What Is an AWS Subnet?
- A subnet’s CIDR block must be a subset of its VPC’s CIDR block.
- AWS supports subnet sizes from
/16(65,536 IPs) down to/28(16 IPs). - You distribute subnets across multiple AZs to increase resilience.
- Subnet A:
192.168.10.0/24inus-east-1a - Subnet B:
192.168.20.0/24inus-east-1b
Public vs. Private Subnets
| Subnet Type | Route Target | Typical Use Cases |
|---|---|---|
| Public | Internet Gateway | Web servers, load balancers |
| Private | NAT Gateway | Databases, application servers |
- Public subnets have a route to an Internet Gateway (IGW) for direct internet access.
- Private subnets use a NAT Gateway (or NAT instance) for outbound internet connectivity without exposing resources to inbound traffic.
Configure route tables to associate subnets with the IGW or NAT Gateway as needed.
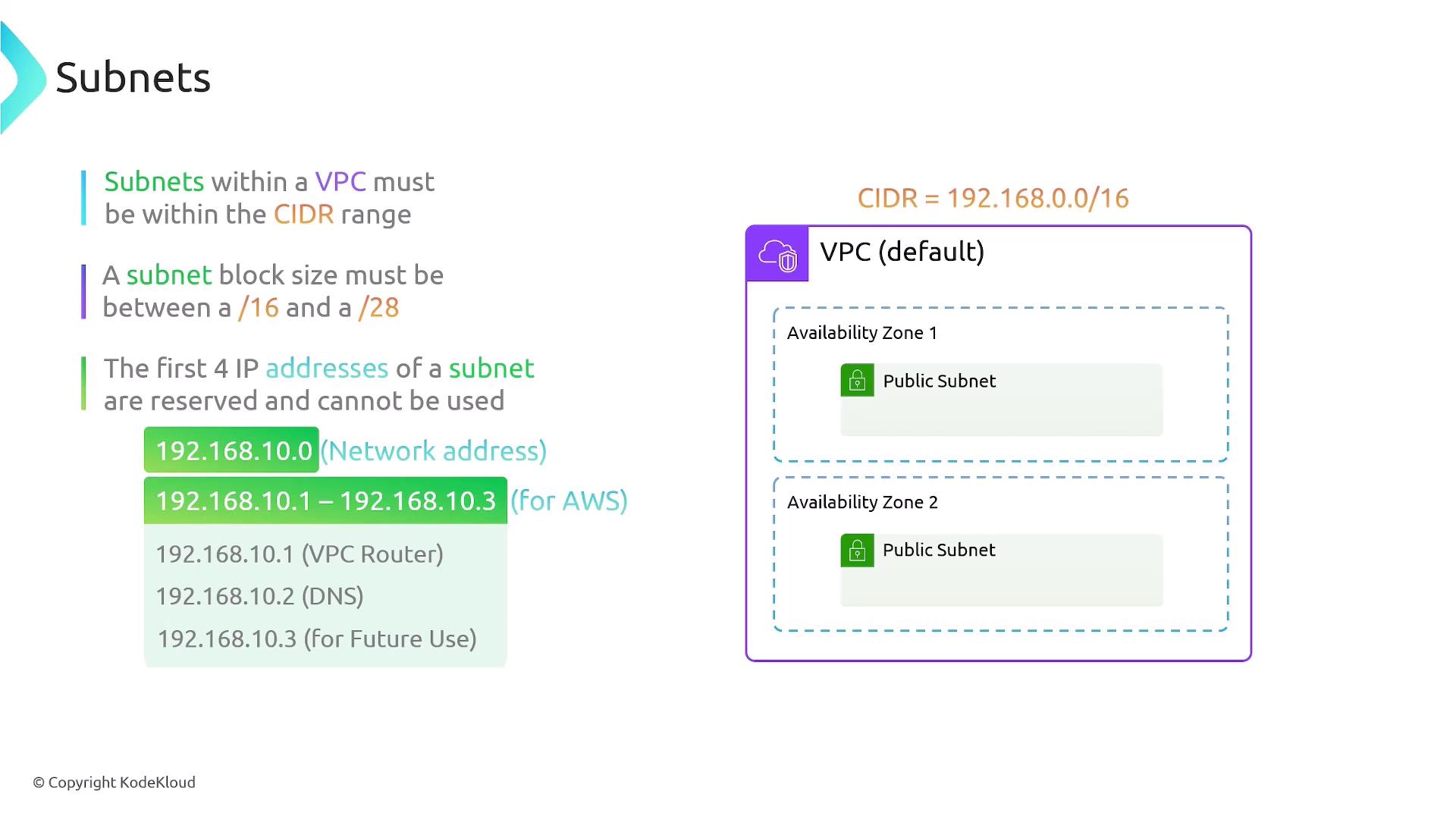
Subnet Requirements
-
CIDR containment
Your subnet’s CIDR must lie within the VPC’s CIDR block.- Valid: VPC
192.168.0.0/16, Subnet192.168.10.0/24 - Invalid: VPC
192.168.0.0/16, Subnet10.100.1.0/24
- Valid: VPC
-
Reserved IP addresses
AWS reserves five IPs in each subnet:Address Offset Purpose .0Network address .1VPC router .2DNS .3AWS future use /.lastBroadcast address -
Size constraints
- Minimum:
/28(16 IPs) - Maximum:
/16(65,536 IPs)
- Minimum:
Configuration Considerations
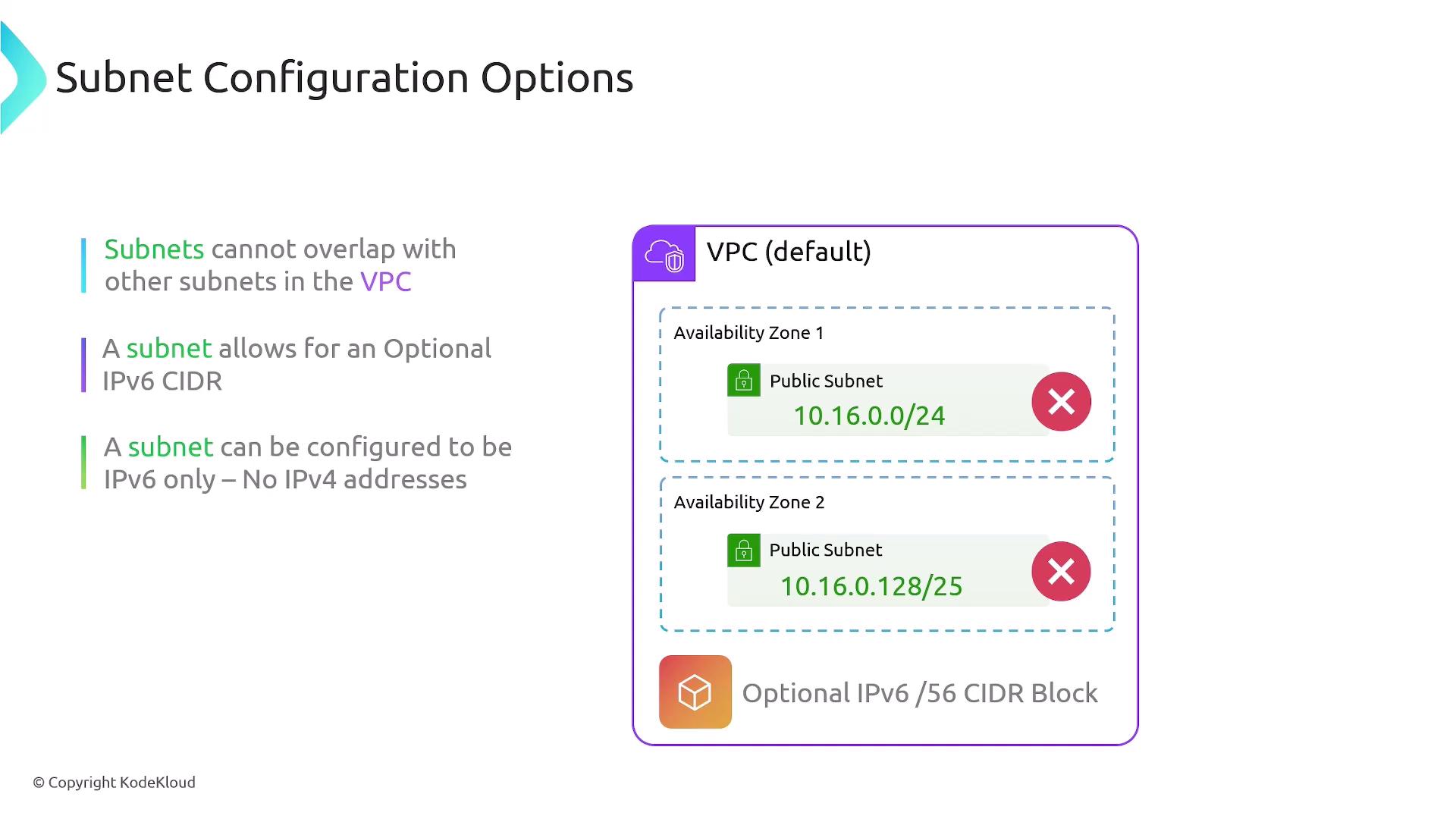
- No overlapping CIDRs within the same VPC. Overlapping is only permitted across distinct VPCs.
Defining overlapping CIDR blocks in the same VPC causes route conflicts and deployment failures.
-
IPv6 support: You can associate a
/56IPv6 CIDR block with your VPC. Subnets may be configured as:- IPv4 only
- IPv6 only
- Dual-stack (IPv4 + IPv6)
- Default communication: All subnets in a VPC can communicate without extra route entries.
- Auto-assign public IP: Enabling this on a subnet ensures every instance launched receives a public IPv4/IPv6 address in addition to its private IP.
Summary
- Subnets are AZ-scoped IP ranges within a VPC.
- Choose public or private routing by using an Internet Gateway or NAT Gateway.
- Support for IPv4, IPv6, or dual-stack.
- CIDR blocks must be non-overlapping and nested within the VPC’s CIDR.