AWS Certified SysOps Administrator - Associate
Domain 4 Security and Compliance
Encryption at Rest Options for AWS Services Overview
Welcome to this lesson on encryption-at-rest options for AWS. In today's discussion, we will explore the different methods to secure your data at rest and explain why robust encryption is a cornerstone of any comprehensive data protection strategy. By utilizing encryption, organizations can mitigate risks such as unauthorized access and data breaches while ensuring data integrity across all AWS services.
Key Takeaway
The AWS Key Management Service (KMS) is the central tool for managing encryption keys. It plays a vital role in safeguarding databases, EBS volumes, S3 buckets, and other storage resources across AWS.
AWS Key Management Service (KMS)
KMS is the primary service AWS provides for key management and encryption. Whether you are securing database disks, EBS volumes on EC2, or S3 data, KMS is indispensable. The diagram below demonstrates how users interact with KMS to manage keys for various services such as CMK, AWS SQS, S3, and EBS.
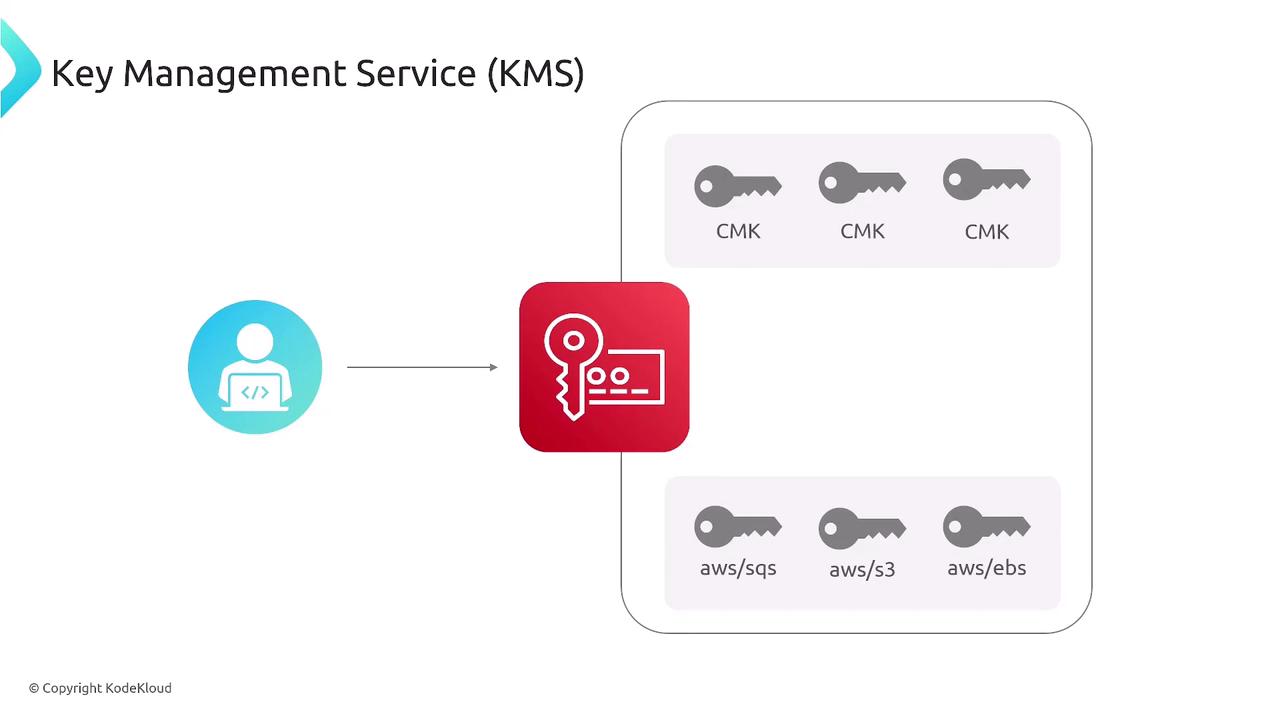
While AWS provides its Amazon Certificate Manager for managing SSL certificates, many AWS services come with integrated encryption features. For instance, when you enable encryption on EBS volumes, databases, or S3 buckets, you are inherently involving KMS to handle the encryption keys. This server-side encryption mechanism ensures that your data remains protected without compromising accessibility.
Amazon S3 Encryption Options
Amazon S3 offers multiple encryption options, each tailored to different use cases. S3 supports:
- KMS-Managed Encryption: Utilizes either single or dual key management mode.
- Native Server-Side Encryption: An option that predates KMS but continues to ensure robust encryption at rest.
The image below showcases the default encryption settings in the Amazon S3 interface, where you can select server-side encryption options with various key management configurations.

For most scenarios, KMS-driven encryption is preferred due to the enhanced control it offers over encryption keys. Additionally, AWS supports client-side encryption, which allows data to be encrypted before it is transmitted to S3.
Encryption Across AWS Storage Services
Almost every AWS storage service employs KMS for at-rest encryption. This includes:
- Amazon Elastic File System (EFS)
- Amazon Elastic Block Store (EBS)
- Storage systems used with services like EMR, EKS, and ECS
Even the Relational Database Service (RDS), which runs on EC2 instances configured as a managed database solution, leverages KMS for secure storage. The following diagram highlights the relationship between EC2 and EBS, emphasizing how encryption is applied throughout the data flow.
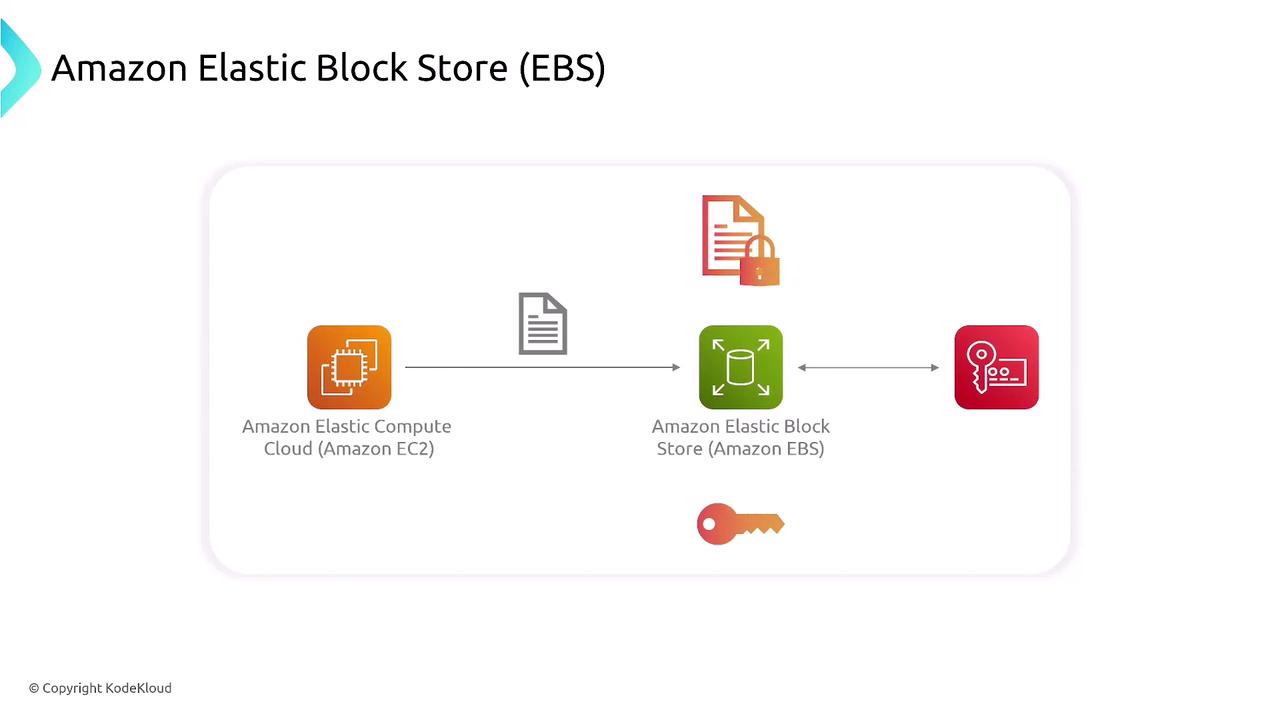
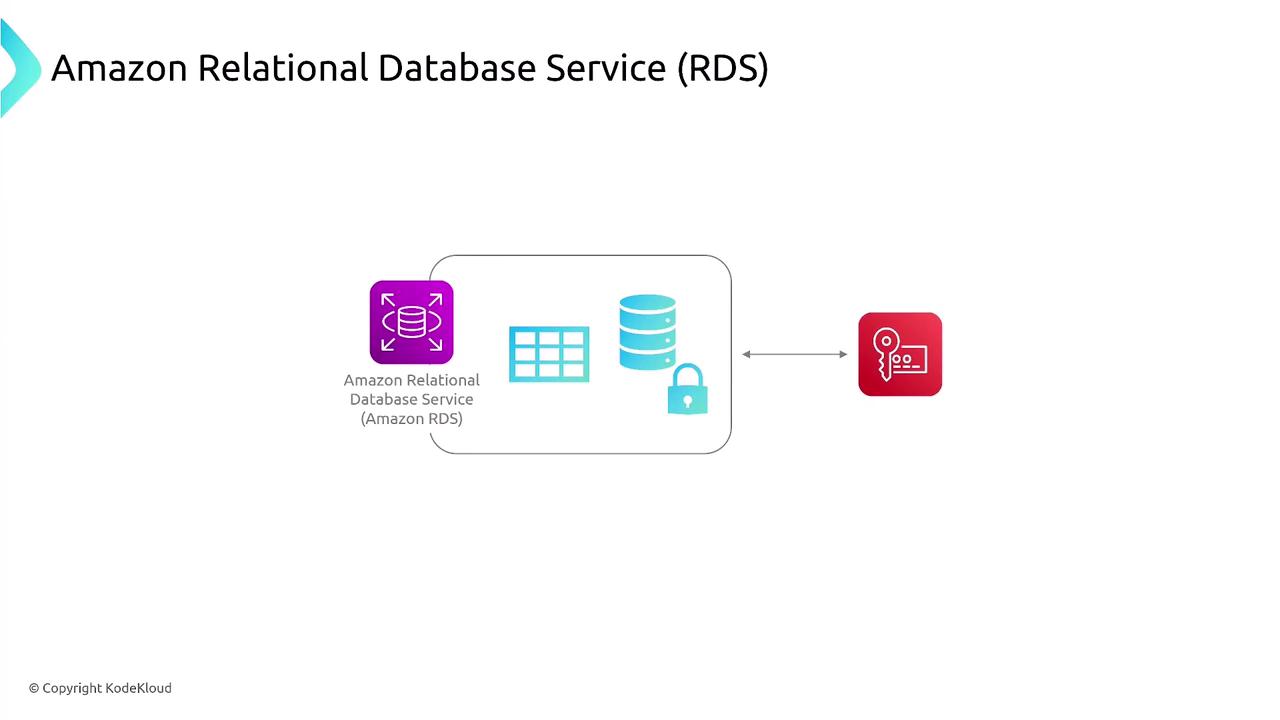
Similarly, database services such as RDS, Aurora, and DynamoDB depend on EBS encryption via KMS to protect data at rest. The diagram below captures the security architecture of Amazon RDS, illustrating how key management integrates with database components to secure your data.
Summary
In summary, the AWS KMS is the linchpin of AWS's encryption-at-rest strategy. It provides a centralized and efficient way to manage encryption keys across a wide variety of AWS storage and database services. In the next lesson, we will further explore advanced data protection strategies and additional methods to secure your AWS infrastructure.
For more detailed information on AWS encryption and key management, check out the AWS KMS Documentation.
Happy securing!
Watch Video
Watch video content