Amazon Simple Storage Service (Amazon S3)
AWS S3 Advanced Features
S3 Encryption
In this lesson we’ll explore how Amazon S3 encrypts your data. We’ll cover:
- What is Encryption in S3?
- Client-Side vs. Server-Side Encryption
- Server-Side Encryption Methods (SSE-S3, SSE-KMS, SSE-C)
- Per-Object Encryption and Bucket Defaults
- Practical Code Examples for Each SSE Method
What Is Encryption?
Encryption transforms readable data (plaintext) into unreadable ciphertext using cryptographic keys. Only holders of the correct key can decrypt the data. In Amazon S3, encryption happens at two layers:
- In transit: Secured by SSL/TLS between your client and S3.
- At rest: Data stored on AWS servers is encrypted on disk.
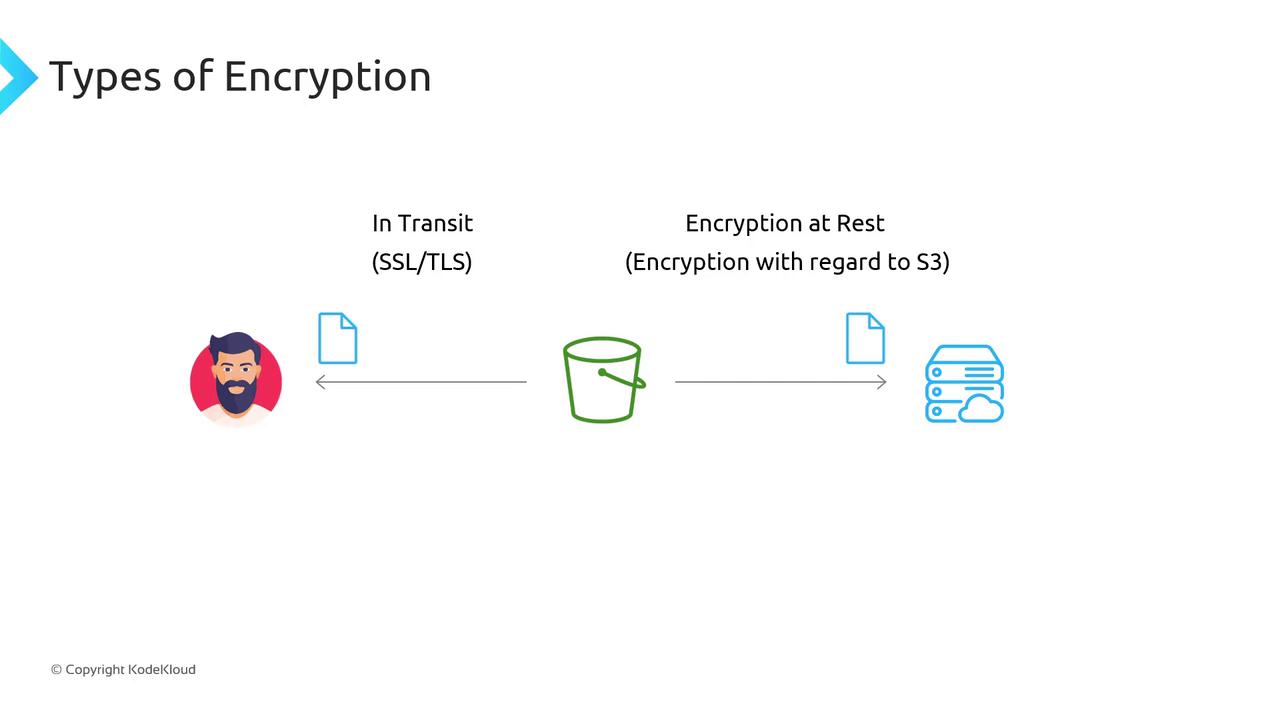
- In transit: Automatic over HTTPS (SSL/TLS).
- At rest: Must be enabled so S3 stores your objects encrypted on disk.
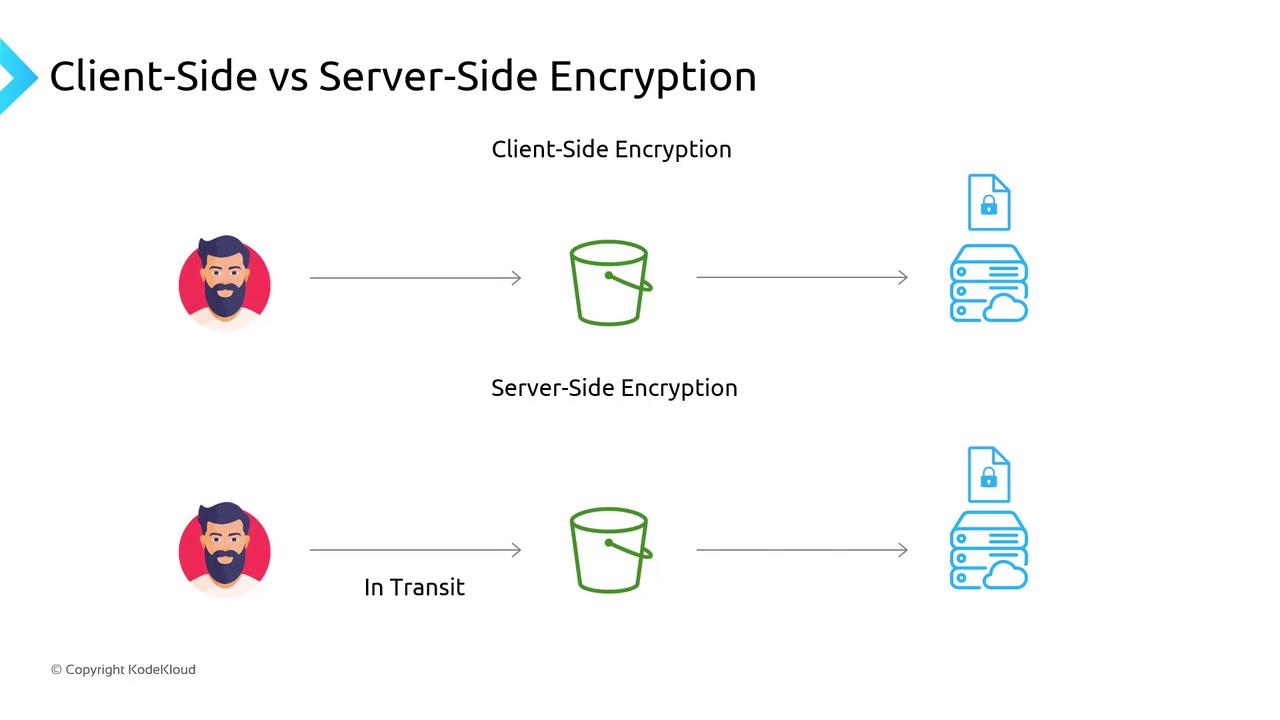
Client-Side vs. Server-Side Encryption
- Client-Side Encryption: You generate, manage, and store keys. You encrypt data locally, then upload only ciphertext to S3.
- Server-Side Encryption: You send plaintext over HTTPS; AWS encrypts it at rest using the method you choose.
S3 supports three server-side methods:

Per-Object Encryption and Bucket Defaults
- Encryption is configured per object.
- You can set a default encryption on the bucket so that any upload without explicit encryption uses the bucket’s setting.
- You can still override the default on a per-object basis.

Note
When you enable default encryption on a bucket, uploads without specified encryption inherit the bucket’s default settings.
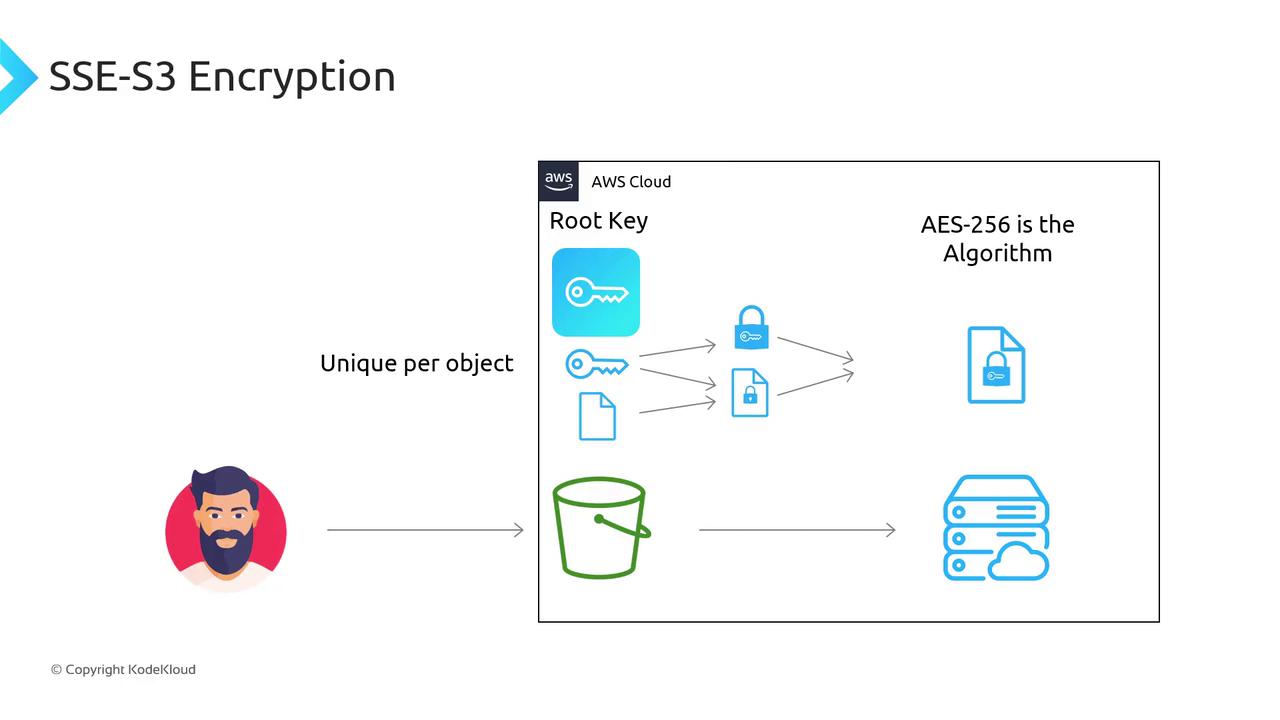
SSE-S3 (Server-Side Encryption with Amazon S3-Managed Keys)
With SSE-S3, AWS handles all key management using AES-256:
- Key generation & management: AWS
- Encryption algorithm: AES-256
- Responsibilities: AWS S3
Encryption Flow
- AWS maintains a master root key (opaque to you).
- For each object, S3 generates a unique data key.
- The object is encrypted with the data key (AES-256).
- The data key is encrypted with the root key.
- Both encrypted object and encrypted data key are stored.
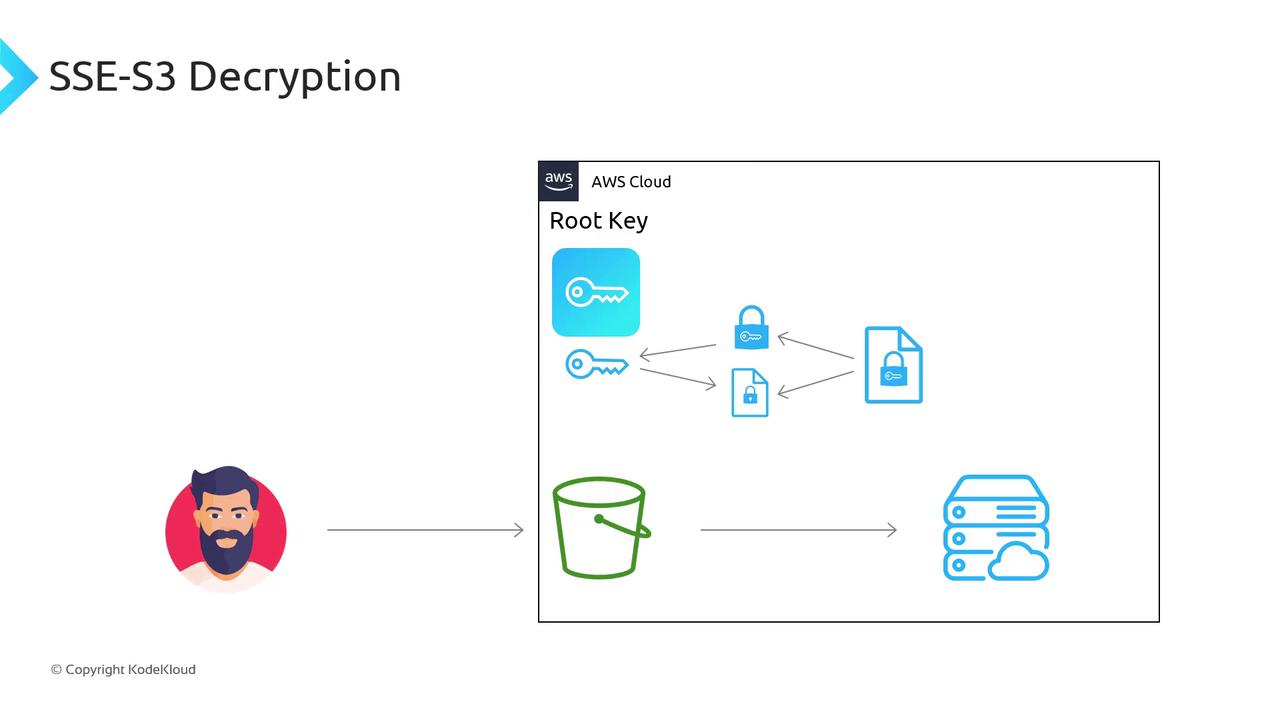
Decryption Flow
- S3 decrypts the data key using the root key.
- S3 decrypts your object with the data key.
- Plaintext is returned to you.
AWS CLI Example
aws s3 cp file.txt s3://my-bucket/ --sse AES256
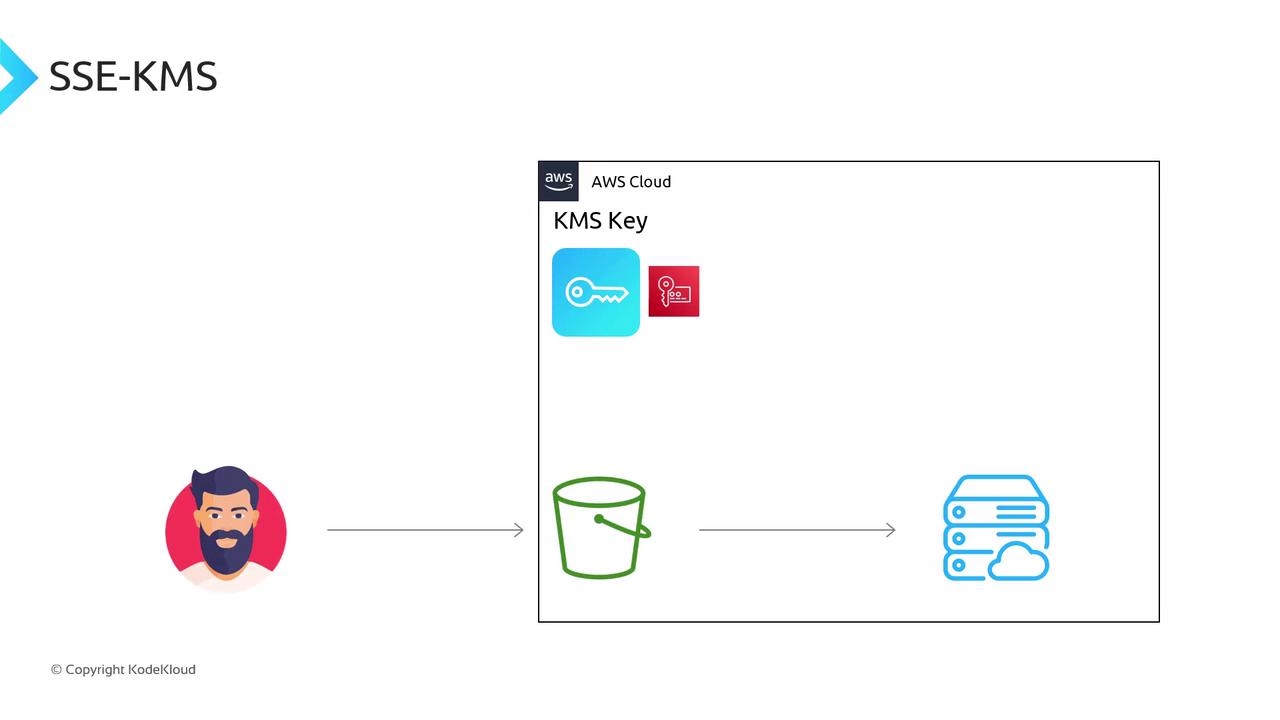
SSE-KMS (Server-Side Encryption with AWS KMS Keys)
SSE-KMS integrates AWS Key Management Service for advanced control:
- Key management: AWS KMS
- Encryption/decryption: AWS KMS invoked by S3
- Features: Key policies, automatic rotation, CMK metadata
The flow is similar to SSE-S3 but uses a KMS Customer Master Key (CMK):
AWS CLI Examples
# Use default AWS managed KMS key
aws s3 cp file.txt s3://my-bucket/ --sse aws:kms
# Specify a custom CMK
aws s3 cp file.txt s3://my-bucket/ \
--sse aws:kms \
--sse-kms-key-id alias/my-kms-key
Boto3 Example
import boto3
s3 = boto3.client('s3')
# Default KMS key
s3.put_object(
Bucket='my-bucket',
Key='file.txt',
Body=b'Data',
ServerSideEncryption='aws:kms'
)
# Custom CMK
s3.put_object(
Bucket='my-bucket',
Key='file2.txt',
Body=b'More data',
ServerSideEncryption='aws:kms',
SSEKMSKeyId='arn:aws:kms:us-west-2:123456789012:key/abcd-efgh'
)
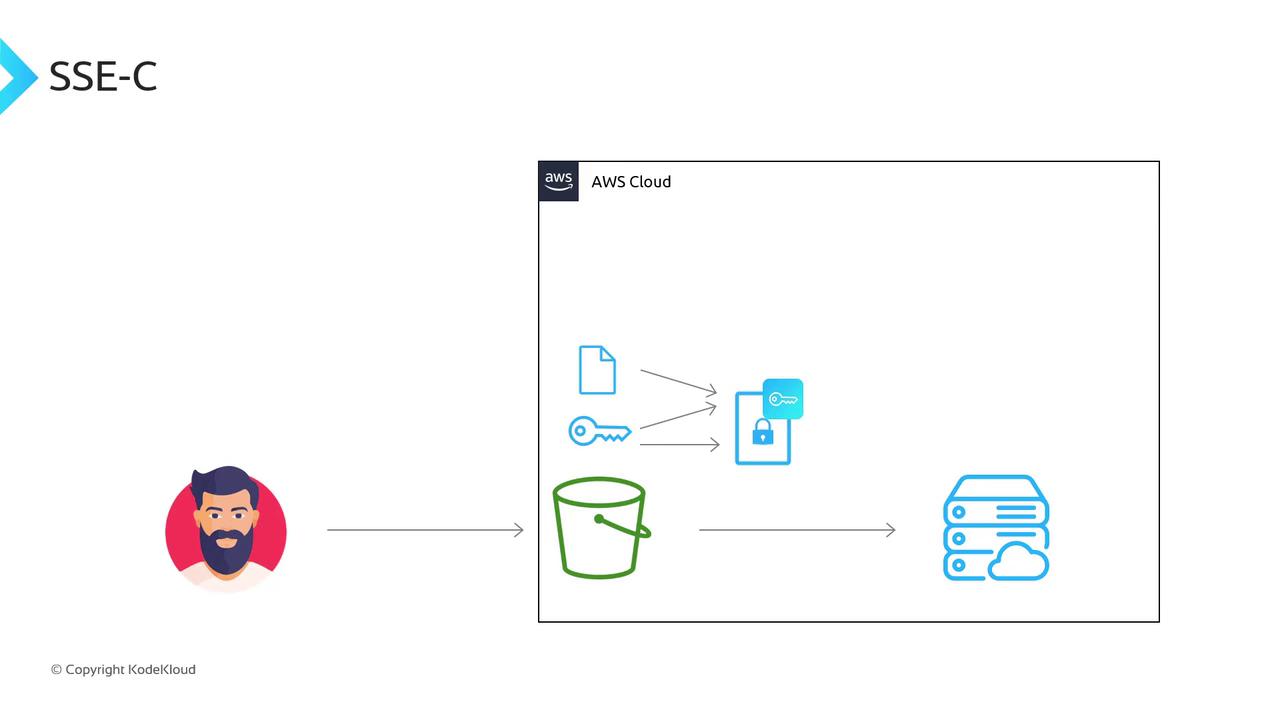
SSE-C (Server-Side Encryption with Customer-Provided Keys)
With SSE-C, you provide the encryption key on each request:
- Key management: Client
- Encryption/decryption: S3
- S3 stores only the MD5 hash of your key for verification
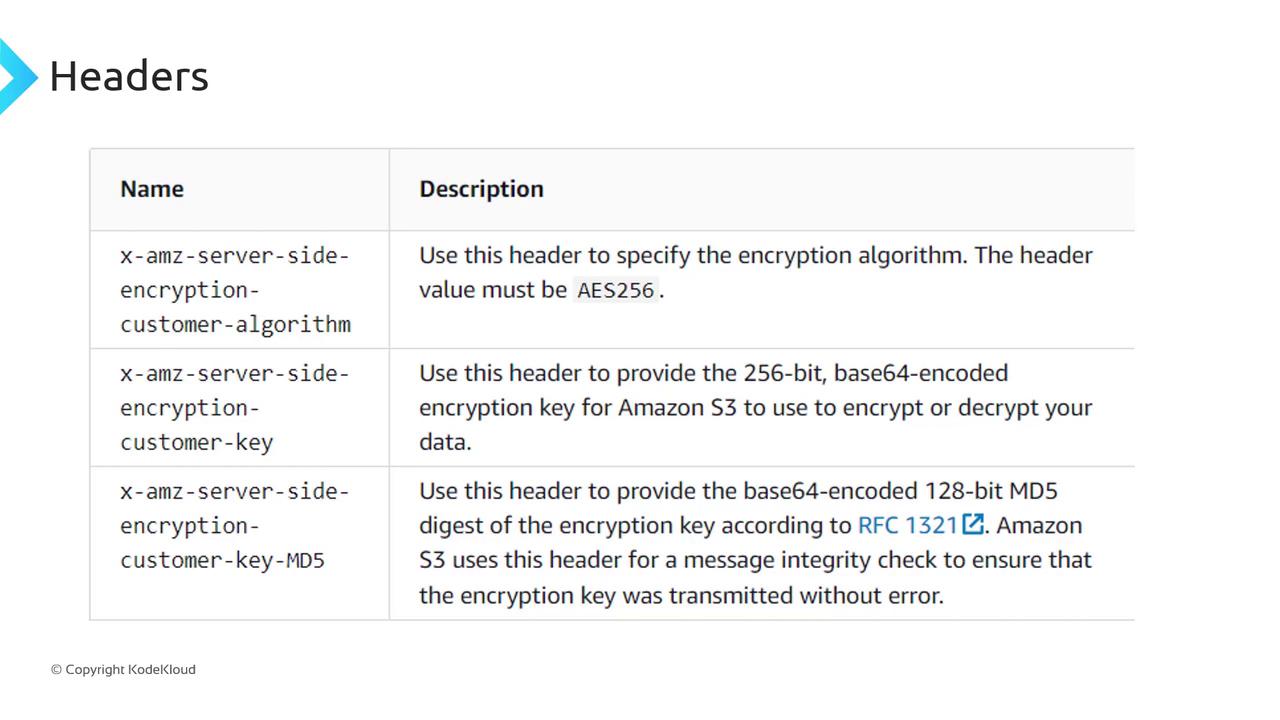
Include these headers (or equivalent CLI/SDK options):
x-amz-server-side-encryption-customer-algorithm: AES256x-amz-server-side-encryption-customer-key: <Base64-encoded key>x-amz-server-side-encryption-customer-key-MD5: <Base64-encoded MD5 of key>
Warning
AWS does not store your customer-provided key. If you lose the key, your data cannot be decrypted.
AWS CLI Example
aws s3 cp file.txt s3://my-bucket/ \
--sse-c AES256 \
--sse-c-key fileb://key.bin \
--sse-c-copy-source-key fileb://key.bin
Boto3 Example
import hashlib
import boto3
# Read or generate a 256-bit key
with open('key.bin', 'rb') as f:
key = f.read()
md5 = hashlib.md5(key).digest()
s3 = boto3.client('s3')
s3.put_object(
Bucket='my-bucket',
Key='file.txt',
Body=b'Sensitive data',
SSECustomerAlgorithm='AES256',
SSECustomerKey=key,
SSECustomerKeyMD5=md5
)
Encryption Headers and Comparison Summary
Below is a quick reference of S3 server-side encryption headers:
| Encryption Method | Key Management | Encryption/Decryption |
|---|---|---|
| Client-Side | Client | Client |
| SSE-C | Client | S3 |
| SSE-S3 | AWS S3 | AWS S3 |
| SSE-KMS | AWS KMS | AWS S3 / AWS KMS |

Choose the encryption approach that balances control, security, and operational overhead for your use case.
Links and References
Watch Video
Watch video content