AWS Certified SysOps Administrator - Associate
Domain 5 Networking and Content Delivery
Demo Exploring the Options with CloudFront
Welcome everyone, this is Michael Forrester.
In this lesson, we explore the range of settings available when creating a CloudFront distribution. CloudFront offers a variety of features—from built-in functions for request manipulation and telemetry to advanced logging, analytics, and enhanced security features such as origin security and field-level encryption. Today, we will focus on the core distribution options.
Creating a CloudFront Distribution
Let's start by creating a new CloudFront distribution. Although I have several distributions already configured, I'll build one from scratch for this demonstration. When selecting an origin, you can choose from multiple sources, including Amazon S3 buckets, load balancers, and more. In this example, we'll select a web Application Load Balancer (ALB) configured for secure connections.
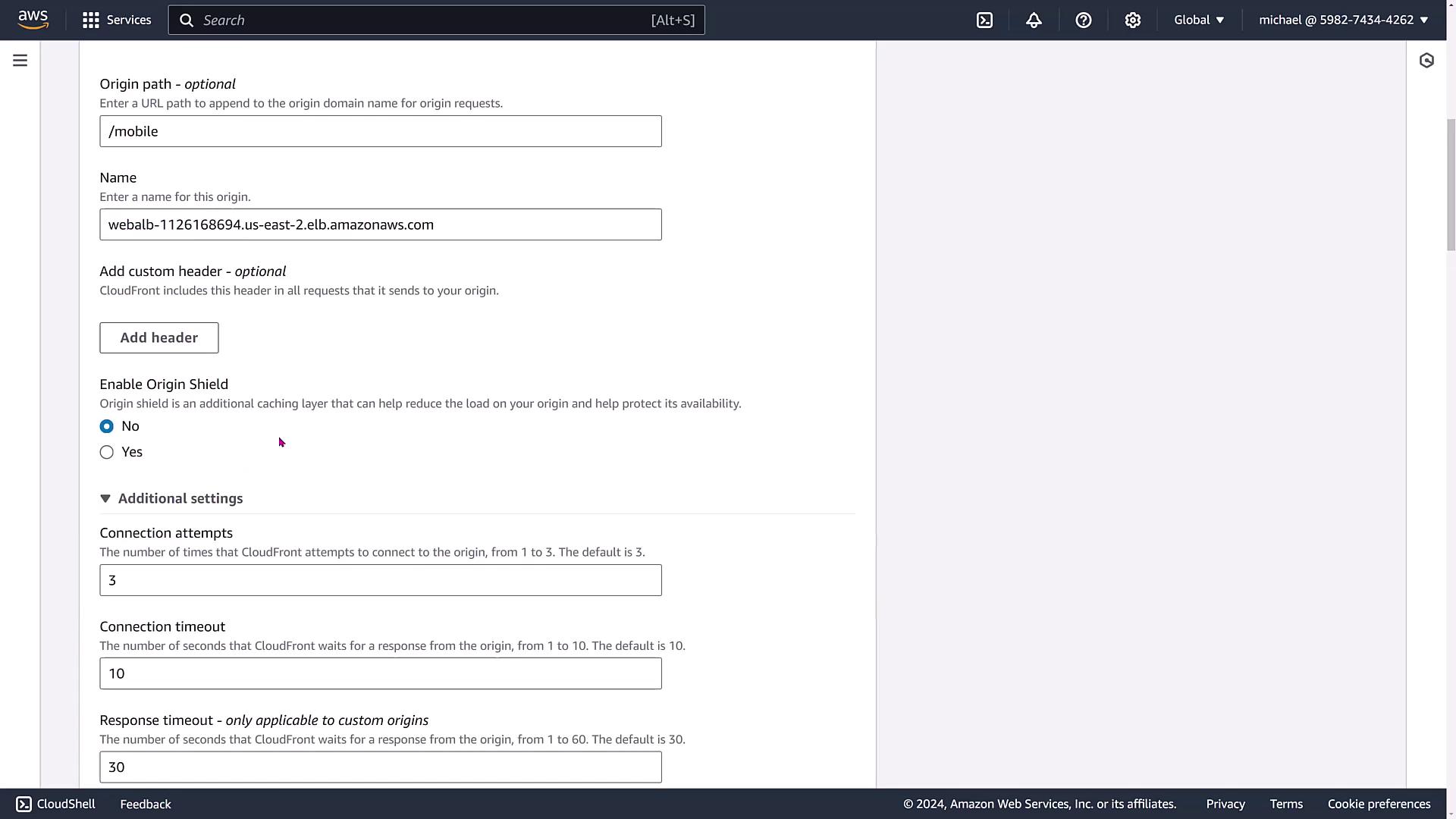
During configuration, you can set the origin path. For instance, adding "/mobile" might indicate that this distribution serves a mobile site exclusively. With the load balancer selected, the DNS name is auto-populated. You can also modify headers and enable Origin Shield, which adds an extra cache layer near the edge. This additional layer can substantially improve availability, especially for static websites.
Configuring Additional Settings
Several settings can be fine-tuned during setup, including:
- Timeouts and Connection Attempts: Adjust these parameters as necessary.
- Protocol Enforcement and SSL/TLS Versions: Specify the origin domain, enforce protocols (or allow matching viewer protocols), and choose SSL/TLS versions.
- Path Patterns, Custom Headers, and Viewer Protocol Policies: Set up default or custom path patterns (e.g., for JPEGs or HTML files) and configure policies to force redirection from HTTP to HTTPS.
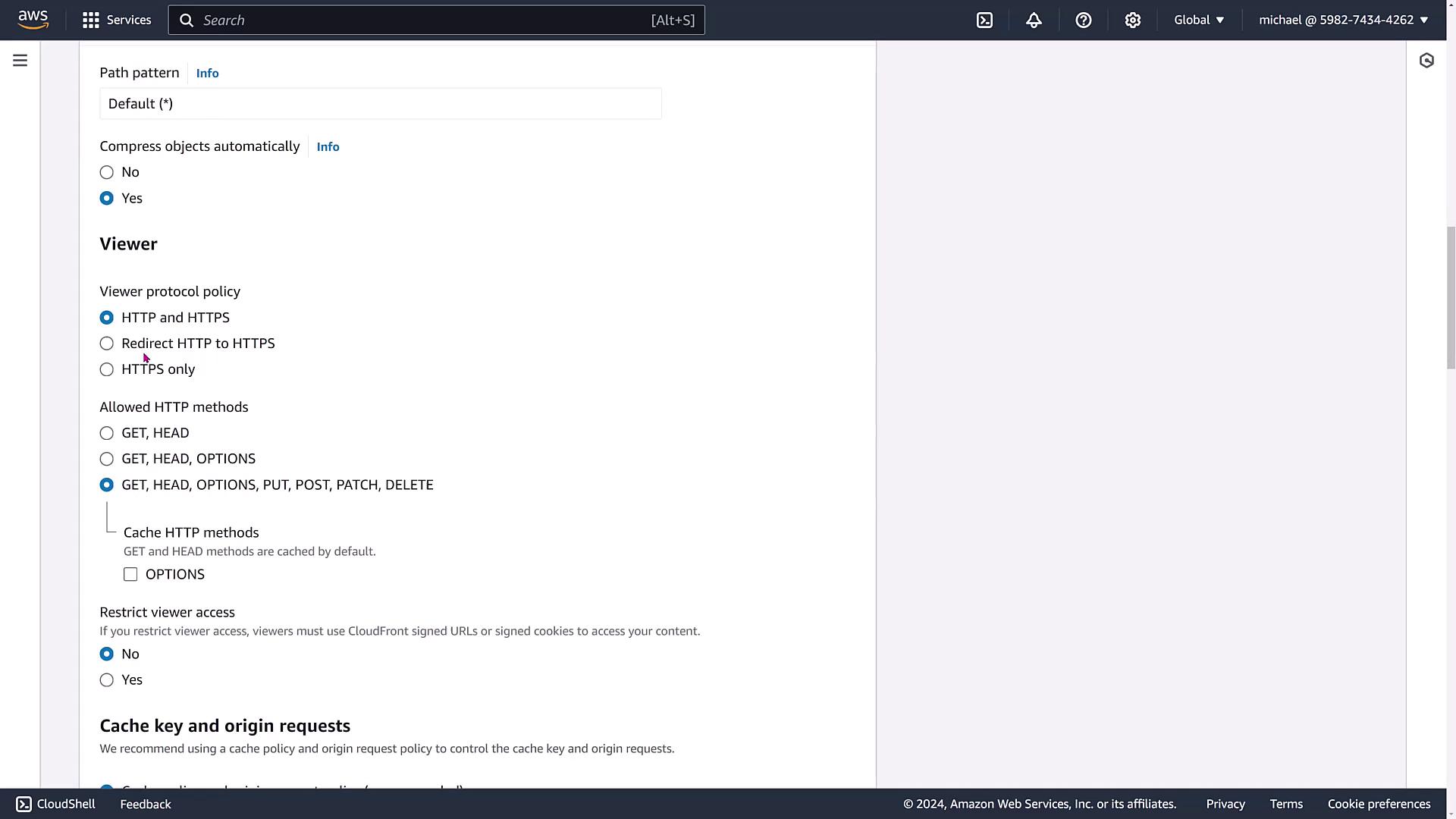
By default, CloudFront captures GET and HEAD requests, but you can enable other HTTP methods if needed. You also have the choice to use signed URLs or signed cookies to restrict access.
Cache Keys and Origin Requests
Beyond viewer settings, you can configure cache keys and origin requests. By setting up a cache policy, CloudFront can forward viewer request parameters to your Elastic Load Balancer, enhancing load balancing efficiency.
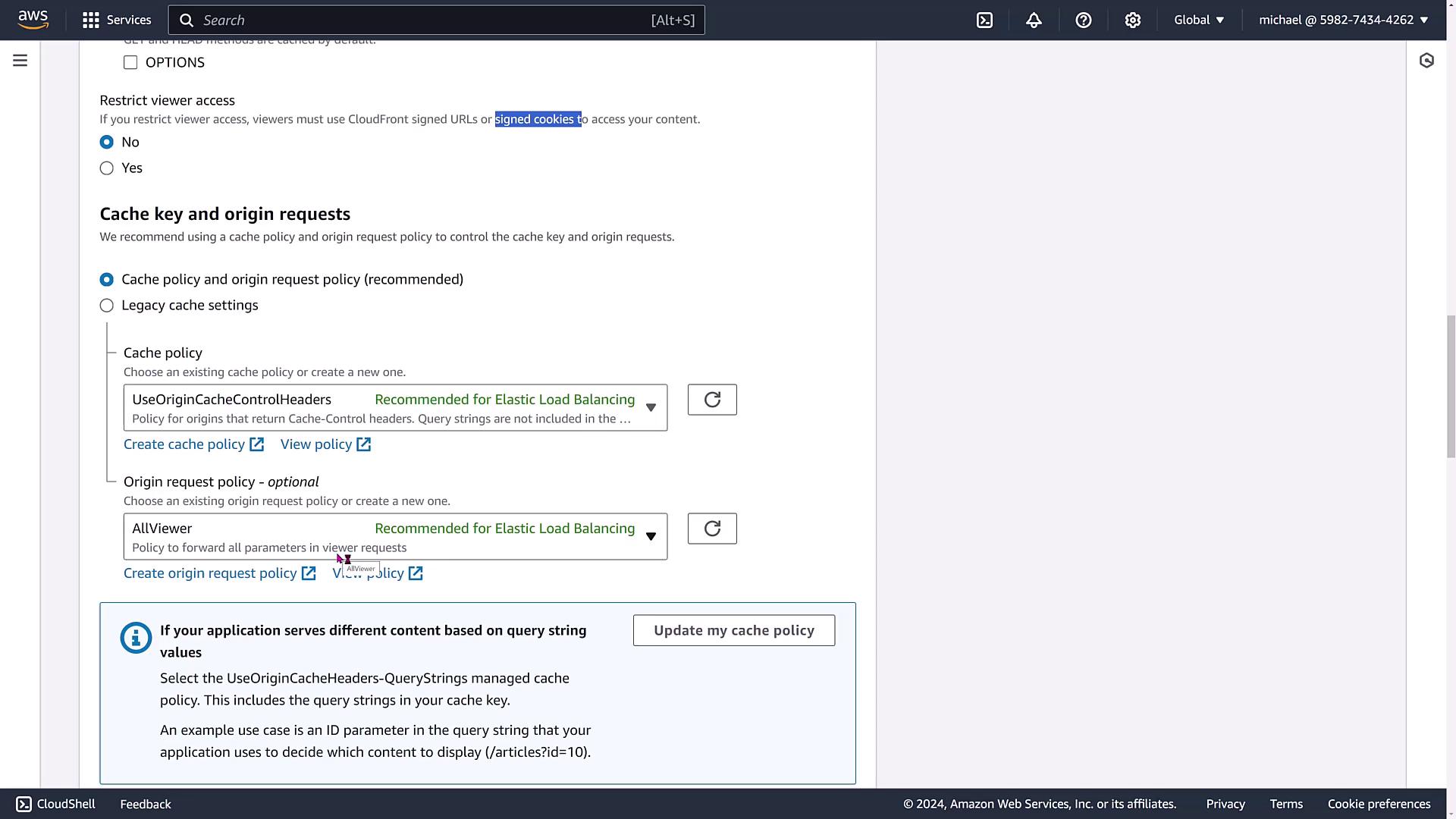
Additional advanced settings include:
- Leveraging Origin Cache Control headers.
- Defining response header policies for cross-origin resource sharing (CORS).
- Enabling support for smooth streaming in IIS.
- Configurations for field-level encryption, real-time logs, and CloudFront functions.
Note
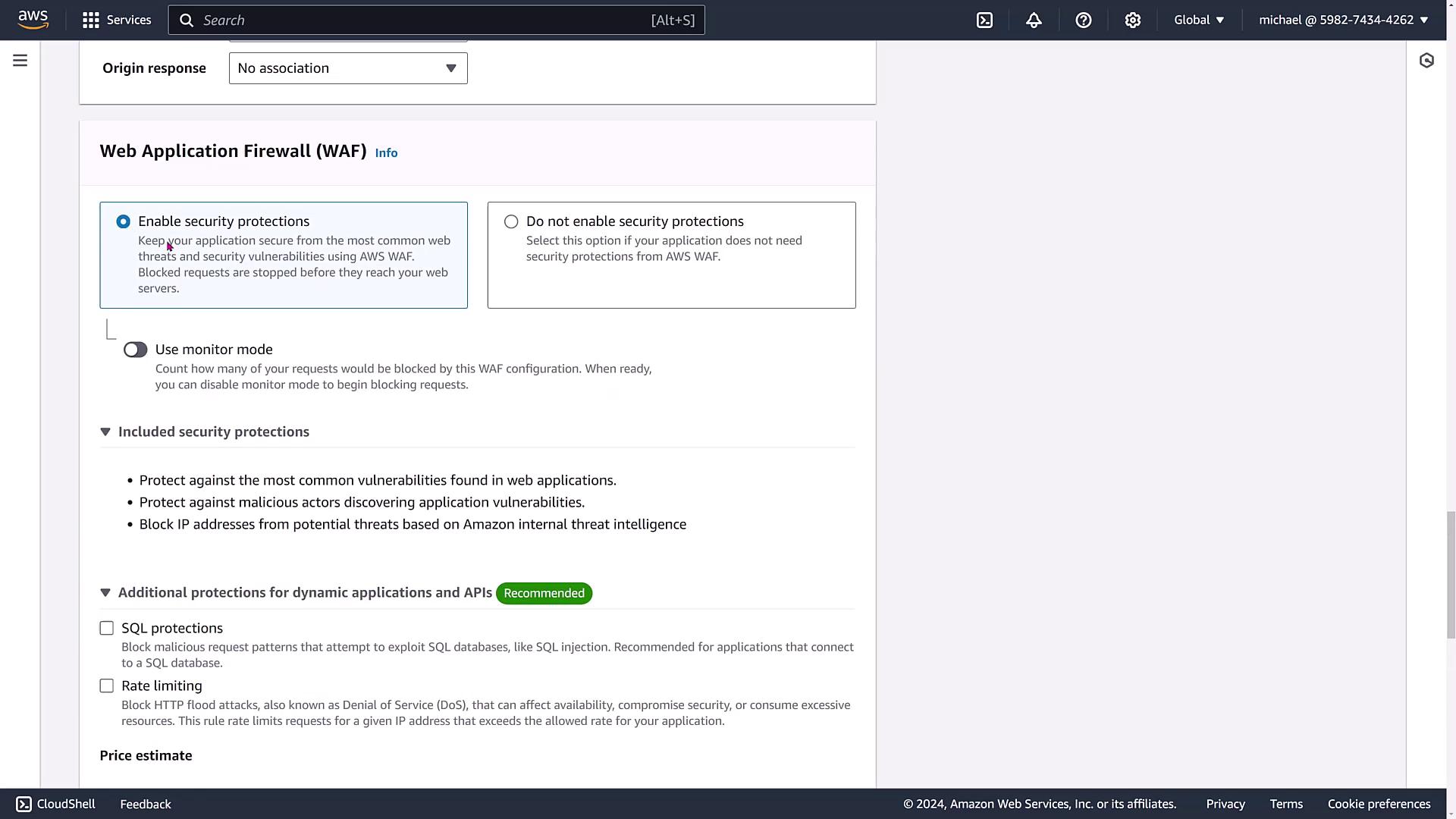
Customizing Distribution Properties
You can also refine your distribution by choosing which edge locations to utilize. By default, CloudFront serves all available locations, but you can restrict them to specific regions (e.g., North America and Europe) to enhance performance for users in targeted areas without significantly increasing costs.
Other customization options include:
- Adding alternate domain names (CNAMEs).
- Attaching your own SSL certificate (note that AWS Certificate Manager certificates must reside in Virginia).
- Configuring settings for newer HTTP versions, default root objects, centralized logging (with bucket and prefix configurations), and IPv6.
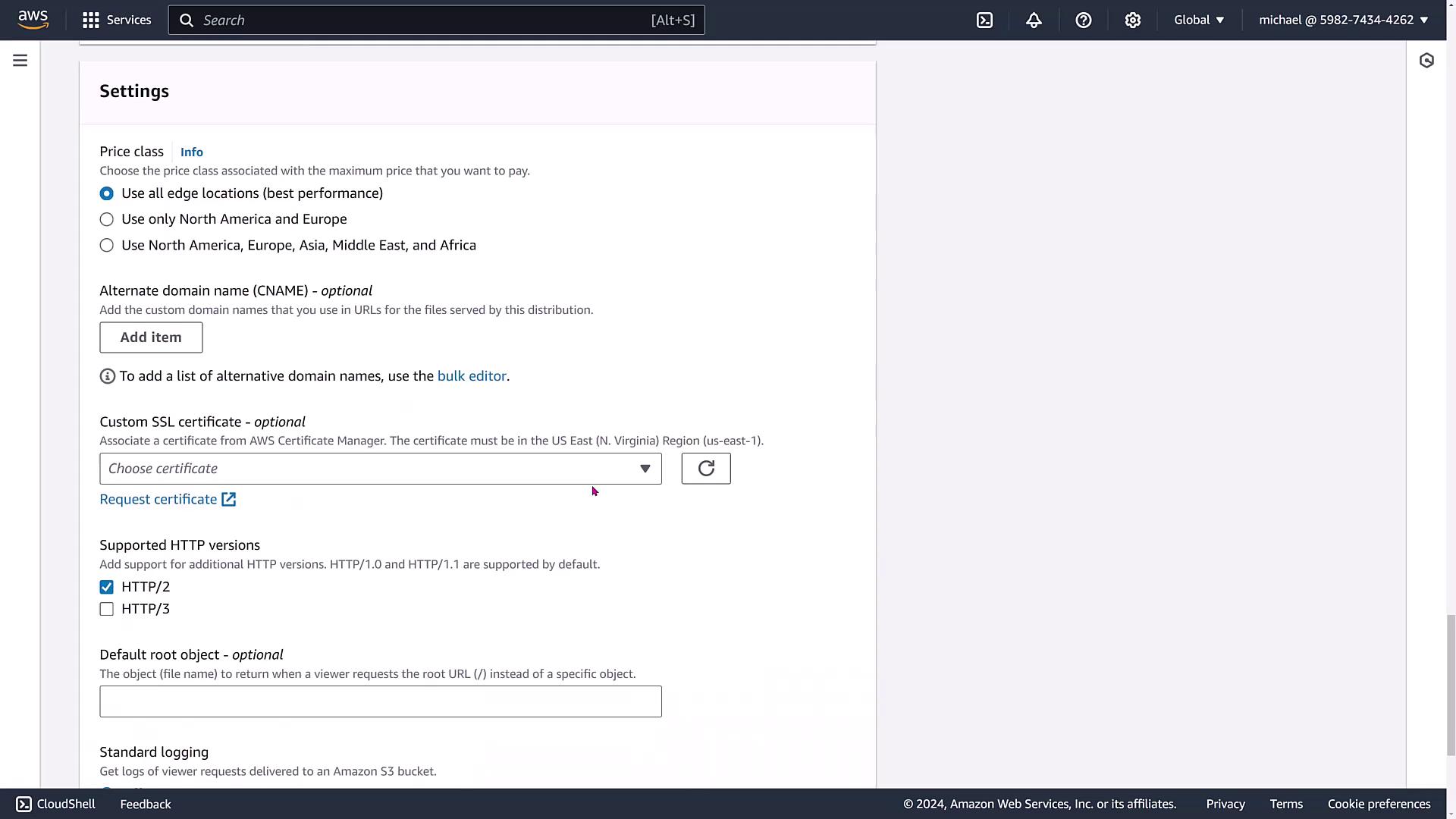
Once active, CloudFront automatically handles scaling. To demonstrate, let's examine an existing configuration with an origin signature. The provided DNS name is used to redirect users—via a CNAME or other redirection method—to the nearest CloudFront edge location.
The example distribution features standard logging, disabled cookie logging, basic security settings (with WAF and geographic restrictions turned off), and a simple setup. Geographic restrictions can be added later using an allowlist or blocklist.
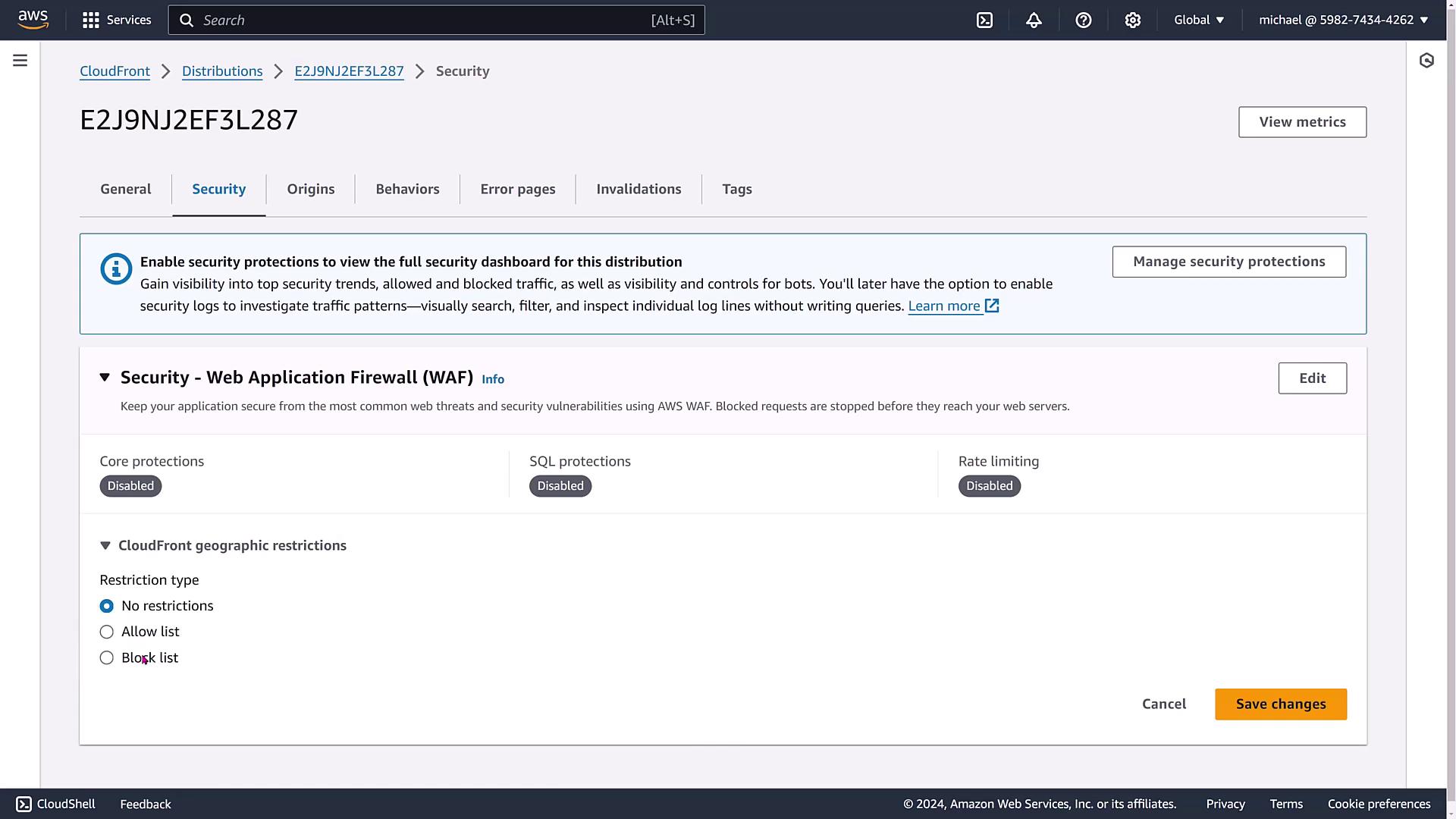
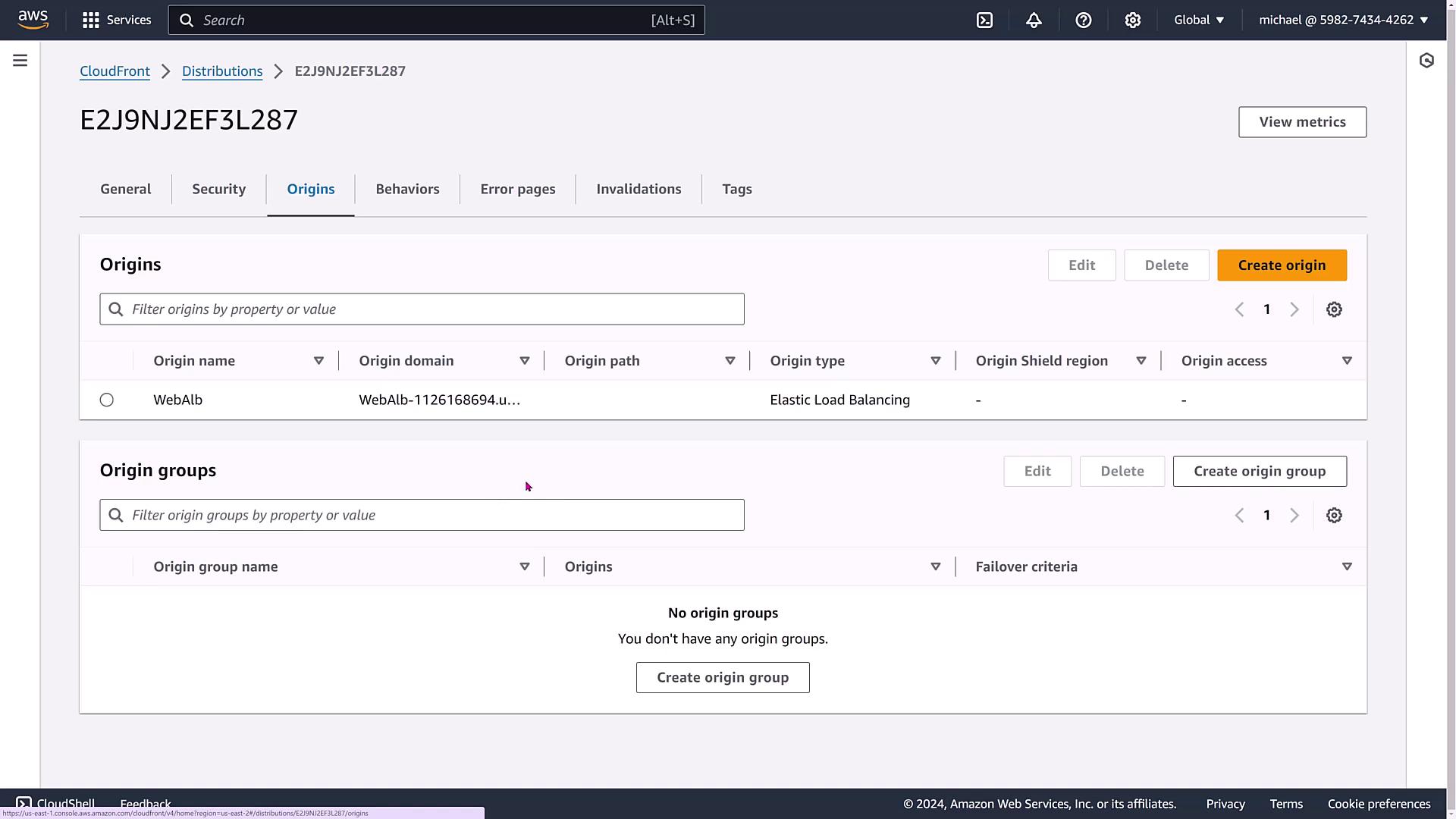
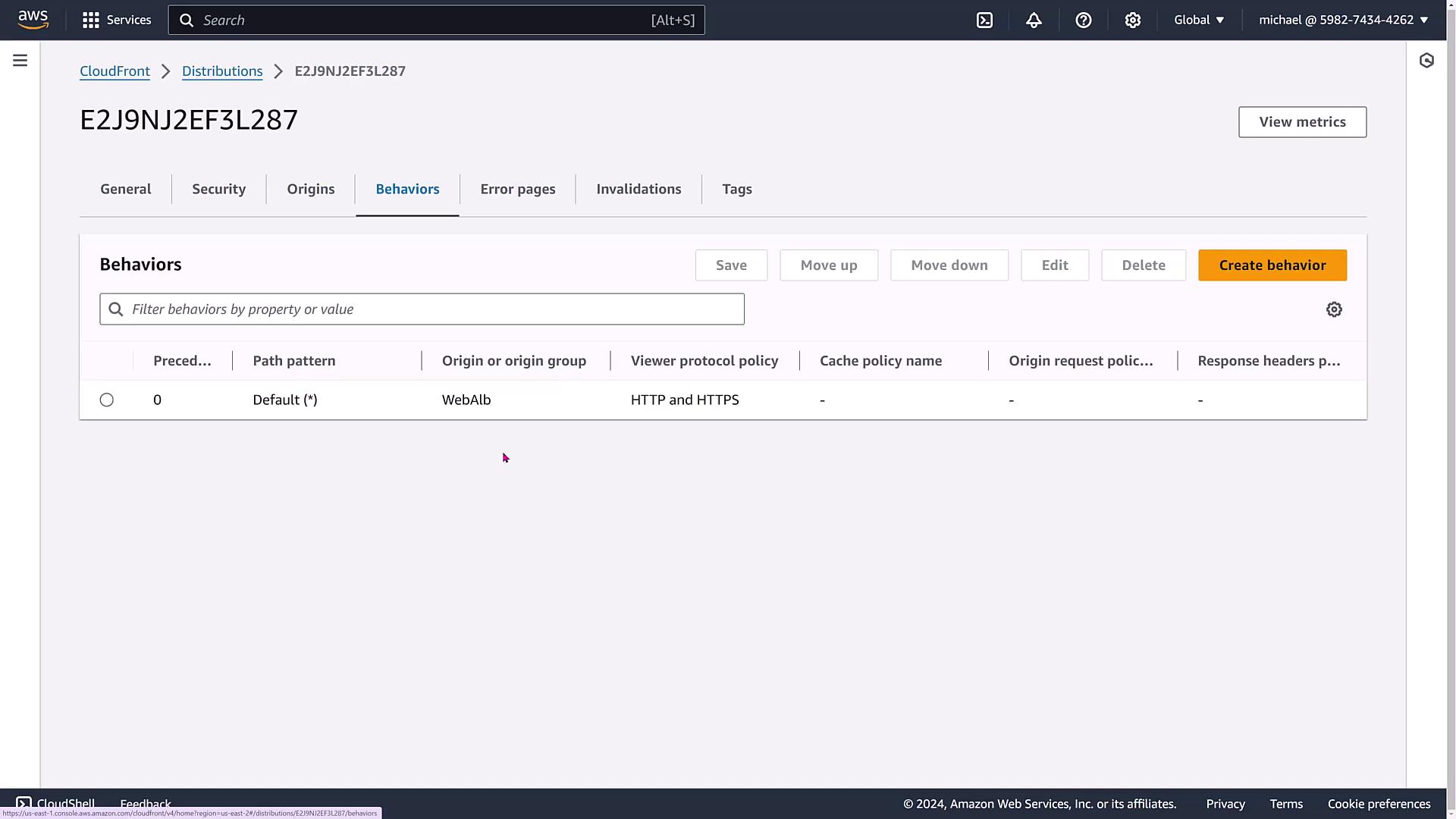
Managing Origins and Behaviors
CloudFront allows multiple origin configurations or origin groups that define primary and secondary failover behaviors.
Custom behaviors can direct some requests over HTTP while forcing HTTPS for others, depending on your application needs.
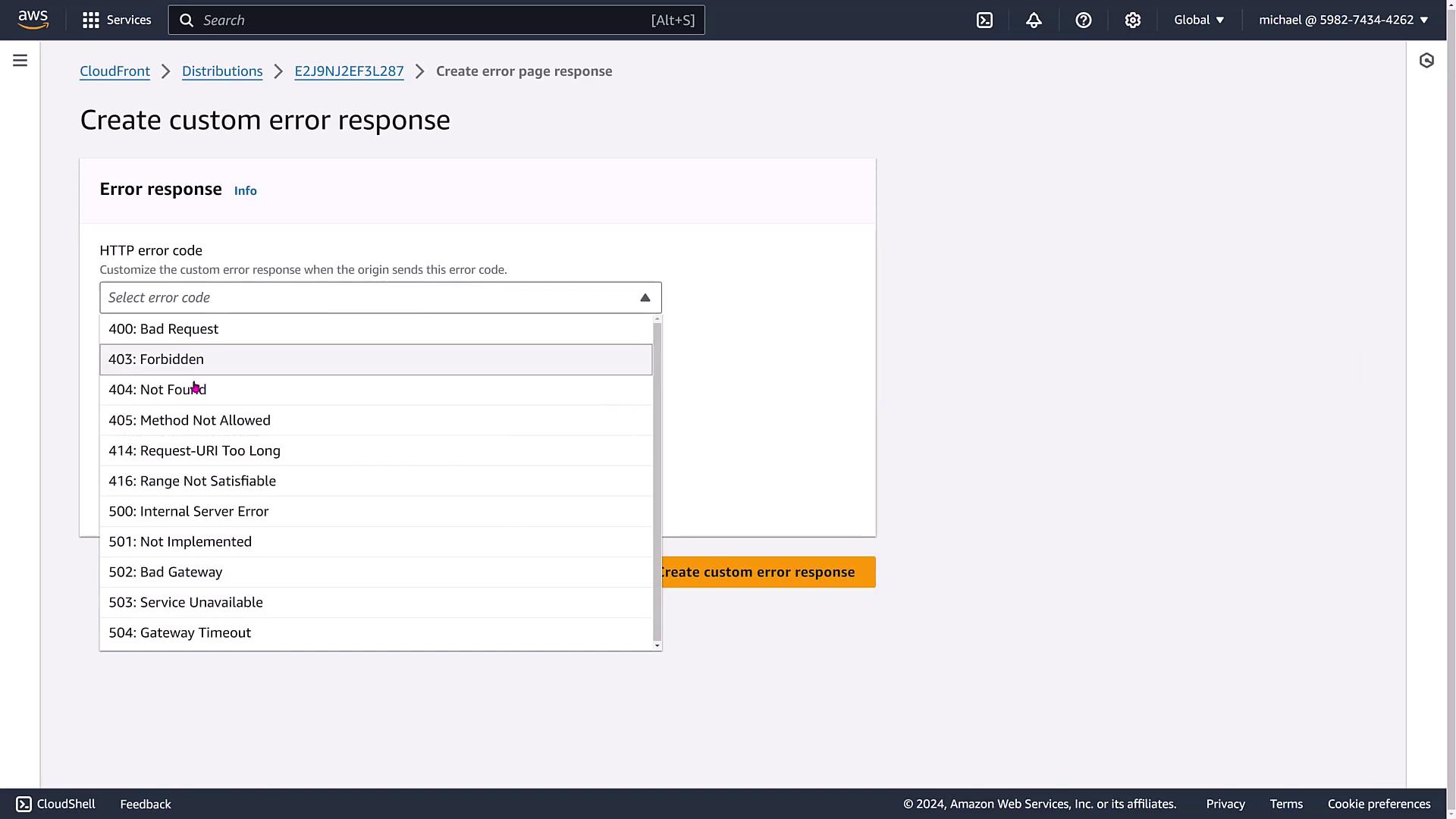
You can also define custom error pages (for example, a tailored 404 response) to provide a better user experience during errors.
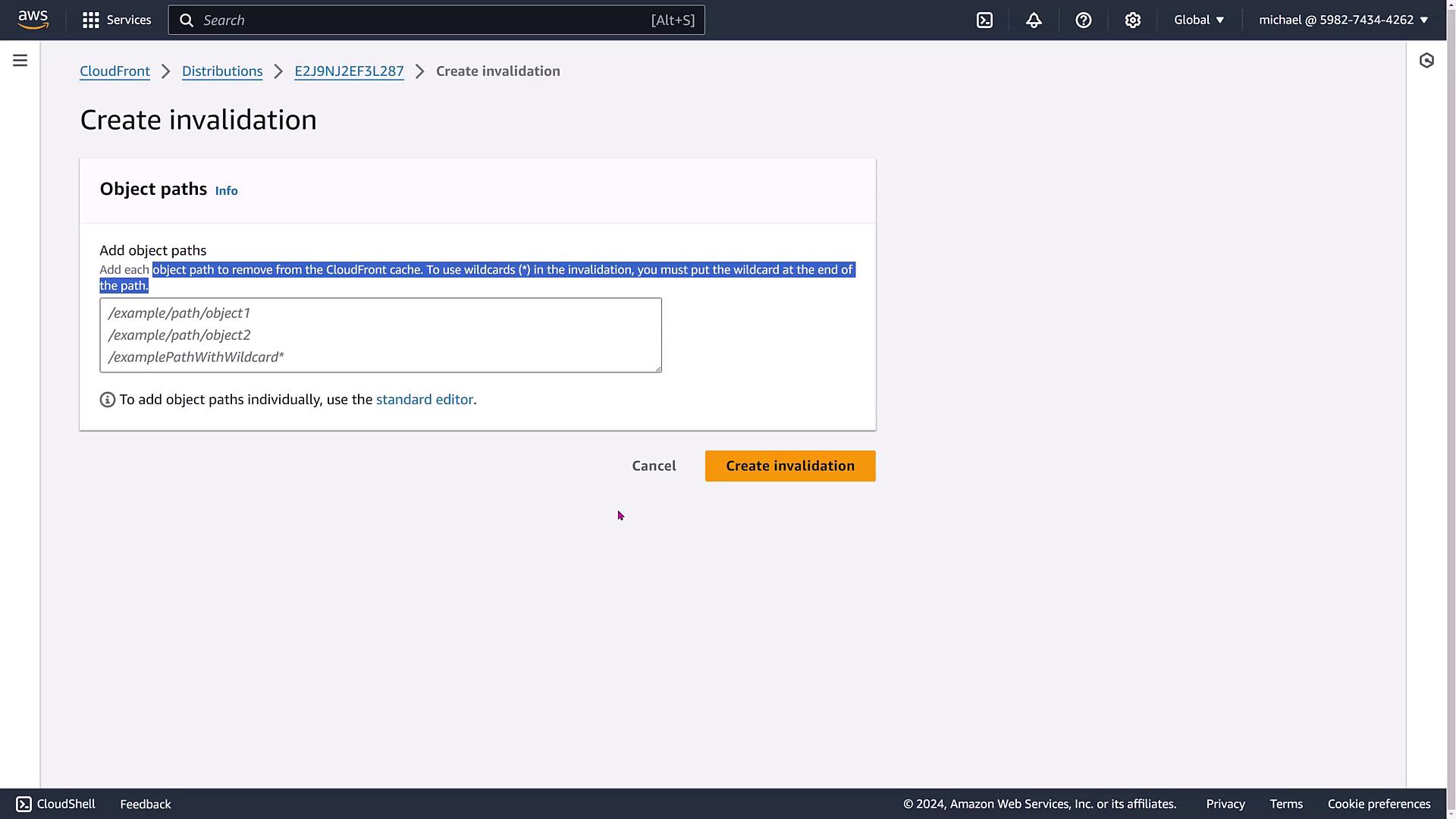
Handling Invalidations and Tags
Invalidations let you remove objects from the CloudFront cache if assets are updated. However, note that invalidations carry costs and impact your entire distribution. A more efficient approach is to version your assets (for example, picture_101.jpg, picture_102.jpg) when updates occur.
Tags can be applied to CloudFront distributions to help organize and manage your AWS resources efficiently.
Monitoring and Metrics
Once the distribution is active, navigate to the metrics dashboard to review key performance indicators, such as hit rates, request counts, and error rates. Even if no data appears immediately, this dashboard provides valuable insights as traffic increases. Metrics for CloudFront functions or Lambda@Edge events will also be displayed here.

Conclusion
This lesson has detailed the extensive configuration options available with CloudFront distributions. Key points include:
- A multitude of security features, such as field-level encryption and AWS WAF integration.
- Flexibility in choosing origins, path patterns, and caching policies.
- The ease of scaling distributions and the ability to customize error responses and behaviors.
- Robust monitoring capabilities to keep track of distribution performance.
Final Note
That's it for this lesson. We'll catch you in the next article.
Watch Video
Watch video content
Practice Lab
Practice lab