AWS Certified SysOps Administrator - Associate
Domain 4 Security and Compliance
Demo Setting up Secrets Manager with RDS
Welcome to this lesson on integrating AWS Secrets Manager with your RDS instances or clusters. AWS provides streamlined integration between these services, making it simple to securely manage your database credentials.
Modifying an RDS Cluster
Begin by navigating to the AWS RDS console. Select an RDS cluster from your list and click on it. Then, click the Modify button to start the configuration process.
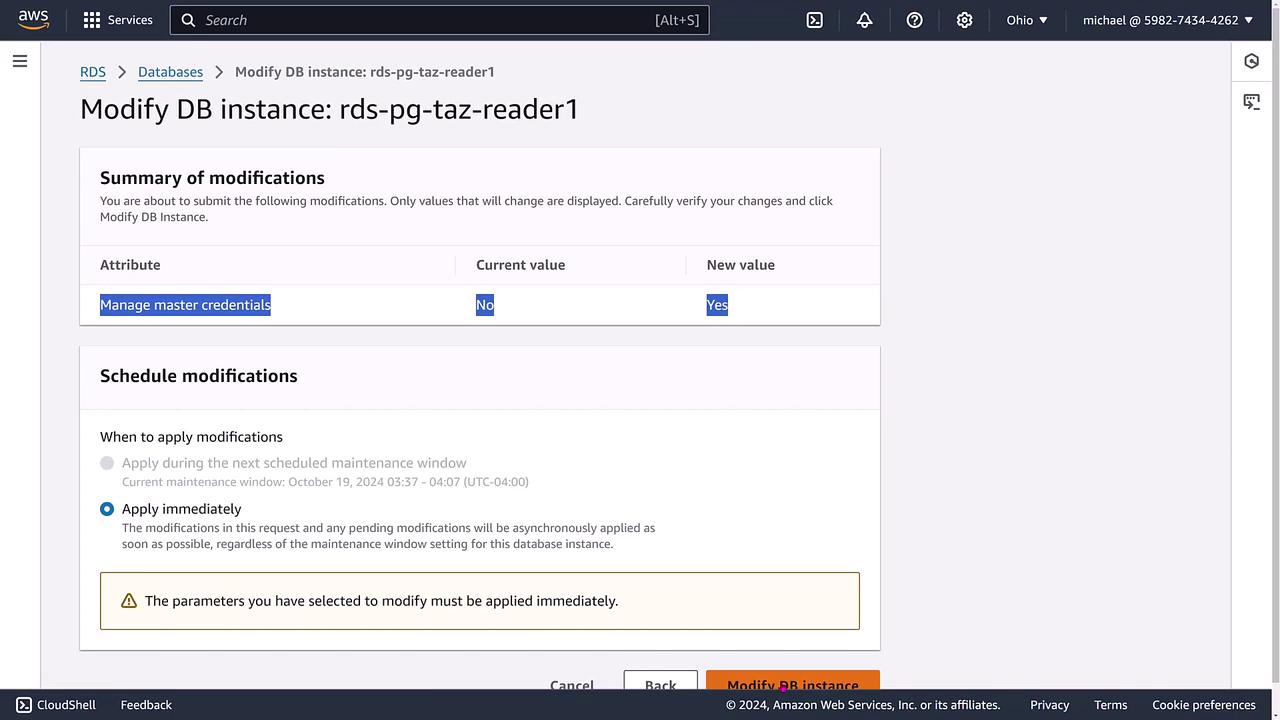
On the modification screen, locate the "Credentials Manager" (or similar) option. By default, the setting is "self-manage." Change it to "Manage in Secrets Manager." You can leave the default encryption key and instance size unchanged. Once your selections are complete, scroll down and click Continue. The console will display a summary of upcoming changes and prompt you to decide whether these changes should be applied during the maintenance window or immediately. For this demo, the changes are applied immediately.
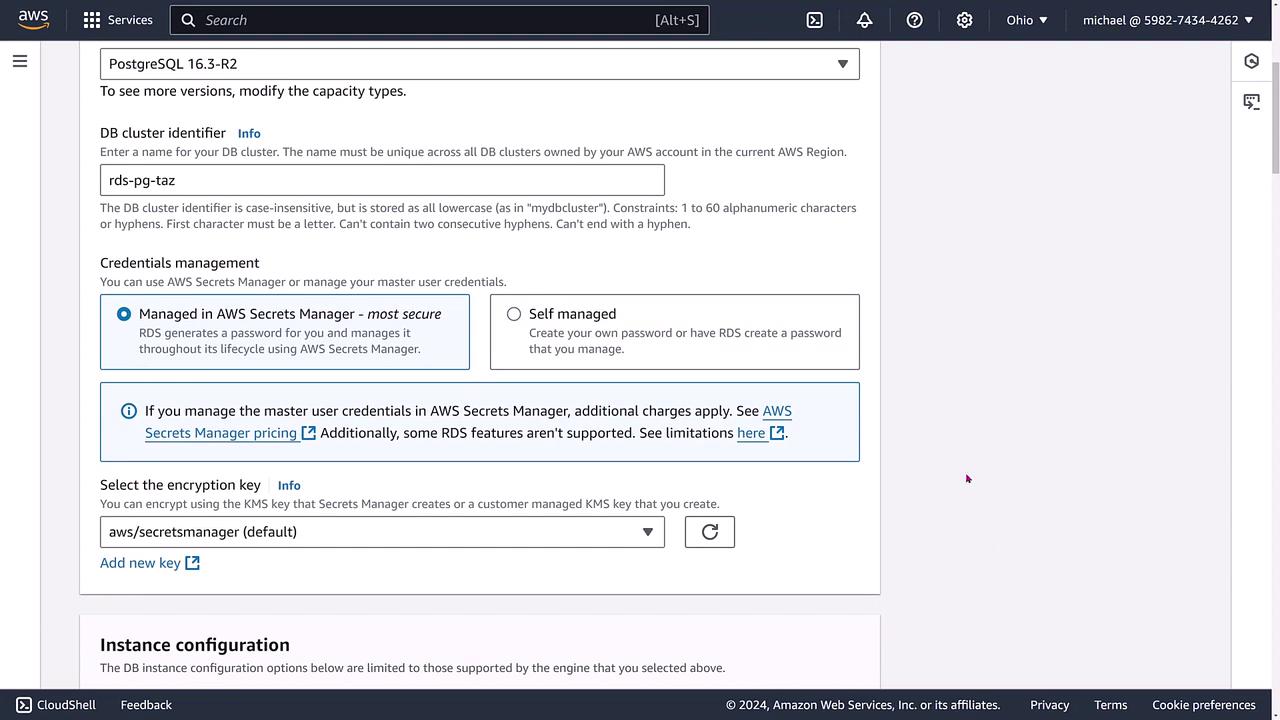
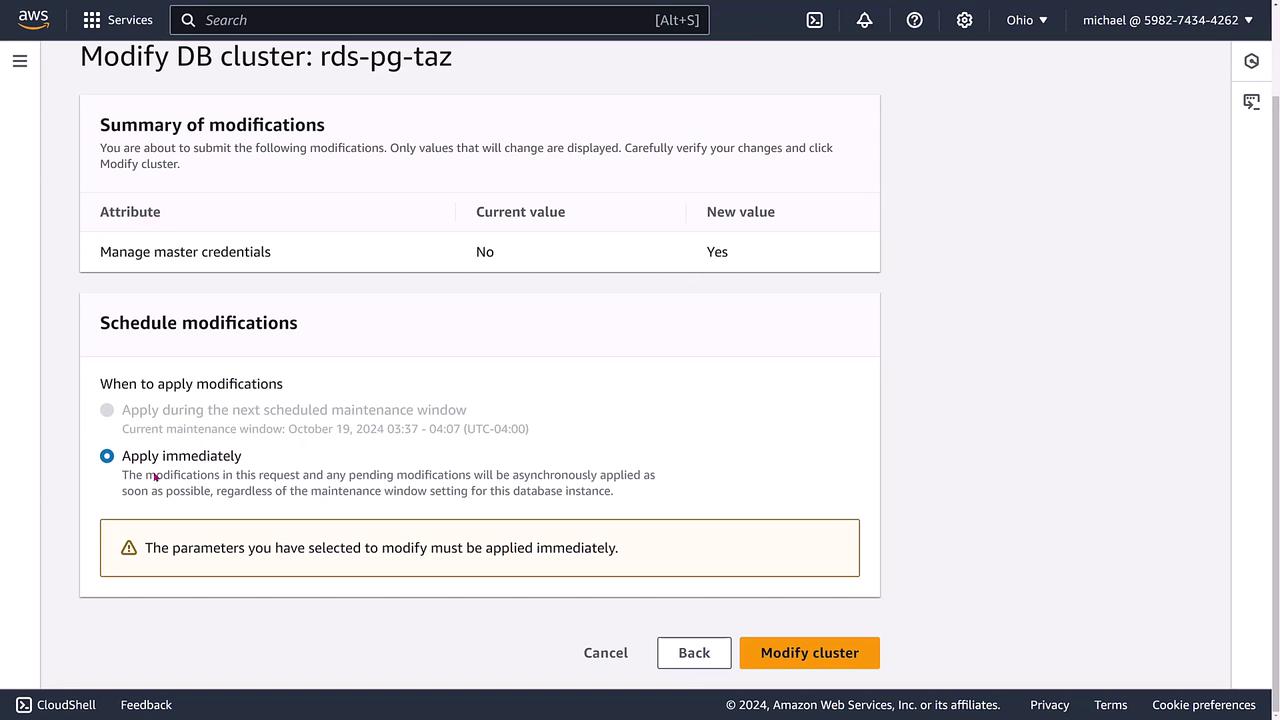
Review the summary carefully, then click Modify Cluster. The system will process the changes, providing a confirmation message once the modifications are successfully applied.
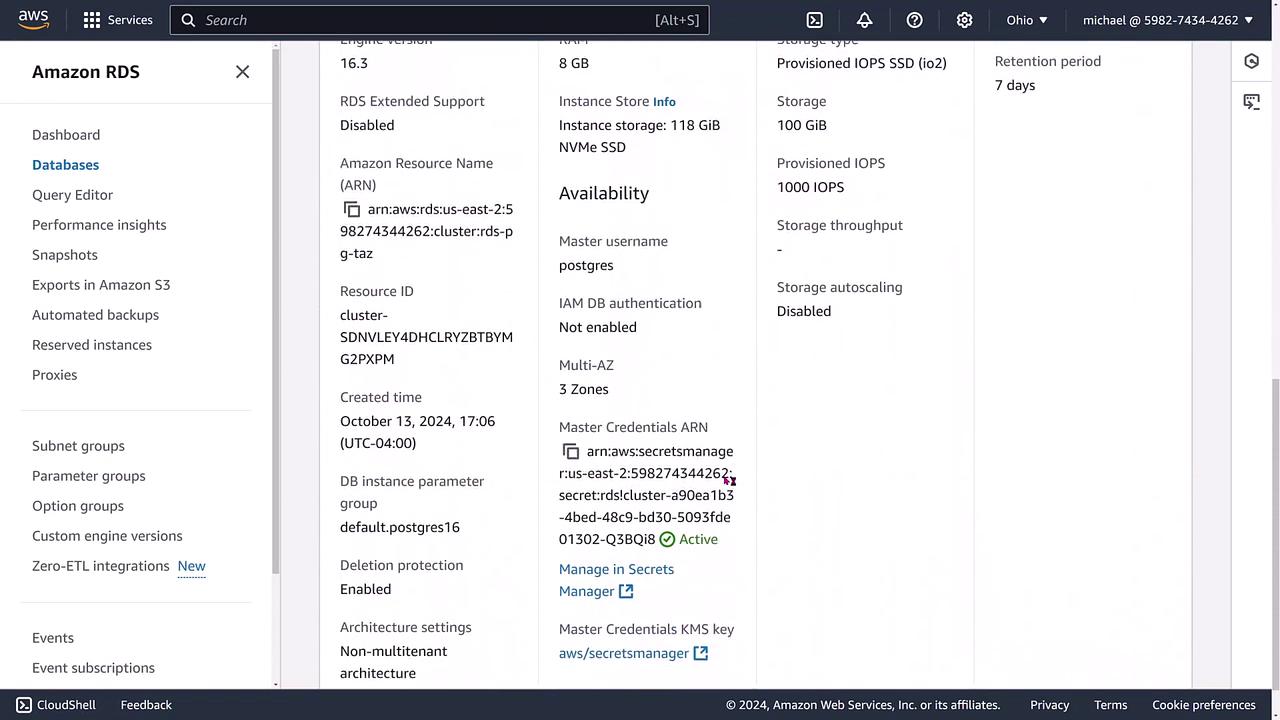
Next, verify that the integration with Secrets Manager is active. Go to the Configuration tab within your RDS cluster details page, and look for an entry indicating that Secrets Manager is now being used for credential management.
Tip
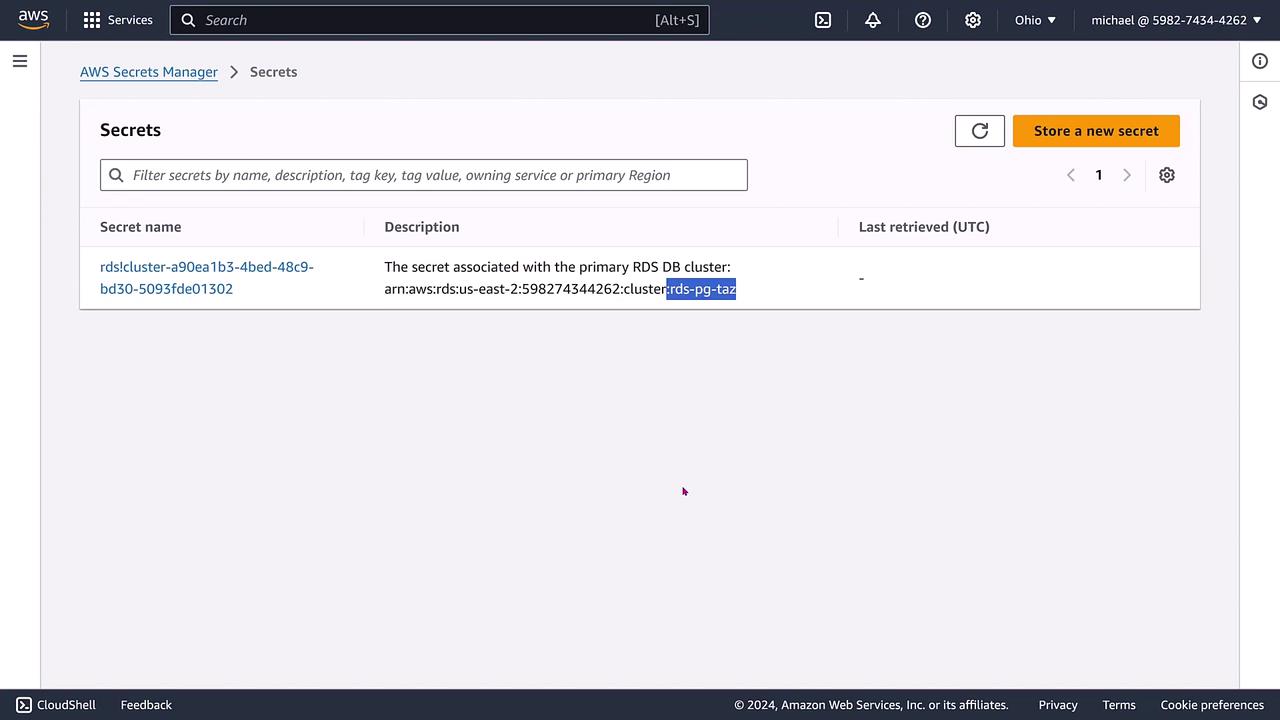
For further confirmation, navigate directly to Secrets Manager. You should see a secret associated with your RDS cluster, clearly identifiable by the cluster name.
Return to the RDS console and review the database details to ensure that the master credentials are being reset as part of the integration process.
Updating a Single Database Instance
The process for integrating Secrets Manager with a single database instance is similar. Select the individual database instance in the RDS console and click Modify. In the options presented, switch the credentials management setting to Secrets Manager without altering other settings. Scroll down and click Continue to apply the changes immediately.
After the modification is complete, verify that Secrets Manager integration is enabled by checking the Configuration tab. You can also follow the link to Secrets Manager from the instance details view.
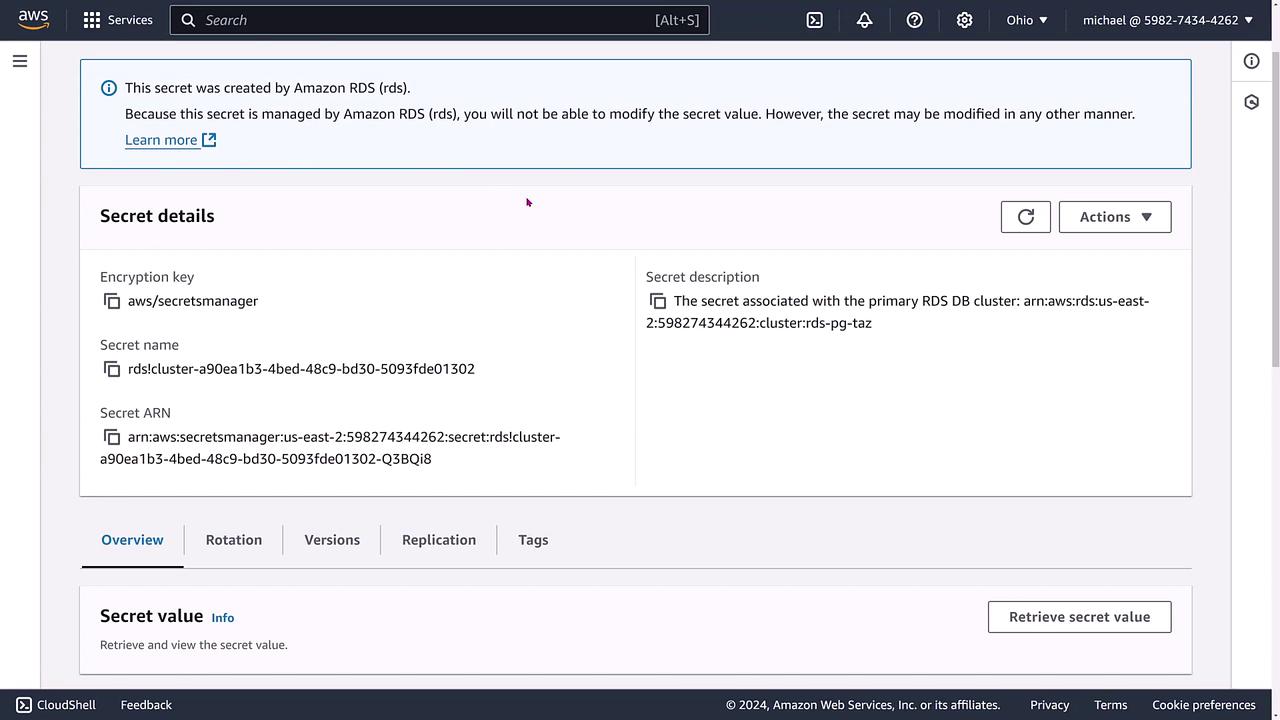
Keep in mind that because the secret was generated by RDS, its value can only be updated indirectly through RDS. Nevertheless, you can manage additional features such as secret rotation, version management, and cross-region replication from within Secrets Manager.
Key Information
By reviewing the Configuration section in the RDS console, you can confirm that your instance or cluster is actively using Secrets Manager. Options for immediate rotation and further secret management should now be readily available.
Conclusion
Enabling Secrets Manager integration with your RDS instance or cluster is straightforward. Simply modify your instance or cluster settings, change the credentials management option to Secrets Manager, and apply the changes. AWS seamlessly handles the credential resetting and secret linkage, ensuring your database credentials remain secure without extra manual intervention.
Thank you for reading this article. For more detailed information, consider exploring the following resources:
Watch Video
Watch video content
Practice Lab
Practice lab