AWS Certified SysOps Administrator - Associate
Domain 5 Networking and Content Delivery
Networking in AWS Understanding Various Logs Available
Welcome to this comprehensive guide on AWS networking logs. In this article, we explore the critical log types available for AWS networking, each playing an essential role in exam preparation and practical troubleshooting. The logs discussed include VPC Flow Logs, AWS CloudTrail Logs, Route 53 DNS Query Logs, ELB Access Logs, CloudFront Access Logs, Global Accelerator Flow Logs, AWS WAF Logs, and Transit Gateway Flow Logs.
VPC Flow Logs
VPC Flow Logs capture detailed information about IP traffic reaching your VPC’s network interfaces. They can be delivered to Amazon S3 or CloudWatch Logs, making them invaluable for monitoring network connectivity, performing security analysis, and ensuring compliance. Tools like GuardDuty may leverage these logs to detect and analyze malicious network patterns.

Flow Logs record extensive information, including source and destination IP addresses, protocols, data volumes, and firewall dispositions (accepted or dropped).
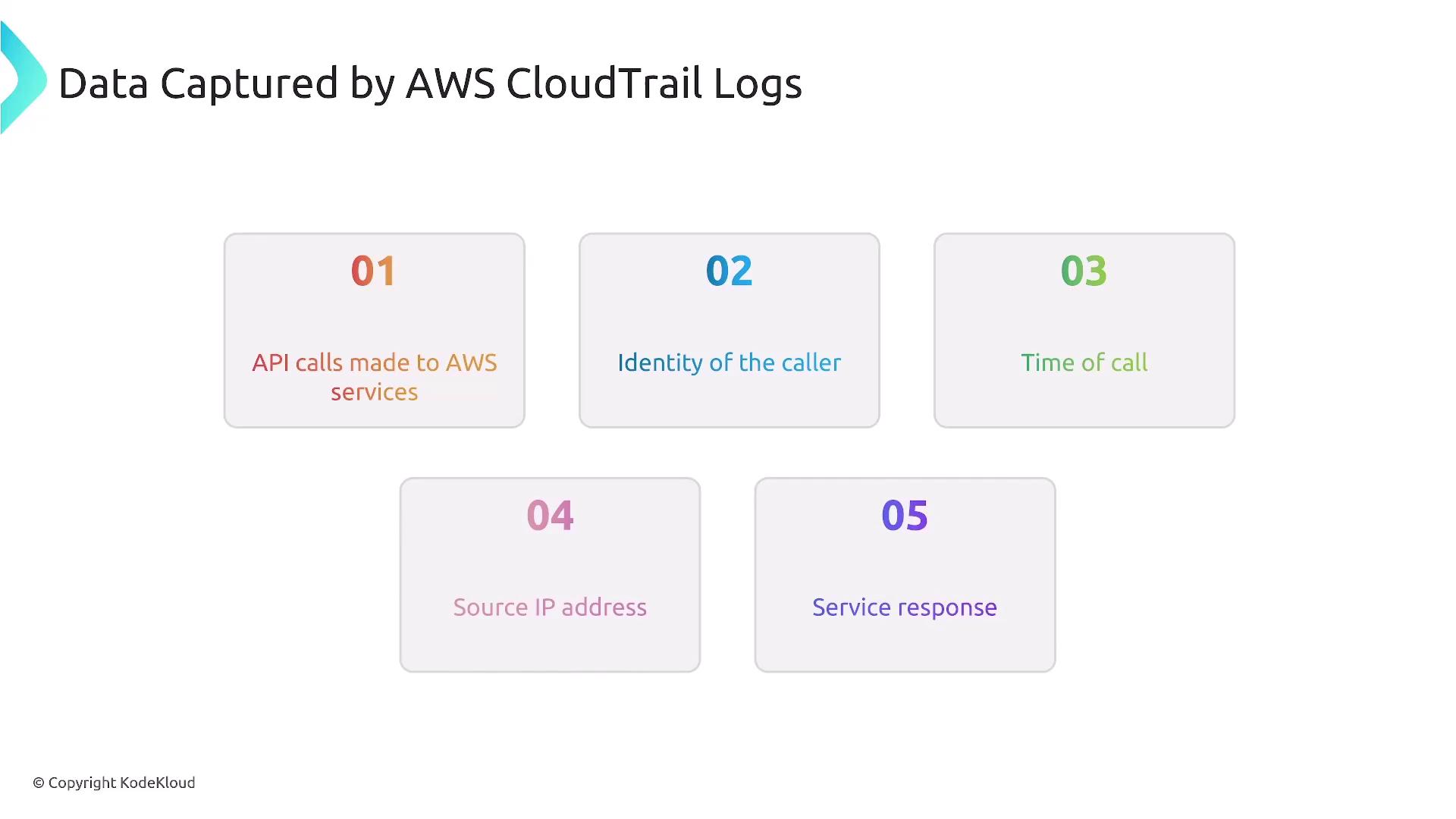
AWS CloudTrail Logs
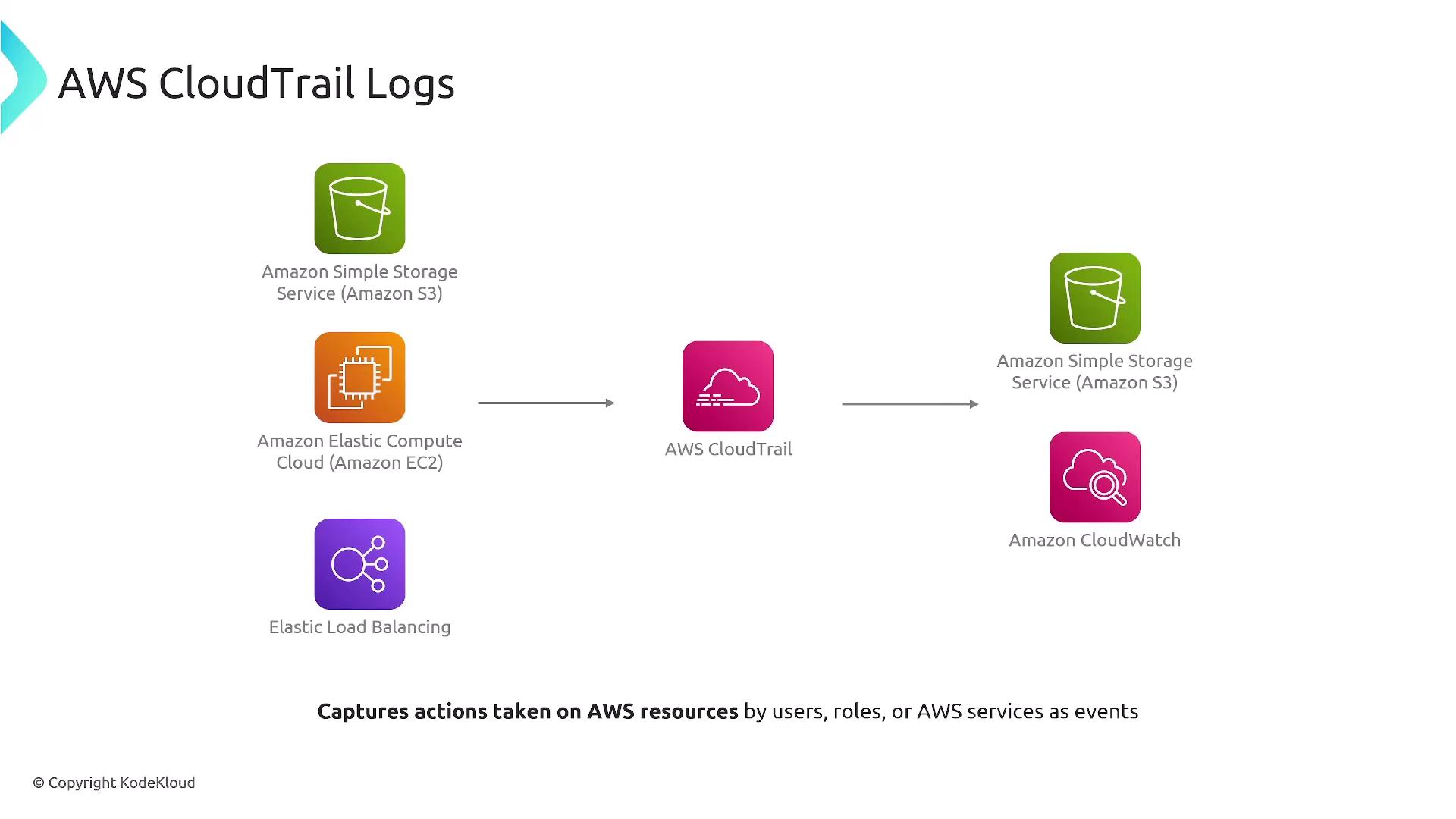
AWS CloudTrail logs record every API call made against your AWS services and resources. These logs capture a wide range of actions—from starting or stopping services to configuration changes and login attempts—and can be generated via the AWS console, command line, or SDK. CloudTrail logs, stored in Amazon S3 or CloudWatch Logs and streamed to EventBridge as events, are crucial for auditing, compliance, troubleshooting, and security monitoring. Note that AWS CloudTrail is enabled by default for new accounts.
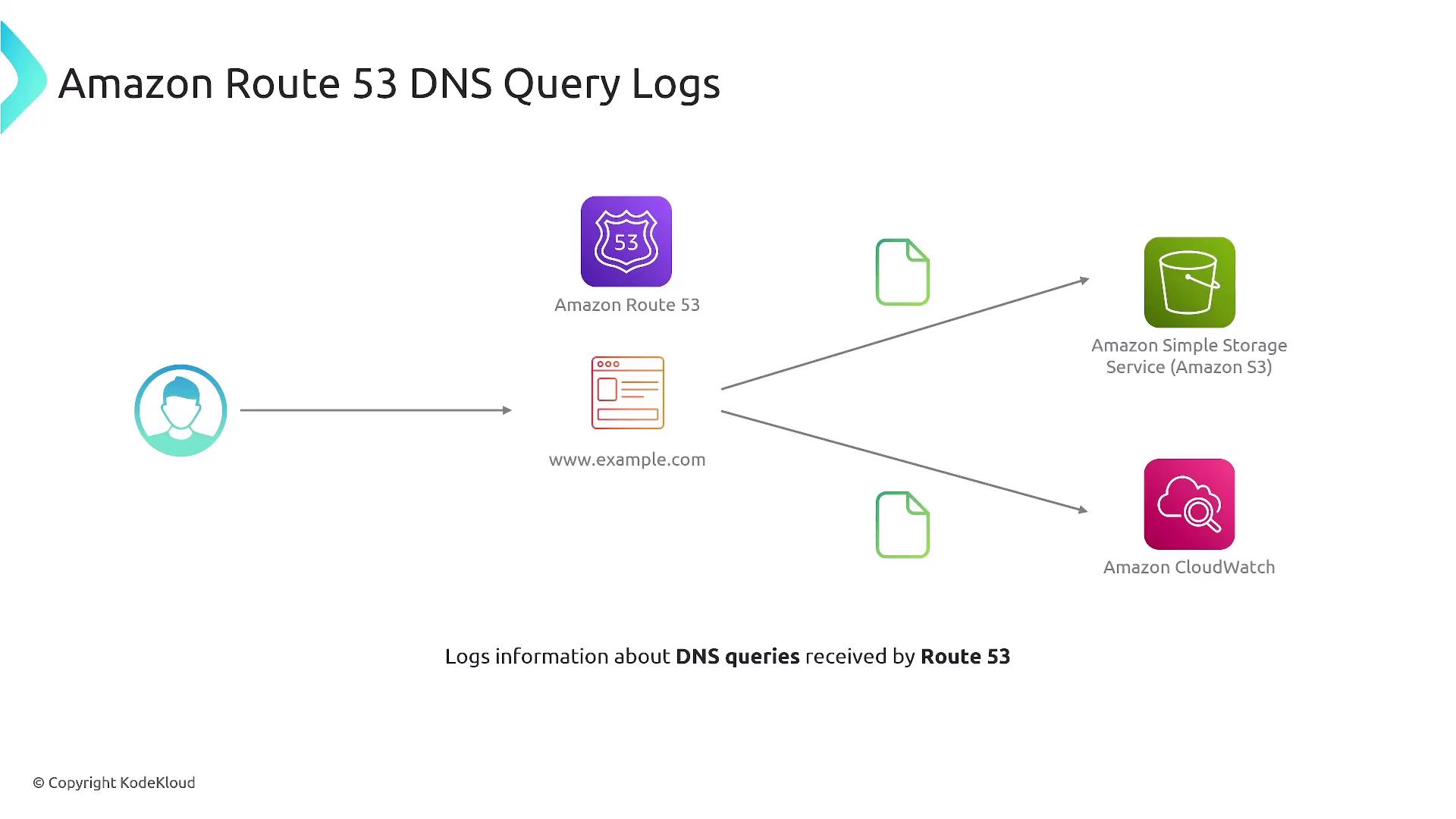
Route 53 DNS Query Logs
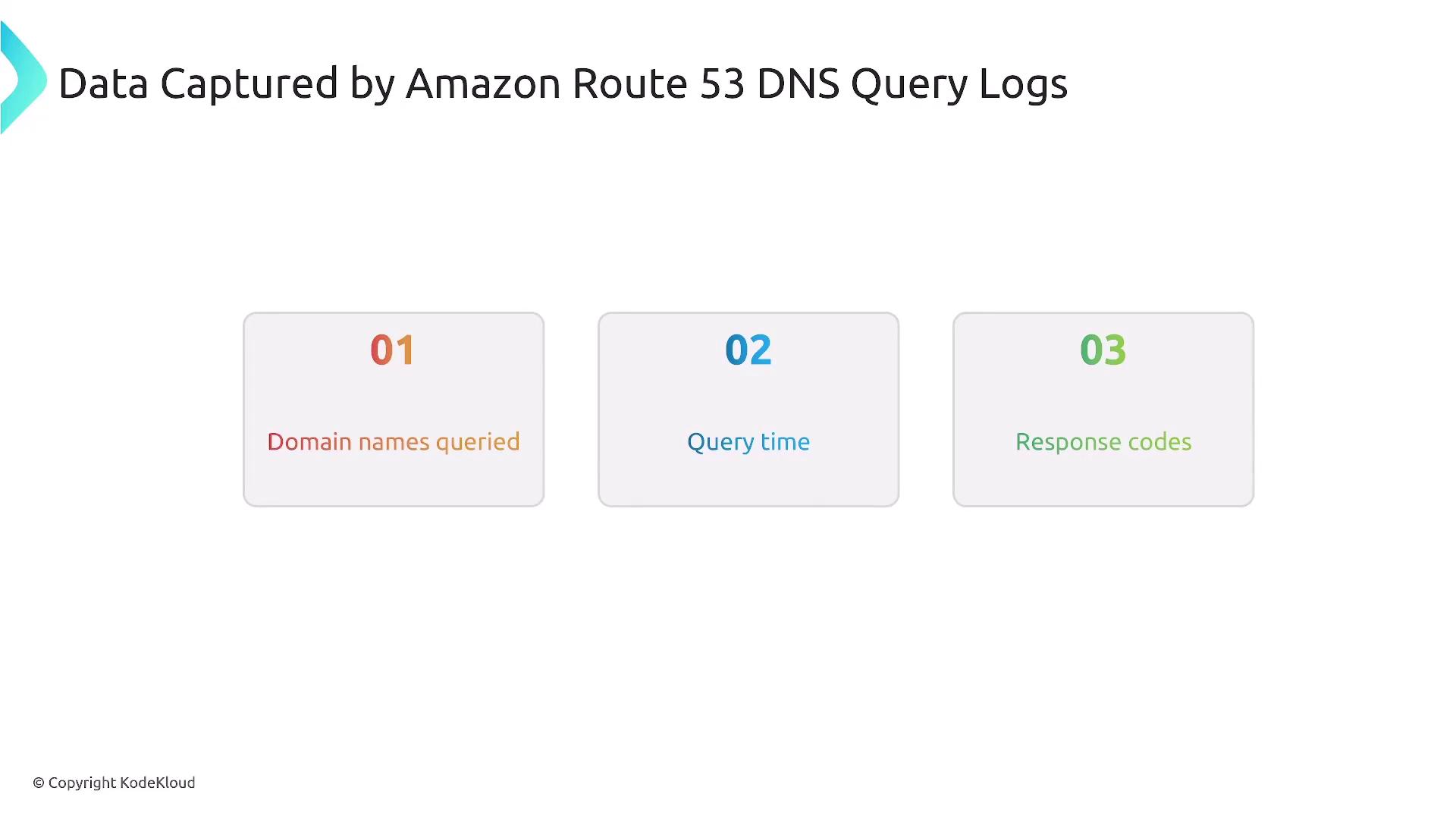
Route 53 DNS Query Logs provide detailed insights into DNS queries processed by Route 53, and they are useful for measuring query patterns, troubleshooting domain name resolution issues, and enhancing security monitoring. Additionally, GuardDuty can leverage this data for threat detection.
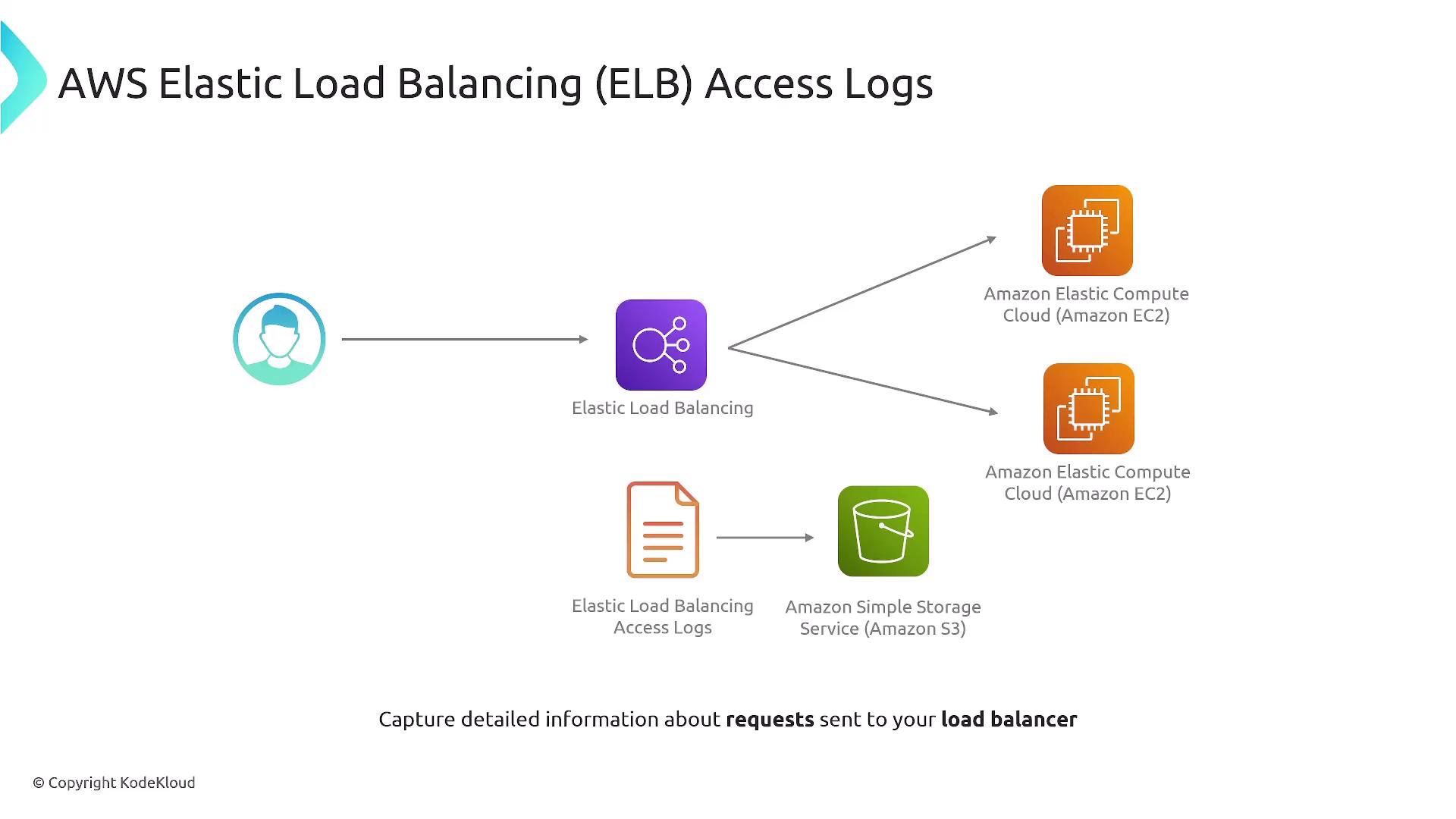
ELB Access Logs
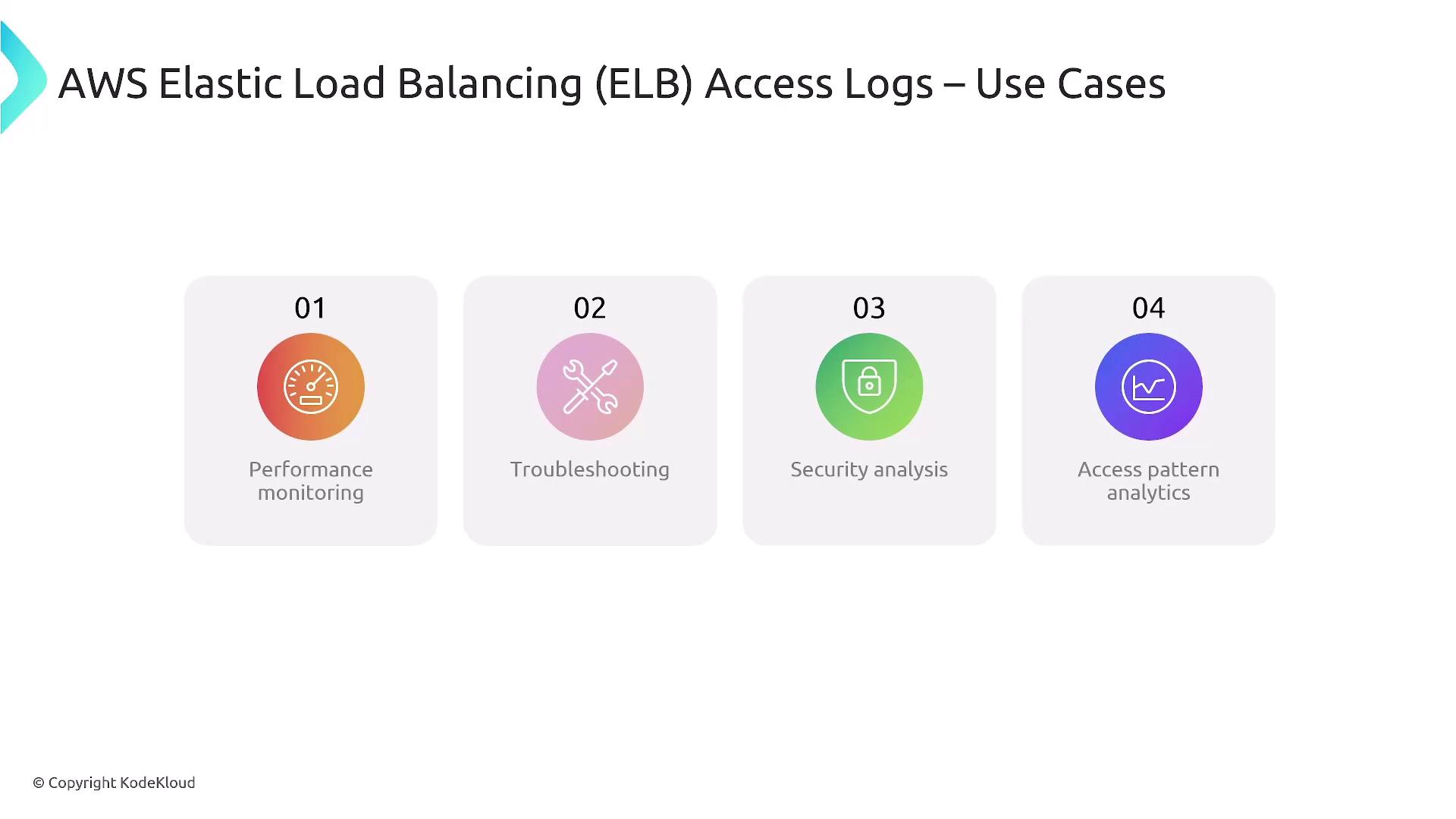
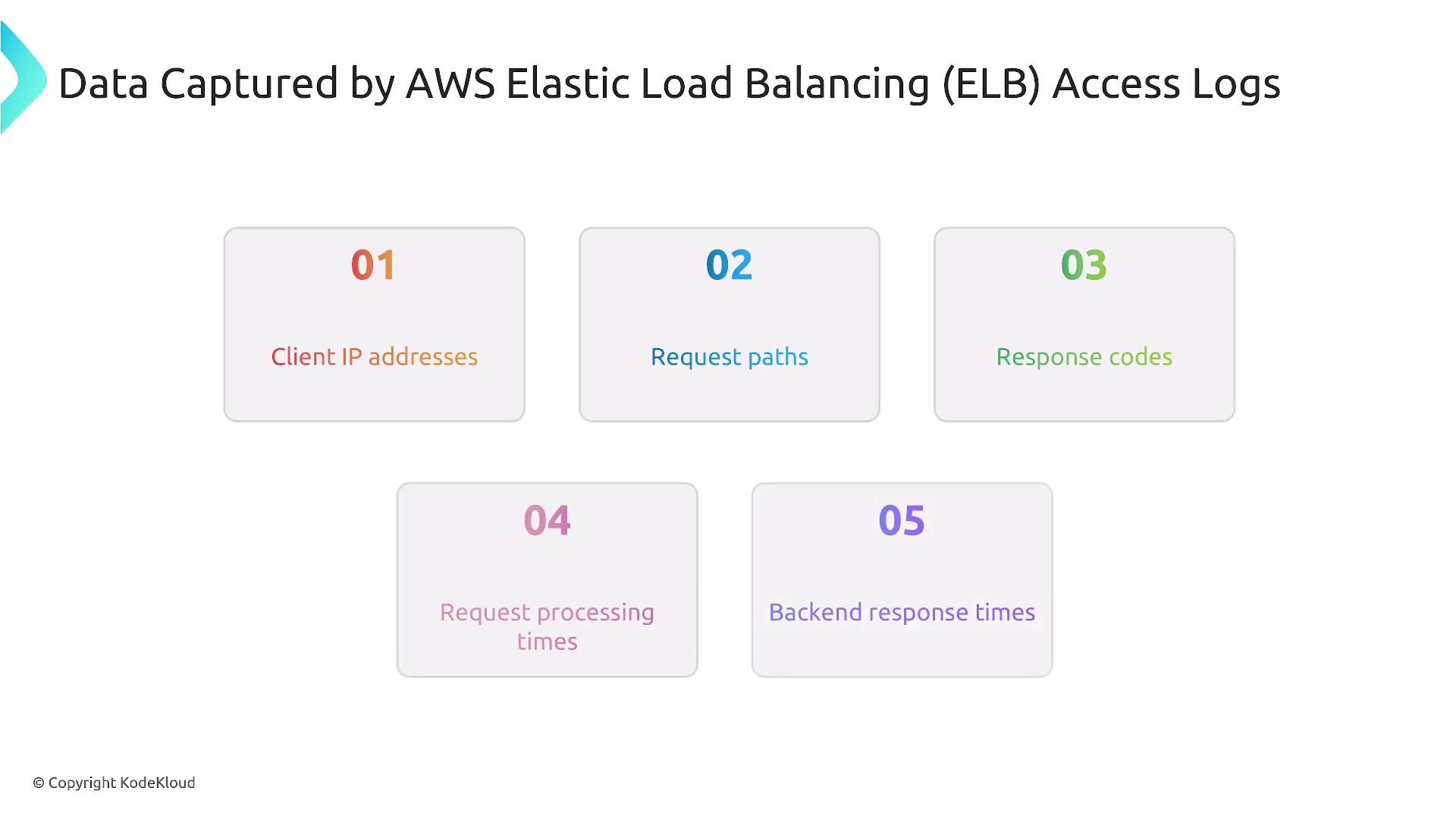
Elastic Load Balancing (ELB) Access Logs deliver detailed request-level information processed by your load balancers. These logs reveal client IP addresses, request paths, response codes, and various timing details. They are essential for performance monitoring, troubleshooting load balancer or backend issues, conducting security analyses, and deriving user access patterns.
CloudFront Access Logs
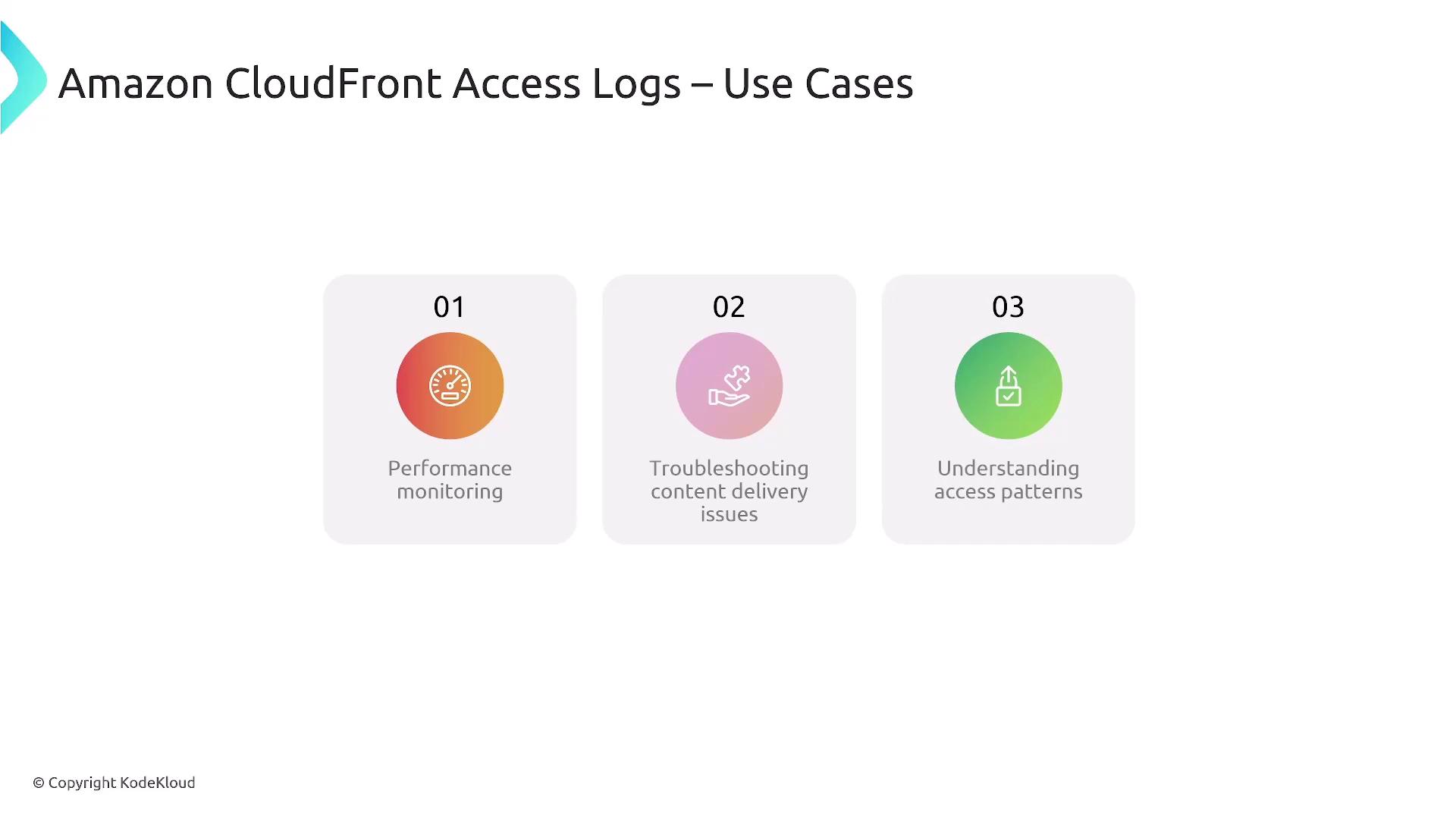
CloudFront Access Logs record detailed information on requests received by the CloudFront CDN. These logs are similar to ELB logs but also include performance metrics that help diagnose content delivery issues and analyze access patterns.
Global Accelerator Flow Logs
AWS Global Accelerator provides global load balancing, with its flow logs capturing traffic data across all entry points. These logs, which are available in CloudWatch Logs or exportable to S3, include source and destination IPs, ports, protocols, and detailed packet and byte counts. They are effective for performance optimization, troubleshooting routing issues, and ensuring application availability.
AWS WAF Logs
AWS Web Application Firewall (WAF) Logs capture metrics on web traffic that is allowed, blocked, or subjected to rate limiting based on your defined rules. They are critical for security monitoring, threat analysis, fine-tuning rules, and compliance auditing. Captured details often include source IP addresses, HTTP methods, headers, URLs, and the outcomes of rule evaluations.
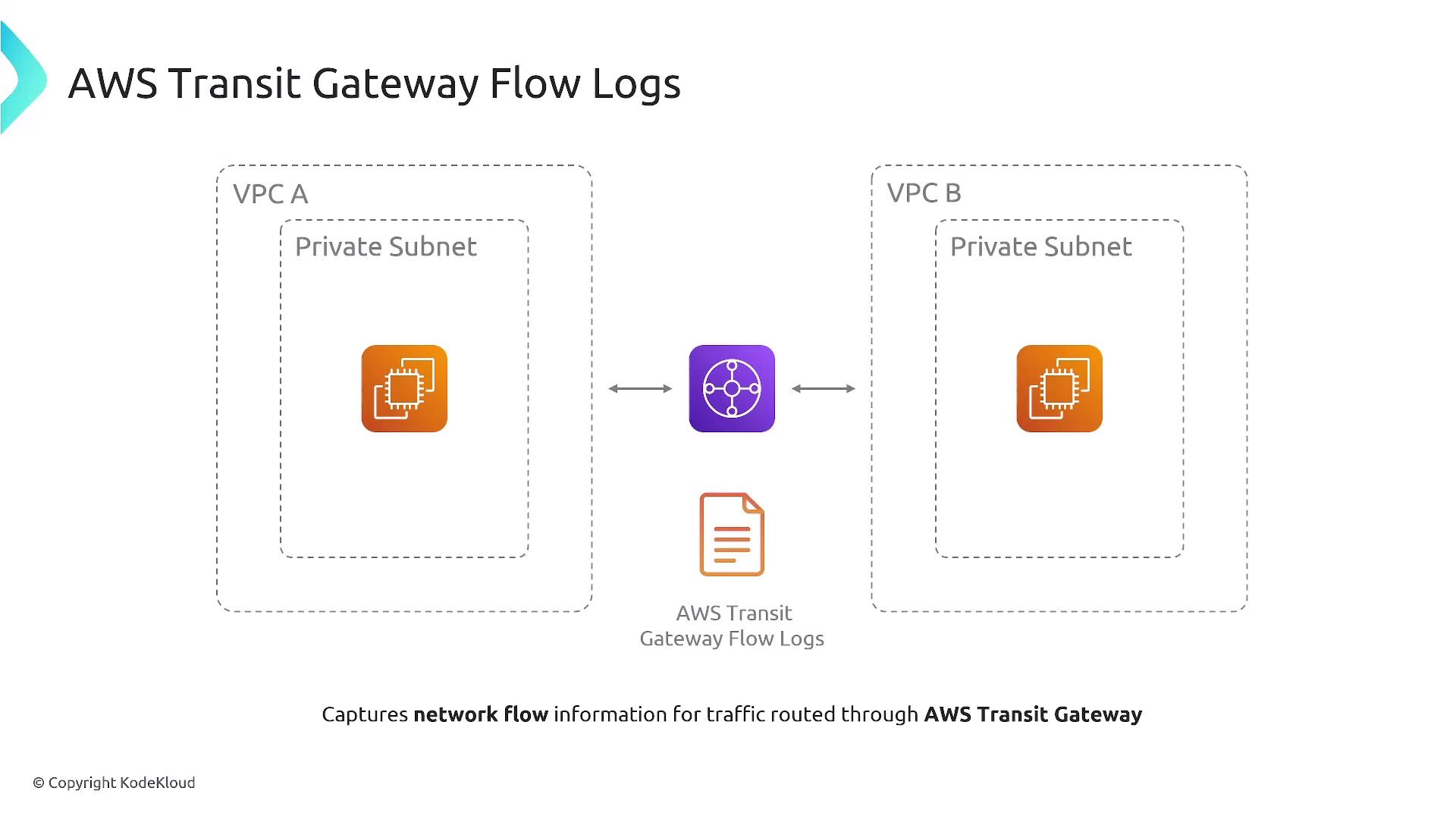
Transit Gateway Flow Logs
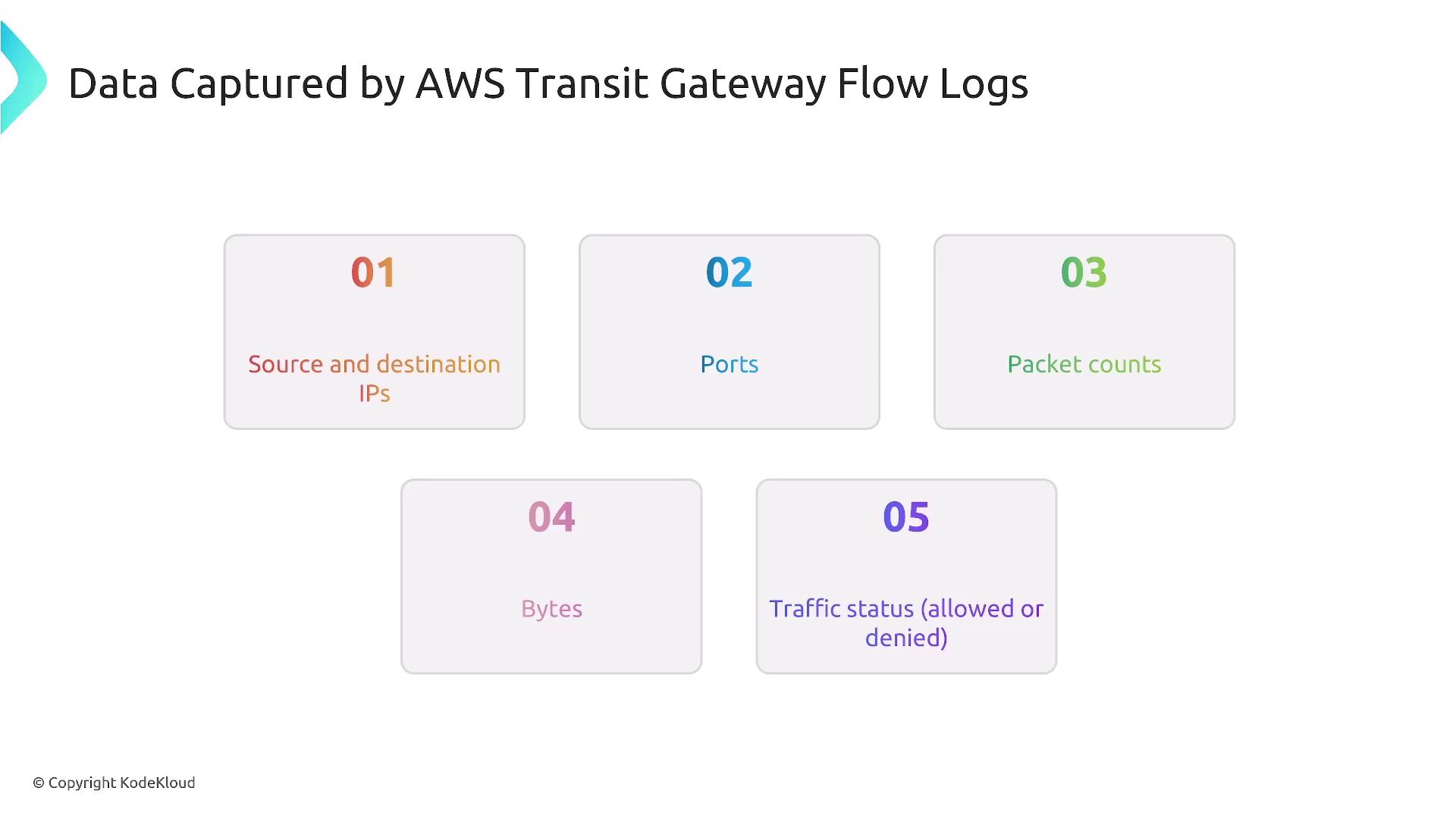
Transit Gateway Flow Logs offer insights into network traffic traversing an AWS Transit Gateway, which can be used to interconnect VPNs, Direct Connect, and VPCs. These logs assist in monitoring both inter- and intra-VPC traffic, troubleshooting routing issues, and performing security analysis. They capture key data points such as source and destination IPs, ports, packet counts, byte counts, and traffic routing statuses.
Summary
Key Takeaways
For managing AWS networking effectively, focus on the following logs:
- VPC Flow Logs: Monitor network connectivity and troubleshoot issues.
- CloudTrail Logs: Audit API actions across your AWS environment.
- Route 53 DNS Query Logs: Resolve DNS problems and improve security monitoring.
- ELB Access Logs: Gain insights into load balancing and client access patterns.
Other logs like CloudFront, Global Accelerator, WAF, and Transit Gateway flow logs are also significant. Their detailed data empowers professionals to enhance security monitoring, streamline troubleshooting, and maintain compliance in complex AWS environments.
We hope this guide helps solidify your understanding of AWS networking logs as you continue to master AWS technologies and prepare for certification exams.
For more details and additional resources, check out these helpful links:
Watch Video
Watch video content