AWS Certified SysOps Administrator - Associate
Domain 5 Networking and Content Delivery
Common Misconfigurations and Troubleshooting VPC Issues
Welcome to this comprehensive guide on troubleshooting common misconfigurations in Virtual Private Clouds (VPCs). In this lesson, we’ll explore key components such as VPCs, subnets, internet gateways, routing tables, IP addressing, firewalls, Network Access Control Lists (NACLs), and security groups. We’ll also review potential pitfalls with NAT gateways and VPC endpoints. Follow along as we break down each issue step by step.
1. Routing Issues
Routing misconfigurations are a frequent cause of connectivity problems. Consider a scenario where you launch a new web server in a public subnet, yet it cannot access the internet. Two key routing aspects must be reviewed:
Public IP Address:
Ensure your web server has a public IP address. This can be auto-assigned via the subnet's DHCP settings or manually attached as an Elastic IP. Without a public IP, the instance won’t be able to reach the internet.Route Table Configuration:
The subnet’s route table must include appropriate entries. For local traffic, you might see a configuration like this: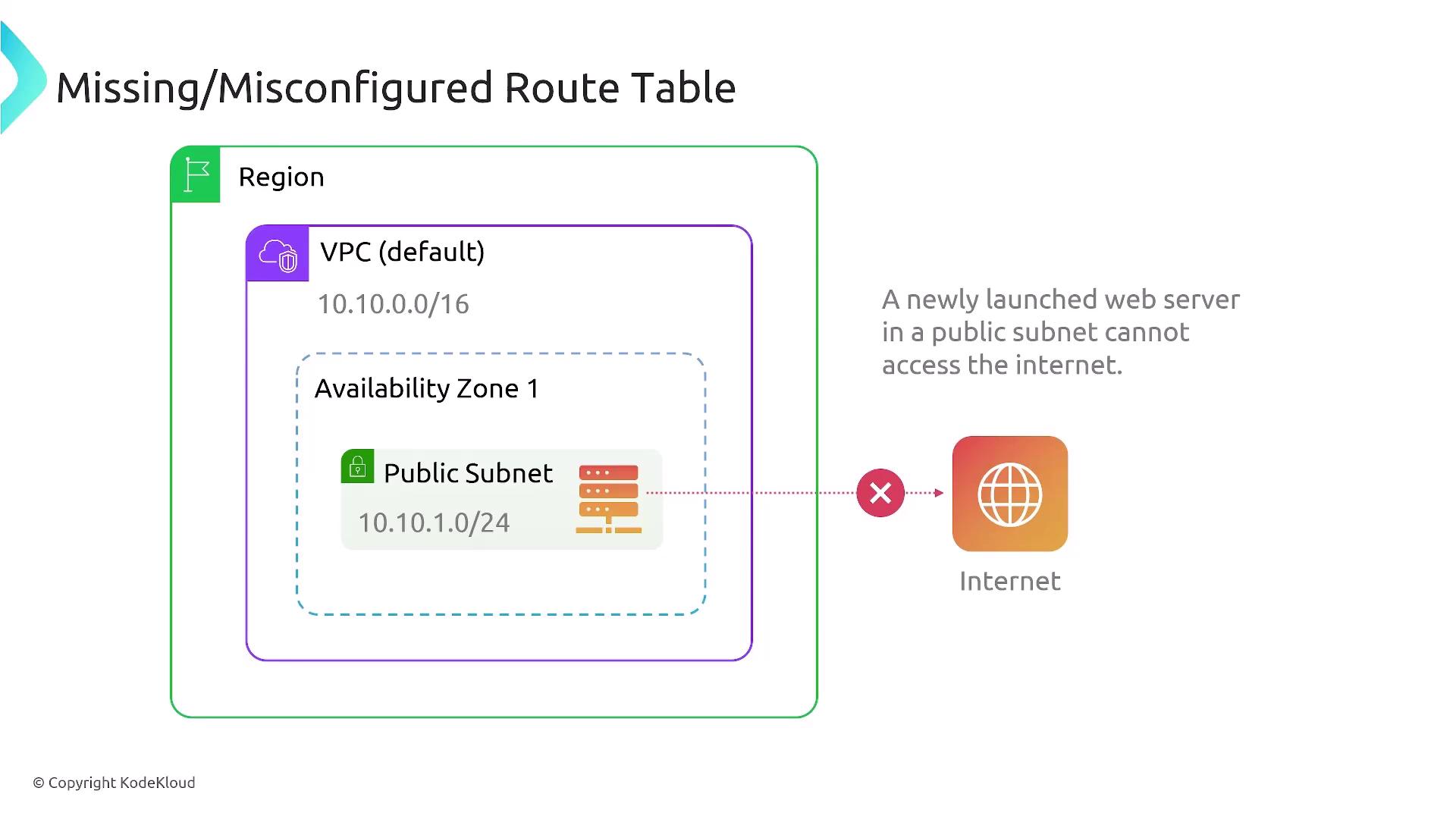
For internet-bound traffic, a default route pointing to the internet gateway is required:
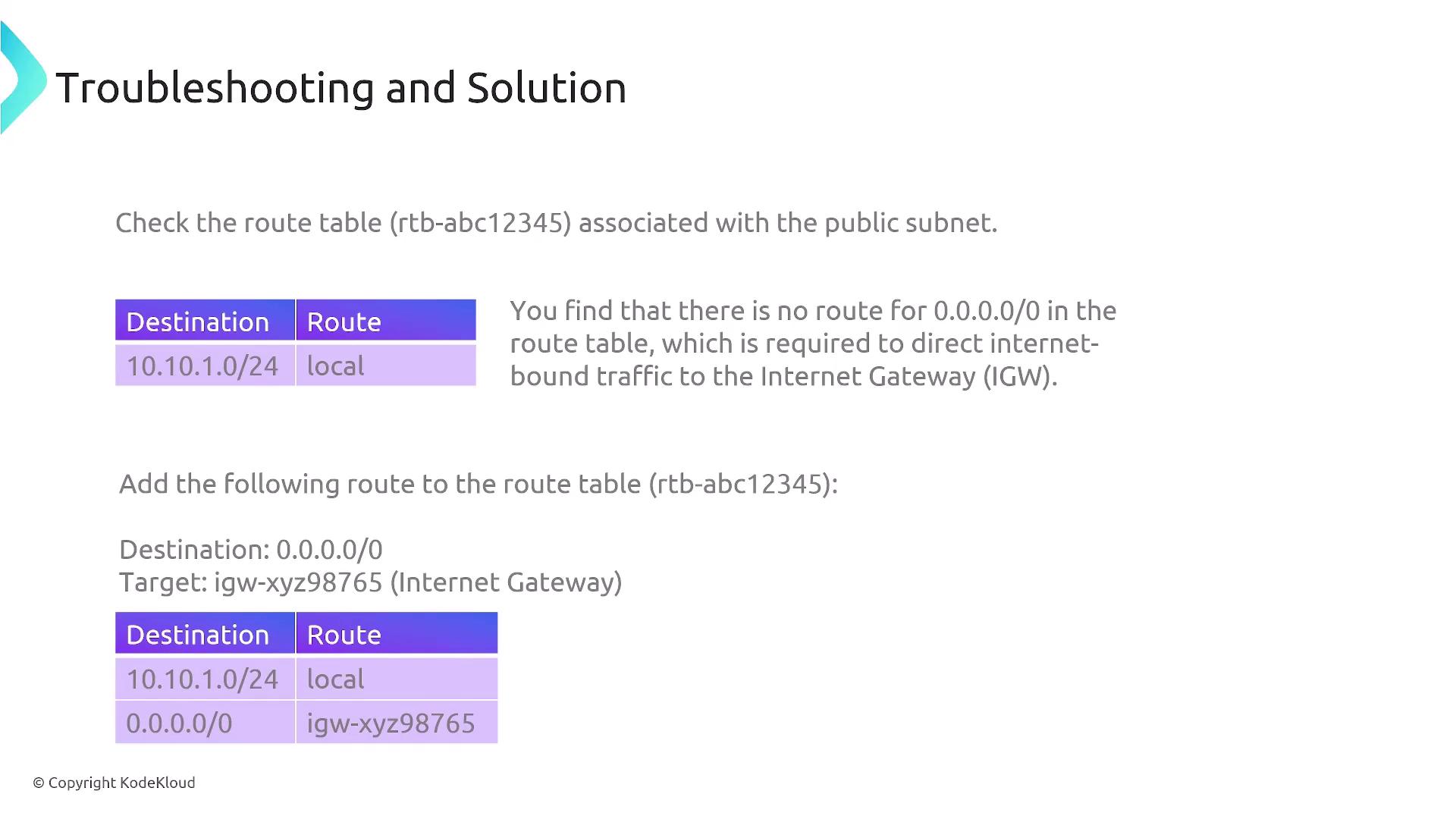
Example route table configuration:
Destination Route 10.10.1.0/24 local 0.0.0.0/0 igw-xyz98765Note
Verify both the public IP assignment and the default route configuration to ensure your instances can communicate externally.
2. Firewall Issues
Even with accurate routing, firewall rules can block necessary traffic. It's crucial to inspect two layers:
Security Groups:
Ensure that the security groups attached to your instances allow the required traffic. For instance, while SSH (port 22) might be permitted, you must also configure rules for HTTP (port 80) and HTTPS (port 443) if the server is handling web traffic.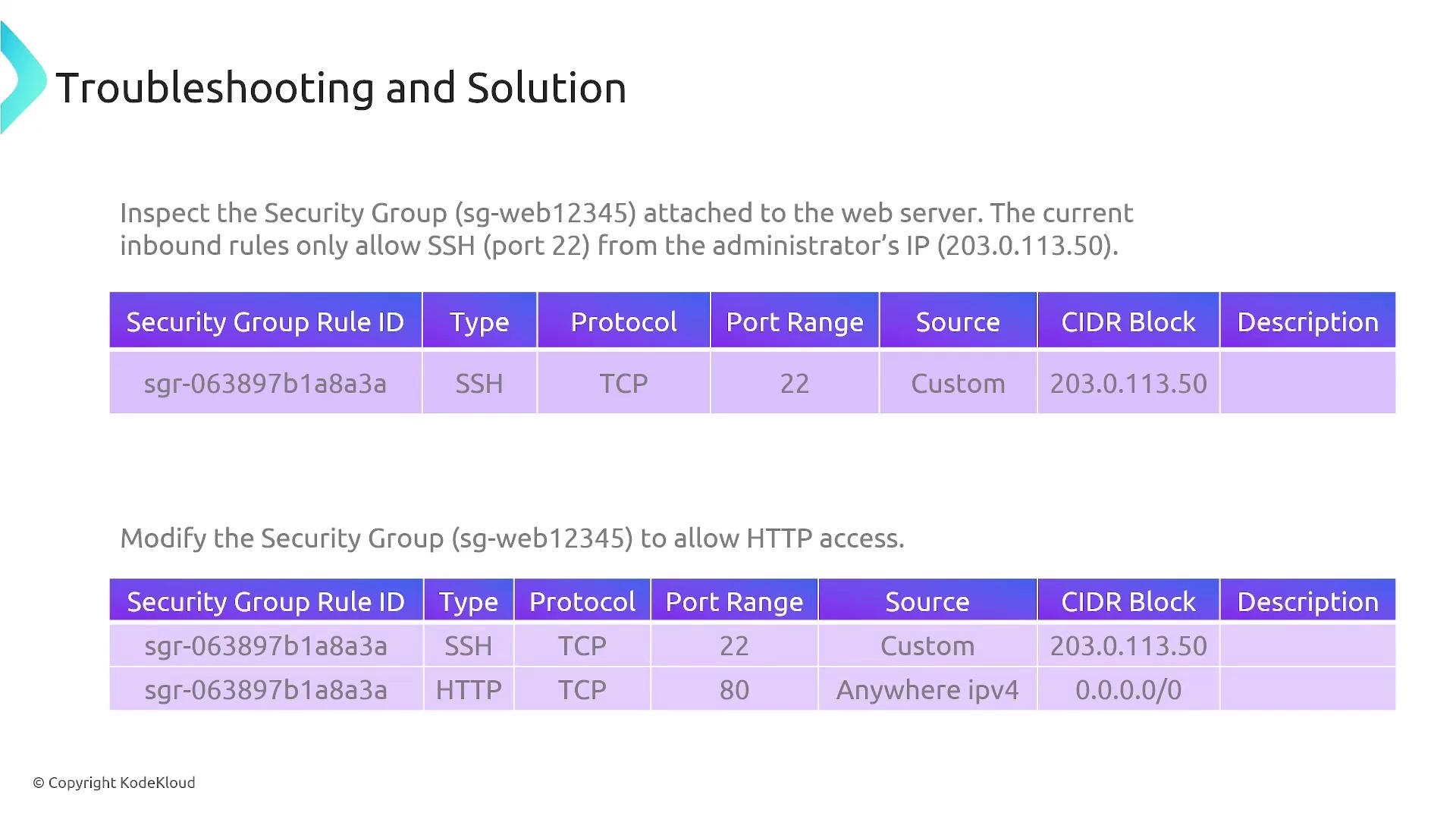
Network Access Control Lists (NACLs):
Confirm that NACLs include the necessary inbound and outbound rules. Misconfigured NACLs can block communication even if security groups are set correctly.Warning
Overly restrictive firewall settings in either security groups or NACLs can lead to unintended traffic blockages. Double-check these configurations during troubleshooting.
3. Internet Gateway Misconfigurations
The internet gateway (IGW) is essential for enabling internet connectivity in your VPC. Common misconfigurations include:
Attachment:
Every VPC must have one attached internet gateway to enable internet access. Without an attached IGW, no routing adjustments will resolve connectivity issues.Routing Conflicts:
Even with an IGW, the route table must be properly configured. Incorrect routing entries that misdirect non-local traffic will result in connectivity failures.
Remember, private IP ranges (e.g., 10.x.x.x, 172.16.x.x) cannot be directly routed to the internet.
4. NAT Gateway Issues
If your VPC relies on NAT gateways for internet access from private subnets, ensure the following configurations are correct:
Placement:
A NAT gateway must reside in a public subnet to properly proxy traffic from private subnets to the internet. If it is launched in a private subnet, internet access will be disrupted.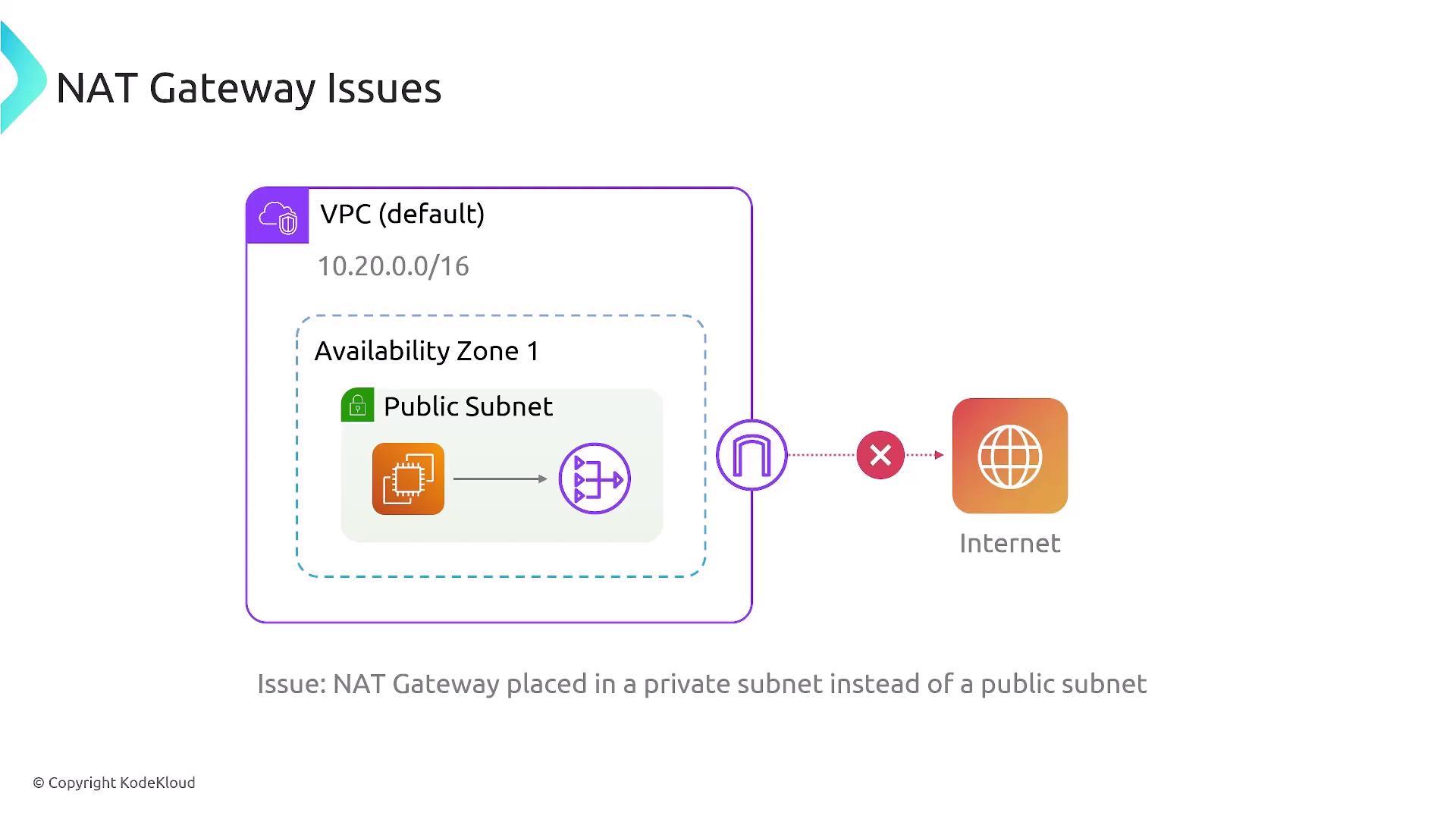
Routing Configuration for Private Subnets:
Private subnets must have a route that sends their internet-bound traffic to the NAT gateway in the public subnet. Without this route, instances in private subnets cannot access the internet.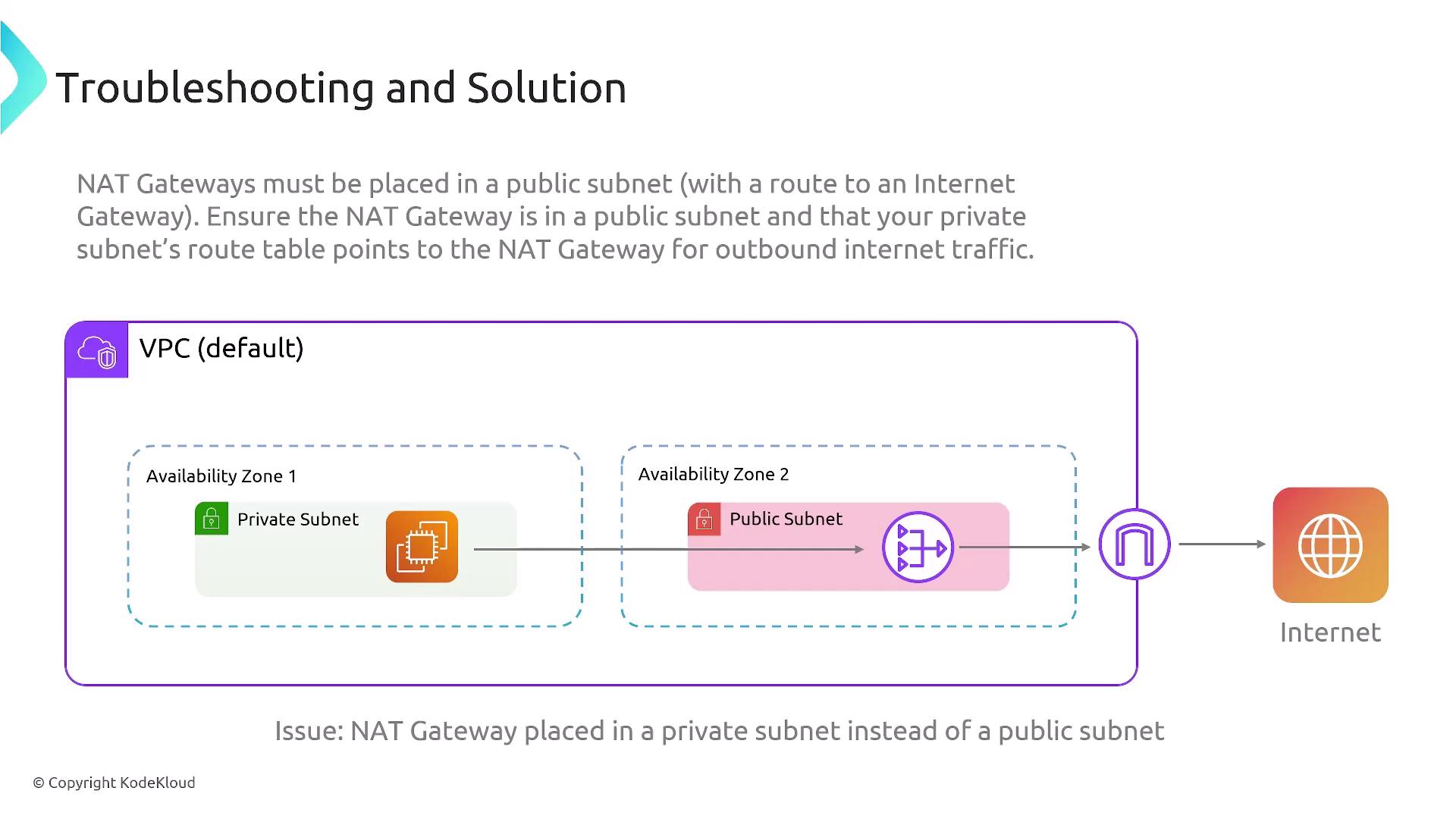
Summary of Key Issues
| Issue Description | Key Point |
|---|---|
| Absence of a Public IP | Instances without a public IP cannot access the internet. |
| Misconfigured Route Table | A missing default gateway (0.0.0.0/0 entry) prevents traffic from being directed to the internet. |
| Firewall Settings | Both Security Groups and NACLs must permit essential traffic like SSH, HTTP, and HTTPS. |
| Internet Gateway Attachment and Routing | An unconfigured or misconfigured IGW blocks internet access even if attached. |
| NAT Gateway Misplacement | The NAT gateway must be placed in a public subnet with proper routing from private subnets. |
Addressing these common misconfigurations will help enhance connectivity and security within your VPC environment. For further details on VPC configurations and best practices, consider exploring additional AWS documentation.
Thank you for reading this troubleshooting guide on VPC issues.
Watch Video
Watch video content