Internet Gateway
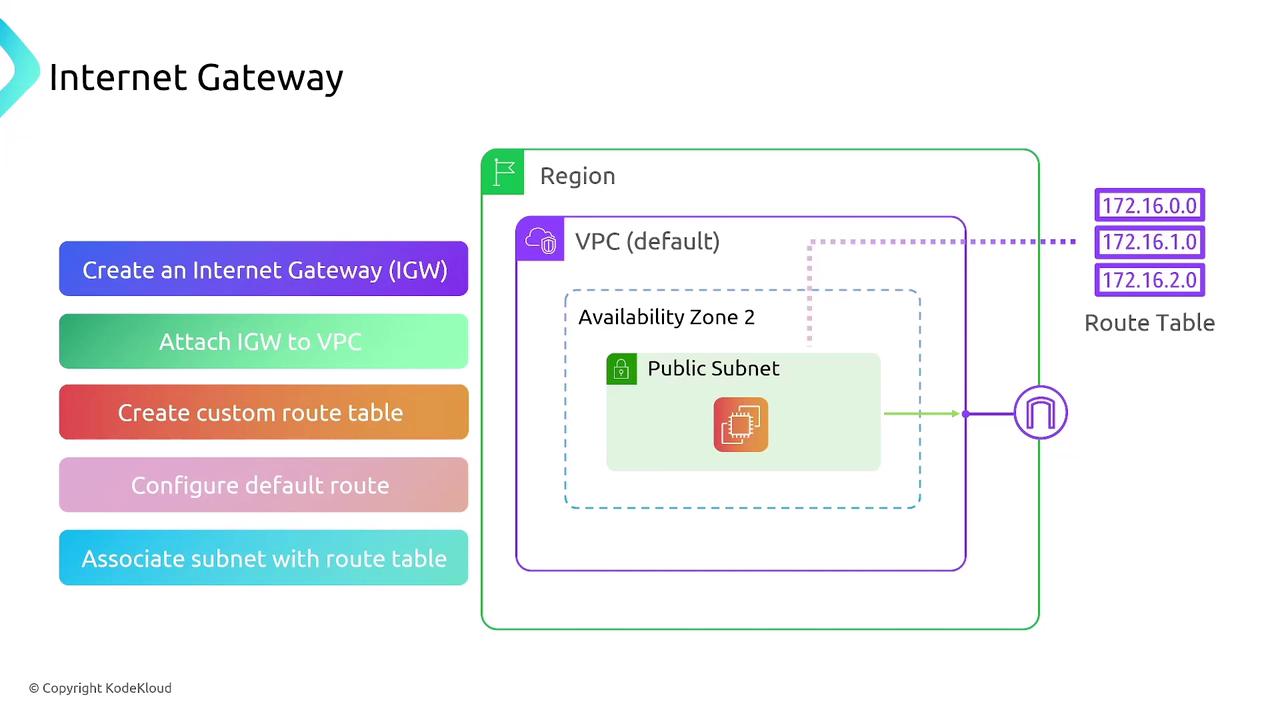
An Internet Gateway is a virtual device that connects your VPC to the internet. Each VPC can have only one attached Internet Gateway. To enable external access for your resources, you must update the route table of your public subnet to direct traffic to the Internet Gateway. Consider the following points:- The resource must reside in a public subnet with an appropriate route.
- Security groups and network ACLs must allow outbound connectivity.
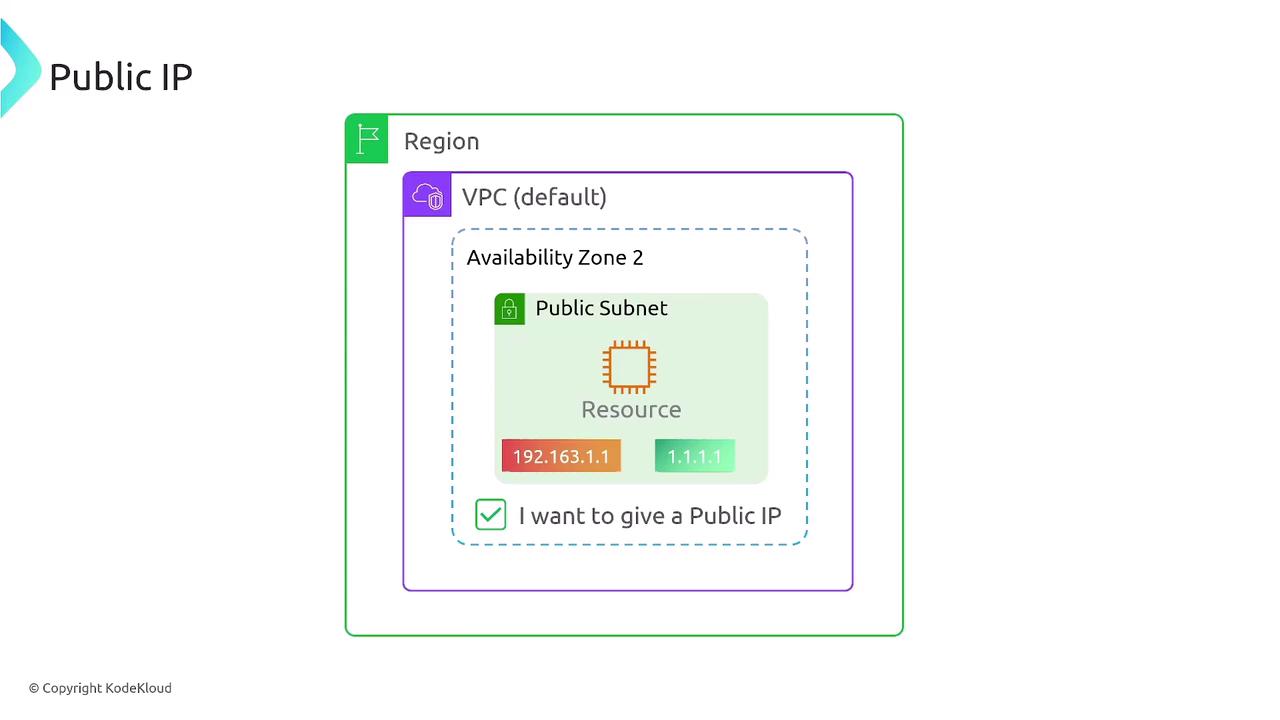
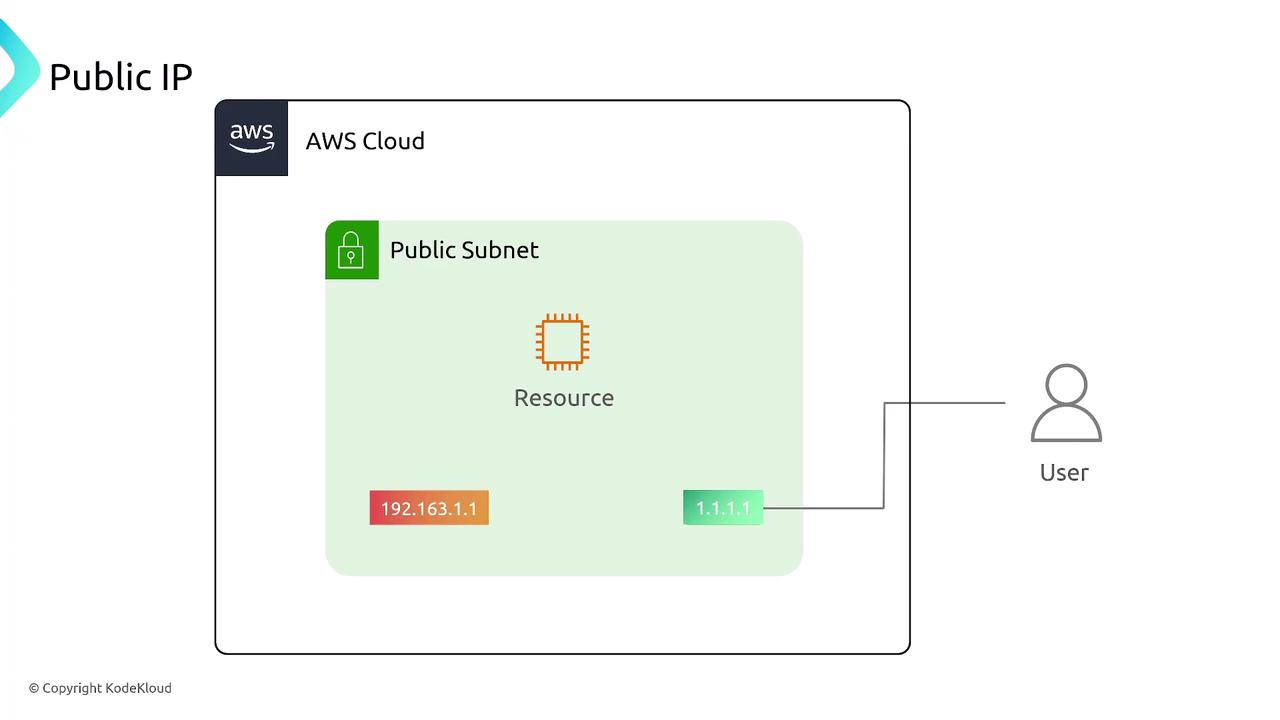
- The resource must have a public IP address (either chosen at launch or assigned as an Elastic IP).
- Create an Internet Gateway.
- Attach the Internet Gateway to your VPC.
- Update the route table to direct non-local traffic through the Internet Gateway.
- Associate the route table with a public subnet.
- Ensure the resource in the subnet is assigned a public IP address.
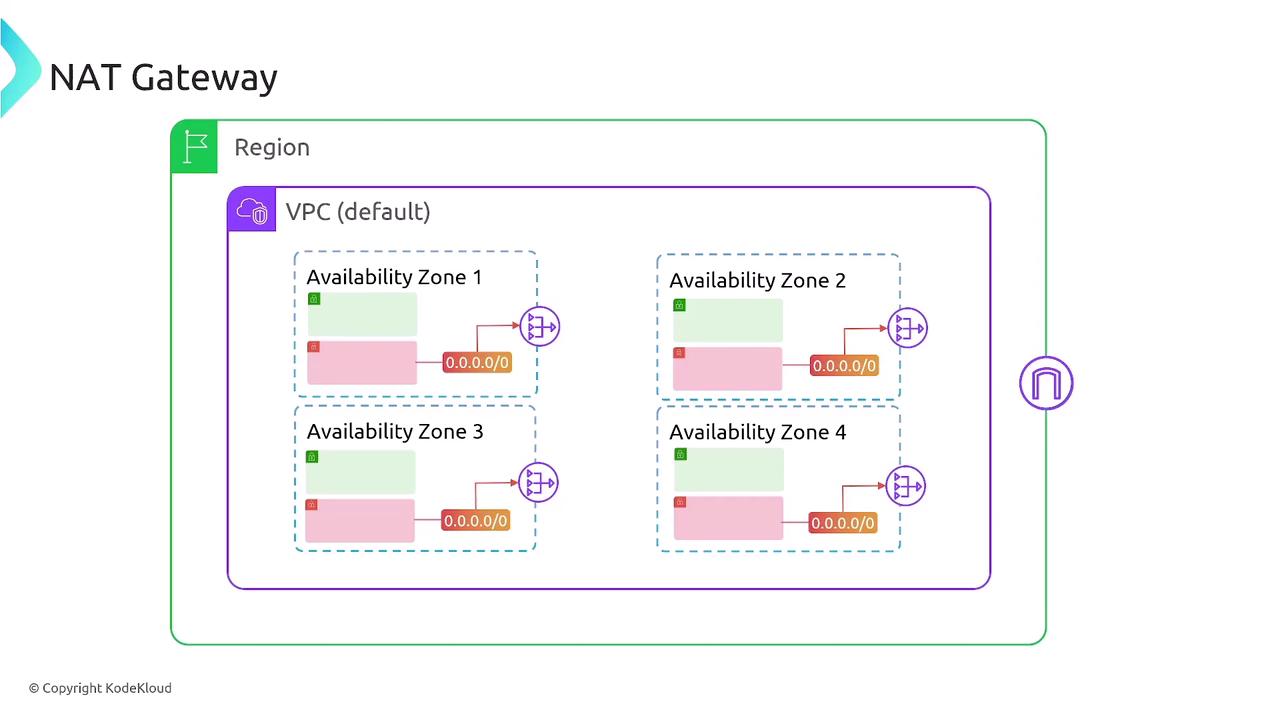
NAT Gateway
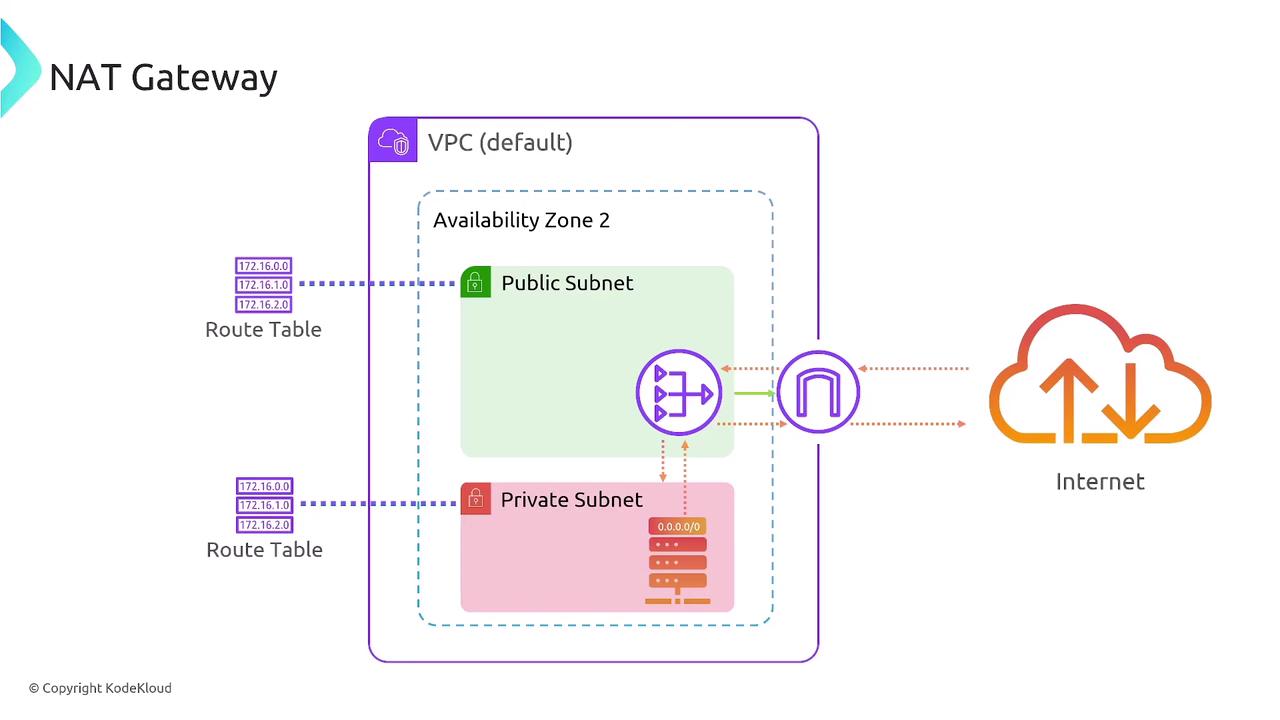
A NAT Gateway enables instances in private subnets to initiate outbound connections while blocking inbound traffic from the internet. This setup maintains the security of your resources while allowing necessary outbound communication. Key considerations when using a NAT Gateway include:- The route table of the private subnet directs outbound traffic to the NAT Gateway.
- The NAT Gateway resides in a public subnet with its own route to the Internet Gateway.
- It acts as a proxy by translating private IP addresses to a public IP address.
- It supports both IPv4 (primarily) and IPv6 (using NAT64), though it is mainly used for IPv4 outbound traffic.
- It is AZ-specific, meaning you should deploy one NAT Gateway per Availability Zone to minimize latency.
Remember that NAT Gateways incur hourly charges as well as fees per gigabyte processed. Monitor usage to manage costs effectively.
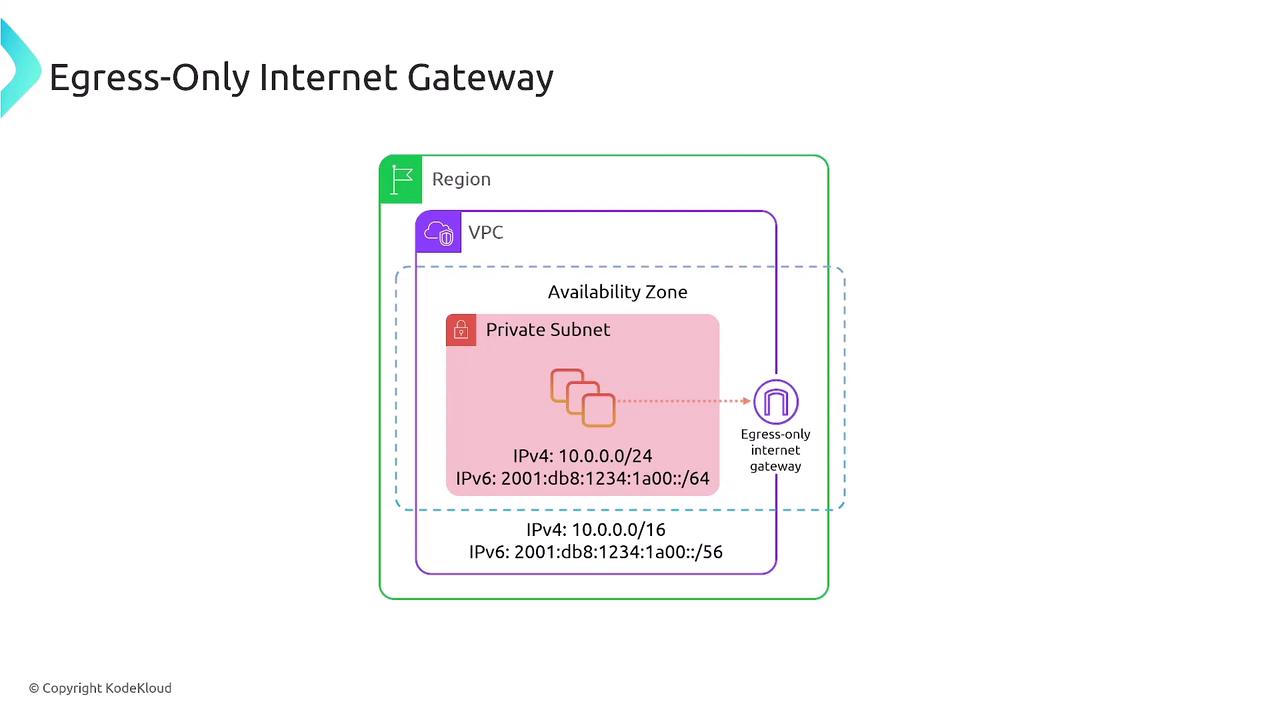
Egress-Only Internet Gateway
The Egress-Only Internet Gateway is used exclusively for IPv6 traffic in private subnets. It allows outbound-only connections, ensuring that no incoming traffic can reach the resource. Key details include:- Supports only IPv6 traffic.
- Permits outbound connections only, with all inbound traffic blocked.
- Does not perform IP translation between IPv6 and IPv4.
- Is configured in the route table similarly to an Internet or NAT Gateway.
- No special placement in public subnets is required.
- While there is no setup fee, standard data transfer charges apply for outbound traffic.
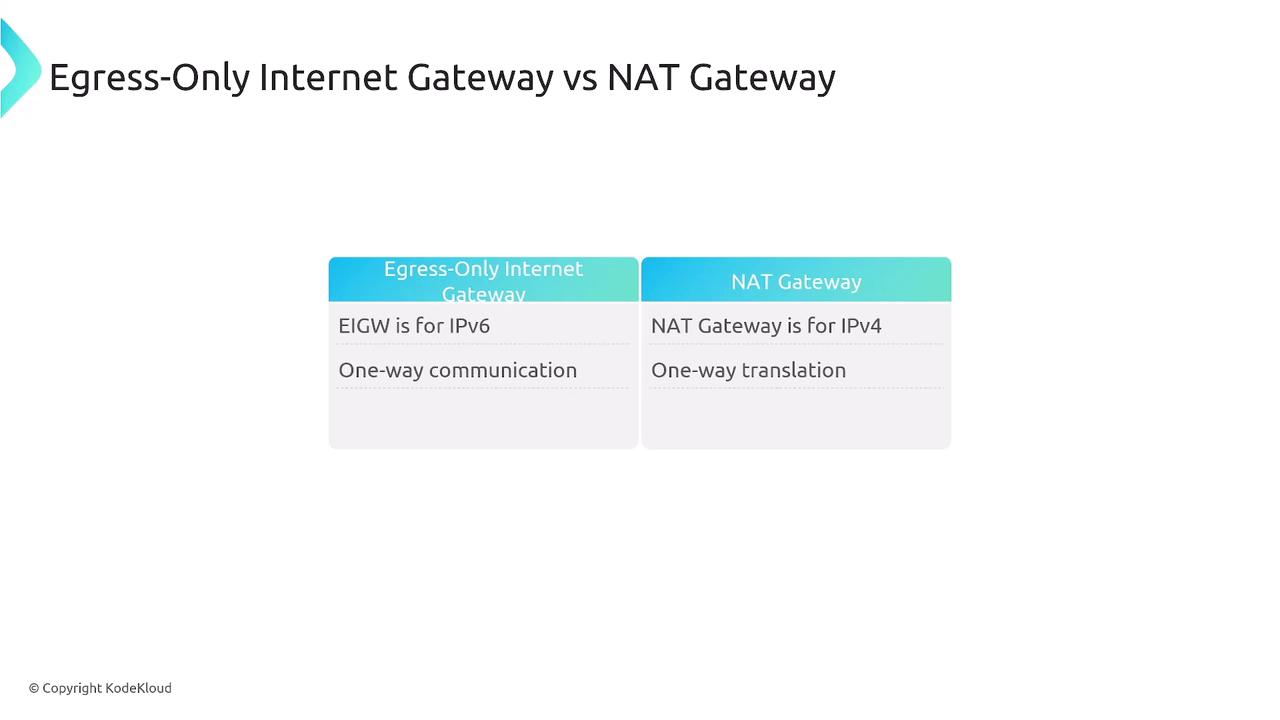
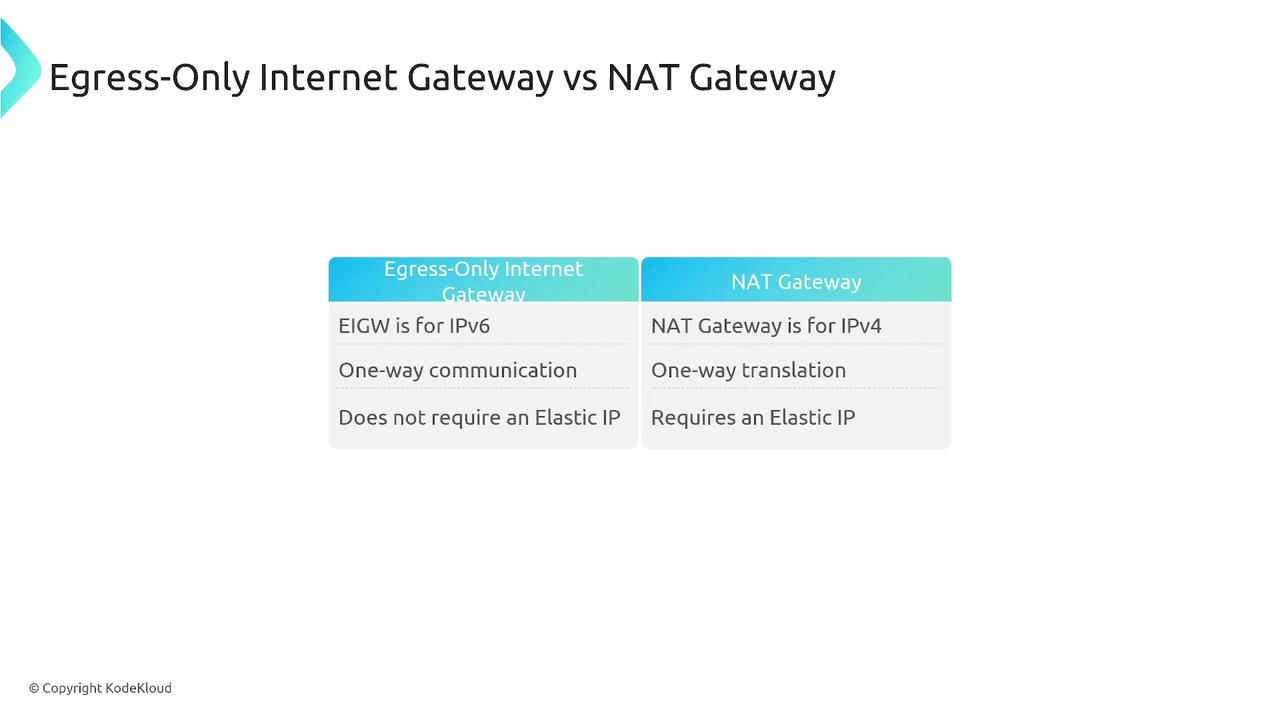
- NAT Gateways translate IPv4 addresses (and support IPv6 via NAT64) and act as proxies.
- Egress-only Internet Gateways offer a direct, unaltered IPv6 connection for outbound traffic without translation.
Summary
-
Internet Gateway:
Provides full bidirectional internet access for public subnets. Every VPC can have one attached, making it essential for resources requiring external connectivity. -
NAT Gateway:
Allows private subnets to access the internet (primarily IPv4) by translating private IP addresses to a public IP address. It prevents inbound connections from external sources. -
Egress-Only Internet Gateway:
Designed for IPv6 outbound traffic in private subnets, it ensures a direct connection without translation and blocks all inbound traffic.