AWS Networking Fundamentals
Core Networking Services
Security Groups NACLs
In this lesson, we’ll cover how firewalls work, then explore AWS implementations: Network ACLs (NACLs) and Security Groups. You’ll learn the differences between stateless and stateful filtering, how to configure rules, and best practices for securing your VPC.
Firewalls: Inbound and Outbound Traffic
A firewall monitors traffic flows and only allows connections matching predefined rules. Each rule controls:
- Inbound: Connections to your resource
- Outbound: Connections from your resource
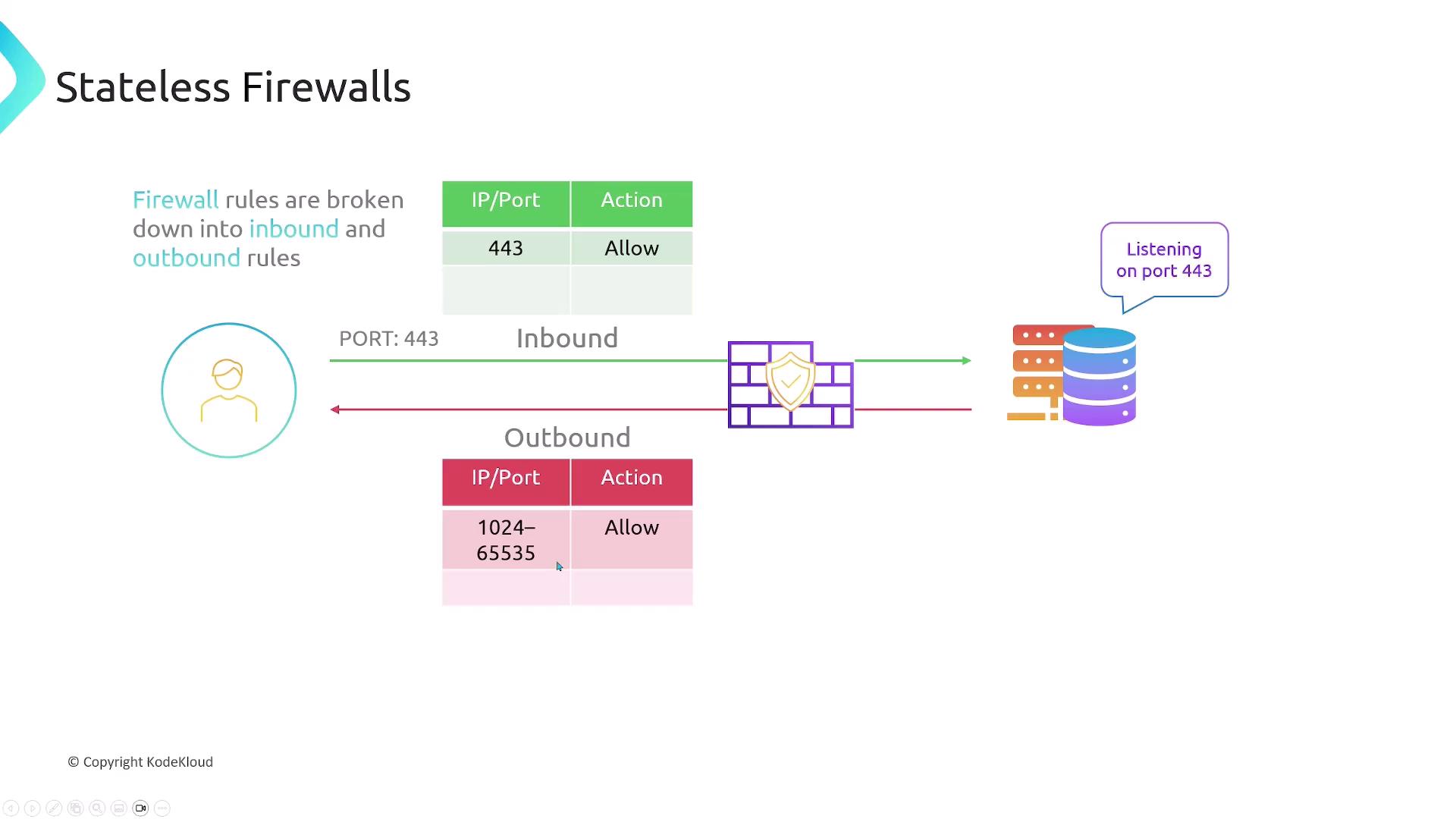
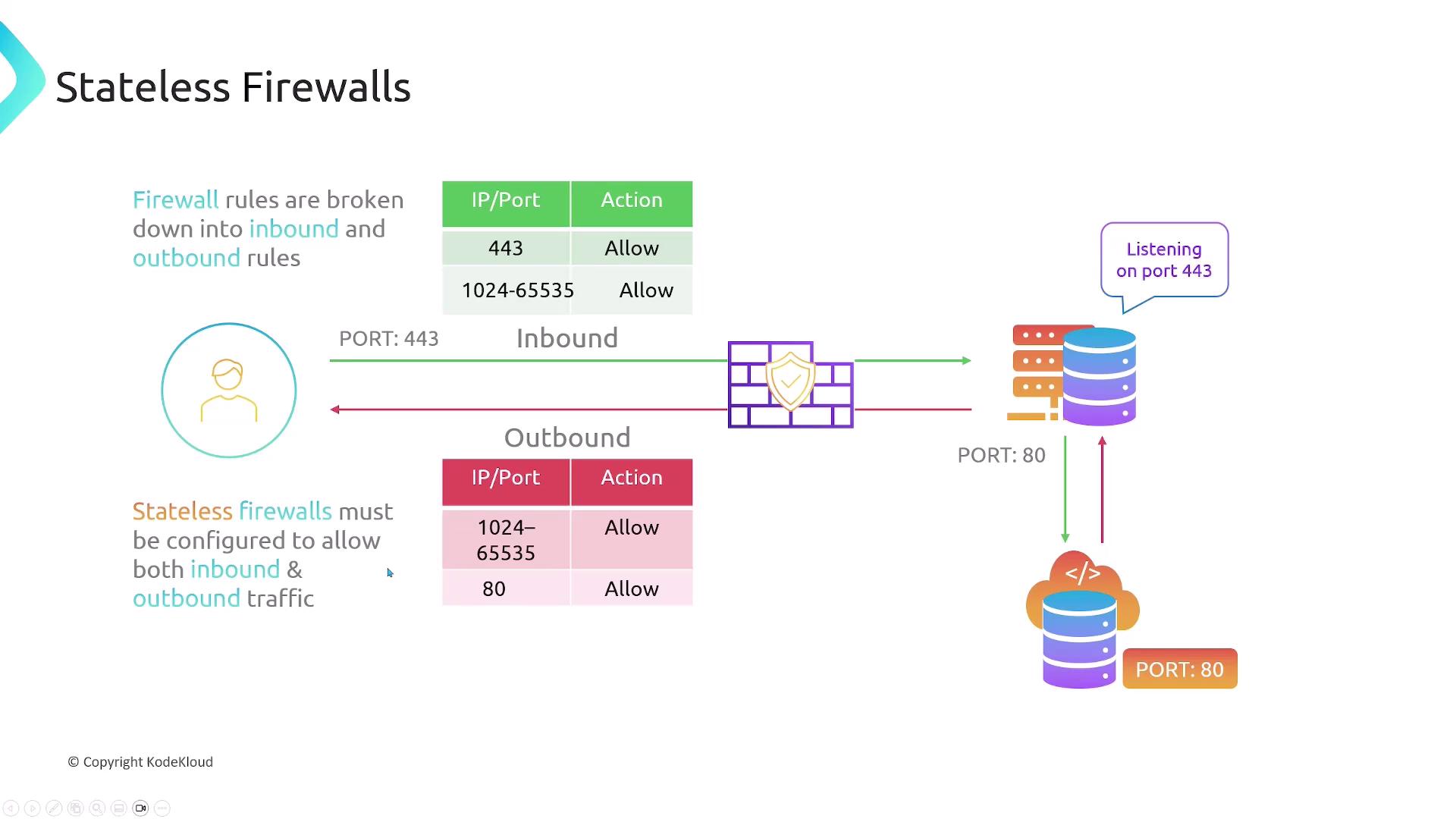
Stateless Firewalls
Stateless firewalls treat inbound and outbound traffic independently. You must explicitly allow both directions for every connection.
For example, a web server listening on HTTPS (port 443) needs:
- Ingress: Allow TCP 443
- Egress: Allow TCP 1024–65535 (ephemeral ports)
If the server also fetches updates over HTTP (port 80):
- Egress: Allow TCP 80
- Ingress: Allow TCP 1024–65535
Warning
Stateless firewalls do not track connection state. If you forget to permit the reply path, your traffic will be dropped.
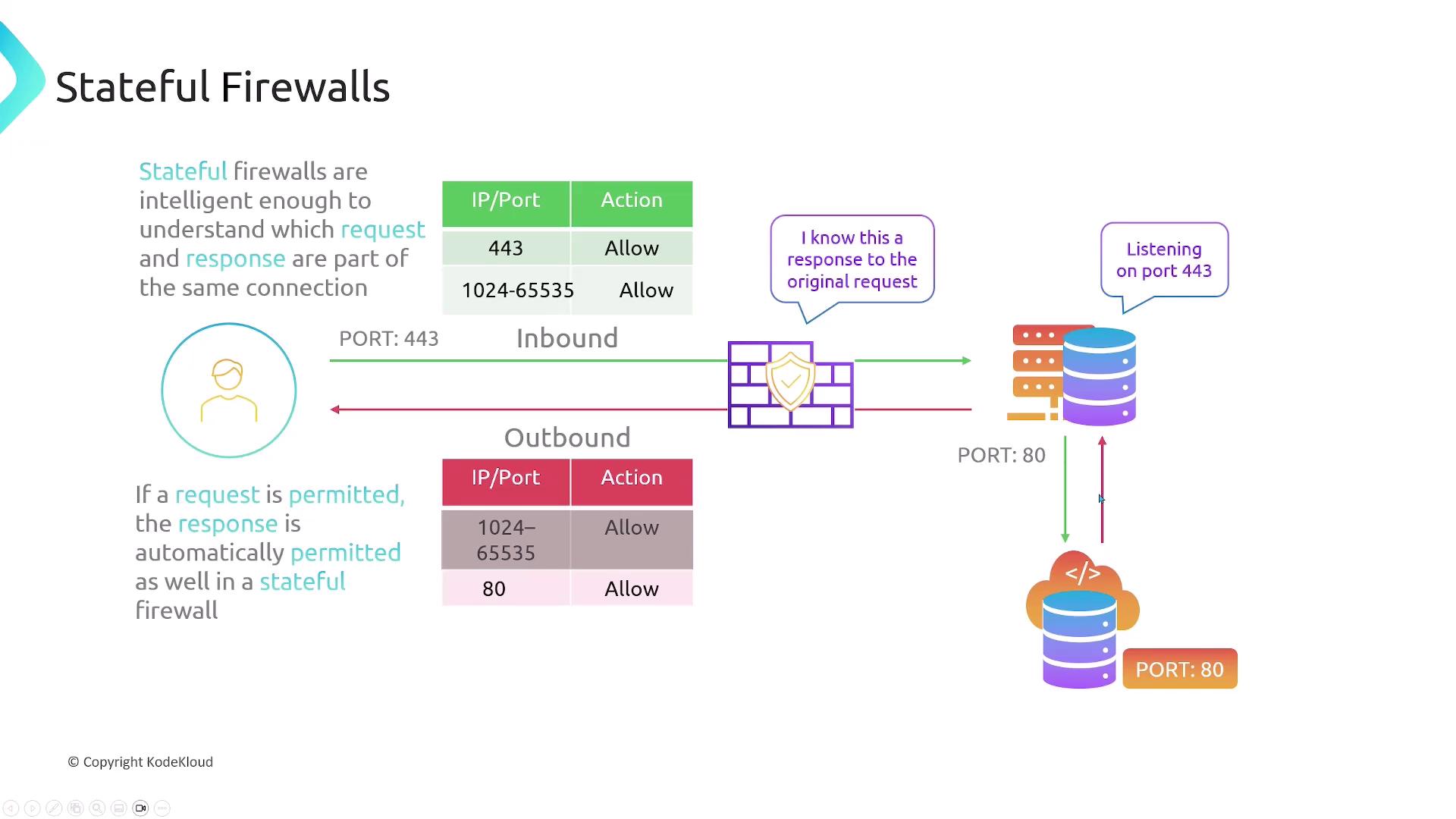
Stateful Firewalls
Stateful firewalls track connection state. Once you allow an incoming request, the outbound response is automatically permitted (and vice versa).
Using the same web server example:
- Ingress: Allow TCP 443
- Egress: No rule needed for ephemeral ports
- Egress: Allow TCP 80
- Ingress: No rule needed for ephemeral ports
Note
Stateful filtering simplifies rules management by automatically permitting return traffic.
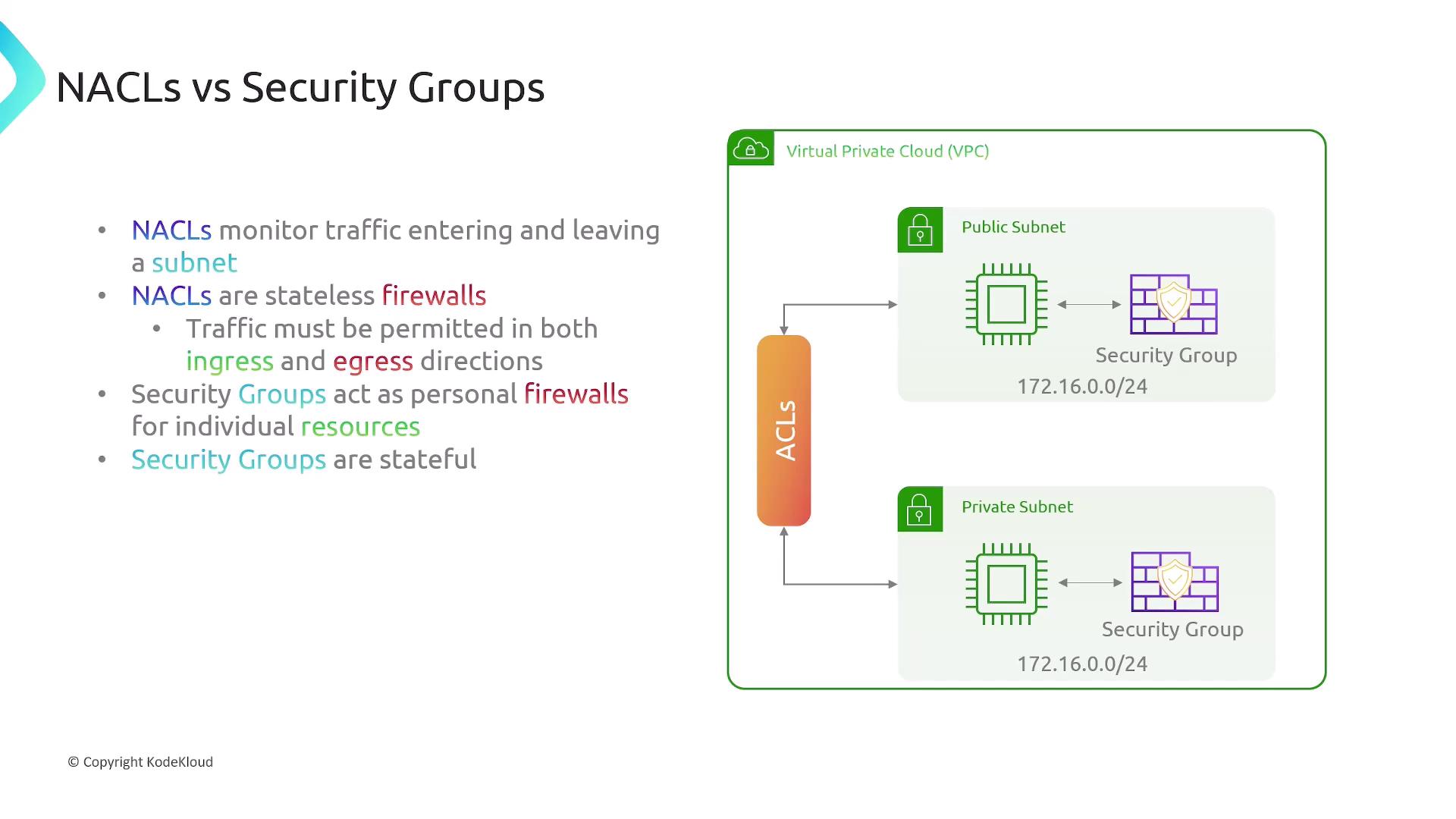
AWS Network ACLs (NACLs)
A Network ACL filters traffic entering and leaving subnets. Key points:
- Every subnet must be associated with exactly one NACL.
- A NACL can apply to multiple subnets.
- NACLs are stateless: separate ingress/egress rules.
- They do not filter intra-subnet traffic.

Comparing NACLs vs. Security Groups
| Feature | Network ACL (Stateless) | Security Group (Stateful) |
|---|---|---|
| Scope | Subnet-level | Instance/ENI-level |
| Direction | Ingress & Egress rules (explicit) | Ingress rules only (egress auto for responses) |
| Default Behavior | Default rule: Deny all | Default egress: Allow all; ingress: Deny all |
| Rule Actions | Allow or Deny | Allow only (implicit deny) |
| Rule Evaluation Order | By rule number (lowest first) | All rules are evaluated; no priority |
| Stateful Tracking | No | Yes |
AWS Security Groups
Security Groups act as stateful firewalls for individual resources (EC2, RDS, ENIs, etc.):
- Only the initiating direction is needed; return traffic is auto-allowed.
- Rules apply per resource, not per subnet.
Configuring Security Group Rules
In the AWS Console, you define Inbound and Outbound rules separately. The fields are identical but apply in opposite directions.
Inbound rules
┌─────────┬─────────┬───────────┬──────────────┬────────────┐
│ Type │ Protocol│ Port Range│ Source │ Description│
├─────────┼─────────┼───────────┼──────────────┼────────────┤
│ HTTP │ TCP │ 80 │ 0.0.0.0/0 │ (optional) │
└─────────┴─────────┴───────────┴──────────────┴────────────┘
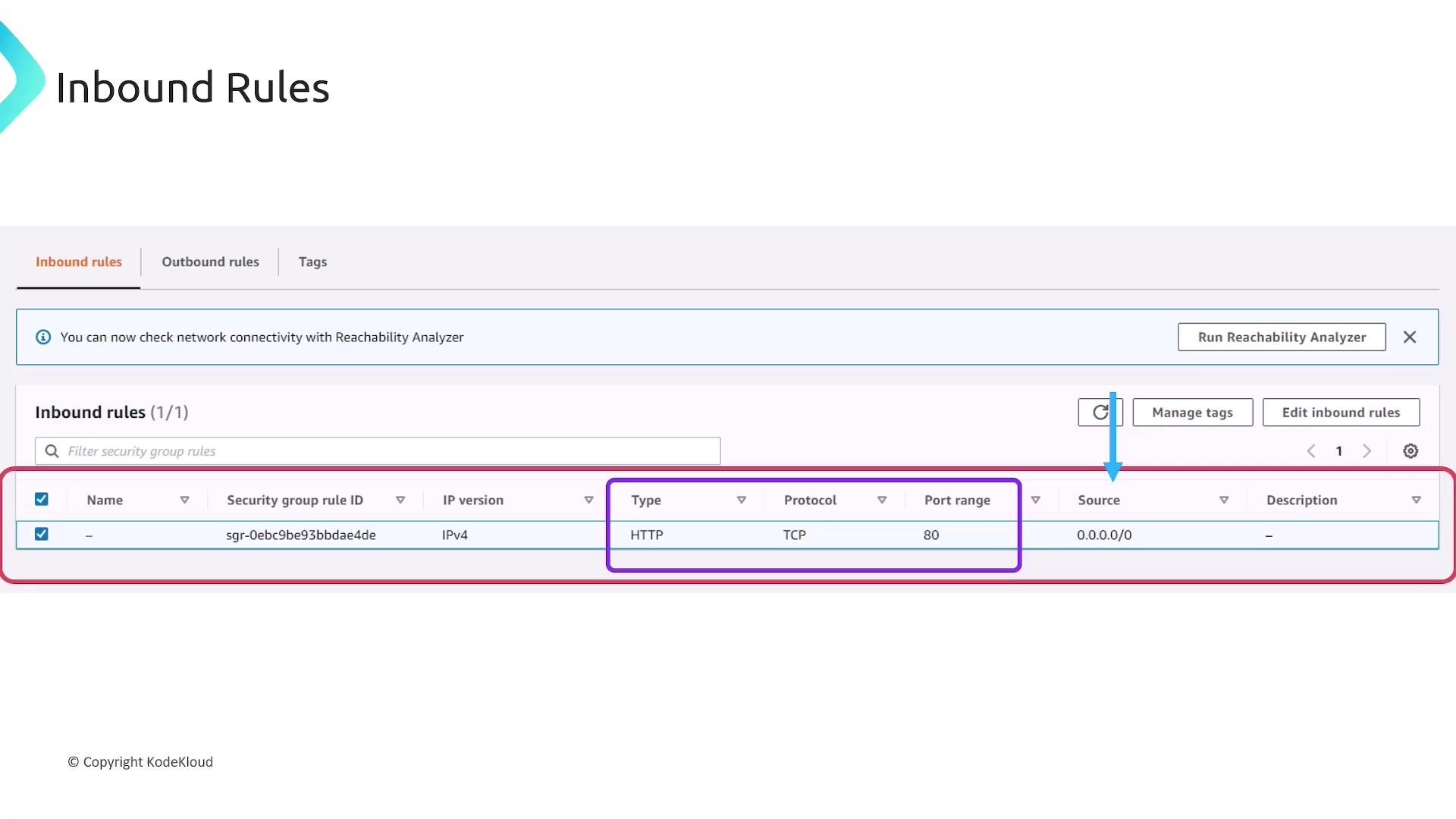
Fields you’ll configure:
- Type: Predefined (HTTP, SSH) or Custom
- Protocol: TCP, UDP, ICMP, or All
- Port Range: Single port or port range
- Source/Destination: CIDR block or security group ID
- Description: Free-form text
Outbound rules follow the same format:

Note
If no outbound rules exist, all traffic is blocked by default. Security Groups can only allow traffic; there’s no explicit deny.
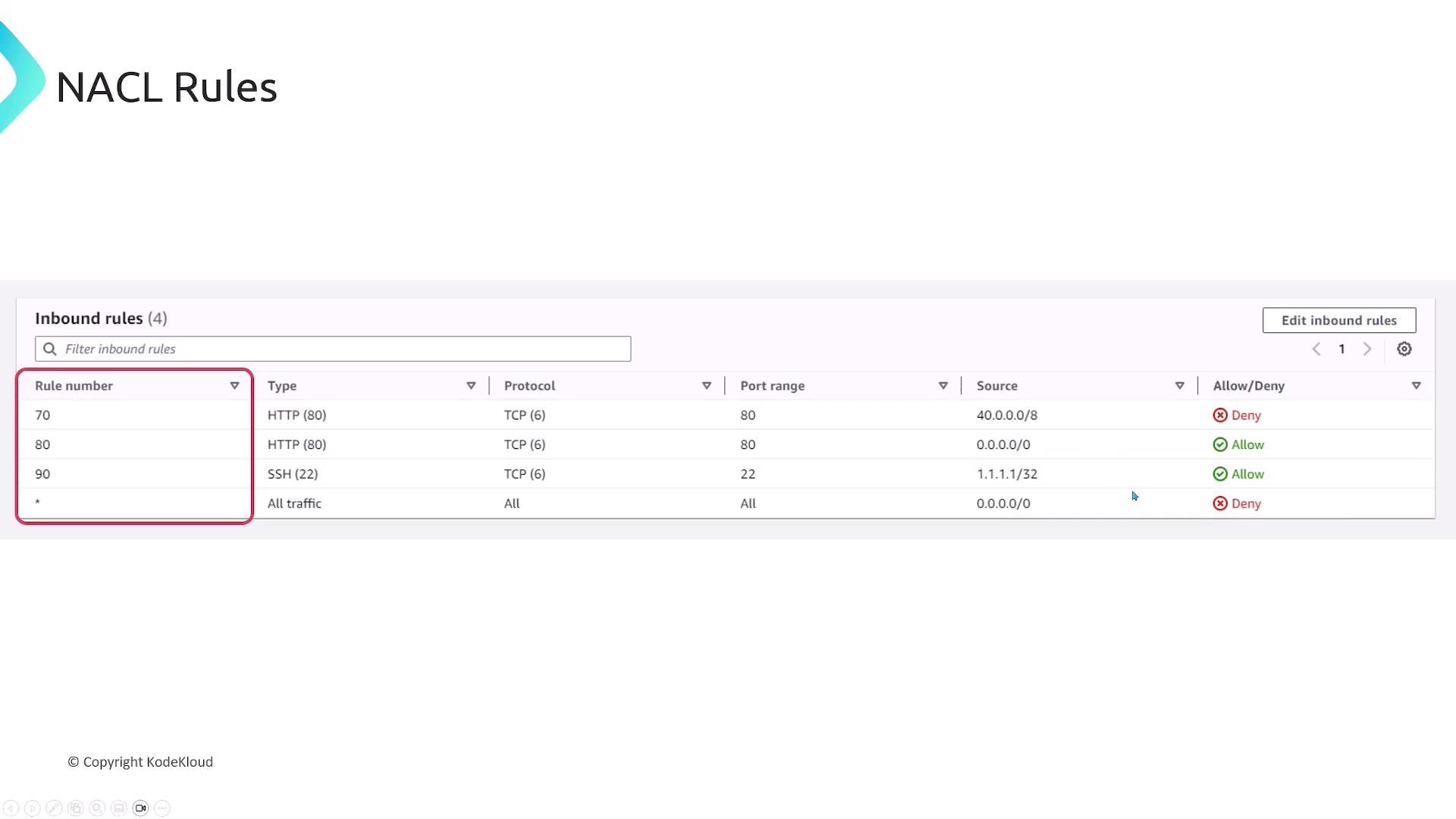
NACL Rules Example
Every NACL rule includes a rule number (priority), type, protocol, port range, CIDR, and an Allow/Deny action. Rules are processed in ascending order.
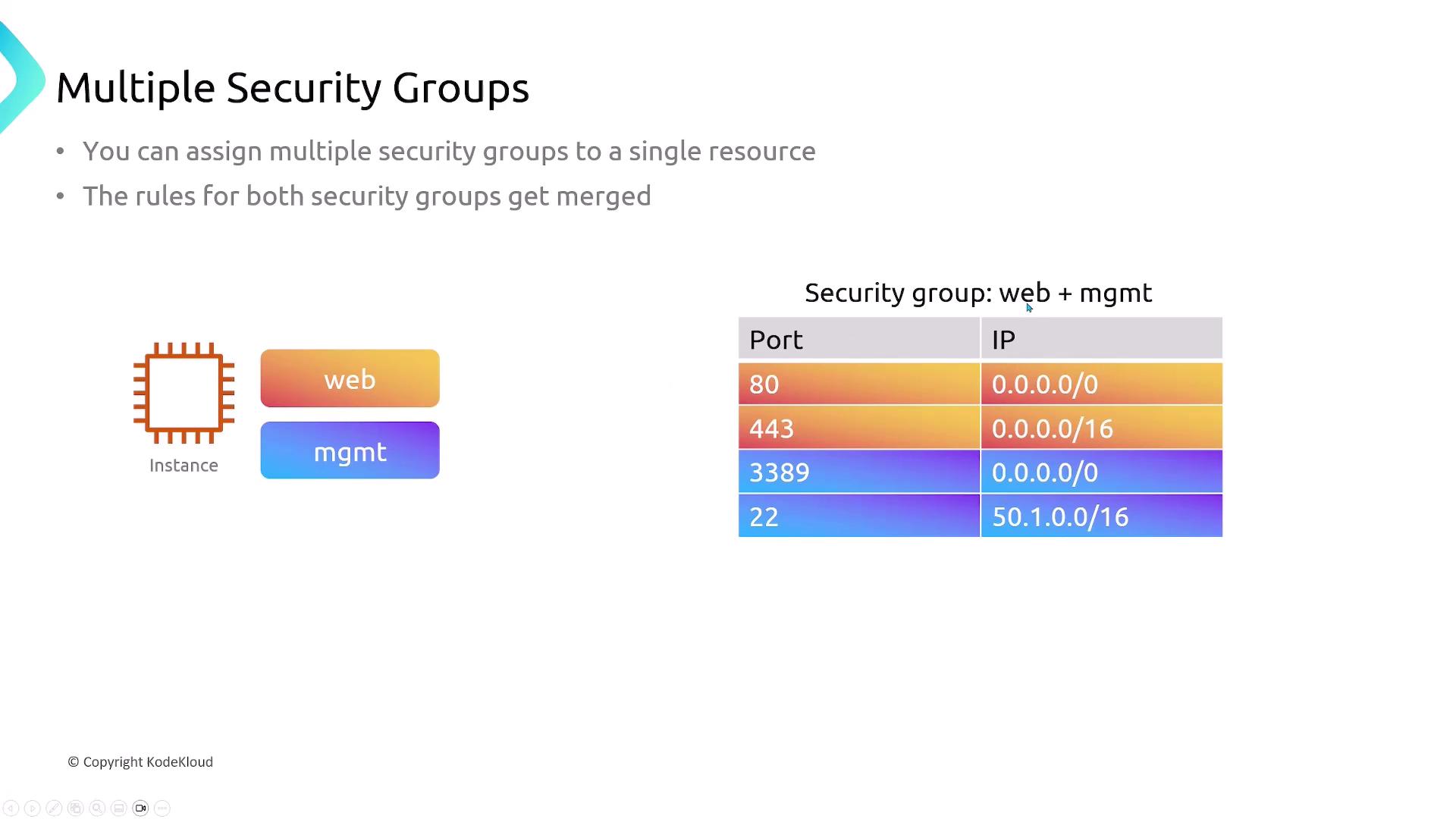
Multiple Security Groups per Resource
You can attach multiple Security Groups to a single resource. AWS merges all allow rules into one effective policy.
Default Behaviors and Associations
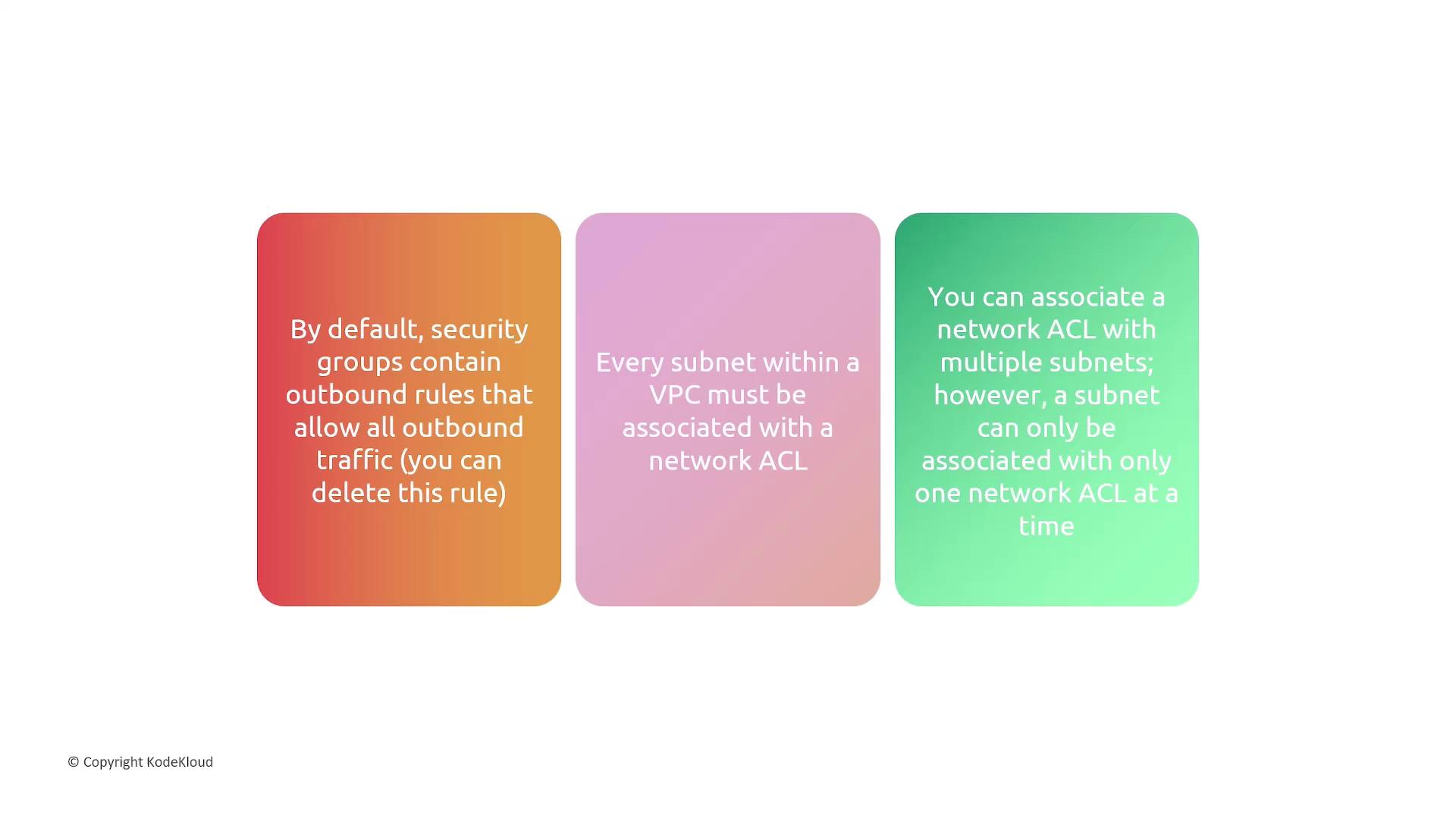
- Security Groups: Default egress allows all traffic.
- NACLs: Each subnet needs one NACL; one-to-many relationship.
- Associations: Subnet ↔ one NACL; NACL ↔ many subnets.
Traffic Exempt from NACL Filtering
Certain AWS control-plane and metadata endpoints bypass NACLs:

- Amazon DNS
- DHCP
- EC2 Instance Metadata
- ECS Task Metadata
- Windows License Activation
- Amazon Time Sync Service
- Reserved VPC Router IPs
Summary
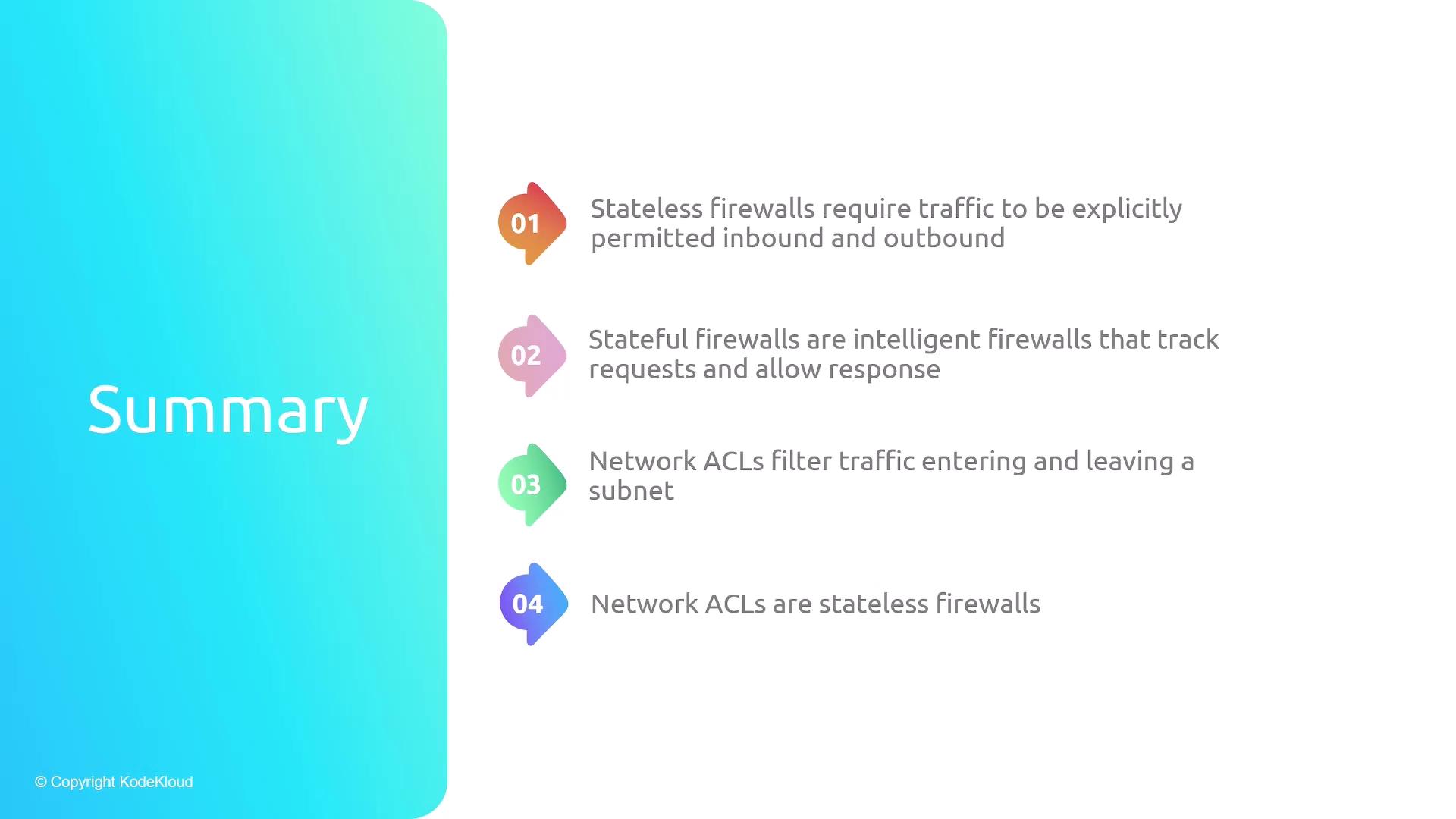
- Stateless Firewalls: Require explicit ingress and egress rules.
- Stateful Firewalls: Automatically permit response traffic.
- NACLs: Stateless, subnet-level, Allow/Deny capabilities.
- Security Groups: Stateful, resource-level, Allow-only rules.
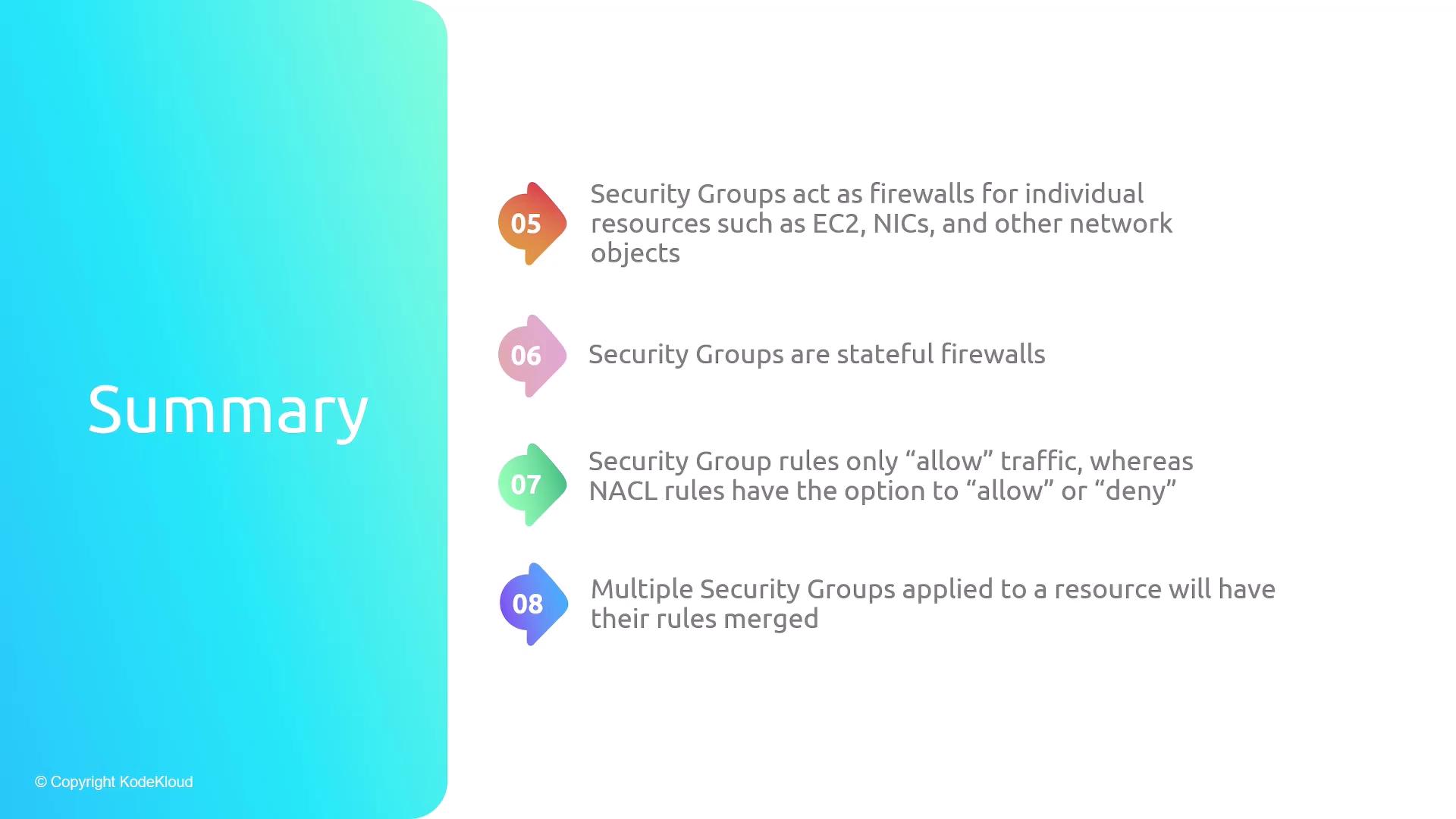
- Applied per ENI/instance; rules are merged across groups.
- Outbound is wide-open by default.

- Each subnet requires exactly one NACL.
- Rules evaluated in numeric order, ending with a catch-all rule.
Links and References
Watch Video
Watch video content