AWS Lambda
Advanced Topics
Lambda Networking Demonstration Option 1
Configuring AWS Lambda networking in your own private VPC allows your function to securely access resources such as RDS databases, ElastiCache clusters, or internal APIs. In this guide, you’ll move a Lambda function out of the default AWS-managed VPC and into a custom VPC.
Steps to Enable VPC Access
Open or create your Lambda function
In the AWS Lambda console, choose your existing function or click Create function to define a new one.Enable VPC configuration
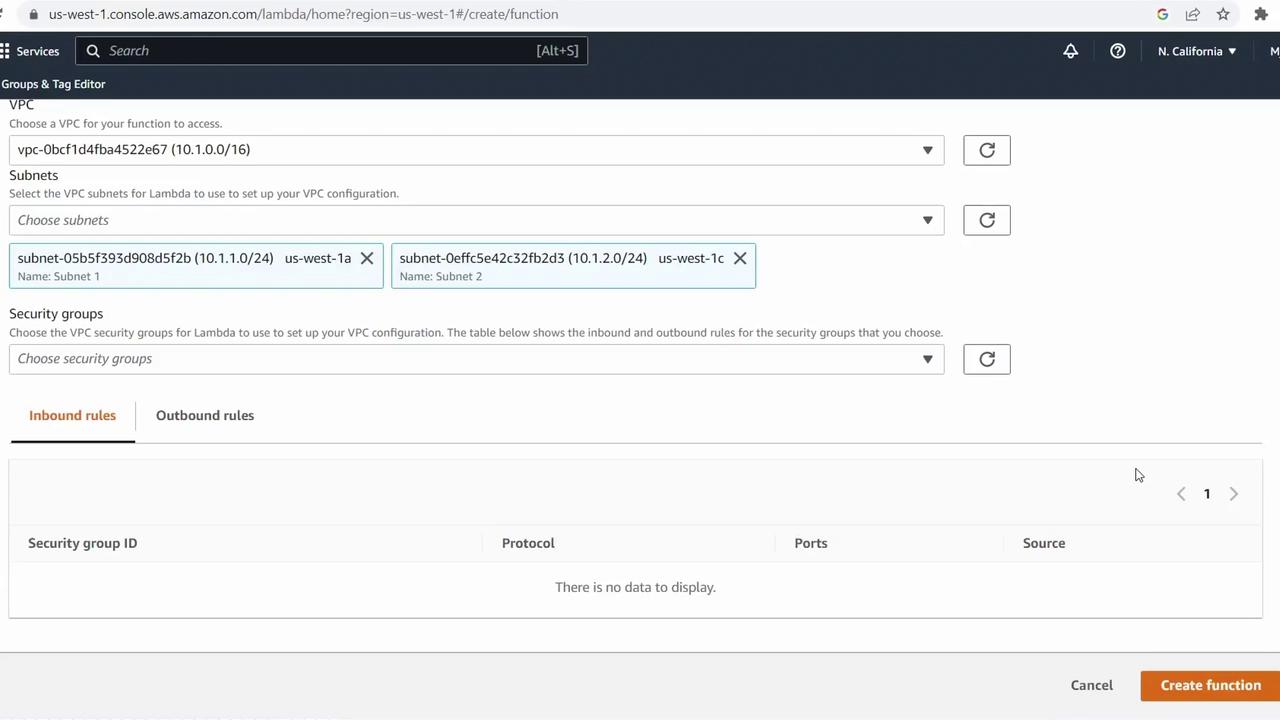
Scroll to Configuration, expand Advanced settings, and toggle Enable VPC on.Select your VPC
From the VPC dropdown, pick the VPC you’ve already provisioned (e.g.,cold-cloud-demo-vpc).Choose subnets for high availability
Expand Subnets and select at least two subnets in different Availability Zones. This ensures your function remains resilient during AZ outages.- One subnet in us-west-1a
- One subnet in us-west-1c
Note
Always select subnets from multiple Availability Zones to maintain high availability. If one AZ goes down, Lambda can still execute in the other.
Assign security groups
Under Security groups, pick existing security groups or create new ones to control inbound and outbound traffic for your function’s Elastic Network Interface (ENI).Warning
Attaching a Lambda function to a VPC can increase cold start times because ENIs must be initialized. Review AWS Lambda cold start considerations for mitigation strategies.
Once these steps are complete, your Lambda function will operate within your private VPC, able to access internal resources while being protected by your defined security groups.
Links and References
Watch Video
Watch video content