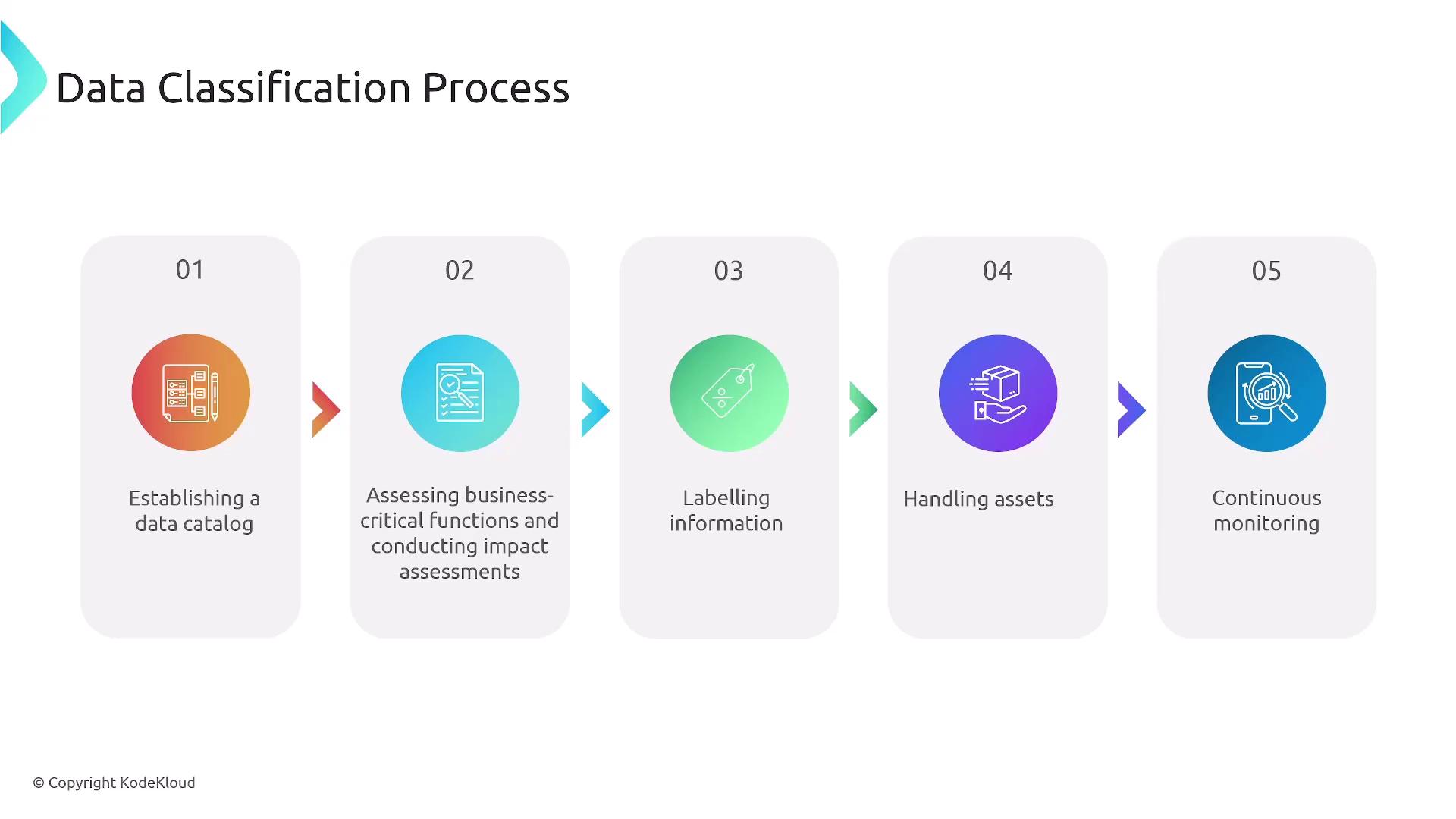
A typical data classification procedure includes:
- Establishing a comprehensive data catalog
- Cataloging and inventorying data assets
- Evaluating business-critical functions
- Conducting impact assessments on potential data breaches or misuse
Once assessed, data is labeled appropriately and secured with tailored controls. Continuous monitoring ensures ongoing protection against unauthorized access or data compromise.
- Whether data should be treated as confidential
- If data integrity is essential
- The implications of data alteration
Additionally, consider business continuity requirements. Ask whether data can be recreated easily if lost, or if its recovery is time-consuming and costly. This analysis is vital for effectively allocating security resources.

Best Practices for Data Protection
Best practices such as those presented in the AWS Well-Architected Framework help organizations make the right trade-offs by focusing on the critical security pillar. Fundamental principles include:- Encrypting data both in transit and at rest
- Restricting direct access to raw data so that only authorized personnel can handle sensitive information
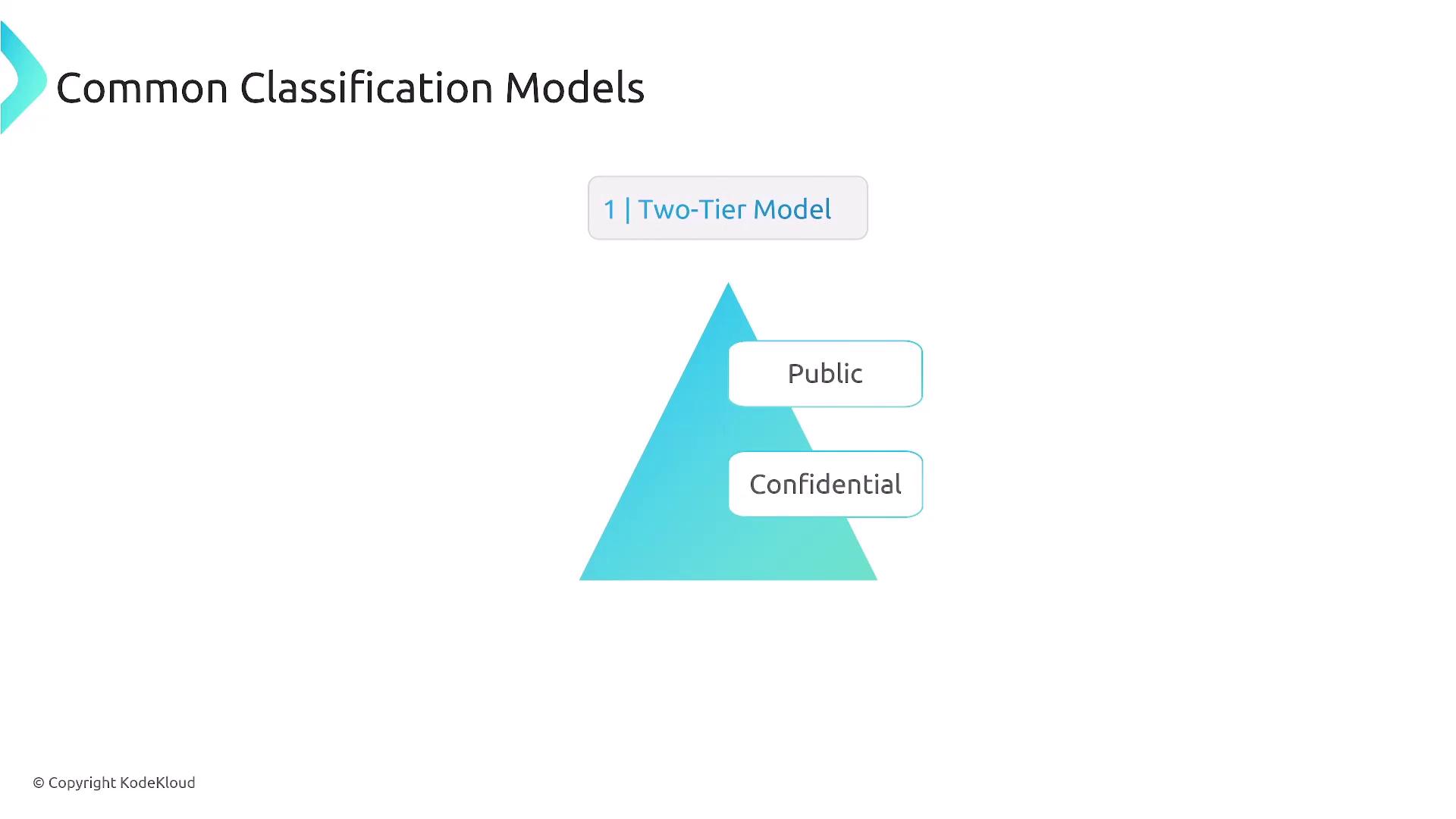
Data Classification Models
Data classification models vary from simple to sophisticated, depending on organizational needs:- Two-Tier Model: Differentiates between public and confidential data.
- Three- or Four-Tier Models: May include categories such as public, private, confidential, and highly restricted or legally protected data.
- Five-Tier Model: Segregates data into community sharing, public release, internal use, confidential, and super-restricted data.
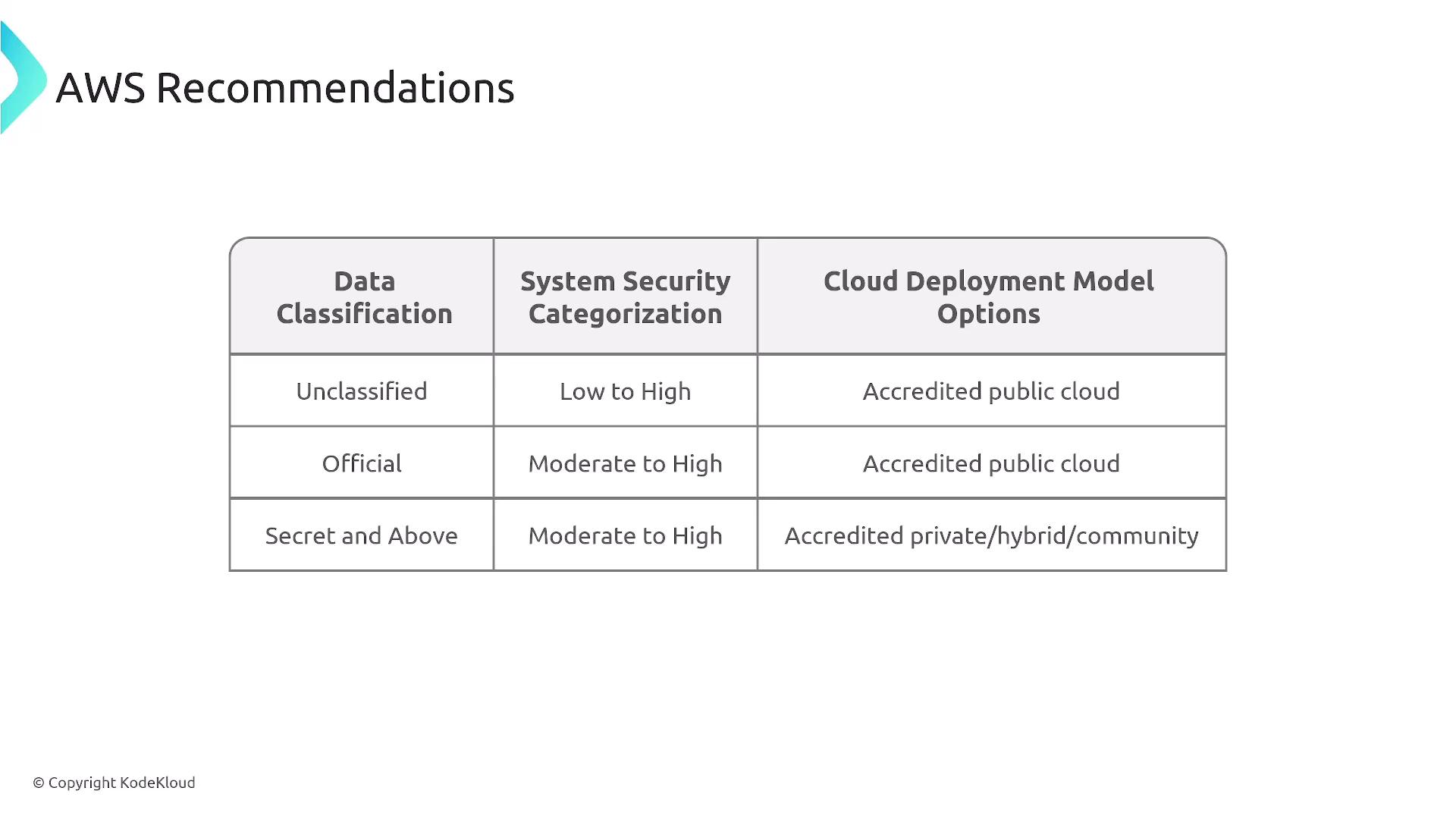
AWS Services Supporting Data Classification
AWS provides a suite of services to facilitate data classification and protection:- AWS Macie employs machine learning to identify Personally Identifiable Information (PII) in S3 buckets.
- AWS Glue offers robust data cataloging capabilities for efficient data management.
- Native tools within AWS database services (such as Neptune and RDS) enable rapid data discovery and classification.
- Software and hardware mechanisms for data at rest
- AWS Certificate Manager for secure data in transit
- AWS Identity and Access Management (IAM) and AWS Organizations to manage access control in multi-account environments
- CloudTrail, AWS Config, and CloudWatch for auditing and logging
- GuardDuty and Inspector to enhance security detection
- Systems Manager for patching and maintenance
- AWS WAF and Shield Advanced for robust web application and DDoS protection
AWS provides an integrated ecosystem designed to streamline data classification and security:
- Data Cataloging: AWS Glue
- Data Protection: Macie, Certificate Manager
- Access Management: IAM, AWS Organizations
- Monitoring and Logging: CloudTrail, CloudWatch, Config