Overview
Network-to-network connectivity by VPC peering involves linking one VPC directly to another. By design, VPCs serve as isolated boundaries within your cloud environment. While you may have distinct VPCs for production and development, there are occasions when these networks need to communicate. AWS’s Transit Gateway is a robust solution for connecting multiple VPCs. However, VPC peering remains the original and straightforward option to connect two VPCs. Importantly, although our example depicts VPCs in the same region, VPC peering also supports cross-region connectivity. For instance, a VPC in the Tokyo region can seamlessly connect with one in the Virginia region.
Private Connectivity and Cross-Account Support
VPC peering leverages AWS’s private backbone network, eliminating the need for public connectivity—even when using private subnets. This feature also supports cross-account connections, enabling you to connect VPCs owned by different AWS accounts as well as those in different regions.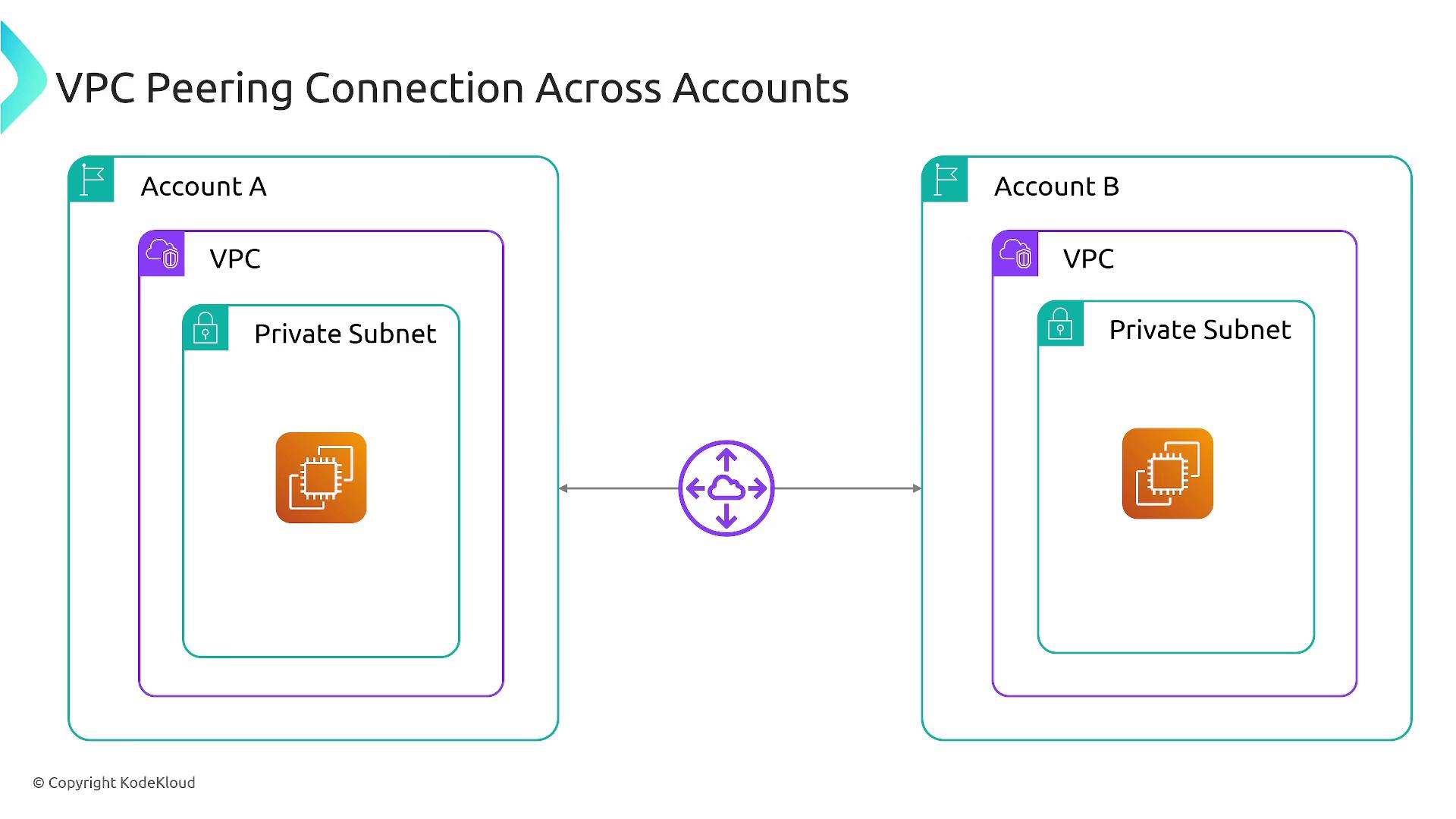
VPC Peering vs. Transit Gateway
VPC peering provides a one-to-one connection, meaning if VPC A is peered with VPC B and VPC C, there is no transitive routing between B and C through A. For scenarios that require connecting multiple VPCs or transitive connectivity, AWS Transit Gateway may be a more flexible solution.
How VPC Peering Works
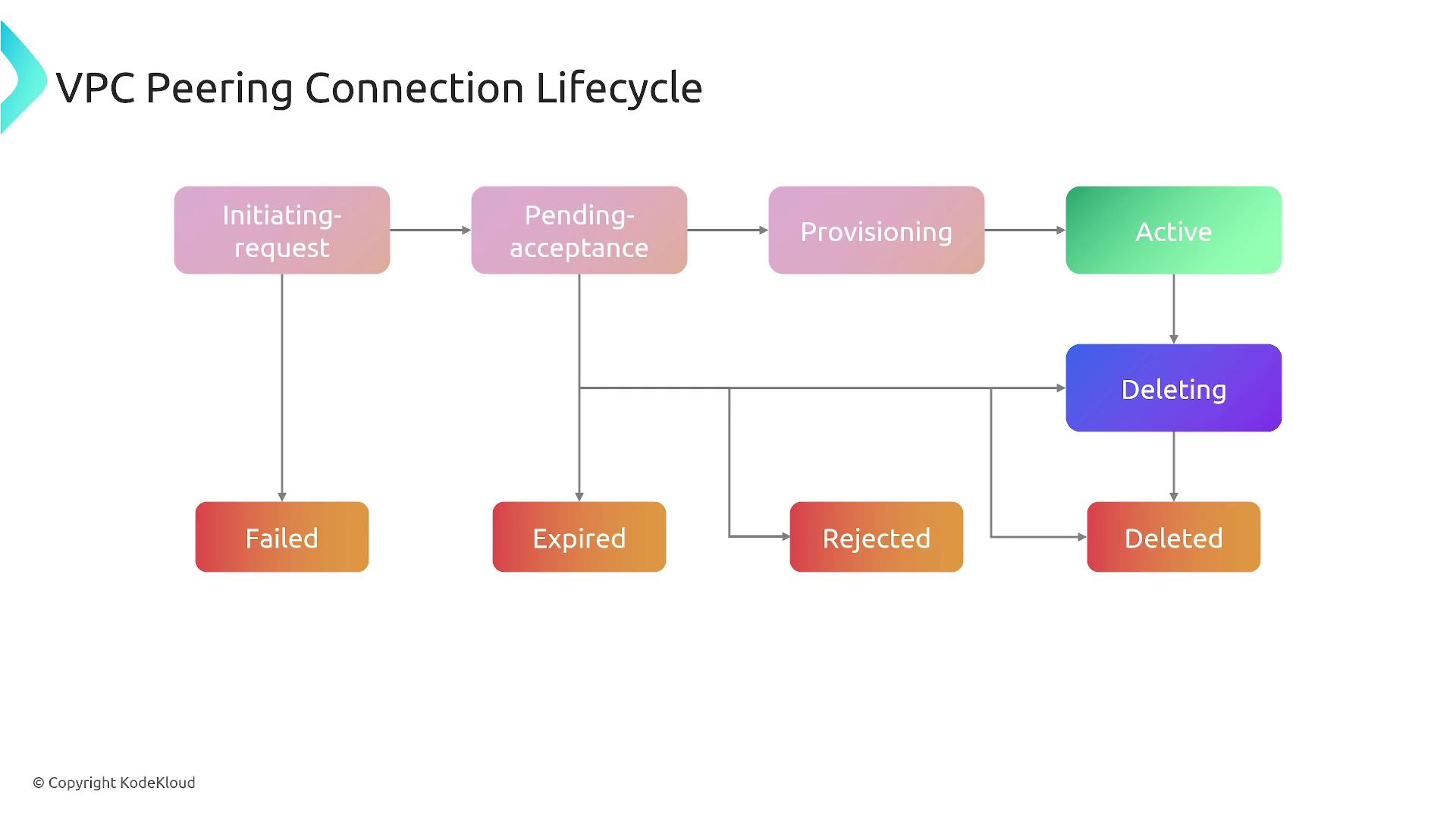
Establishing a VPC peering connection involves the following steps:- The owner of a VPC initiates a peering request to the target VPC.
- AWS notifies both parties via email and the AWS Management Console that a peering request is pending.
- Once the target VPC accepts the request, update the route tables on both VPCs to enable direct communication.
Ensure that the IP address ranges (CIDR blocks) of the peered VPCs do not overlap. For example:
- Two VPCs configured with /16 CIDR blocks (like 10.10.0.0/16) would conflict.
- Using distinct CIDR blocks (such as 10.10.0.0/24 and 10.10.1.0/24) avoids conflicts. For IPv6, overlapping is typically not an issue since every address is unique.
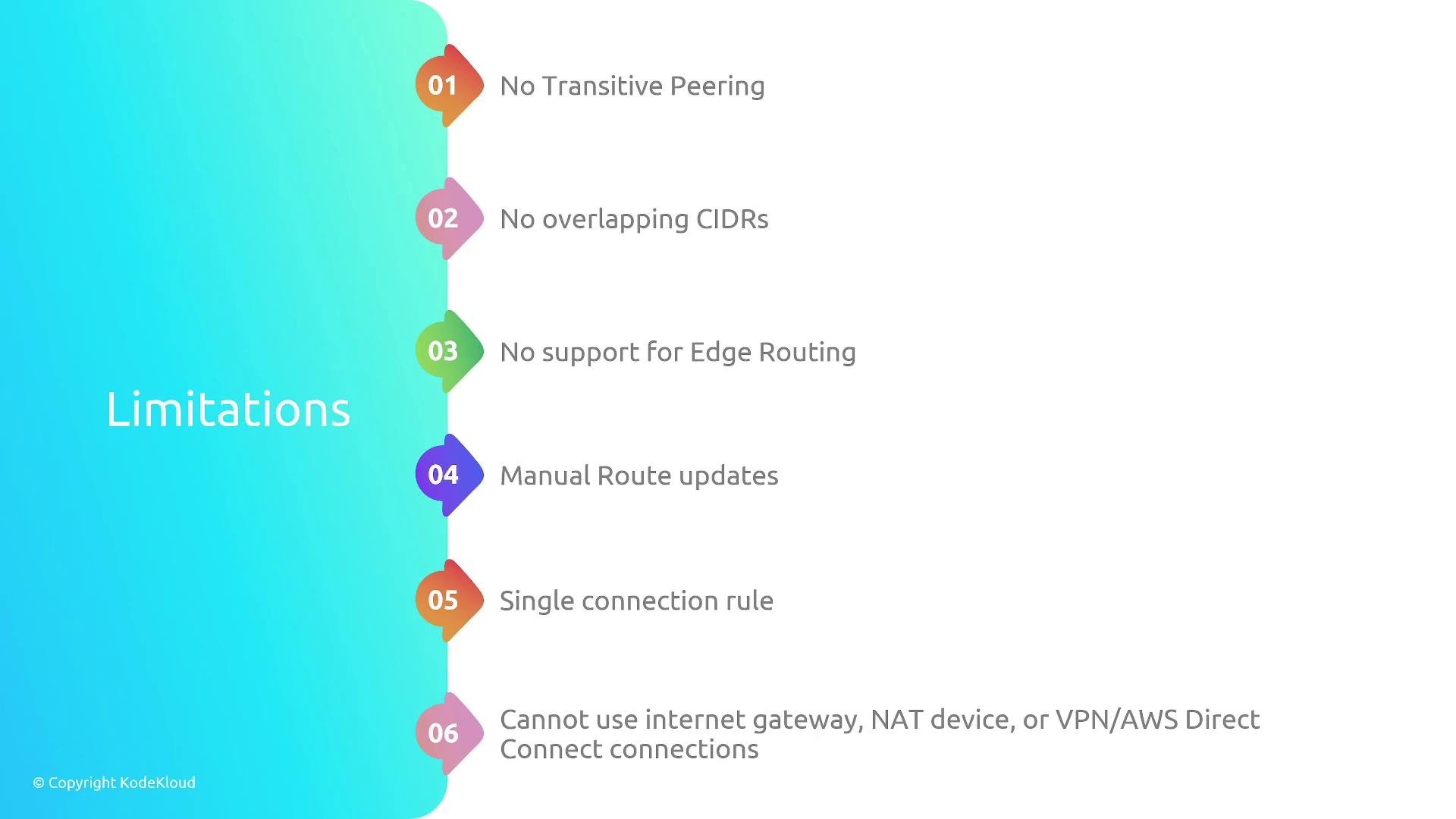
Important Considerations
-
Non-transitive Nature:
VPC peering is strictly one-to-one. Even if VPC A is peered with both VPC B and VPC C, B and C cannot communicate through A. A direct peering connection is needed for those VPCs to interact. -
IP Address Overlap:
Always check that the CIDR blocks of the peered VPCs do not overlap—overlapping addresses prevent proper routing between networks. -
No Edge Routing:
VPC peering does not support edge routing. Unlike Transit Gateway, which provides advanced routing features, VPC peering requires manual updating of each VPC’s route table. -
Latency Considerations:
When peering VPCs across regions, even though connections use AWS’s backbone, the physical distance may introduce latency. This could affect performance in high-traffic scenarios.