Certificate files follow specific naming conventions. Public key certificates typically have a .crt or .pem extension (e.g., server.crt, server.pem, client.crt, client.pem). In contrast, private keys usually include the word “key” in their file name or extension (e.g., server.key or server-key.pem). If a file name lacks “key,” it is almost certainly a public key certificate.
TLS Certificates in the Kubernetes Cluster
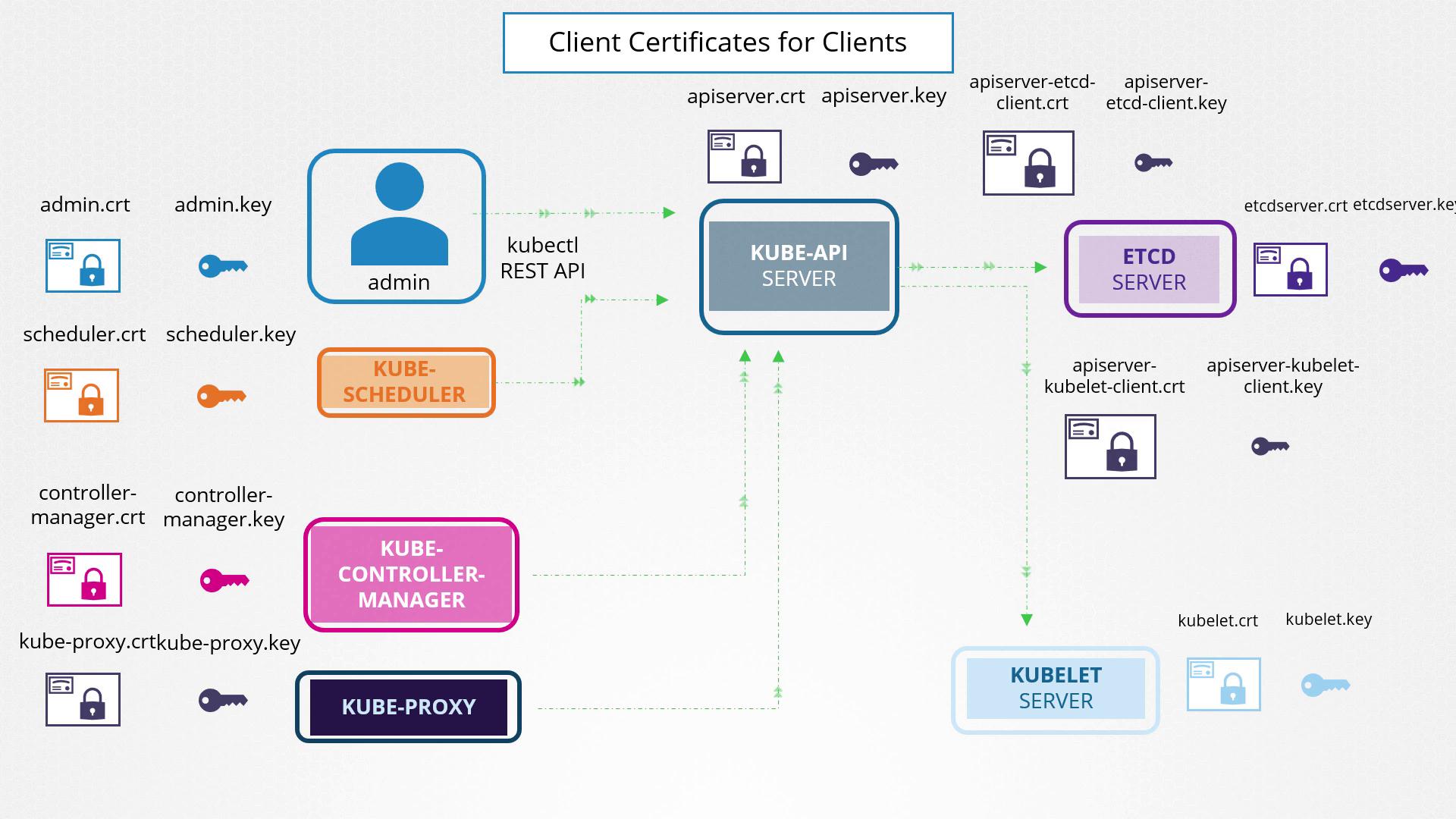
A Kubernetes cluster consists of master and worker nodes that require secure, encrypted communication. Whether the connection is being made by an administrator using the kubectl utility or directly interacting with the Kubernetes API, a secure TLS connection is essential. Additionally, services within the cluster use server certificates to secure their communications, while client certificates authenticate users or other cluster components.Kubernetes Components and Their Certificates
Below is an overview of the main Kubernetes components and the associated certificate configurations:-
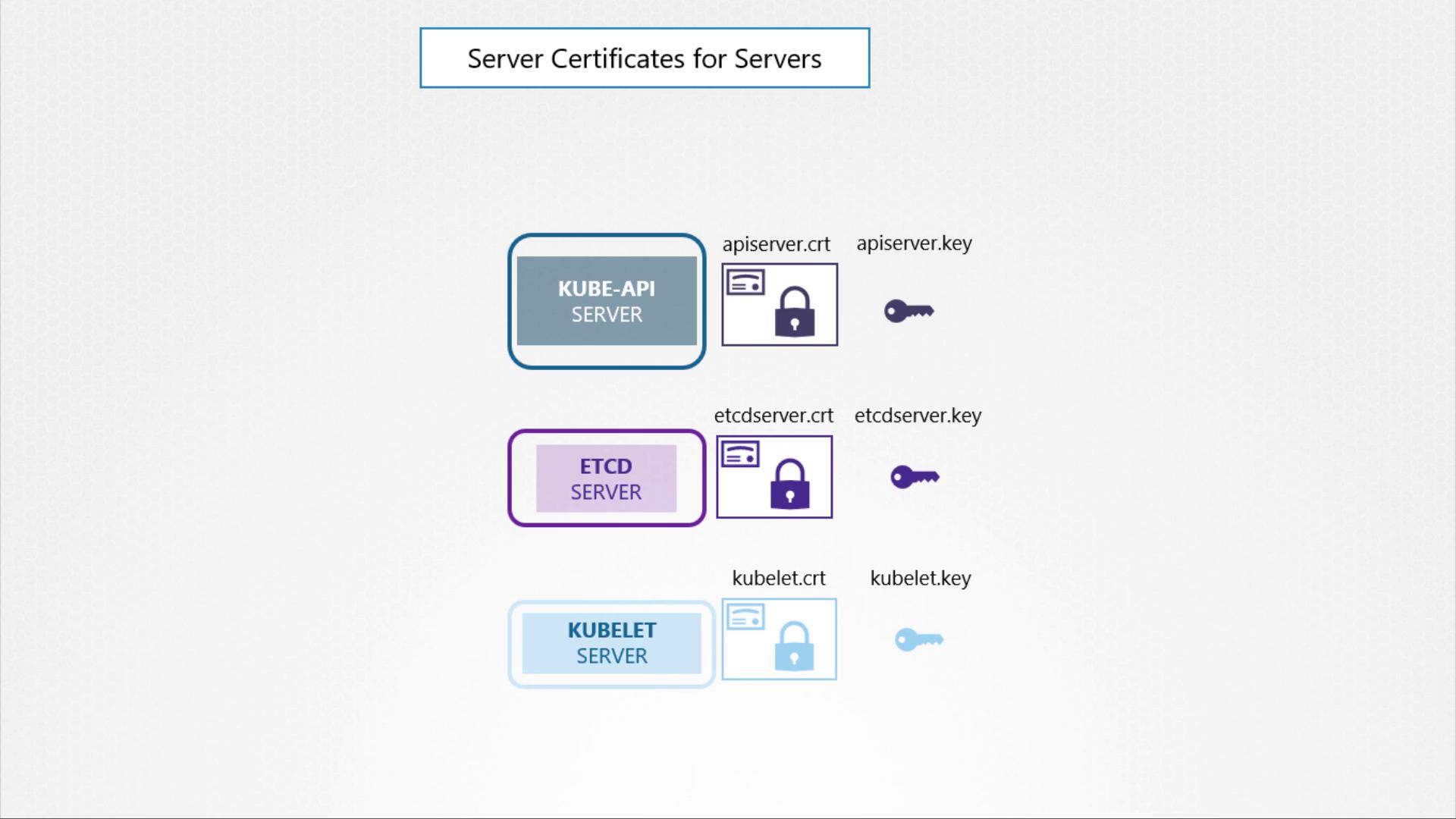
Kube API Server
The API server exposes an HTTPS service for managing the cluster. It acts as a server and requires its own certificate and key pair (e.g.,api-server.crtandapi-server.key).
Note: Certificate names may vary based on your cluster setup. -
ETCD Server
Serving as the datastore for all cluster information, ETCD requires a unique pair of certificates and keys (e.g.,etcd-server.crtandetcd-server.key). -
Kubelet on Worker Nodes
On each worker node, the kubelet service exposes an HTTPS endpoint that communicates with the API server for monitoring and management. This service uses its own certificate and key pair (typically namedkubelet.certandkubelet.key).
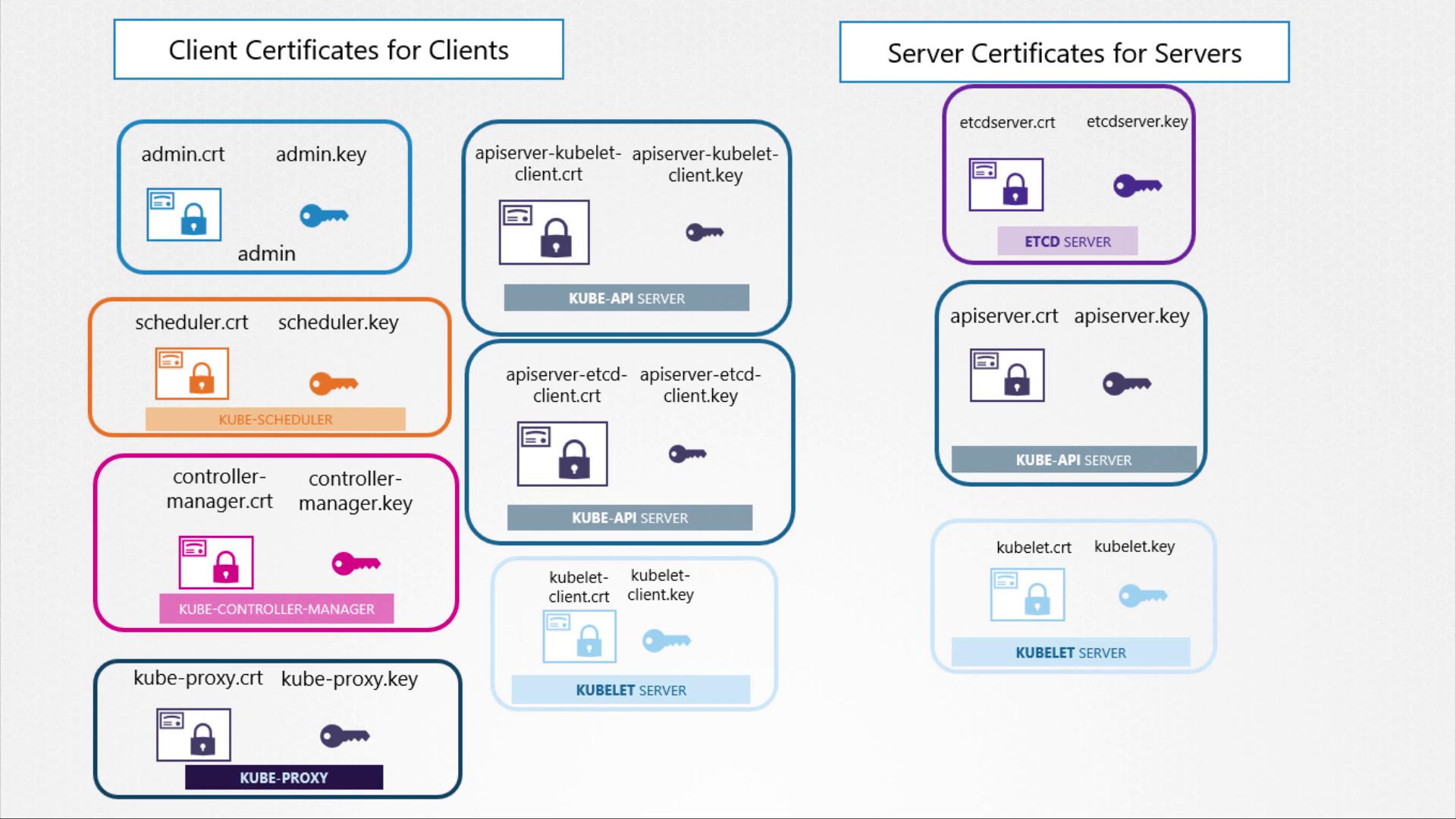
Client Components and Their Certificates
Several components operate as clients and require authentication when connecting to the Kube API Server:-
Administrator (kubectl/REST API)
The admin user employs a client certificate and key pair (e.g.,admin.crtandadmin.key) to establish a secure connection to the API server. -
Scheduler
Managing pod scheduling, the scheduler requires its own client certificate (e.g.,scheduler.crtandscheduler.key) to interact with the API server. -
Kube Controller Manager
This component also utilizes a dedicated certificate pair for authenticating its requests to the API server. -
Kube Proxy
Handling network routing within the cluster, the kube proxy uses a client certificate (generally namedkube-proxy.crtandkube-proxy.key) for secure communications with the API server.
Grouping Certificates for Enhanced Management
For easier certificate management, you can group TLS certificates into two main categories:| Category | Usage |
|---|---|
| Client Certificates | Used by components (e.g., admin, scheduler, controller manager, kube-proxy) to authenticate with the API server. |
| Server Certificates | Used by server components (e.g., Kube API Server, ETCD Server, kubelet) to secure their services. |
Utilizing a Certificate Authority (CA)
All certificates must be signed by a Certificate Authority. Kubernetes clusters require at least one CA, though multiple CAs may be used for additional segregation (for example, one CA for general cluster services and another exclusively for ETCD). In this guide, we use a single CA for simplicity. The CA itself has a certificate and key pair, typically namedCA.crt and CA.key.