company1-logs. By leveraging IAM roles, you avoid hardcoding credentials on your server and follow AWS best practices for secure access management.
Prerequisites
- An AWS account with administrative privileges
- A running EC2 instance
- An existing S3 bucket named
company1-logs
Step 1: Create the IAM Role
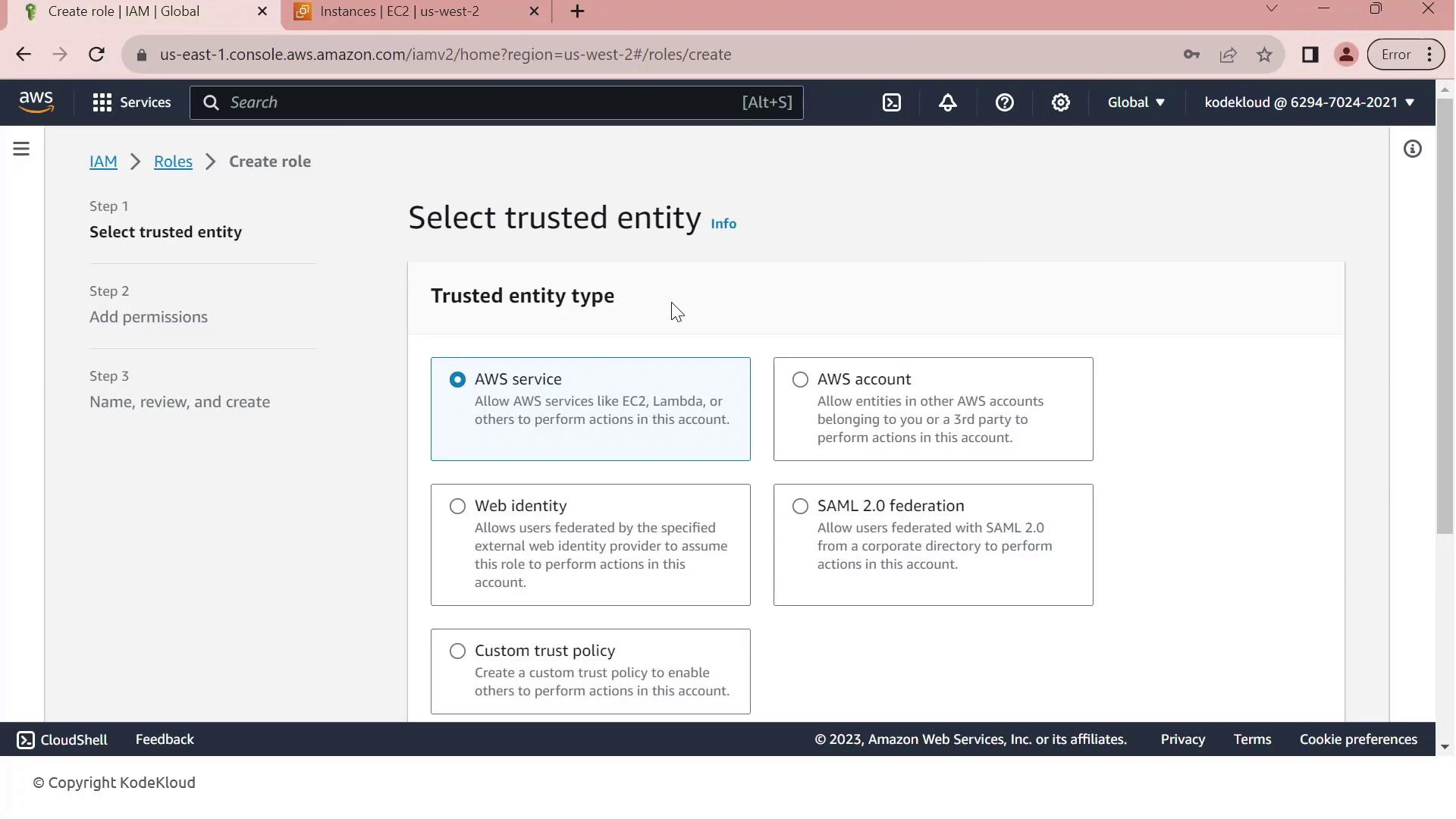
- Open the IAM console, select Roles, then click Create role.
- On Select trusted entity, choose AWS service.
- Under Use cases for other AWS services, select EC2.
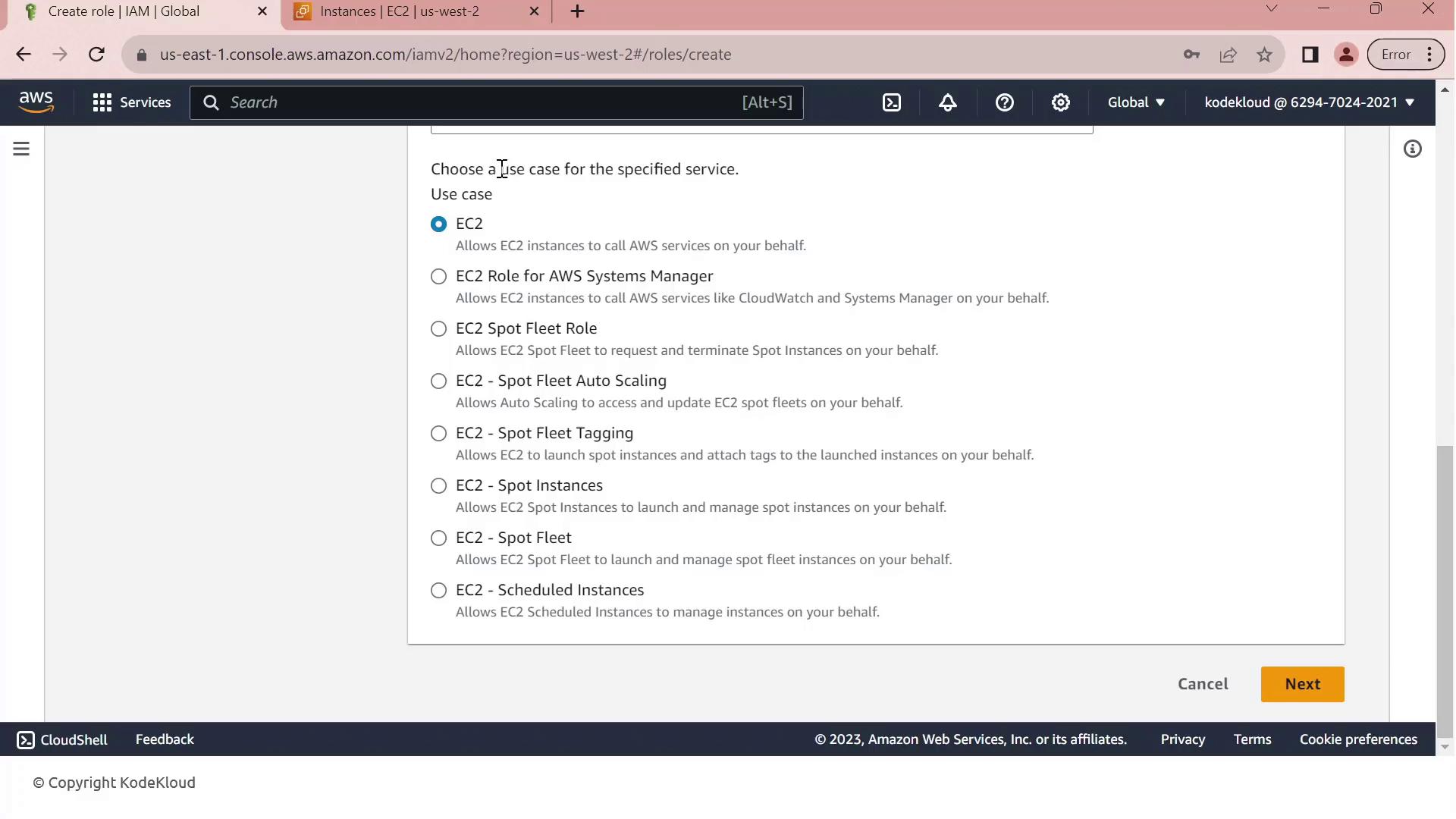
- Click Next to move to the permissions page.
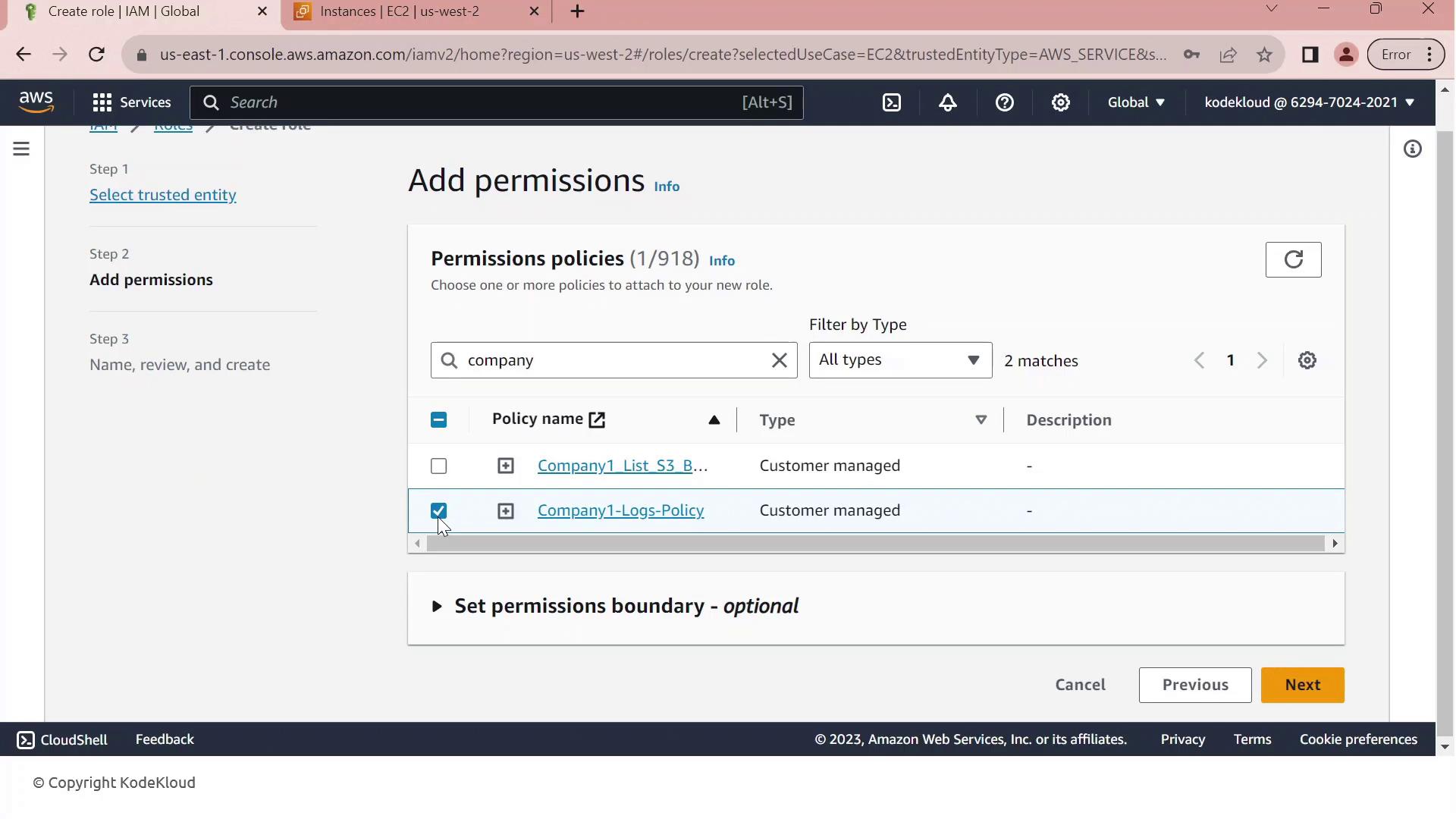
- In Permissions, search for company1 and select the Company1 logs policy which grants
s3:GetObjectaccess to thecompany1-logsbucket.
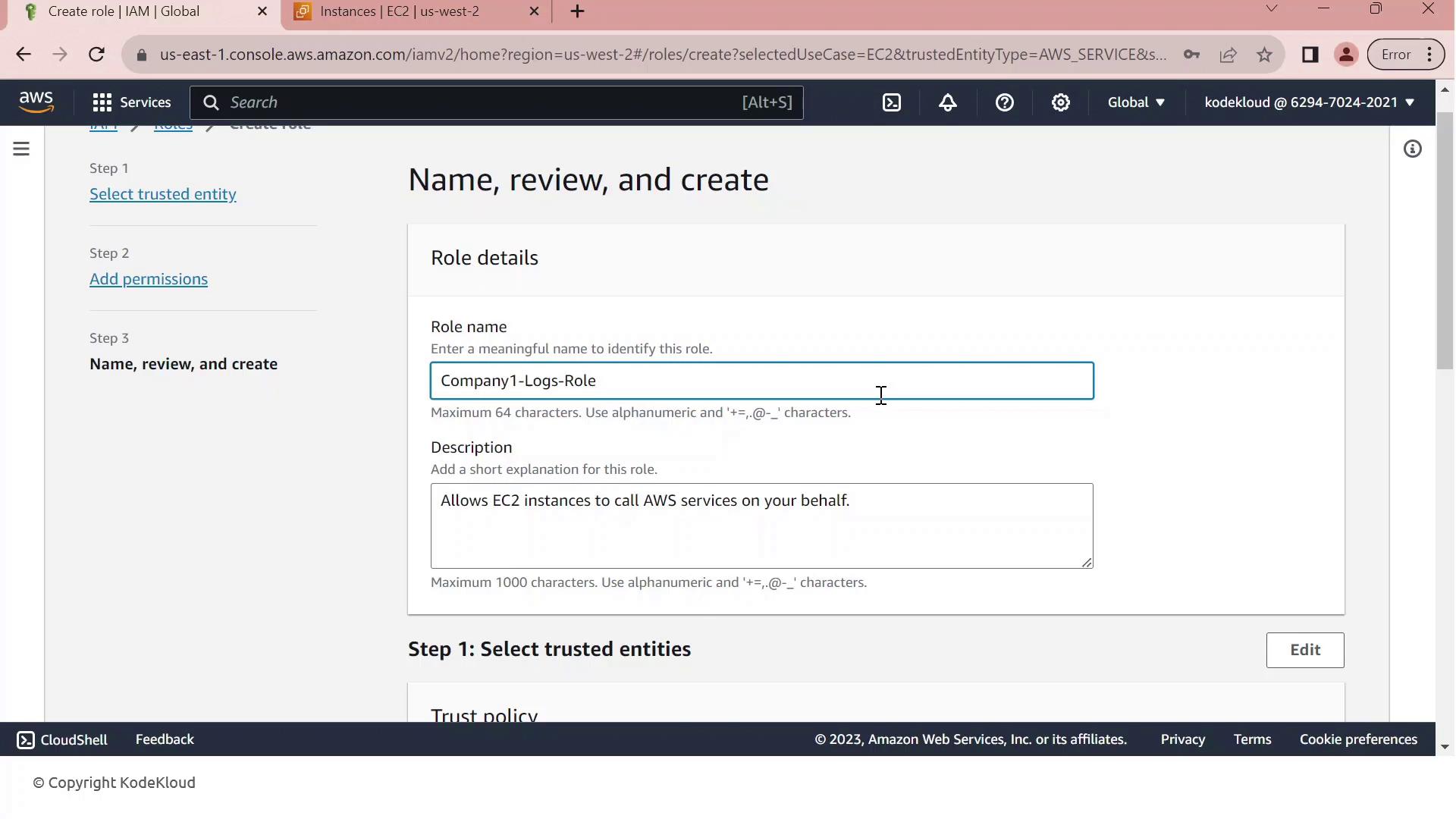
- Click Next, then enter a Role name (e.g.,
Company1-Logs-Role) and an optional description.
-
Review the Trust relationship to ensure EC2 can assume this role. It should resemble:
- (Optional) Add tags to categorize your role, then click Create role.
You’ve successfully created an IAM role that EC2 instances can assume to access S3 resources securely.
Step 2: Attach the IAM Role to Your EC2 Instance
- Go to the EC2 console, select Instances, and choose your running instance.
- From the Actions menu, select Security > Modify IAM role.
- In the IAM role dropdown, pick Company1-Logs-Role.
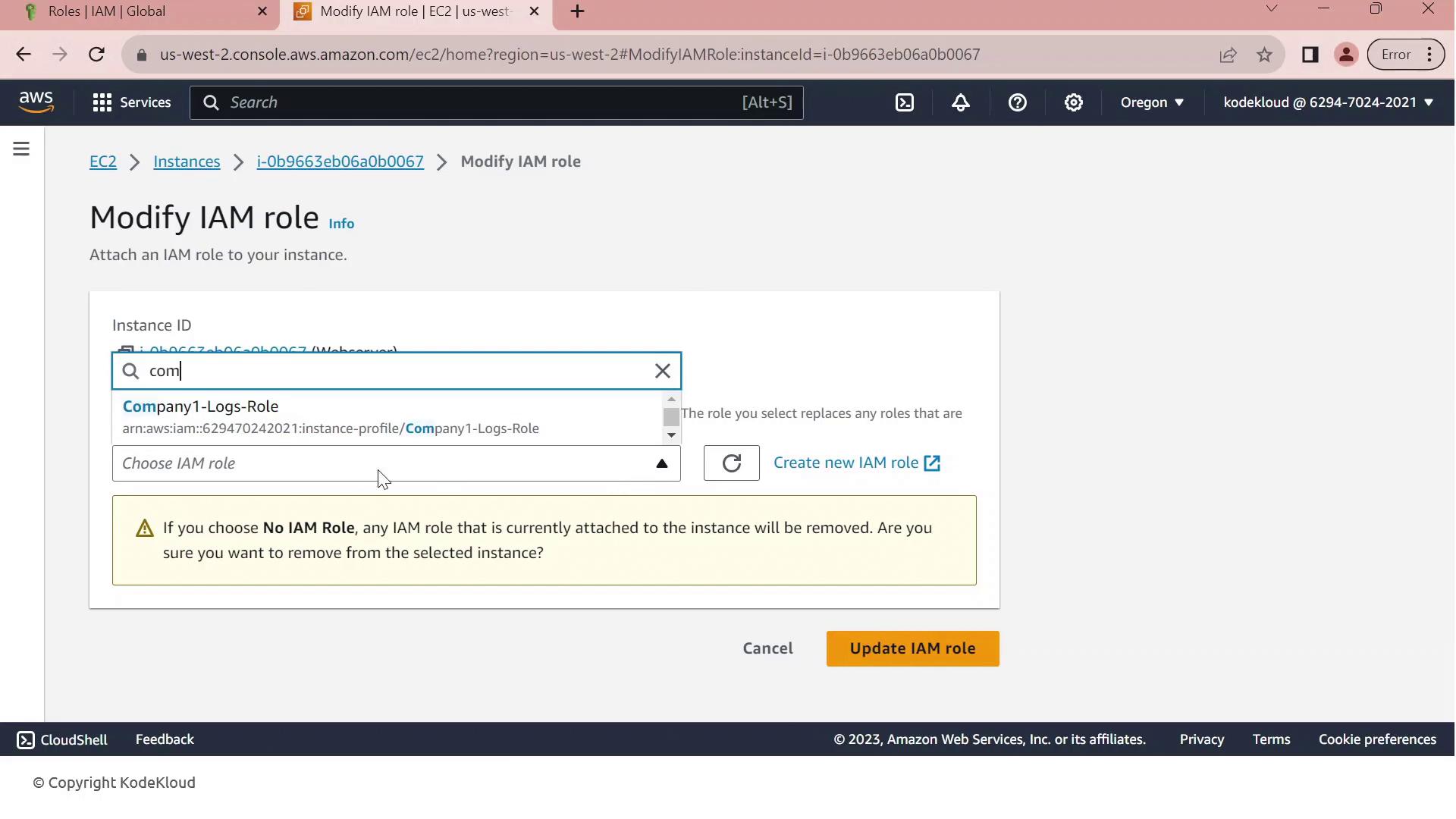
- Click Update IAM role to apply the change.
If your EC2 instance already has an IAM role attached, updating it will replace the existing role and associated permissions. Ensure this change aligns with your security policies.
Company1-Logs-Role, allowing it to securely read log files from the company1-logs bucket without embedded credentials.