IAM: The Foundation of AWS Security
At the heart of AWS security is Identity and Access Management (IAM). IAM controls who can access resources and what actions they can perform, addressing the fundamental question: “Who can access what, and how can that access be securely managed?” This is achieved through well-defined IAM policies—JSON documents that explicitly allow or deny permissions. By default, access is implicitly denied until explicitly granted. IAM policies protect users, groups, roles, and AWS services, while additional measures like Multi-Factor Authentication (MFA) and the principle of least privilege further strengthen security.
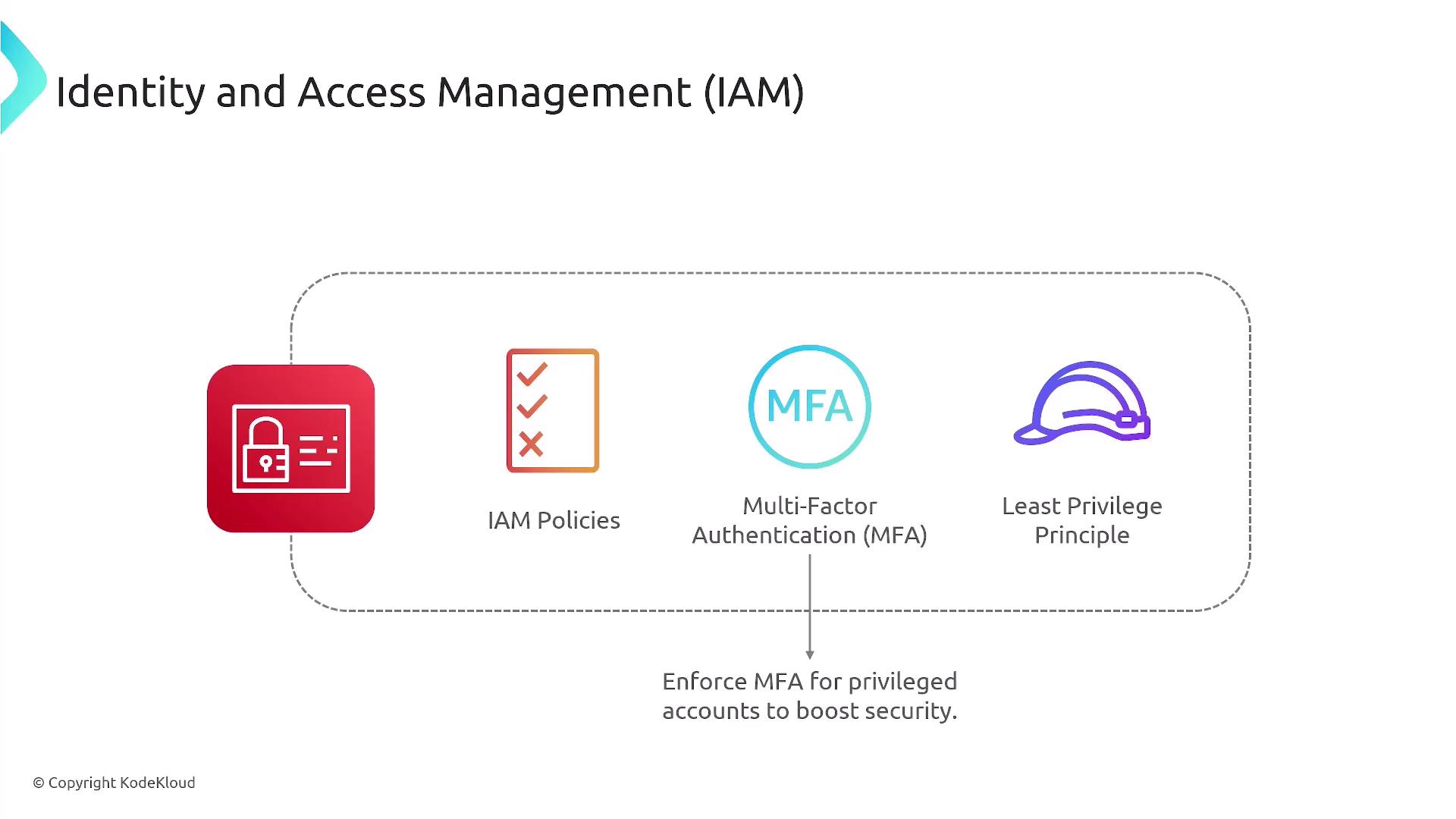
All AWS security controls start with a correctly configured IAM setup.
Network Protection Strategies
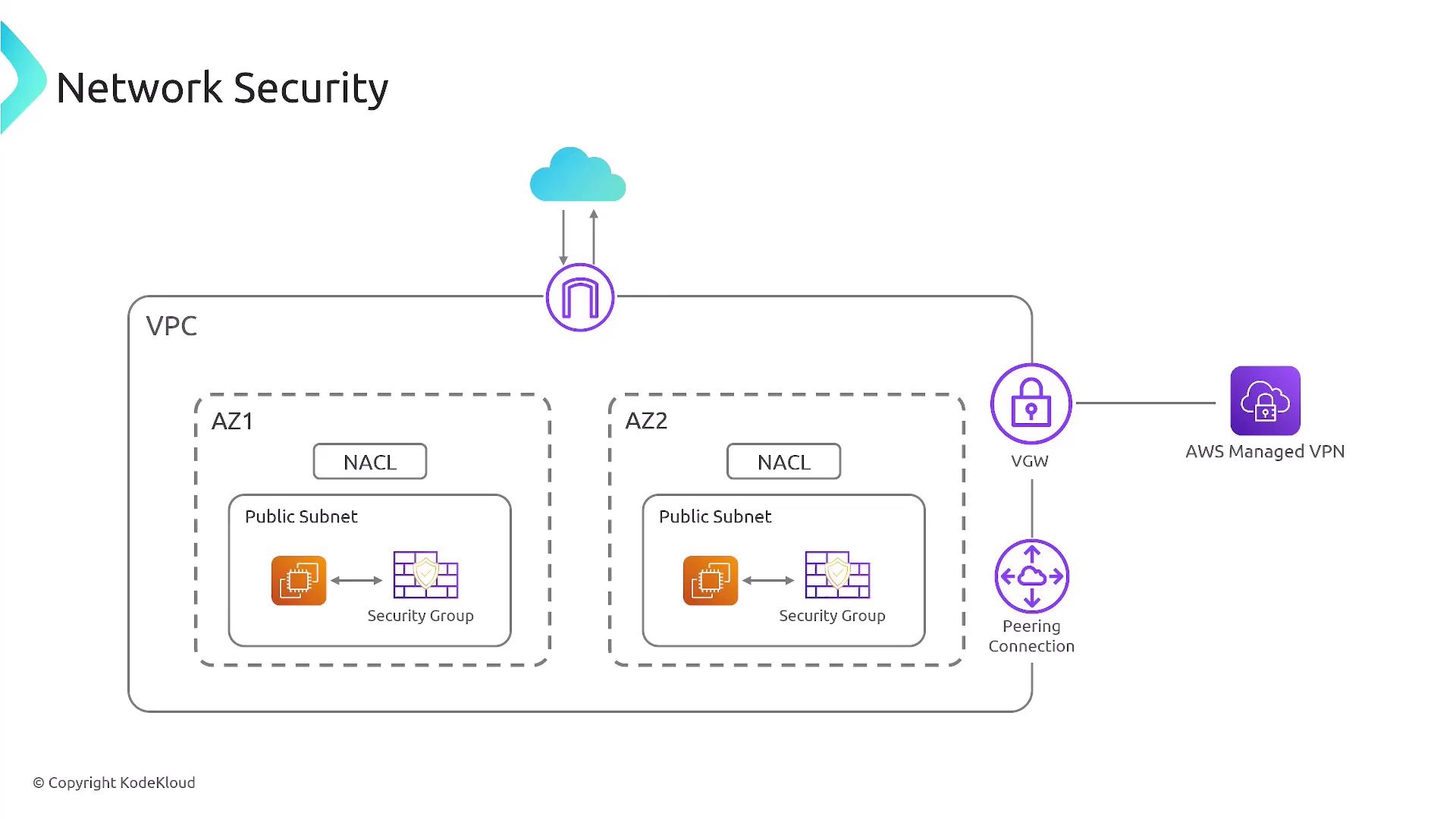
AWS network security is built upon the Virtual Private Cloud (VPC) construct, which allows you to isolate resources within a defined network space. Within a VPC, you design subnets that benefit from multiple layers of firewall protection:- Security Groups: Act as stateful firewalls to control inbound and outbound traffic.
- Network Access Control Lists (NACLs): Provide stateless, subnet-level security.
Data Protection Strategies
Data protection in AWS covers both data at rest and data in transit:- Data at Rest:
- AWS supports encryption for stored data on hard drives, databases, and S3 buckets.
- Services like AWS Key Management Service (KMS) and AWS Certificate Manager ensure that only authorized users with the proper keys can access the information.
- Data in Transit:
- AWS secures data moving across networks, safeguarding it from interception and unauthorized access.
Using encryption for both data at rest and in transit is essential for maintaining confidentiality and integrity.
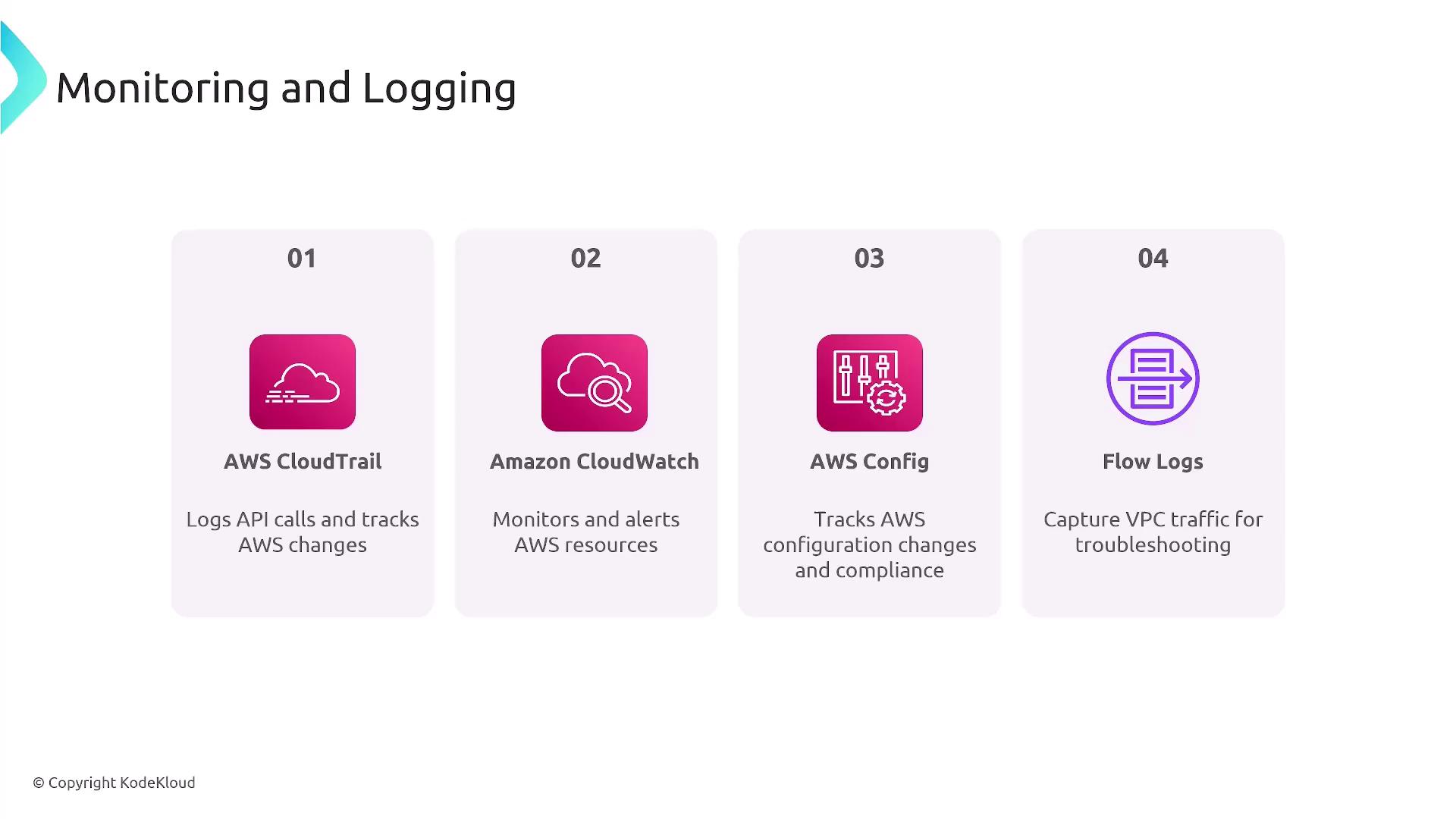
Monitoring and Logging
Effective monitoring and logging are crucial for identifying and addressing security issues. AWS offers a suite of tools for comprehensive oversight:- CloudTrail: Tracks all API calls within your AWS account.
- CloudWatch: Collects metrics and logs to provide insights into resource performance and operational health.
- Config: Monitors configuration changes and alerts you to unauthorized modifications.
- VPC Flow Logs: Captures IP traffic details across network interfaces in your VPC.
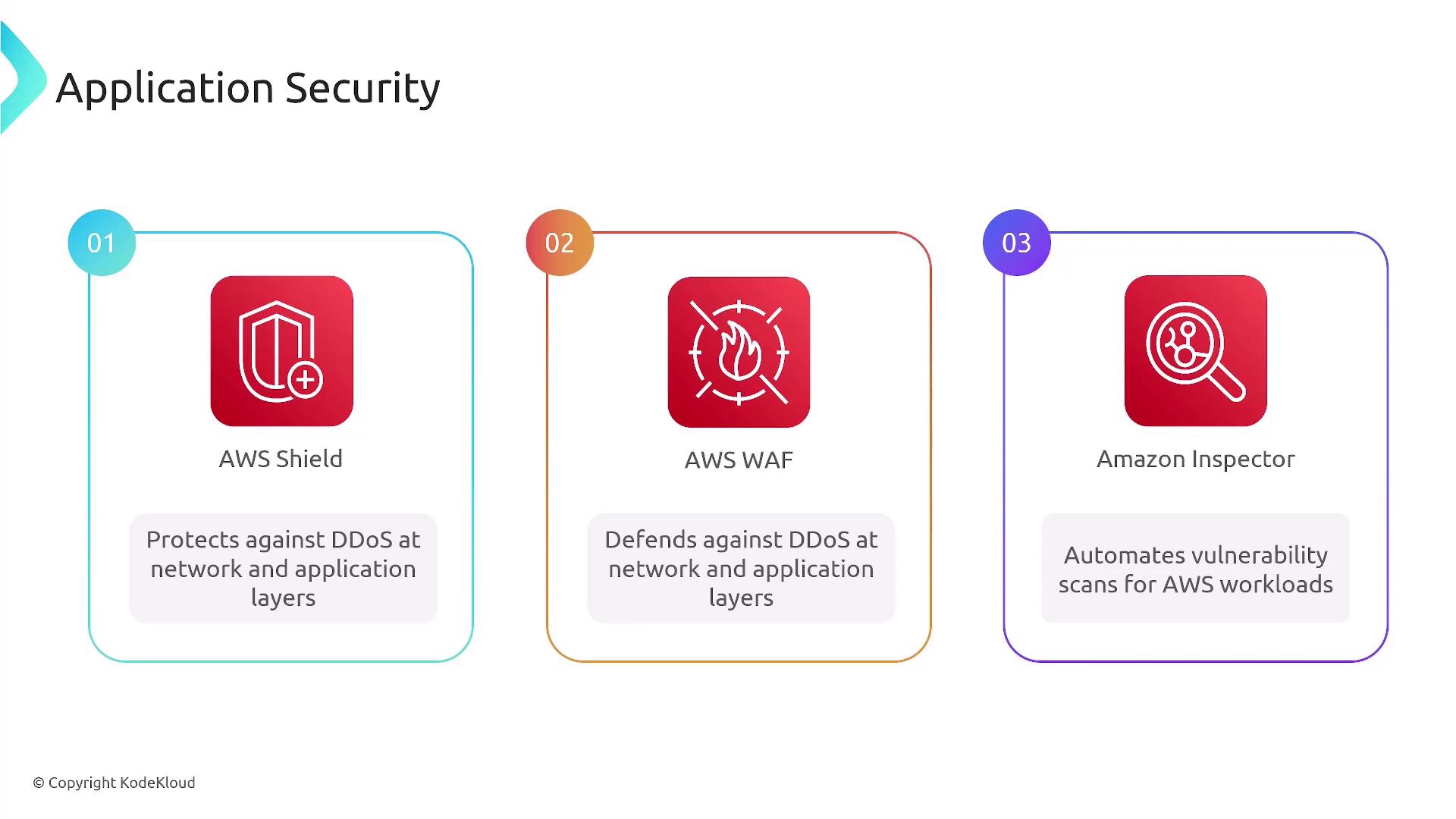
Application Security
AWS addresses application-level security through a range of dedicated services:- Shield: Offers robust DDoS protection for your applications.
- Shield Advanced: Provides enhanced DDoS mitigation features with additional benefits.
- Web Application Firewall (WAF): Guards against common web exploits such as SQL injection and cross-site scripting by using custom rules.
- Inspector: Automates vulnerability assessments for applications, Lambda functions, containers, and virtual machines.
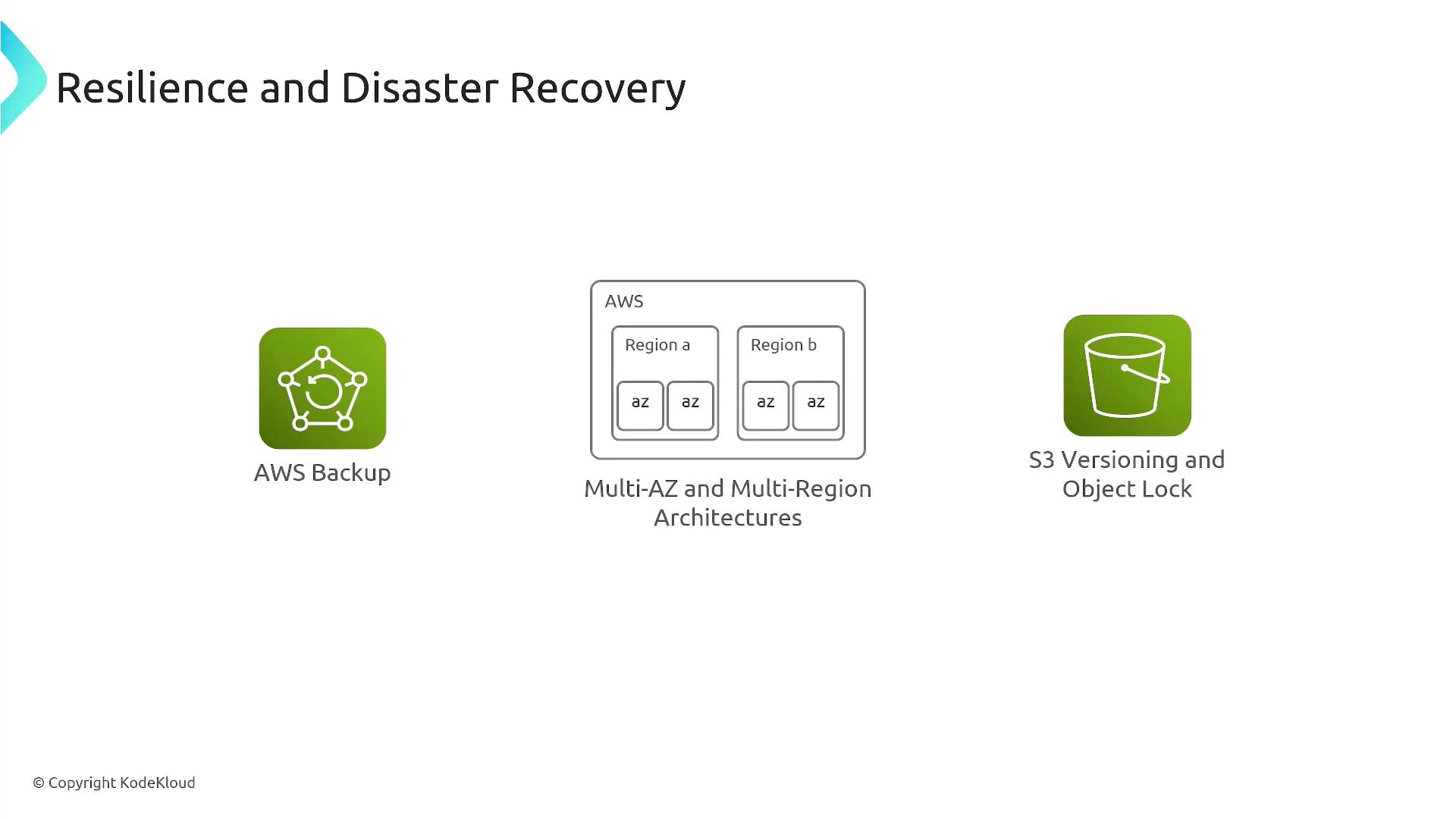
Resiliency and Recovery
AWS provides a highly resilient infrastructure with powerful recovery features:- AWS Backup: Allows you to implement centralized backup policies across regions and availability zones.
- Multi-AZ and Multi-Region Architectures: Enhance data availability and durability.
- S3 Versioning and Governance Locks: Offer an extra layer of protection by preserving historical data and preventing accidental deletions.
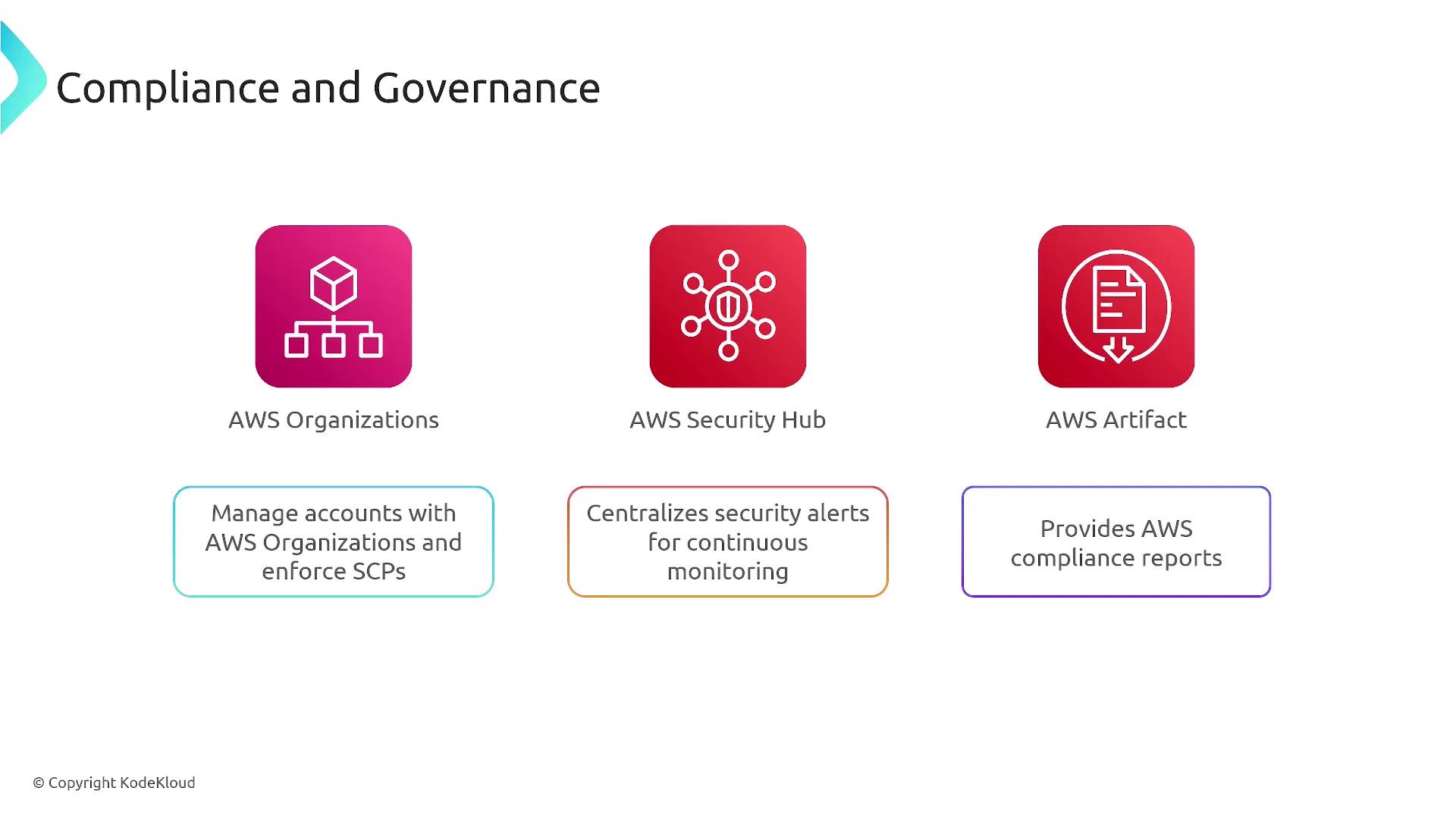
Additional Security Strategies
Beyond the core protection mechanisms, AWS supports a wide array of security strategies. Regular vulnerability assessments, patch management, and security awareness training are vital complements to AWS security services. Although AWS does not provide security awareness training, integrating such programs into your overall security plan is highly recommended.