Why Load Balancers?
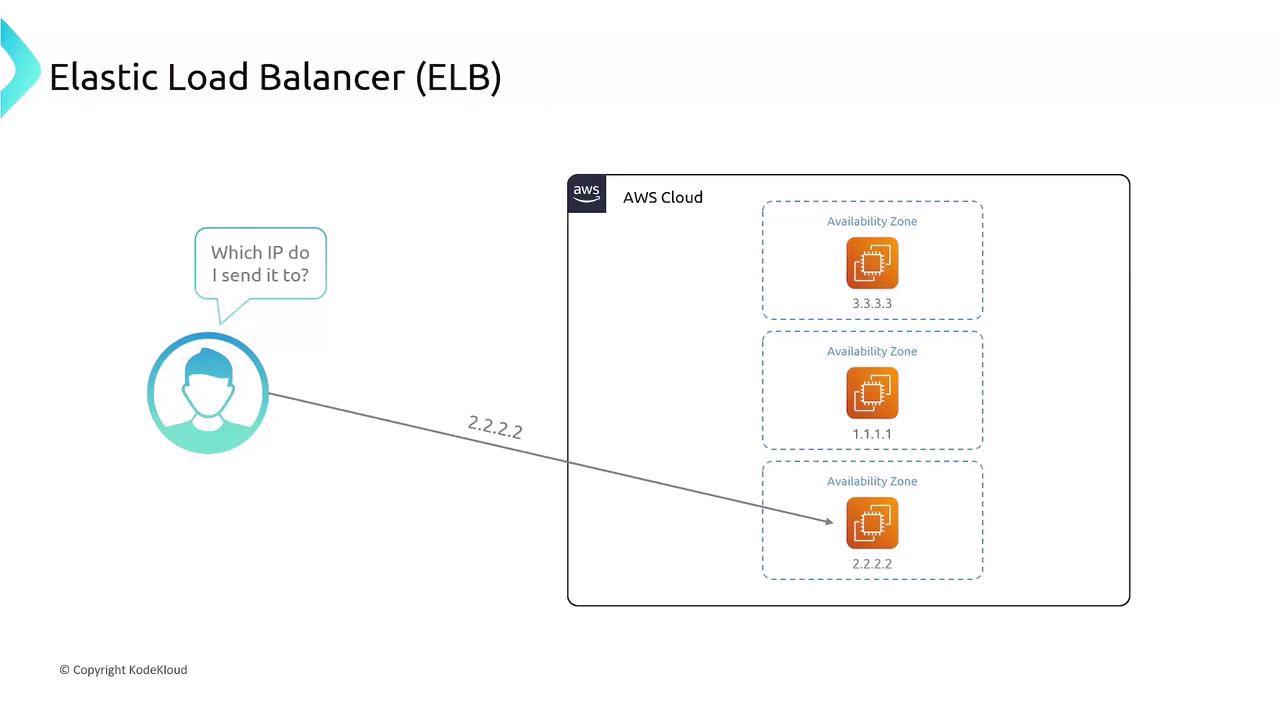
Imagine hosting your web application on a single EC2 instance at public IP1.1.1.1. If that instance fails, your site goes offline. To add redundancy, you deploy instances across multiple Availability Zones:
- EC2 A: 1.1.1.1
- EC2 B: 2.2.2.2
- EC2 C: 3.3.3.3
Types of AWS Load Balancers
AWS provides three managed load-balancing options to suit different workloads:| Load Balancer Type | OSI Layer | Protocols | SSL Termination | Use Case |
|---|---|---|---|---|
| Classic Load Balancer (CLB) | 4 & 7 | HTTP, HTTPS, TCP, SSL | Yes (one certificate) | Legacy workloads |
| Application Load Balancer (ALB) | 7 | HTTP, HTTPS, WebSockets | Yes (multiple) | URL/path-based routing |
| Network Load Balancer (NLB) | 4 | TCP, UDP | No | Ultra-low latency transport load |
1. Classic Load Balancer (CLB)
The original AWS load balancer supports HTTP, HTTPS, TCP, and SSL but lacks modern features like multiple certificates and advanced routing.Classic Load Balancer is considered legacy. AWS recommends using Application Load Balancer (ALB) or Network Load Balancer (NLB) for new deployments.
2. Application Load Balancer (ALB)
ALBs operate at the application layer (Layer 7) and excel at HTTP, HTTPS, and WebSocket traffic. They provide content-based routing and host/path-based rules:- URL path and host header conditions
- HTTP methods, headers, query strings, source IP
- HTTP redirects and custom responses
- Application-level health checks


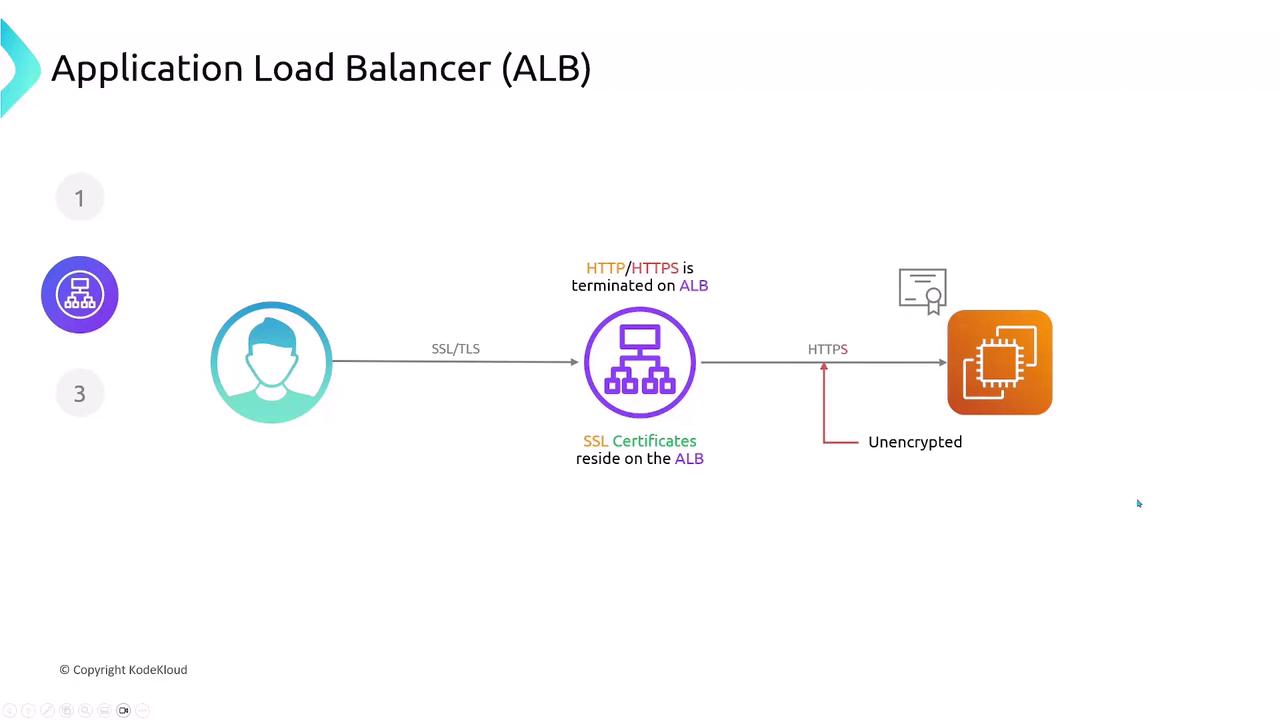
ALB Traffic Flow and SSL Termination
Application Load Balancers terminate SSL/TLS connections, decrypting traffic at the edge. Your SSL certificates reside on the ALB, and you can choose to forward decrypted traffic to backends over HTTP or re-encrypt using HTTPS.Ensure your backend instances are configured to handle re-encrypted HTTPS if you require end-to-end encryption.
3. Network Load Balancer (NLB)
Operating at the transport layer (Layer 4), NLBs handle millions of requests per second with ultra-low latency. They forward TCP/UDP connections directly to targets without TLS termination.- High throughput and low latency
- Static IP support and Elastic IP attachment
- Basic transport-level health checks (TCP)
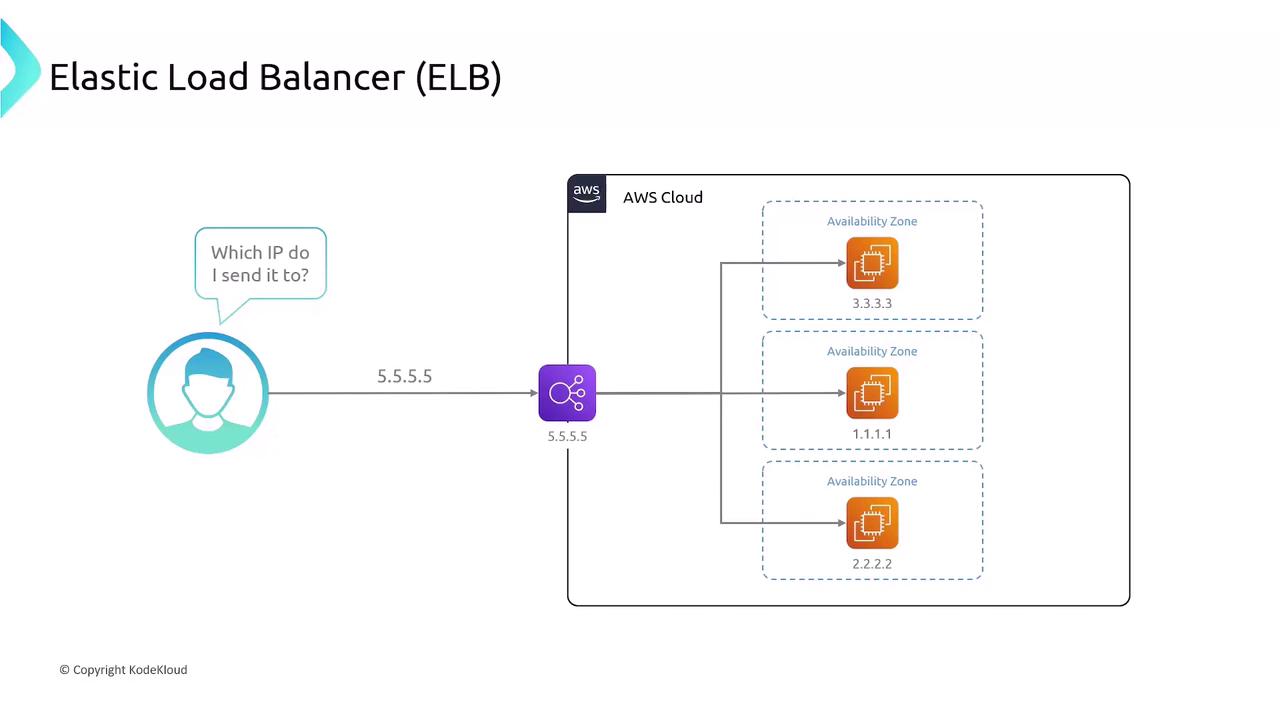
ELB Architecture in a VPC
When you create an ELB, AWS launches a load-balancer node in each selected subnet (one per AZ). Clients resolve the ELB’s DNS name, and AWS distributes traffic across all nodes, which in turn forward requests to registered targets.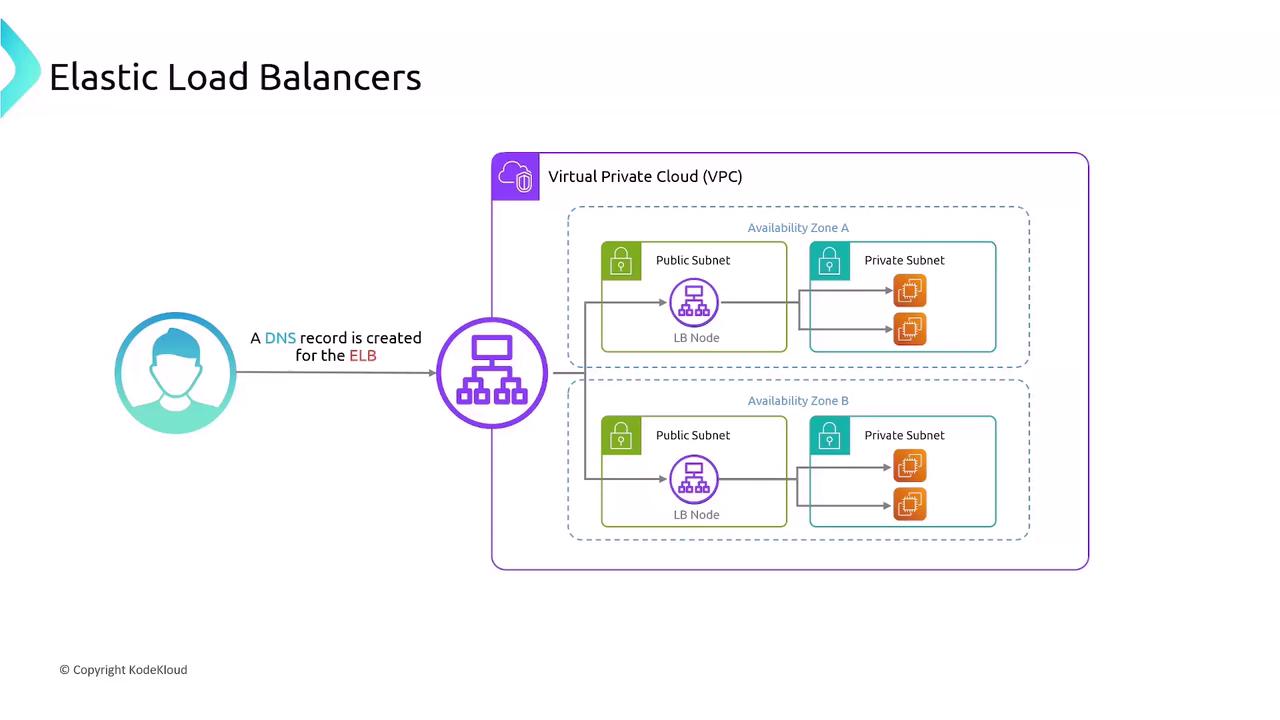
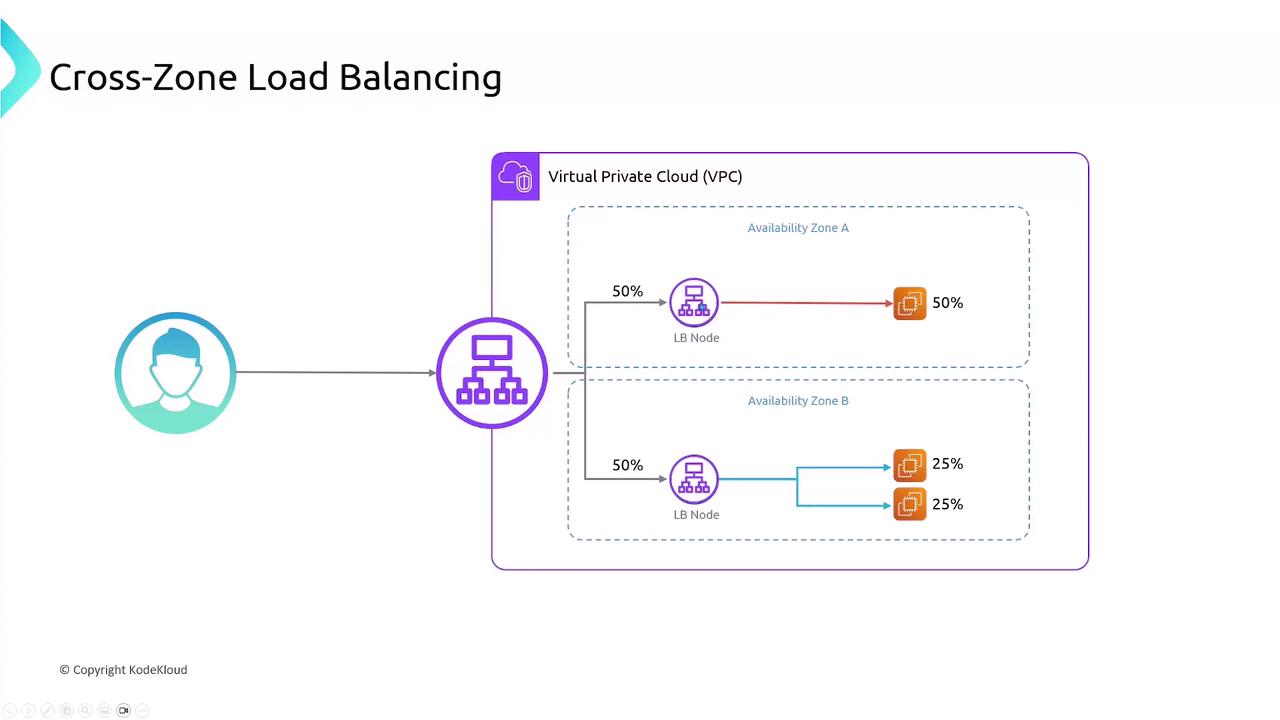
Cross-Zone Load Balancing
By default, each ELB node only routes traffic to targets in its own Availability Zone, which can cause uneven distribution if instance counts differ. Enabling cross-zone load balancing ensures each node spreads requests across all zones evenly.Cross-zone load balancing can improve utilization but may incur additional inter-AZ data transfer charges.
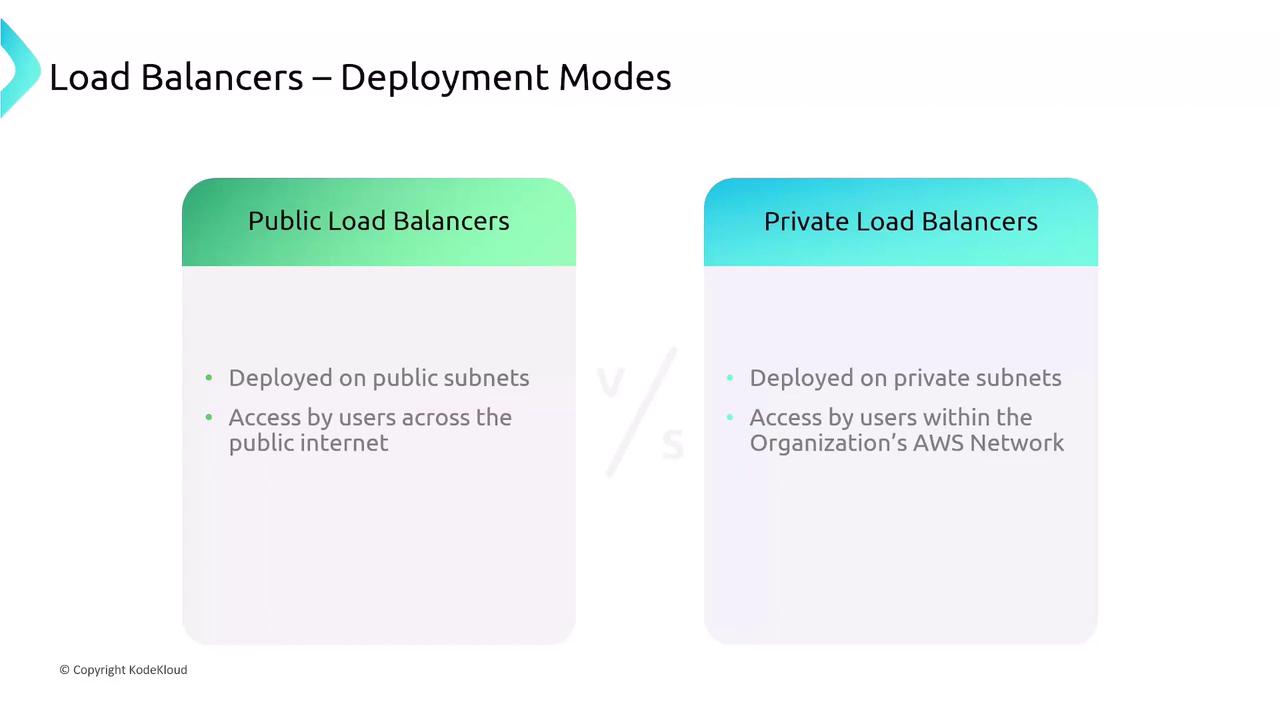
Public vs. Private Load Balancers
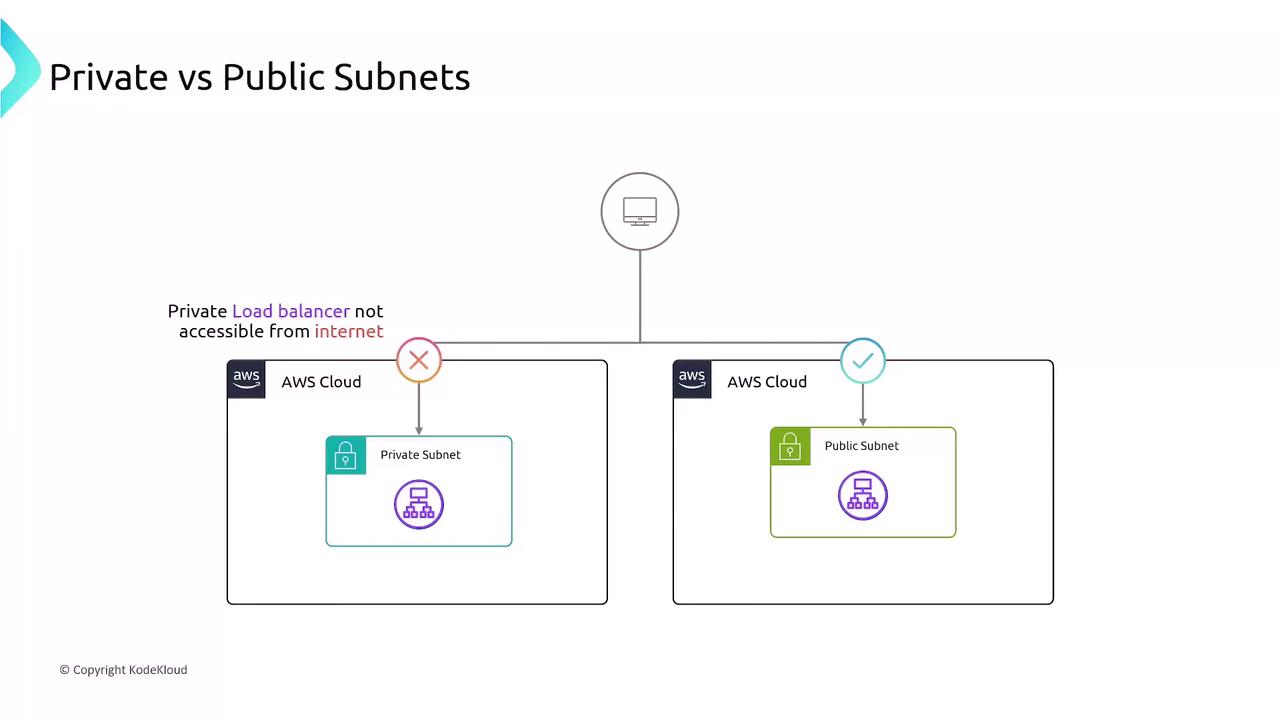
When deploying an ELB, you specify subnets:- Public Load Balancer: Internet-facing on public subnets
- Private Load Balancer: Internal-only on private subnets
Example: Multi-Tier Application
Consider a two-tier application in a VPC across two Availability Zones:-
API Layer
- EC2 instances hosting your public API
- Internet-facing public ALB distributes incoming user traffic
-
Database Layer
- EC2 instances running database or business logic
- Internal private ALB restricts access to only the API servers

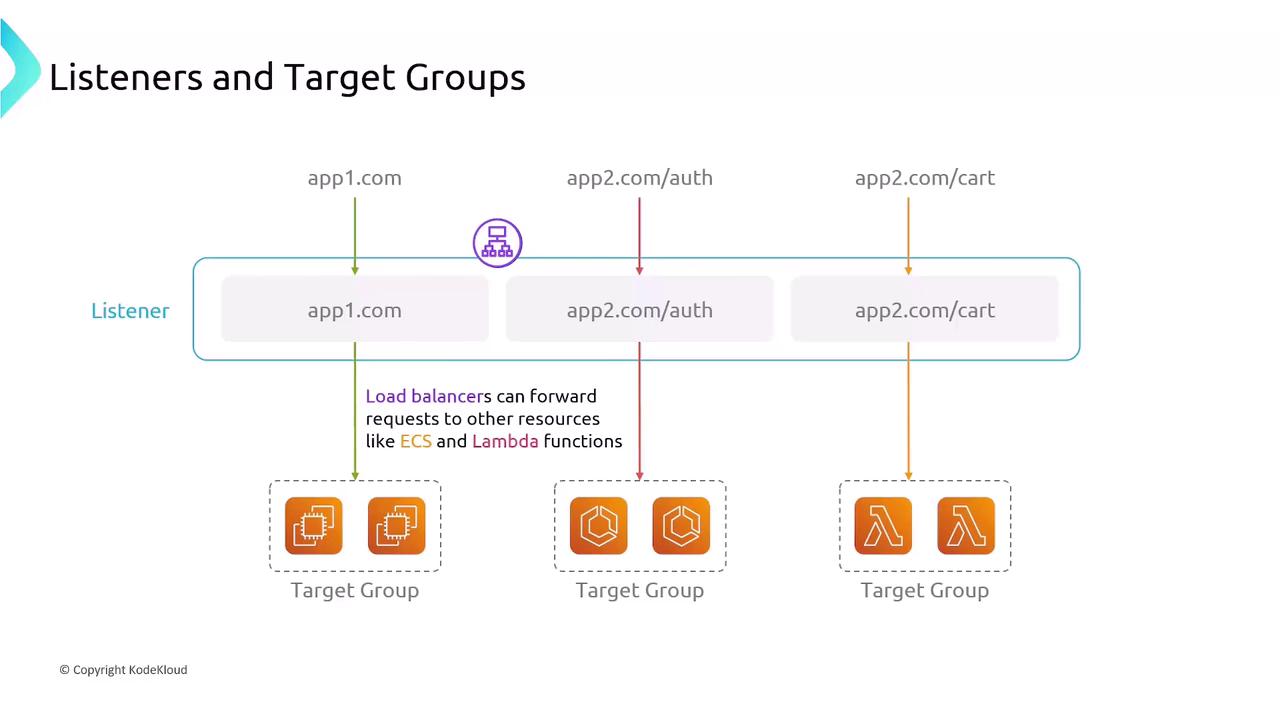
Listeners and Target Groups
Listeners and target groups define how ELBs receive and route traffic:- Listeners: Check for incoming connections on a specific protocol and port. ALB listeners support content-based rules (host, path, headers).
- Target Groups: Logical groups of endpoints (EC2 instances, IPs, ECS tasks, Lambda functions). Each listener rule forwards traffic to one or more target groups, with configurable health checks.
Summary
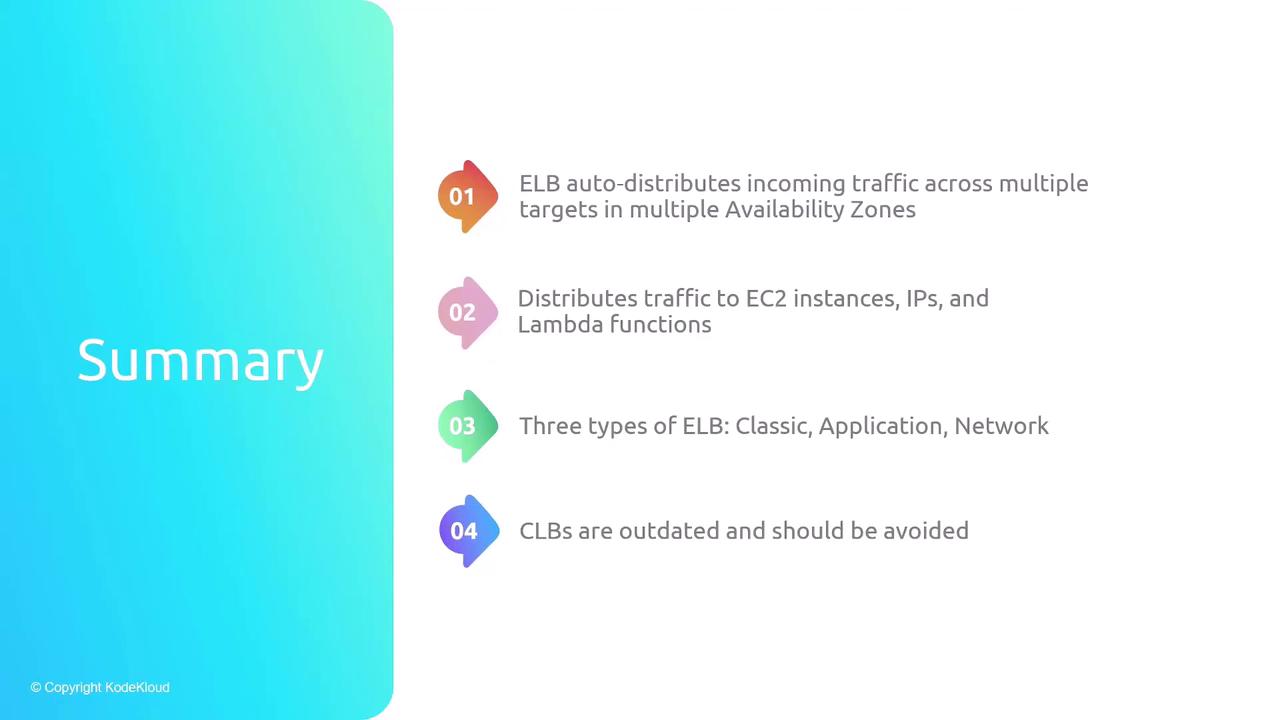
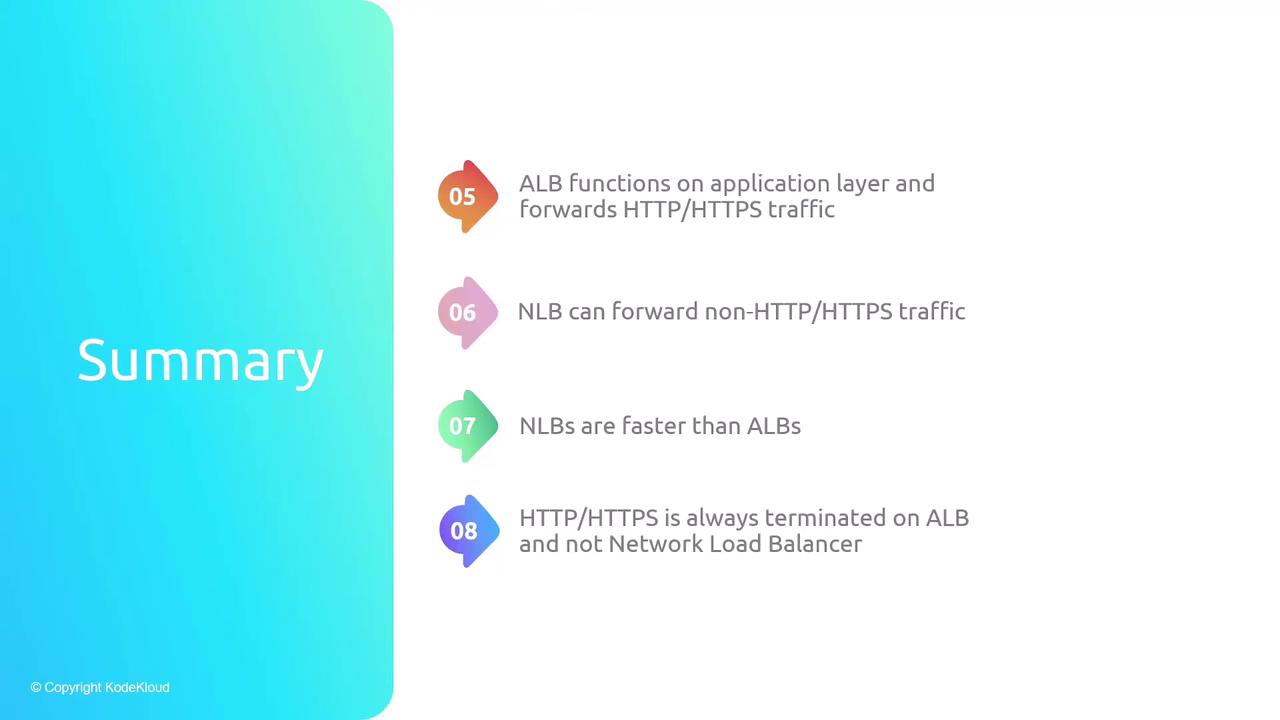
- ELBs distribute traffic across multiple targets and AZs automatically.
- Supports EC2 instances, IP addresses, containers (ECS), and Lambda functions.
- Classic (CLB): Legacy; limited features, one SSL cert.
- Application (ALB): Layer 7 routing with advanced rules and TLS termination.
- Network (NLB): Layer 4 transport load balancing with ultra-low latency.
- Cross-zone load balancing for even traffic distribution across AZs.
- Listeners parse connections; target groups manage backend health and routing.