External Secret Store Backends
For full control over sensitive data, choose a dedicated secret store. Below is a comparison of popular backends:| Provider | Use Case | Key Features |
|---|---|---|
| HashiCorp Vault | On-premises or self-managed clusters | Encryption, dynamic credentials, access policies |
| AWS Secrets Manager | EKS and AWS-hosted workloads | Automatic rotation, versioning, audit trails |
| AWS Systems Manager Parameter Store | Configuration & secrets | Hierarchical params, secure strings |

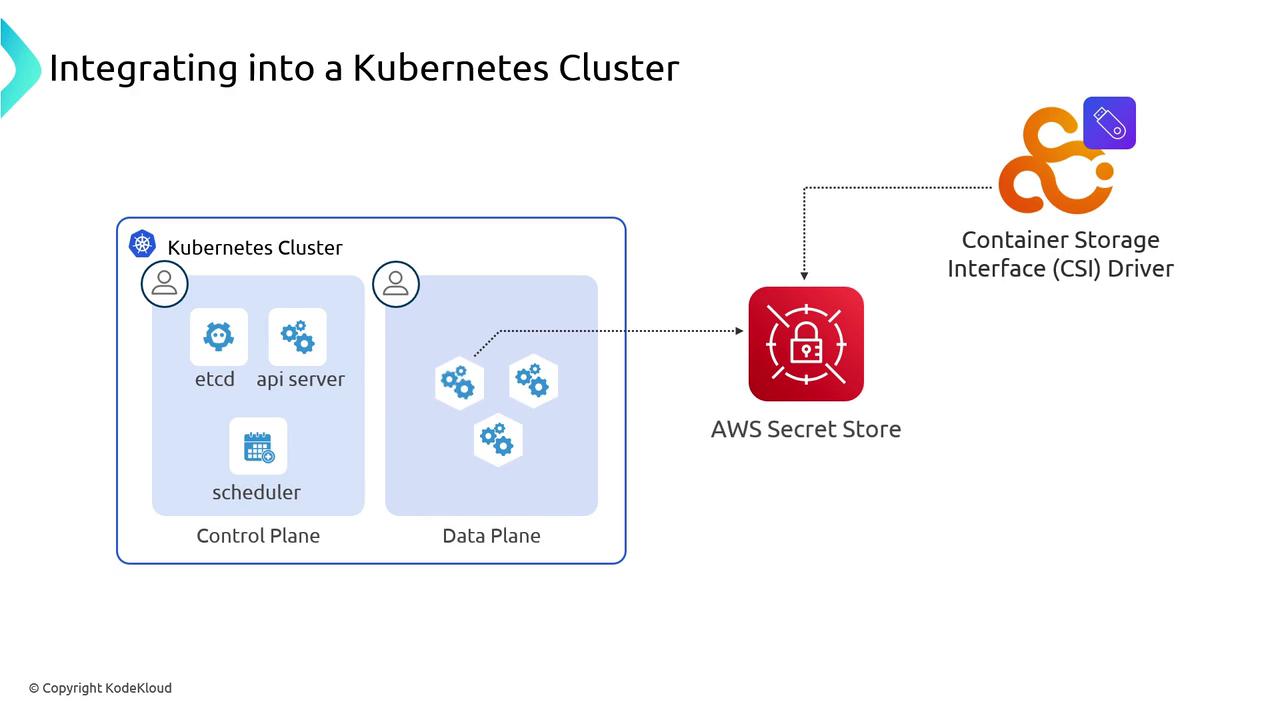
Secret Store CSI Driver
The Secrets Store CSI driver lets you mount external secrets into pods without embedding SDKs:- Fetches secrets from your chosen backend.
- Exposes them as files on a read-only volume.
- Optionally syncs them into native Kubernetes Secret objects.
The CSI driver follows the Kubernetes CSI specification to integrate external stores as volumes.
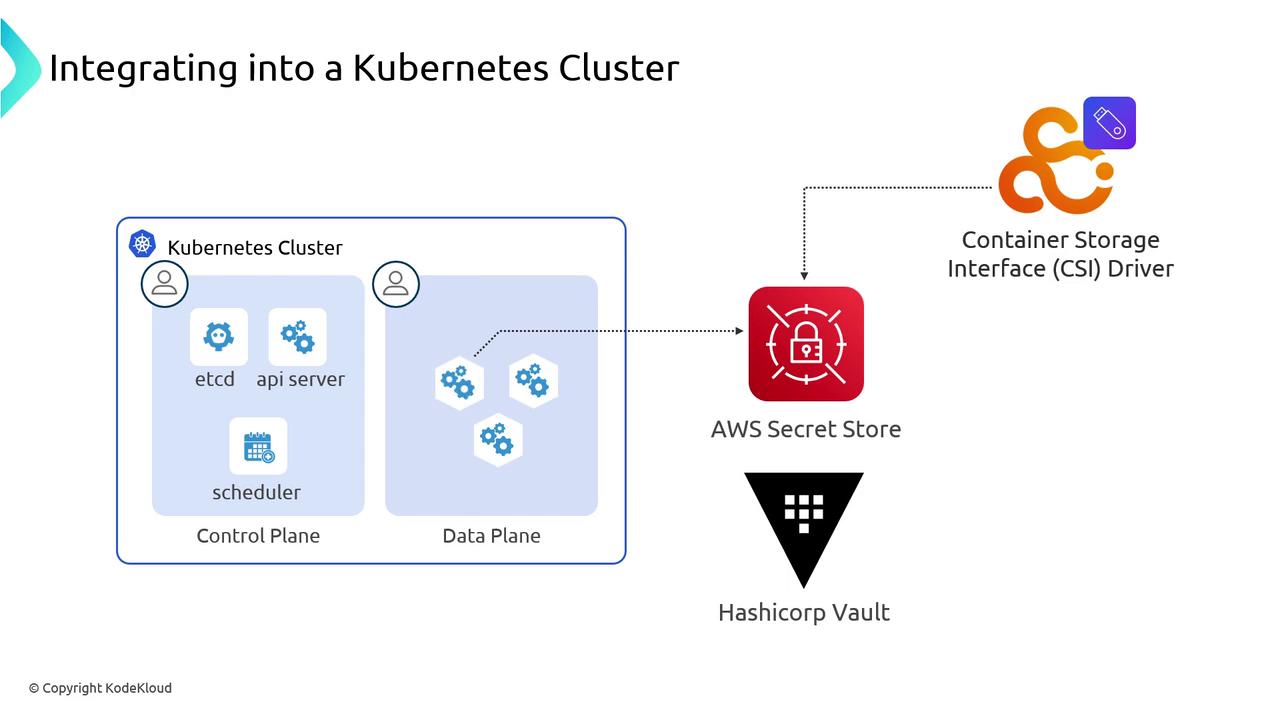
Multi-Backend Support
The Secrets Store CSI driver is provider-agnostic. Supported backends include:- AWS Secrets Manager
- AWS Systems Manager Parameter Store
- HashiCorp Vault
- Microsoft Azure Key Vault
- Google Cloud Secret Manager
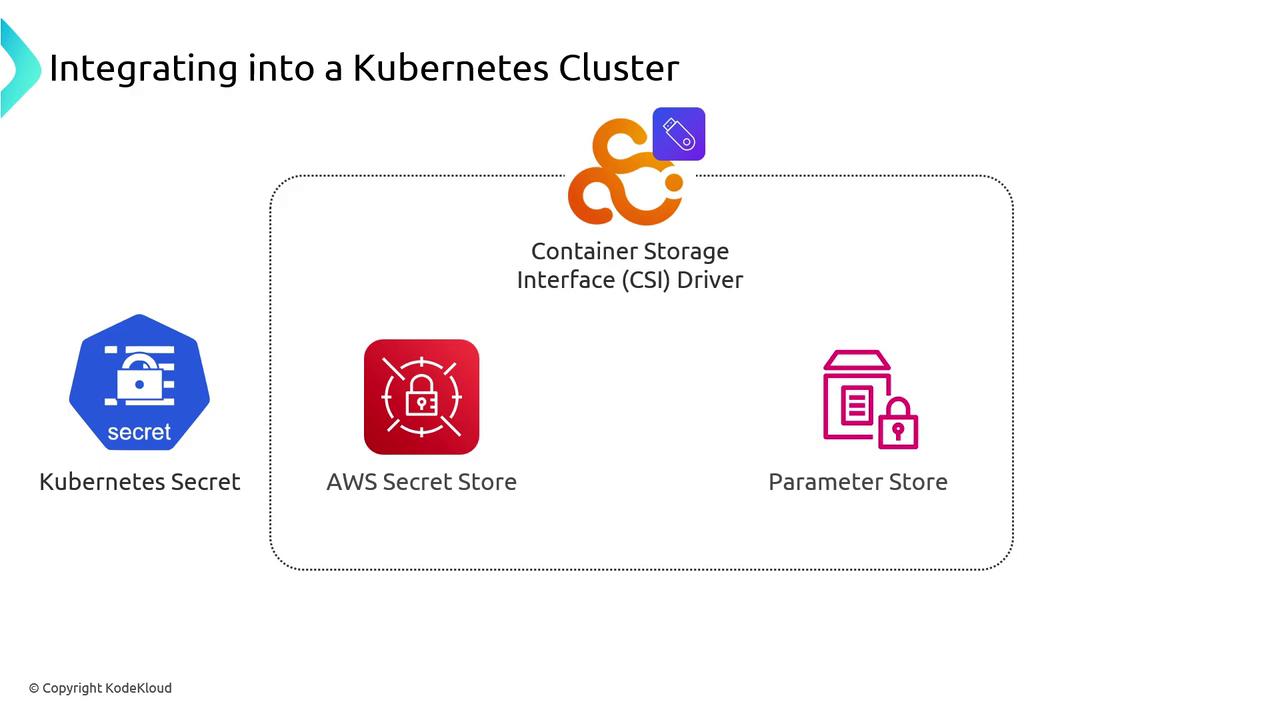
AWS CSI Driver for Secrets & Config
AWS offers a dedicated CSI provider that mounts both Secrets Manager and Parameter Store entries as volumes—eliminating the need for ConfigMaps or Kubernetes Secrets:- Secrets Manager: Encrypted, versioned secrets with rotation
- Parameter Store: Hierarchical configuration values and secure strings
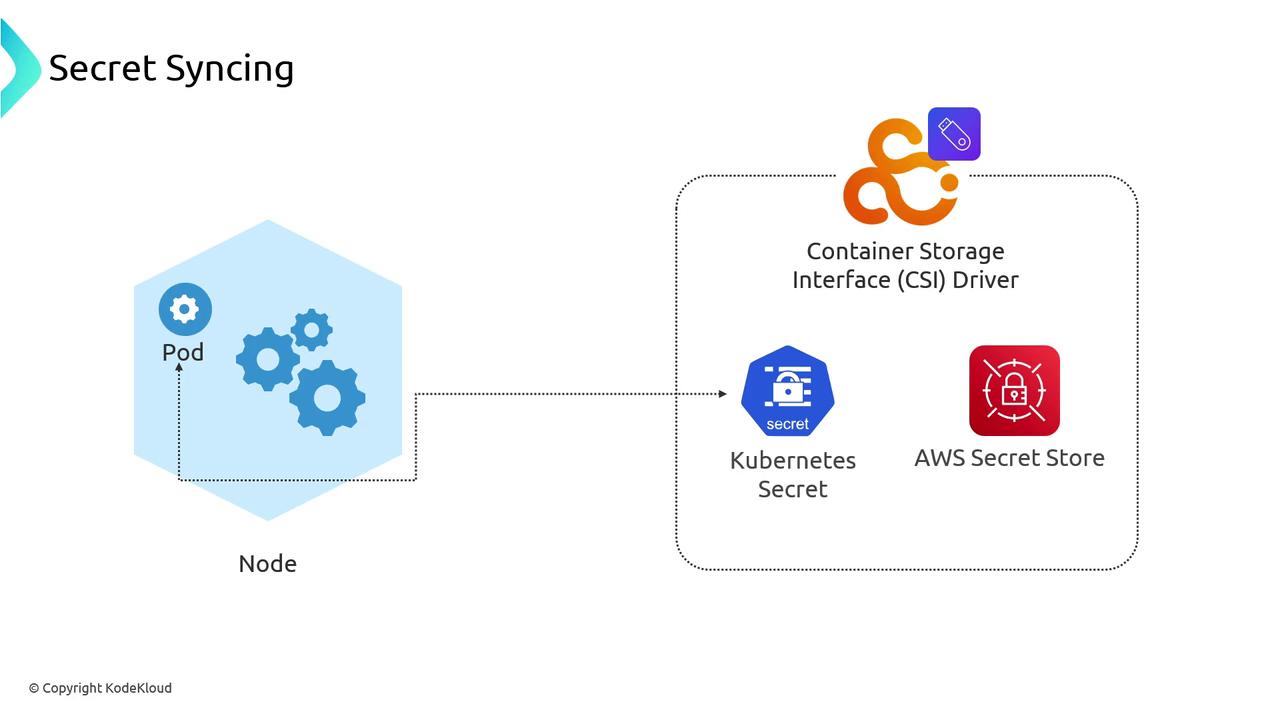
Syncing to Native Kubernetes Secrets
If your pods rely on in-cluster Secrets (e.g., for environment variables), enable “secret syncing”:- CSI driver fetches from the external store
- Creates a temporary Kubernetes Secret
- Mounts or injects it into the pod
- Deletes the synced Secret on pod termination
Synced Secrets are stored as standard Kubernetes Secrets. Ensure RBAC policies restrict access to these temporary Secrets.
Automatic Rotation
Most external secret stores support credential rotation. Configure the CSI driver’s refresh interval or restart pods to pick up new versions automatically:- Versioned secrets ensure rollbacks if issues arise.
- Rotation schedules can trigger updates without downtime.
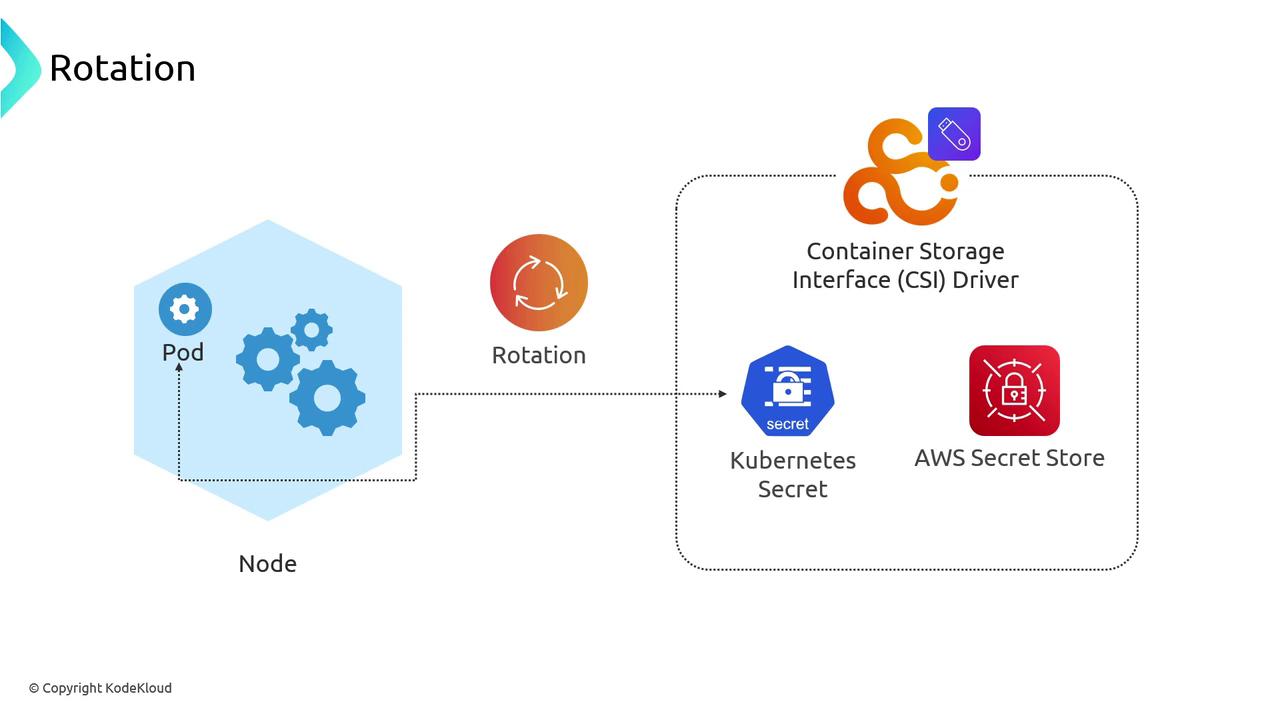
Pod Identity and IRSA
Use Pod Identity or AWS IAM Roles for Service Accounts (IRSA) so that workloads assume an IAM role and fetch secrets without embedded credentials:- Eliminates long-lived access keys in containers.
- Leverages cloud provider identity mechanisms.
Key Takeaways
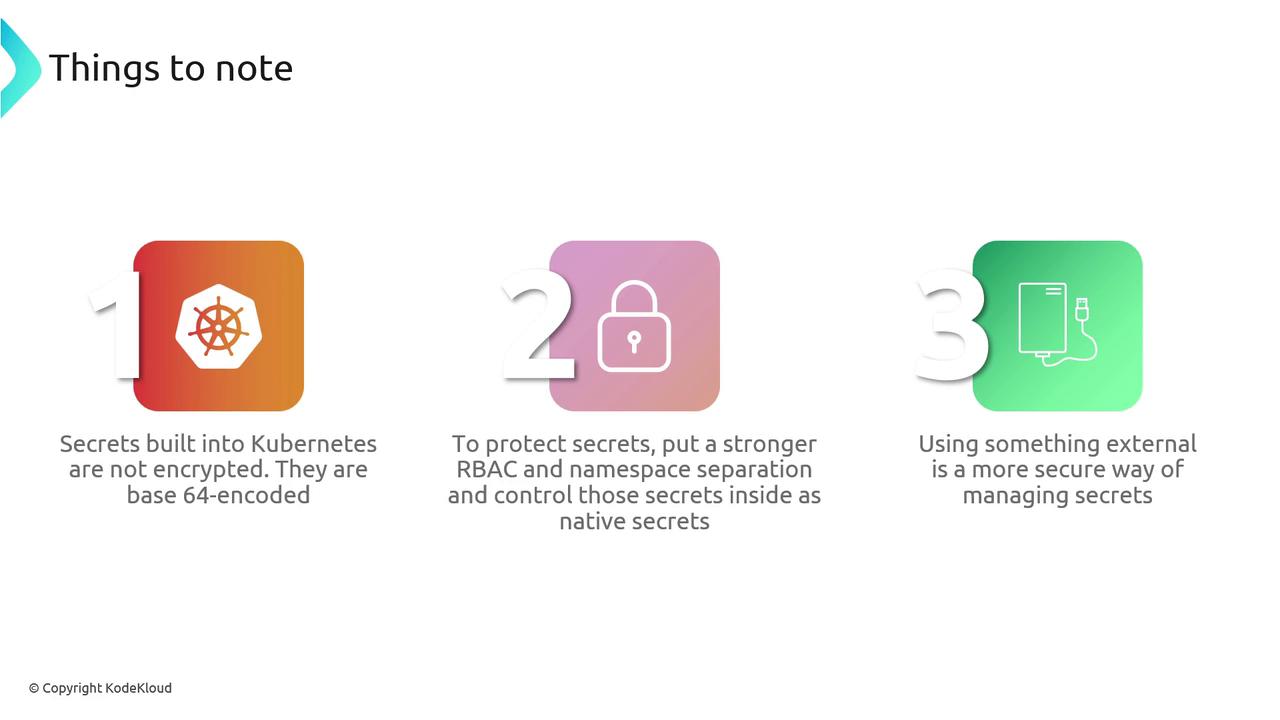
- Kubernetes Secrets are Base64-encoded by default, not encrypted.
- Strengthen cluster security with RBAC and namespace isolation.
- The most robust solution uses an external secret store plus the CSI driver for encryption, rotation, and auditability.