AWS Certified SysOps Administrator - Associate
Domain 4 Security and Compliance
Importance of Network Defense
Welcome back, students.
In this article, we explore the vital role of network defense within the AWS ecosystem. As AWS nears its 20-year milestone, its robust and scalable network defense mechanisms have only grown more efficient. With AWS providing real-time traffic visibility across your account, you can actively block and filter a broad range of threats. This centralized control not only enables the management of firewall rules and aggregation of security events but also ensures strict policy compliance, especially when working with AWS Organizations.
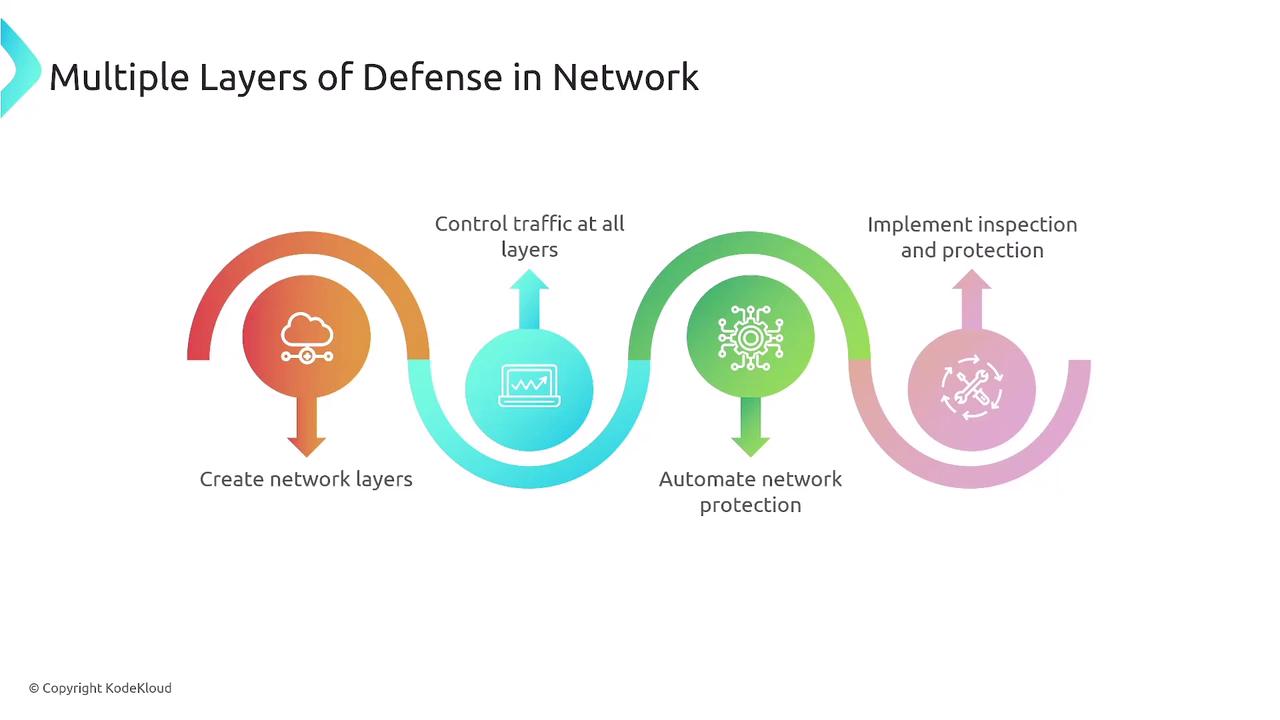
Multiple Layers of Defense
One of the core principles in network security is defense in depth, which involves implementing multiple layers of protection. Almost every application workload relies on network connectivity, whether through the internet or a private network. Thus, it is essential to design robust security measures at every level.
When you open a port for internet access, you must secure that entry point through careful control and traffic filtering. The objective is to direct and inspect traffic from the IP layer up to the application layer while automating detection processes so that defense does not rely solely on human intervention.
Network Layering in AWS
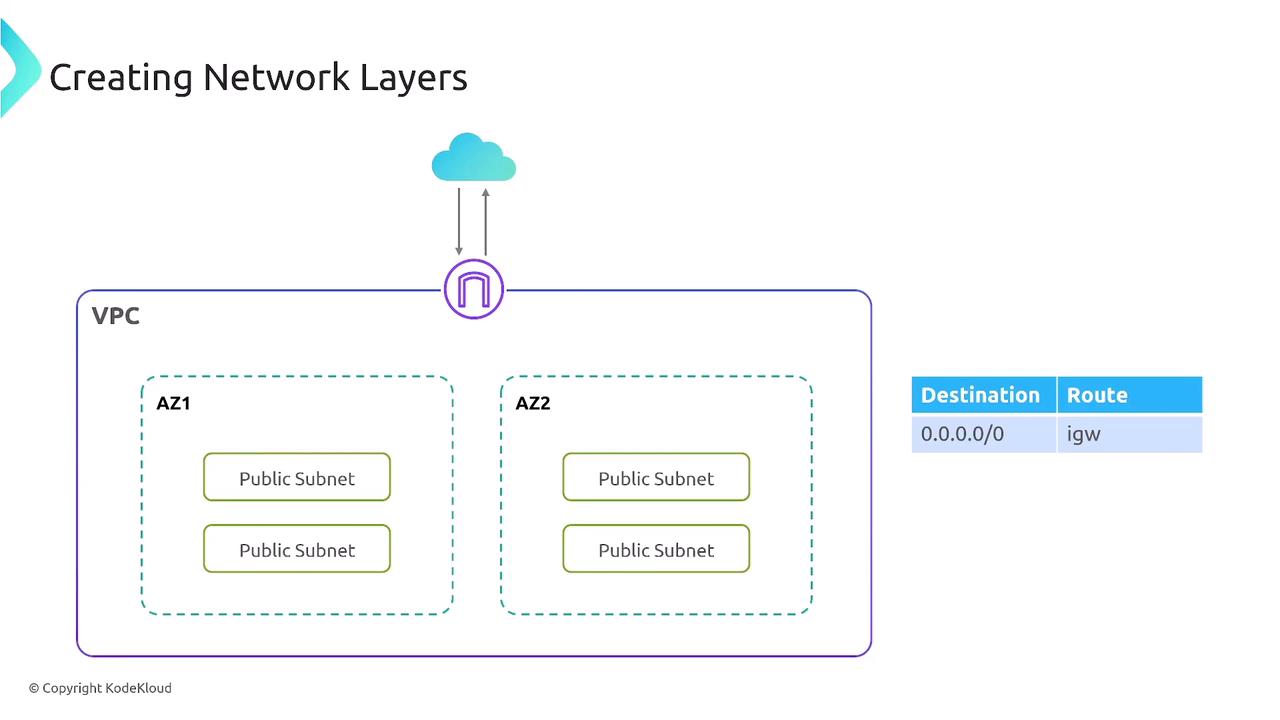
Network defense in AWS begins with the Virtual Private Cloud (VPC). Within a VPC, creating subnets allows you to manage both public and private traffic routes. The network gateway directs traffic in and out, giving you the flexibility to configure direct, indirect, or no internet access for your workload.
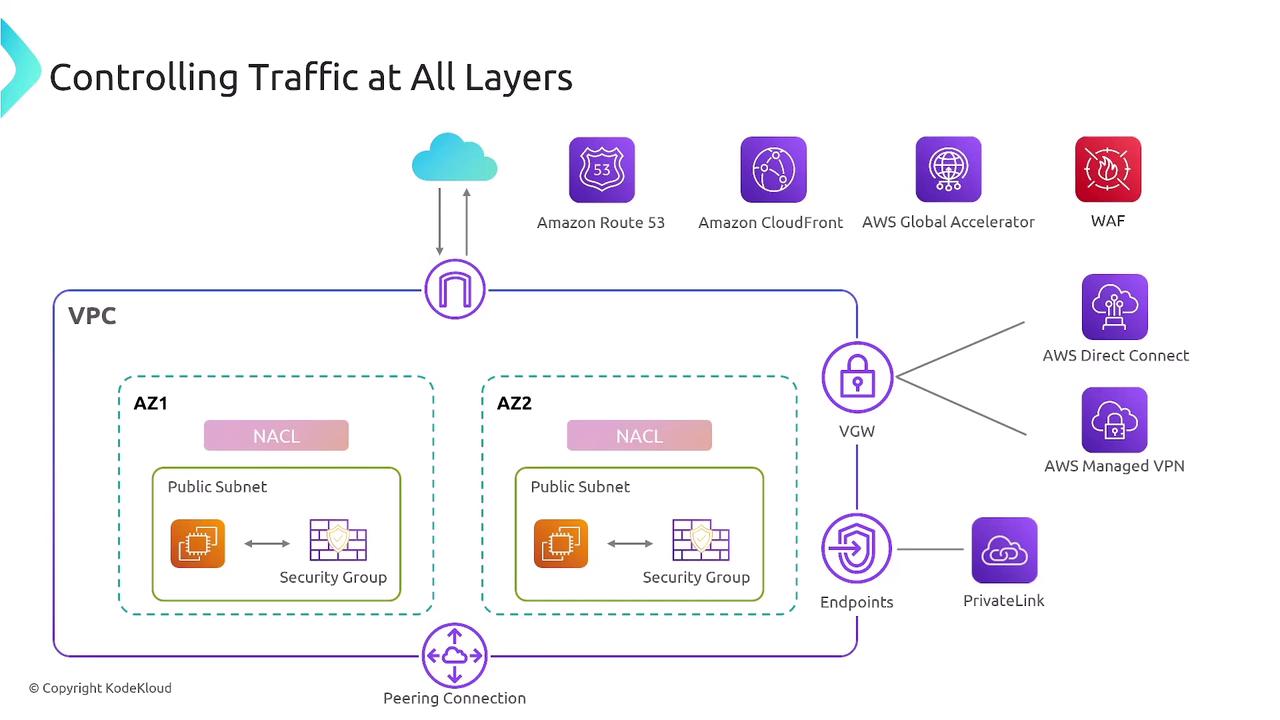
Key considerations for securing your network include:
- Configuring Network Access Control Lists (NACLs) on your subnets
- Implementing stateful firewalls (Security Groups) for each instance with network connectivity
These security measures ensure minimal port exposure while enabling additional protection layers, such as a web application firewall. In addition, VPC endpoints powered by AWS PrivateLink keep traffic private when accessing AWS services such as Amazon S3 or DynamoDB.
Enhancing Network Security with Encryption
To secure private connections, you can use a Virtual Private Network (VPN) or enhance AWS Direct Connect with MACsec for encryption. Although Direct Connect improves capacity and reduces costs, it does not provide encryption by default; VPN remains the primary choice for encrypted communication.
AWS offers a variety of services designed to offload and redirect traffic while defending against Distributed Denial-of-Service (DDoS) attacks.
Automating Network Protection
Automating network protection is key to staying ahead of emerging threats. AWS provides both built-in services and customizable remediation strategies to assist with this. Some services to consider include:
- AWS Shield Advanced
- AWS Web Application Firewall (WAF)
- AWS CloudFormation or Systems Manager for automated remediation
- Resource Access Manager for controlled resource sharing
- AWS GuardDuty for continuous threat monitoring
- VPC Flow Logs for capturing and analyzing IP traffic via Amazon S3 or CloudWatch Logs
Note
GuardDuty can work in tandem with flow logs to alert you of potential threats and assist in mitigating them.
Additionally, features such as VPC traffic mirroring allow you to replicate traffic from specific segments to external security tools for in-depth content inspection, threat monitoring, and troubleshooting.
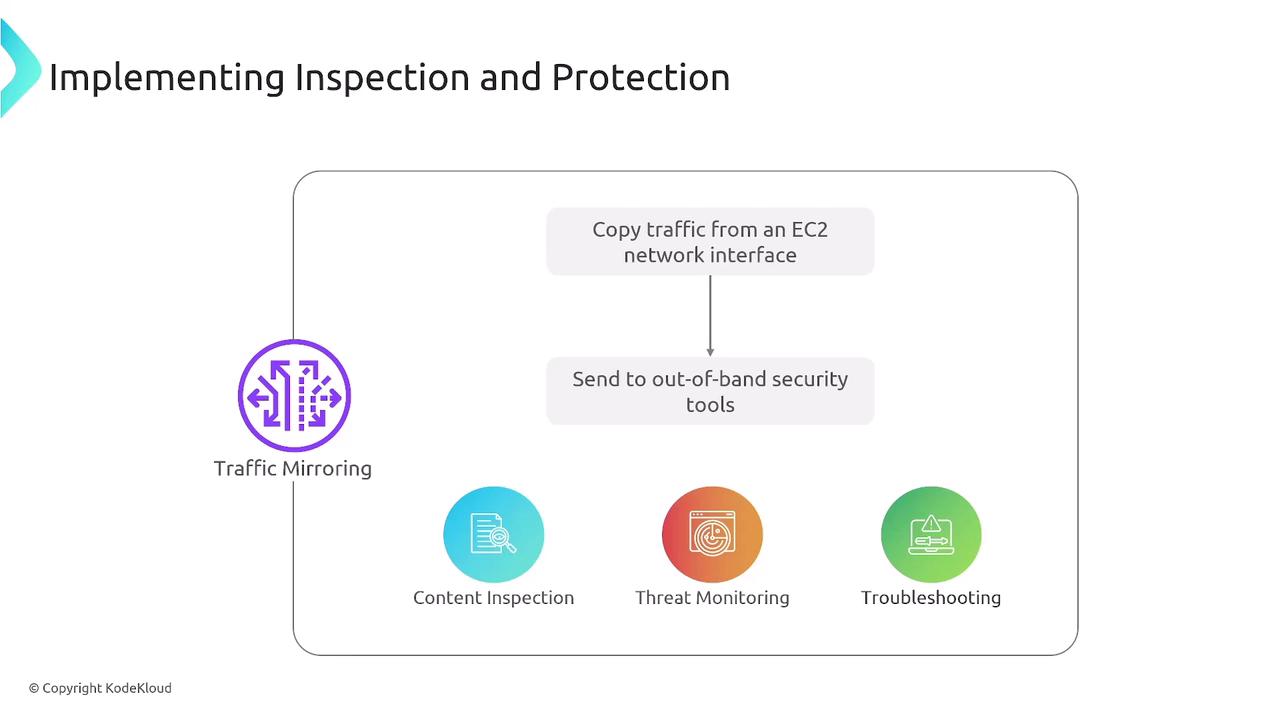
AWS Network Defense Services
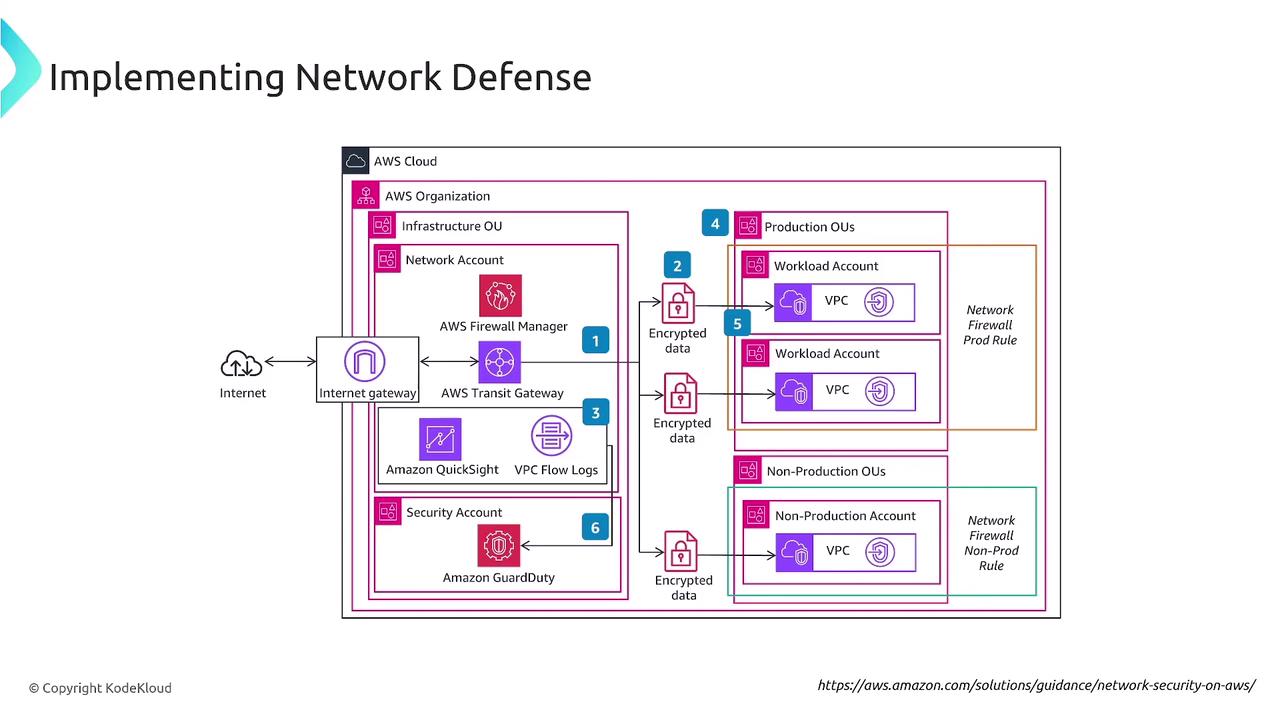
AWS provides a comprehensive suite of network defense services, including:
- AWS Firewall Manager for centralized management of firewall policies
- VPC Peering and Transit Gateway for controlling inter-VPC traffic flow
- AWS GuardDuty and additional monitoring services for proactive threat detection
These services work together to ensure that your network remains secure by actively filtering traffic and enforcing best practices for network security.
Conclusion
The components discussed in this article are integral to robust network defense as emphasized in the AWS SysOps exam. By implementing multiple layers of security, automating protective measures, and leveraging AWS's rich portfolio of security services, you can fortify your network infrastructure against evolving threats.
We hope this discussion has provided you with valuable insights into building a resilient network defense strategy. See you in the next article.
Watch Video
Watch video content