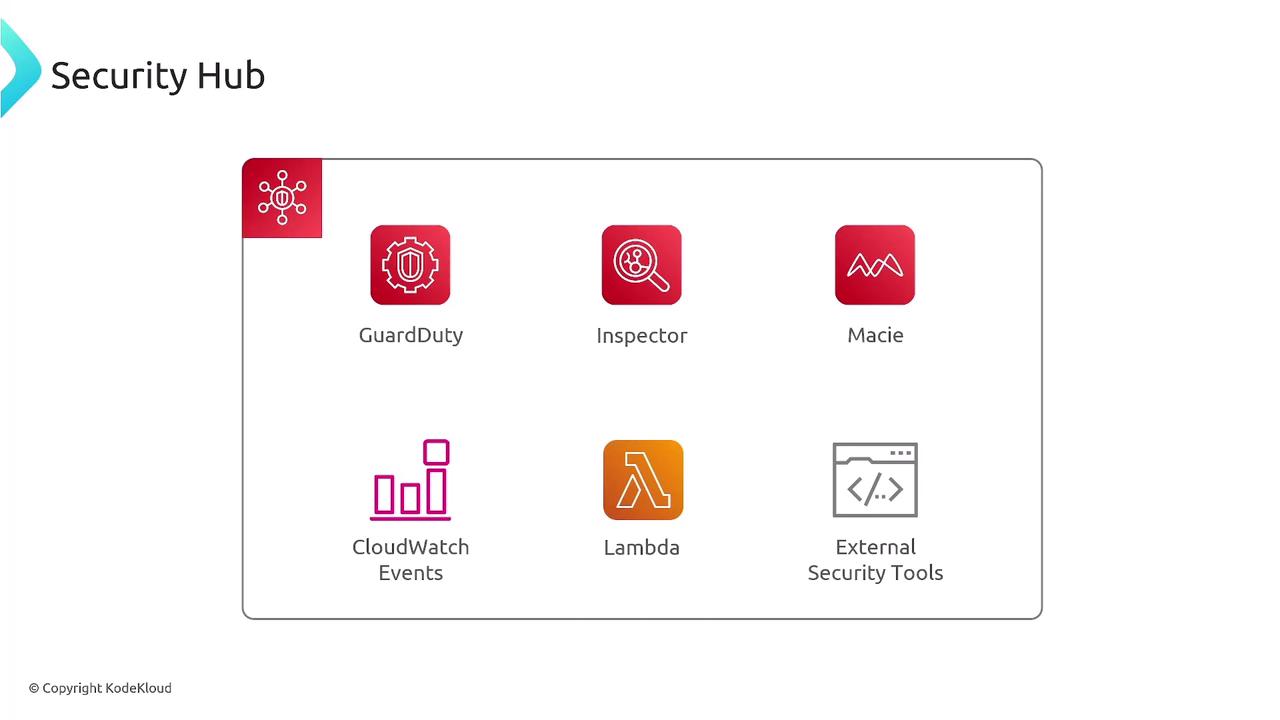
Security Hub collects and correlates security data from several services including:
- GuardDuty: Monitors network activity for potential threats.
- Inspector: Identifies vulnerabilities in EC2 instances, Lambda containers, and more.
- Macie: Scans S3 buckets for personally identifiable information (PII).
- CloudWatch Events: Triggers automated actions based on defined events.
It also integrates with leading third-party solutions such as CrowdStrike and Palo Alto to further enhance your security posture.
Key Benefits
AWS Security Hub offers several key advantages:
- Centralized View: Monitor security across all AWS accounts and regions from one unified dashboard.
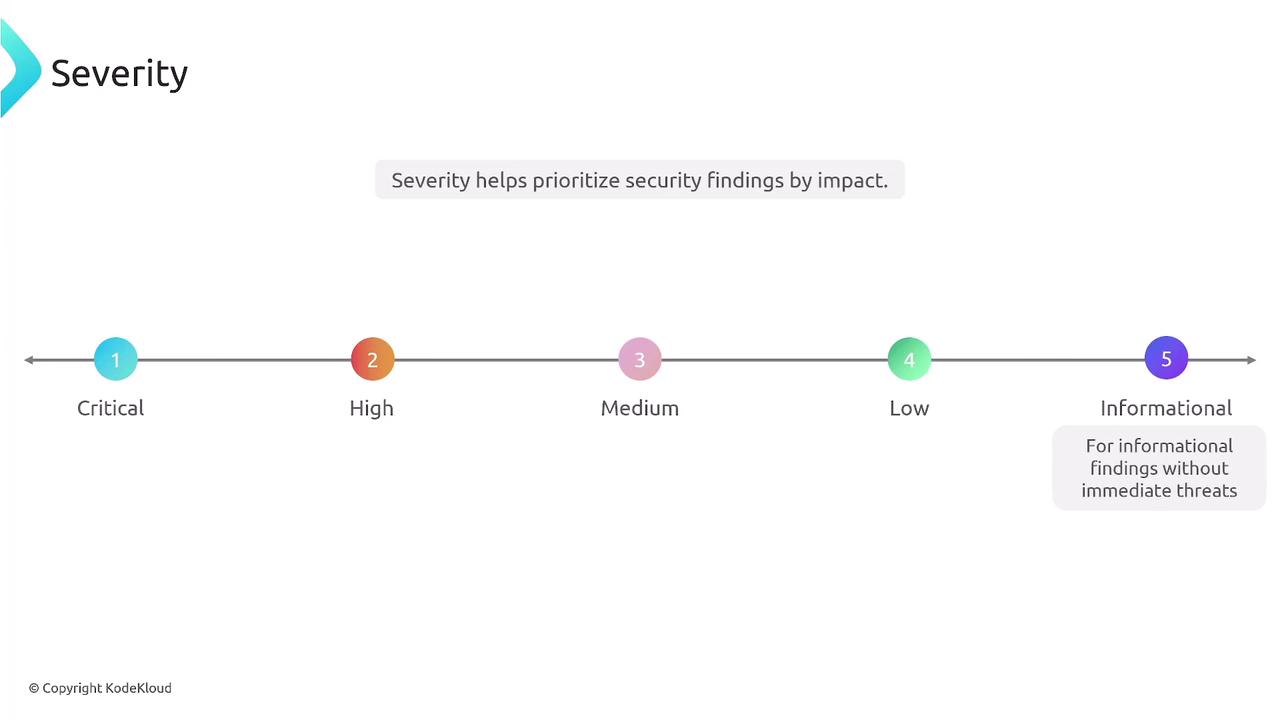
- Prioritization: Findings are categorized by severity (Critical, High, Medium, Low, Informational), enabling you to focus on the most significant threats.
- Automation: Integrate with AWS Lambda, Step Functions, or Systems Manager to enable automated responses.
- Compliance: Streamline auditing processes and compliance checks with built-in rule packs.
- Scalability: Easily scale your security monitoring as your environment grows across regions and accounts.
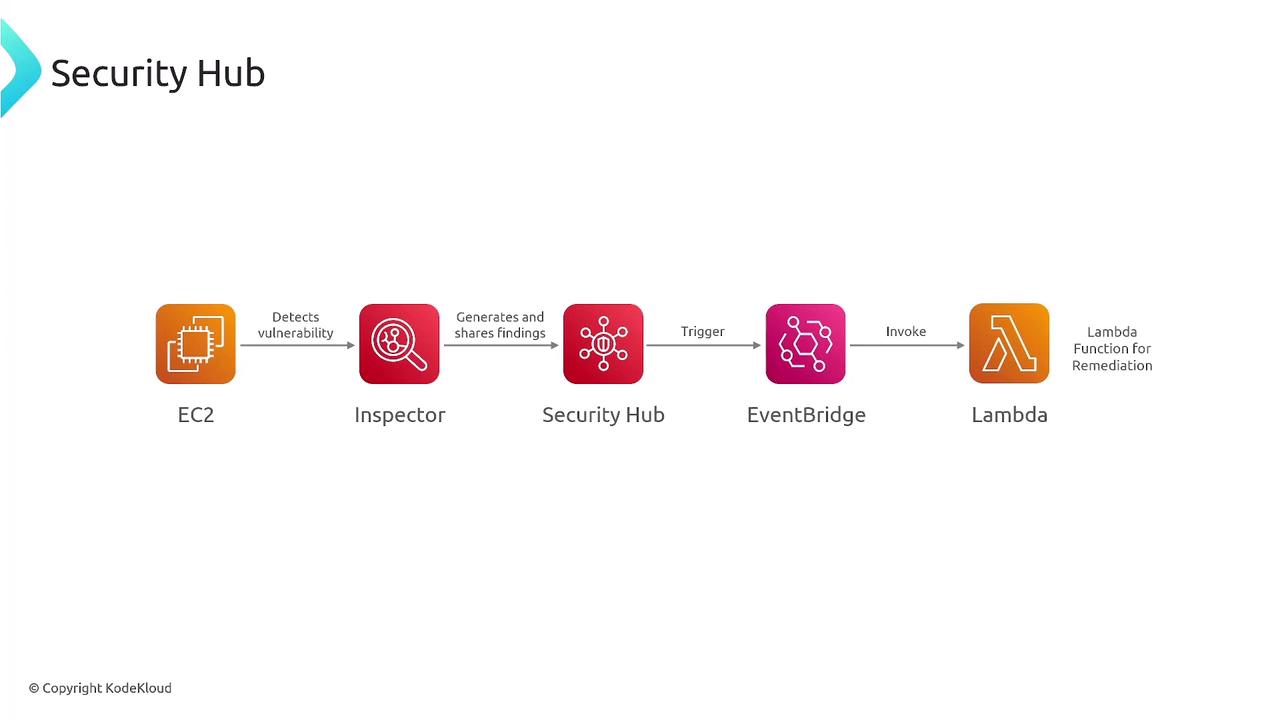
For example, if a vulnerability is detected on an EC2 instance by Inspector, Security Hub aggregates the finding, prioritizes it, and triggers an EventBridge event. This event can then invoke a Lambda function to either remediate the issue or notify the appropriate teams.
Furthermore, other AWS services like AWS Config and Step Functions can be seamlessly integrated into your security workflows to detect configuration changes and orchestrate complex remediation processes across multiple services.
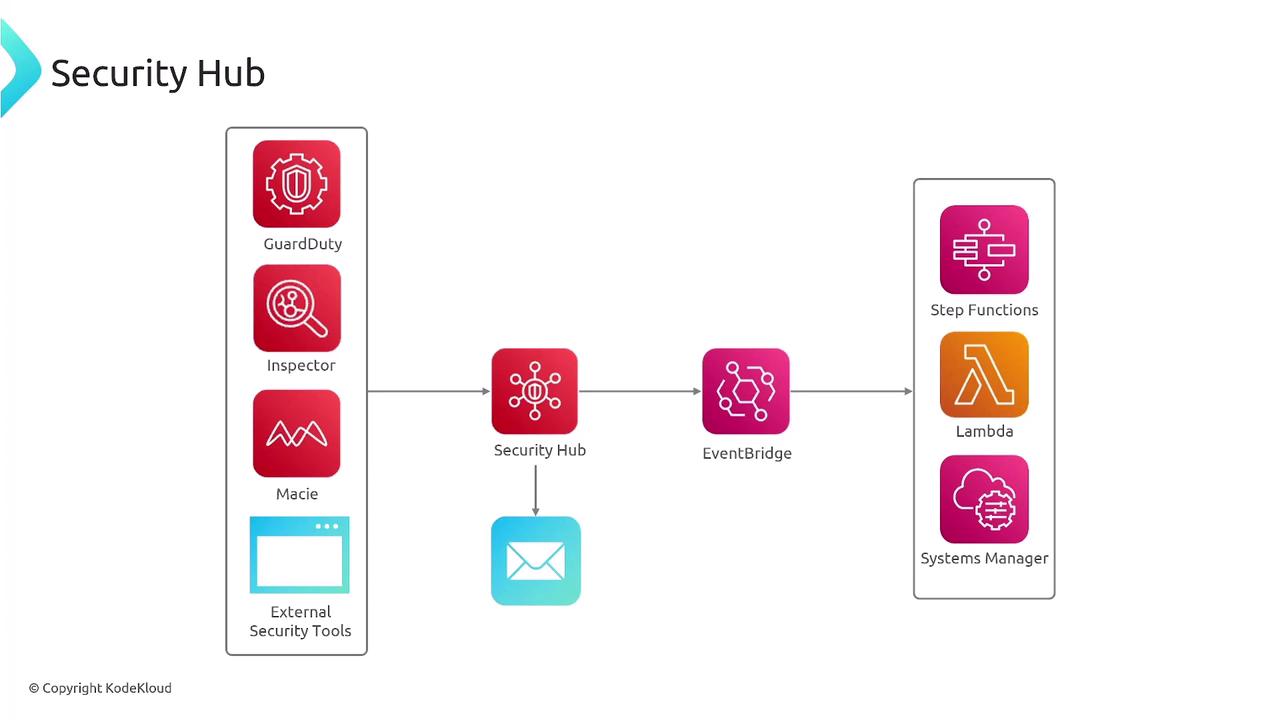
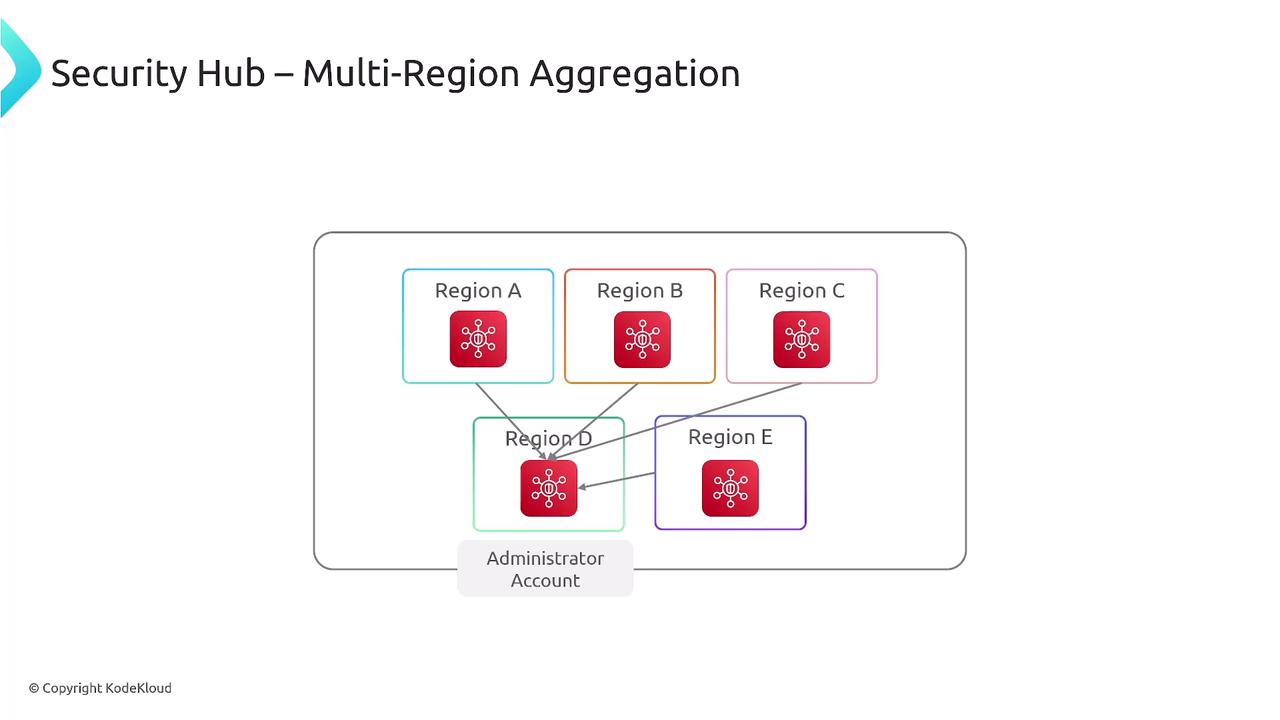
Since Security Hub supports multi-region data aggregation, tracking security findings across diverse geographical locations becomes effortless. It leverages AWS Config to monitor configuration changes and enforce compliance rule packs. During setup, you will be prompted to enable AWS Config, choose compliance packs (such as PCI DSS, HIPAA, or various CIS benchmarks), and designate a primary administrator account.
Security Findings Format
AWS Security Hub standardizes all security findings using the AWS Security Finding Format (ASFF). Below is an example of a typical finding:
{
"AwsAccountId": "123456789012",
"CreatedAt": "2023-07-30T12:00:00Z",
"Description": "The S3 bucket my-bucket is publicly accessible.",
"Title": "Public S3 Bucket",
"Severity": {
"Label": "HIGH",
"Original": "8.0",
"Normalized": 80
},
"Resources": [
{
"Type": "AwsS3Bucket",
"Id": "arn:aws:s3:::my-bucket",
"Region": "us-east-1",
"Tags": {
"Environment": "Production",
"Department": "Engineering"
}
}
],
"Compliance": {
"status": "FAILED",
"RelatedRequirements": [
"CIS-1.2",
"PCI-DSS-3.0"
]
},
"Remediation": {
"Recommendation": {
"Text": "Remove public access from the S3 bucket.",
"Url": "https://docs.aws.amazon.com/s3/"
}
},
"RecordState": "ACTIVE"
}
Additional fields such as product-specific details, user-defined attributes, verification state, confidence, and criticality might also be included, though they are not required for exam preparation.
Understanding Severity Levels
Severity ratings in AWS Security Hub assist in prioritizing remediation efforts. Each finding is assigned a severity label accompanied by a numeric value on a scale of 0 to 100. For instance:
{
"Severity": {
"Label": "HIGH",
"Original": "8.0",
"Normalized": 80
}
}
A normalized value of 80 typically indicates a high-risk finding that demands prompt attention. Critical findings with normalized values nearing 100 require immediate action, while medium and low severities suggest issues that need attention but are not as urgent. Informational findings are generally recommendations or audit flags.
The Security Hub Console
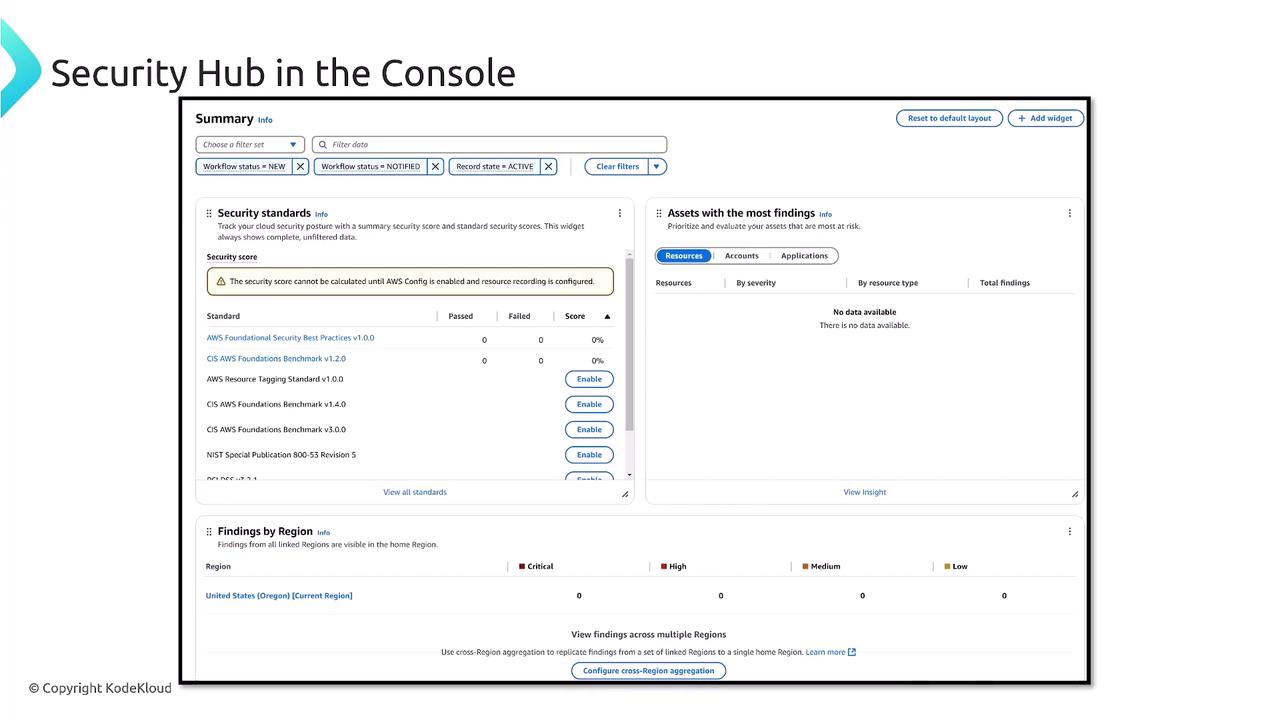
When you launch the AWS Security Hub console, you are presented with a dashboard that allows you to enable and configure various security standards. You may encounter standards such as:
- AWS Foundational Security Best Practices 1.0
- CIS AWS Foundational Benchmark (versions 1.2.0, 1.4, and 3.0)
- NIST publications
- PCI DSS checks
Once the findings are available, you can filter them by account, resource, application, or region. In addition, cross-region aggregation is configurable, ensuring streamlined monitoring across your entire AWS landscape.
Note
Security Hub's integration with AWS Config and EventBridge not only tracks configuration changes and compliance rule packs but also facilitates automated remediation using services like Lambda, Step Functions, or Systems Manager.
Thank you for exploring this lesson on AWS Security Hub. We look forward to guiding you through more advanced cloud security topics in future articles.
Watch Video
Watch video content