Overview of Systems Manager and Session Manager
AWS Systems Manager simplifies operational tasks by allowing you to install an SSM Agent on your EC2 instances. Many Amazon Machine Images (AMIs) — including Amazon Linux 2 and those produced using tools like Packer or EC2 Image Builder — already come with the SSM Agent pre-installed. Alternatively, the agent can be installed during instance configuration, although this may slightly increase boot time. Systems Manager is designed to address the challenges of managing diverse environments, including AWS cloud instances, on-premises servers, and even IoT devices. Its core capabilities include patch management, configuration management via the Parameter Store, and maintenance windows. Among these, Session Manager provides a secure method to connect to your instances without needing bastion hosts or managing SSH keys.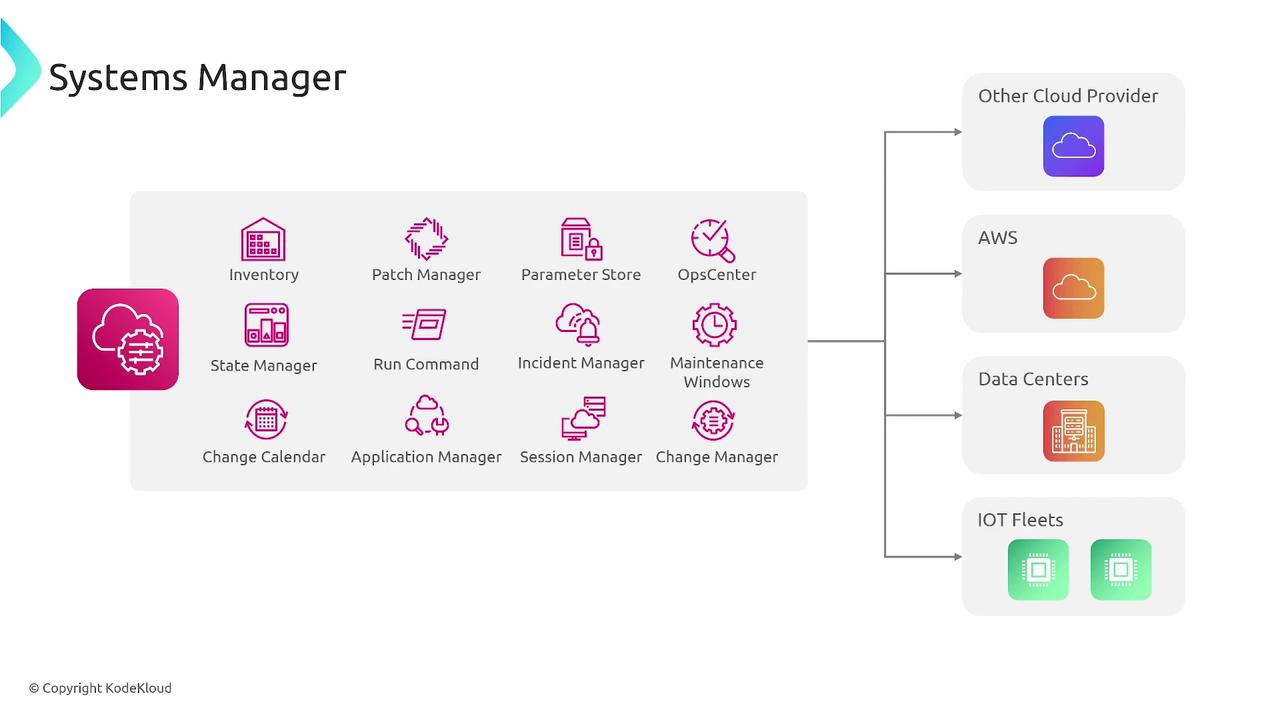
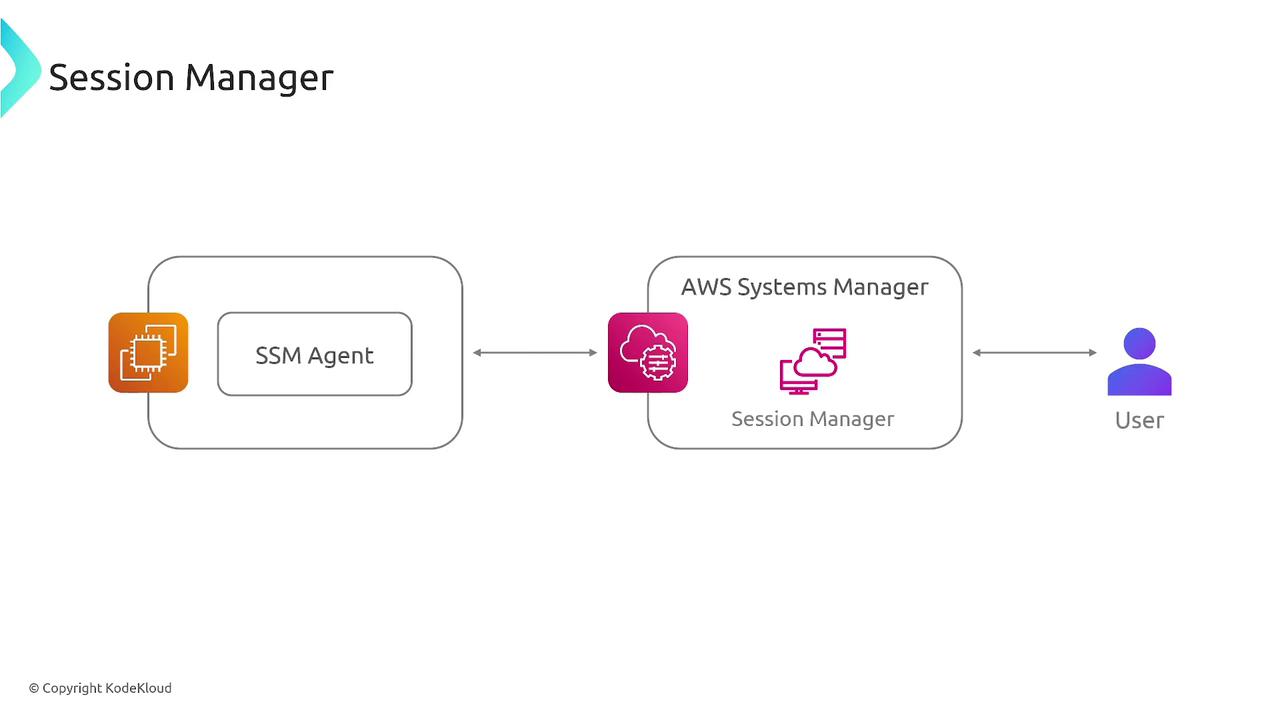
How It Works
The process of configuring Session Manager involves the following key steps:-
SSM Agent Installation
Ensure that the SSM Agent is installed and running on your EC2 instance. Most modern AMIs include this agent by default, or it can be manually installed as part of your instance configuration. -
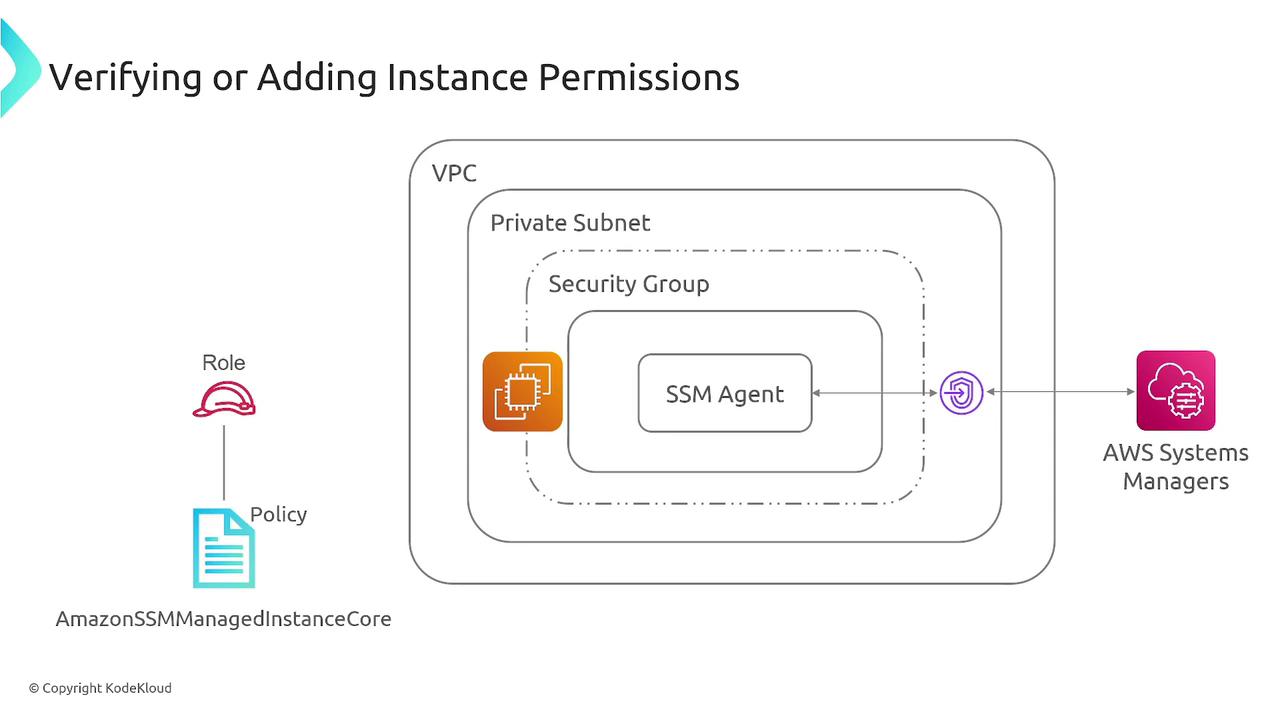
IAM Permissions
Attach an IAM role to your EC2 instance that includes the AmazonSSMManagedInstanceCore managed policy. This policy provides the necessary permissions for the instance to communicate with AWS Systems Manager. -
Network Connectivity
Your instance must have outbound HTTPS access (port 443) to AWS endpoints, such as ec2messages.region.amazonaws.com. This connectivity can be established either directly or via a private interface endpoint for secure interactions.
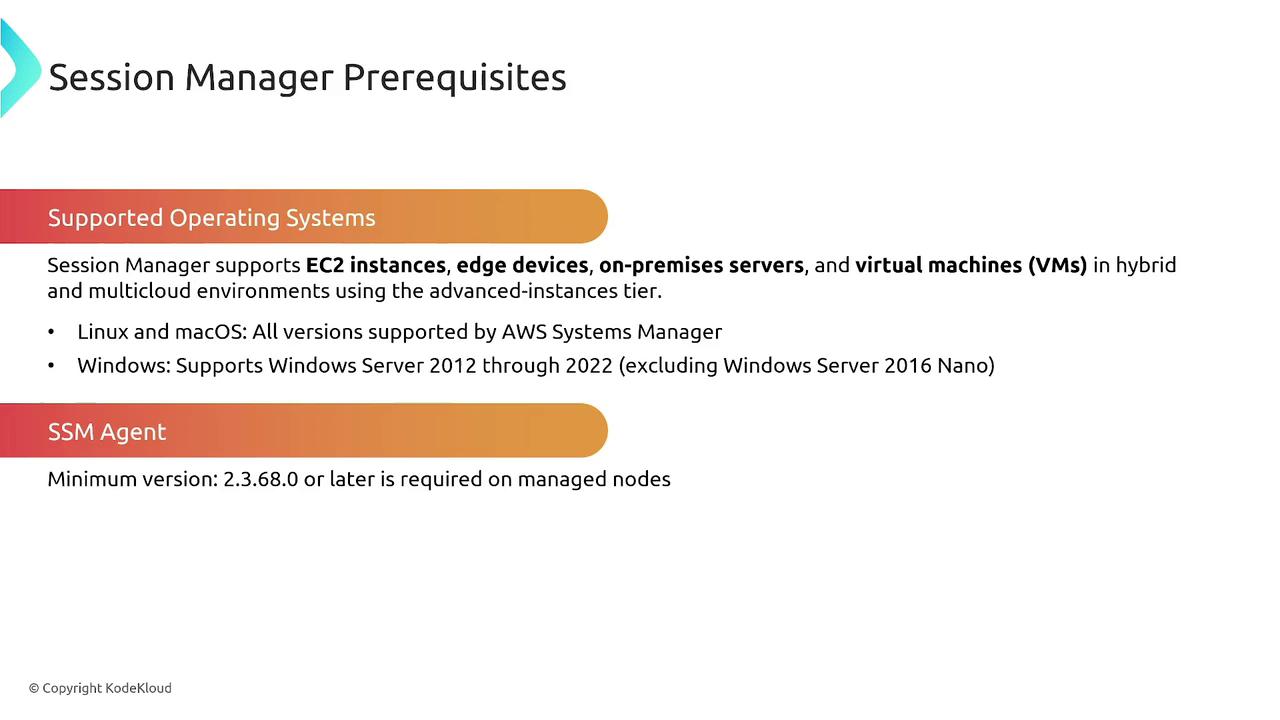
Supported Operating Systems
Session Manager supports a variety of operating systems, including:- Linux: Most distributions are supported.
- Windows: Supported from Windows Server 2012 onwards (note that support for Windows Server 2012 may be phased out in line with Microsoft’s lifecycle policies).
- macOS
Unsupported platforms, such as Solaris or certain legacy systems, are not supported by Session Manager.
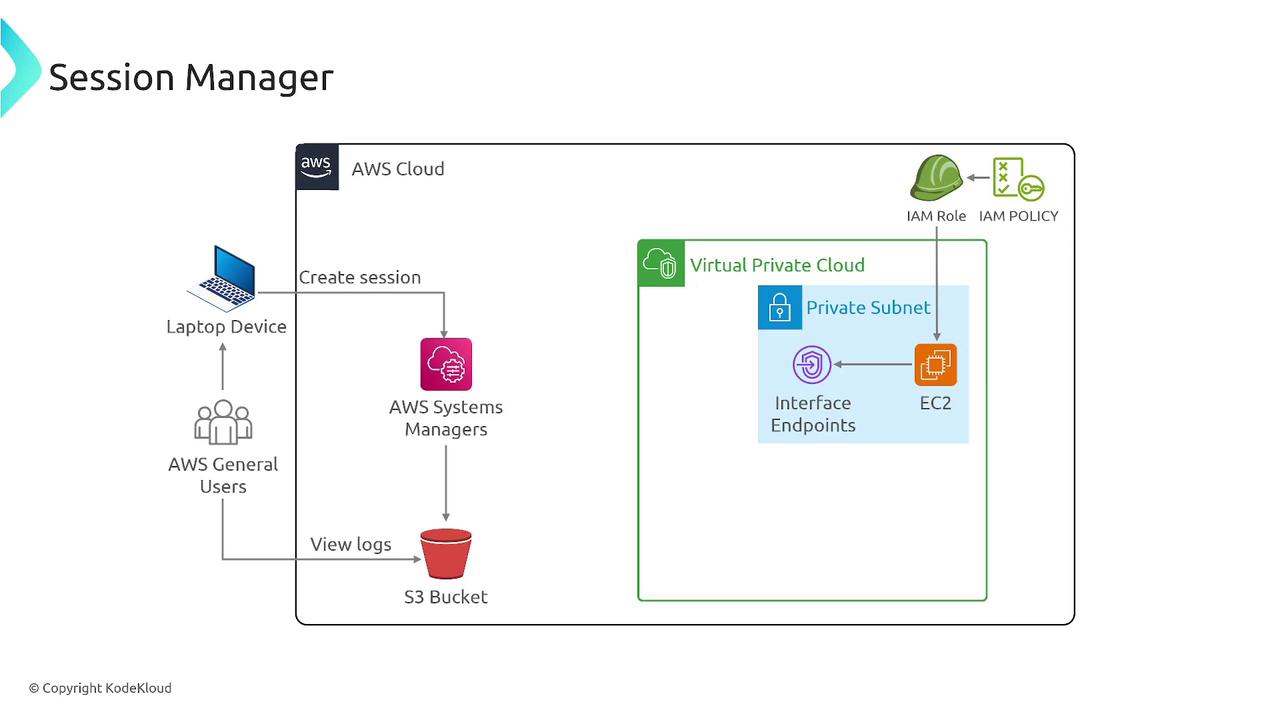
Configuring Your EC2 Instance
Once the SSM Agent is installed and the instance possesses the appropriate IAM role and network configuration, you are ready to establish a session. You can initiate a Session Manager session either through the AWS Management Console or via the AWS CLI, connecting over HTTPS on port 443. This setup ensures that even instances in private subnets are managed securely.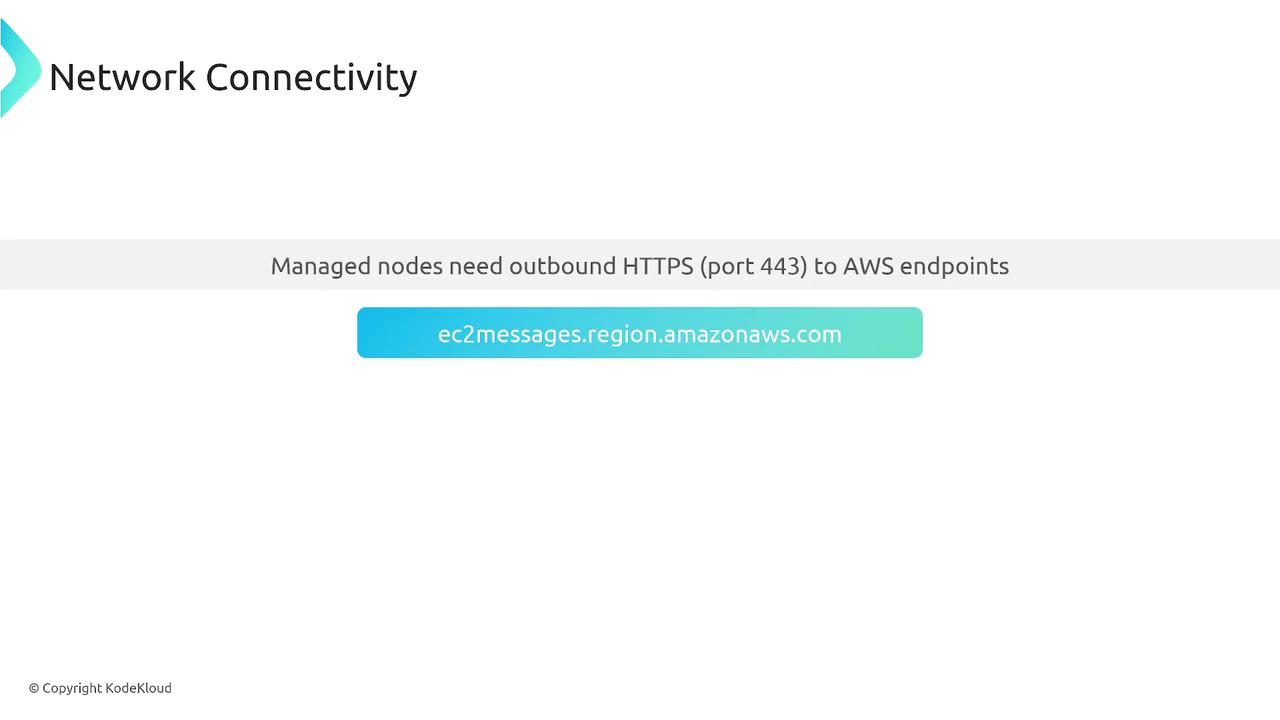
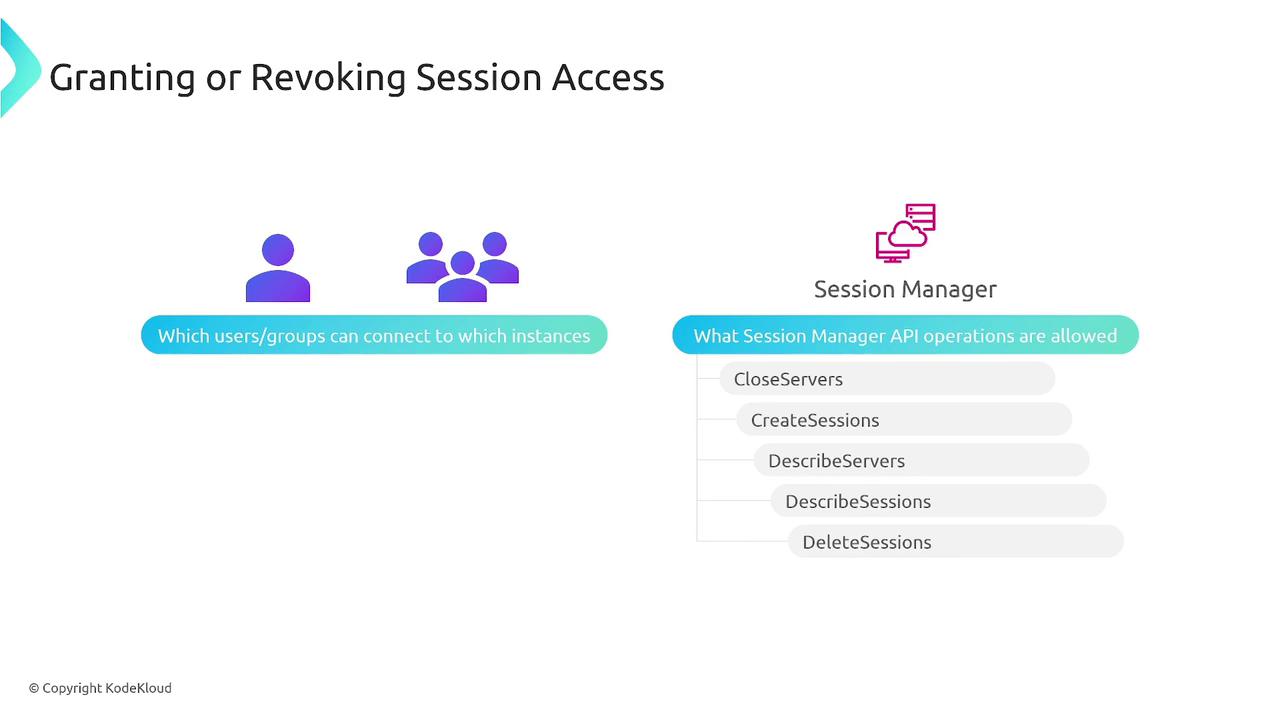
Managing Session Access
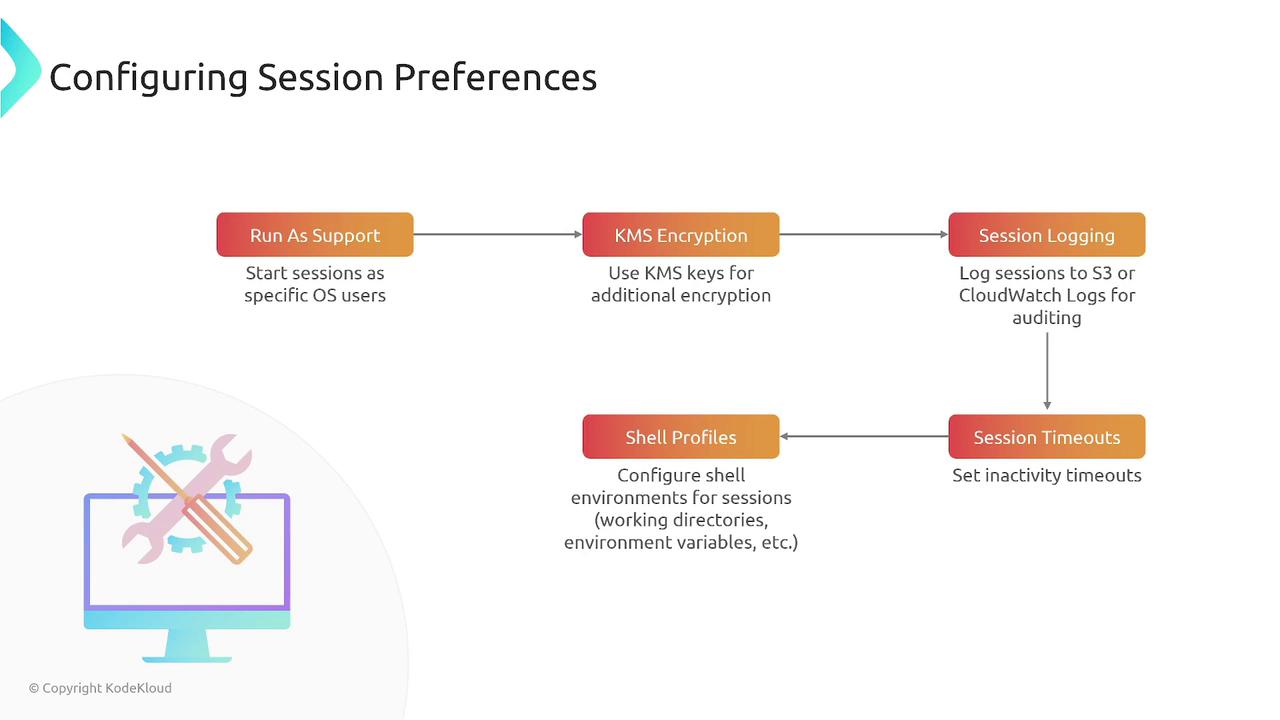
Session Manager also provides fine-grained control over user sessions. As an administrator, you can grant or revoke access and control operations such as creating, describing, or closing sessions. In addition, you can define session management preferences to enhance security and efficiency. These settings include:- Default user for sessions
- KMS encryption for session logs
- Logging defaults to Amazon S3 or CloudWatch Logs
- Session timeout durations
- Working directories and environment variables
Summary
To summarize, the key steps to configure EC2 connectivity using Systems Manager Session Manager include:- Ensuring that your EC2 instances are running a supported operating system with the SSM Agent installed.
- Attaching the correct IAM role that includes the AmazonSSMManagedInstanceCore policy to enable communication with Systems Manager.
- Verifying outbound HTTPS connectivity (port 443) to the required AWS endpoints.
- Utilizing Session Manager to manage your instances securely without needing bastion hosts or direct SSH/RDP connectivity.
- Configuring session preferences and logging to enhance auditing and security practices.