Certified Jenkins Engineer
Containerization and Deployment
Demo Exploring AWS and Setting up Jenkins Instance
In this lesson, we begin the deployment phase of our CI/CD pipeline using AWS services—EC2, S3, and Lambda. You’ll see how to prepare your AWS environment, install necessary Jenkins plugins, and configure both AWS and SSH credentials to automate deployments.
Reviewing the EC2 Instance
Navigate to the EC2 Instances dashboard in the AWS Console. You should see a single instance named dev-deploy in the running state.
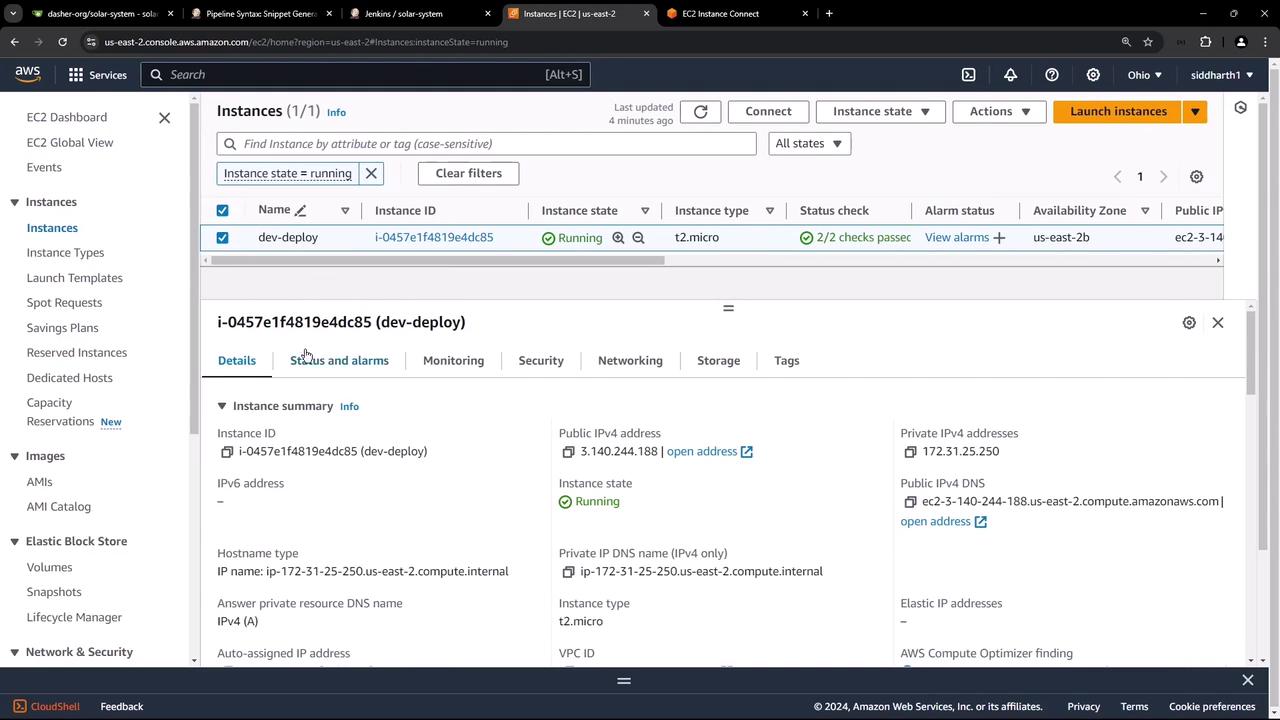
This VM already has Docker installed. To verify, SSH into the instance and run:
sudo docker ps
CONTAINER ID IMAGE NAMES
f0f9299ee8fe siddharth67/solar-system:7d1e24920bd455706b179c6724d5566d797634 solar-system
0.0.0.0:3000->3000/tcp
We’ll use this EC2 host to deploy our feature-branch Docker images.
Setting Up AWS IAM Credentials
Create an IAM user (jenkins-user) with full access to EC2, S3, and Lambda. Attach these managed policies:
| Policy Name | Service | Access Level |
|---|---|---|
| AmazonEC2FullAccess | EC2 | Full |
| AmazonS3FullAccess | S3 | Full |
| AWSLambda_FullAccess | Lambda | Full |
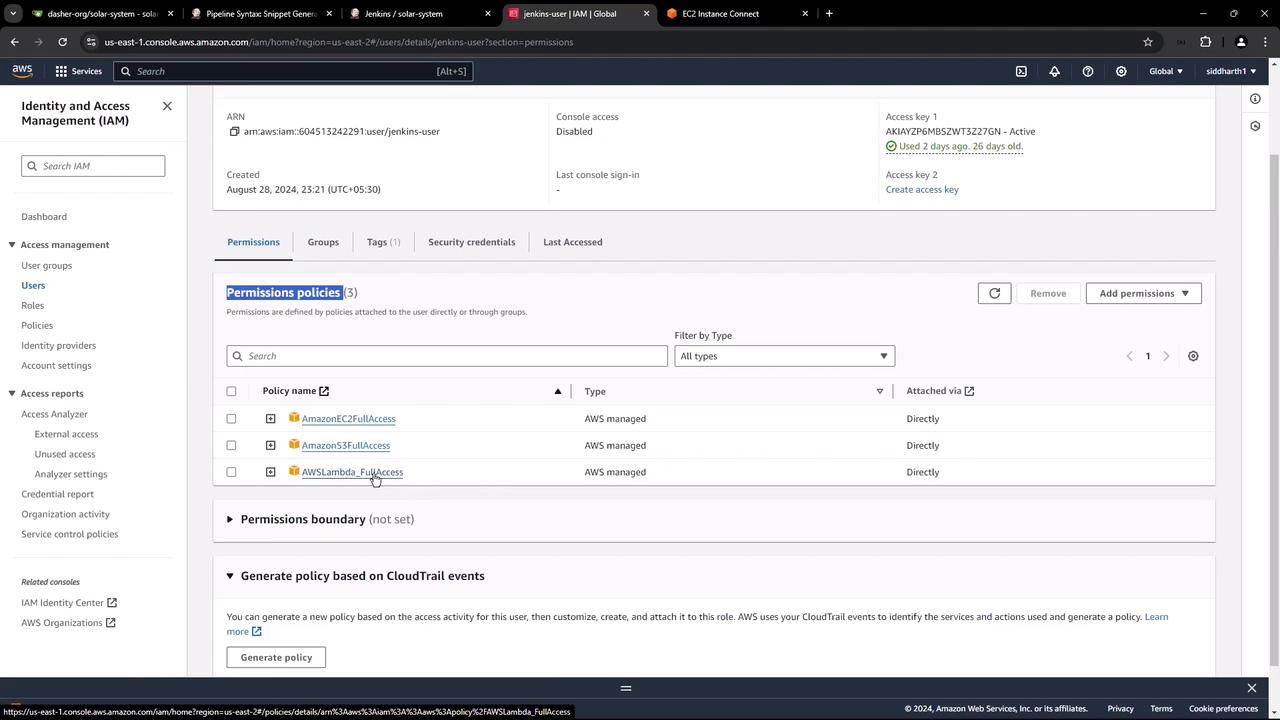
Once created, AWS will display the Access Key ID and Secret Access Key.
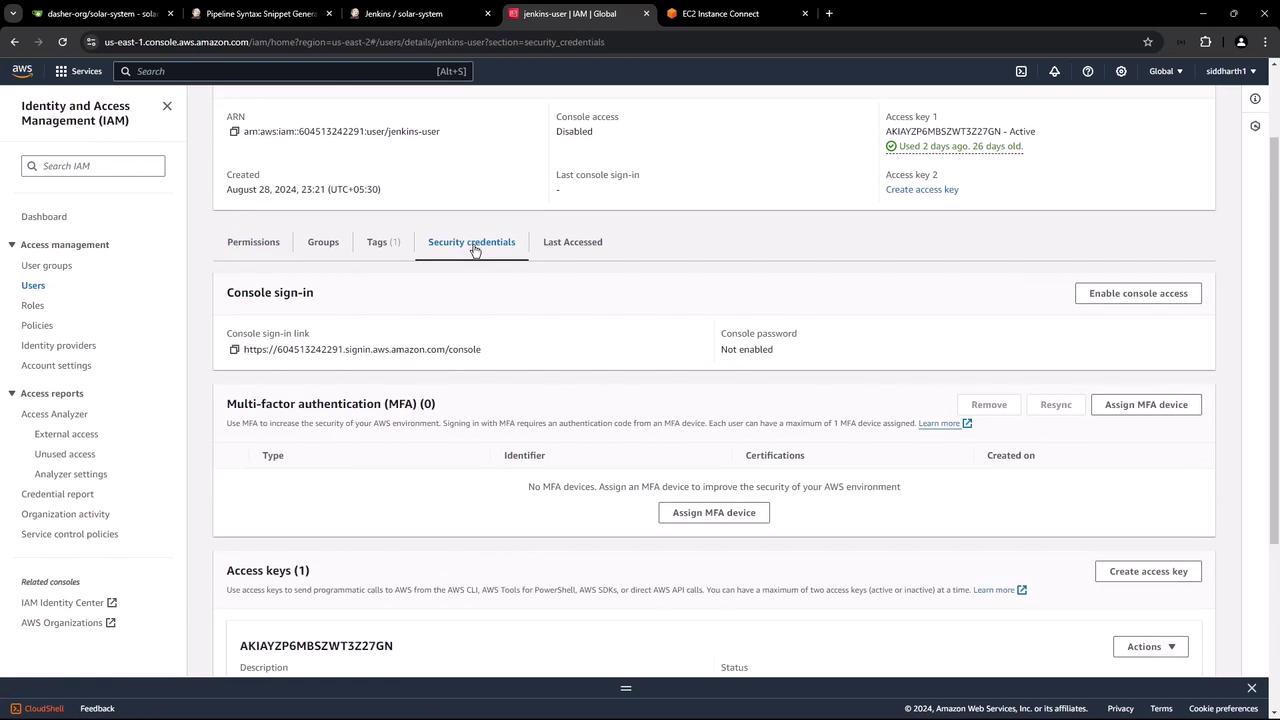
Warning
Keep your Access Key ID and Secret Access Key safe—do not commit them to source control.
Finally, review your user details to confirm MFA and key status:

Installing the AWS Steps Plugin in Jenkins
To enable AWS API calls in your pipelines, install the Pipeline: AWS Steps plugin:
- In Jenkins, go to Manage Jenkins → Manage Plugins → Available.
- Search for Pipeline: AWS Steps, select it, and click Install without restart.
- Restart Jenkins when prompted.
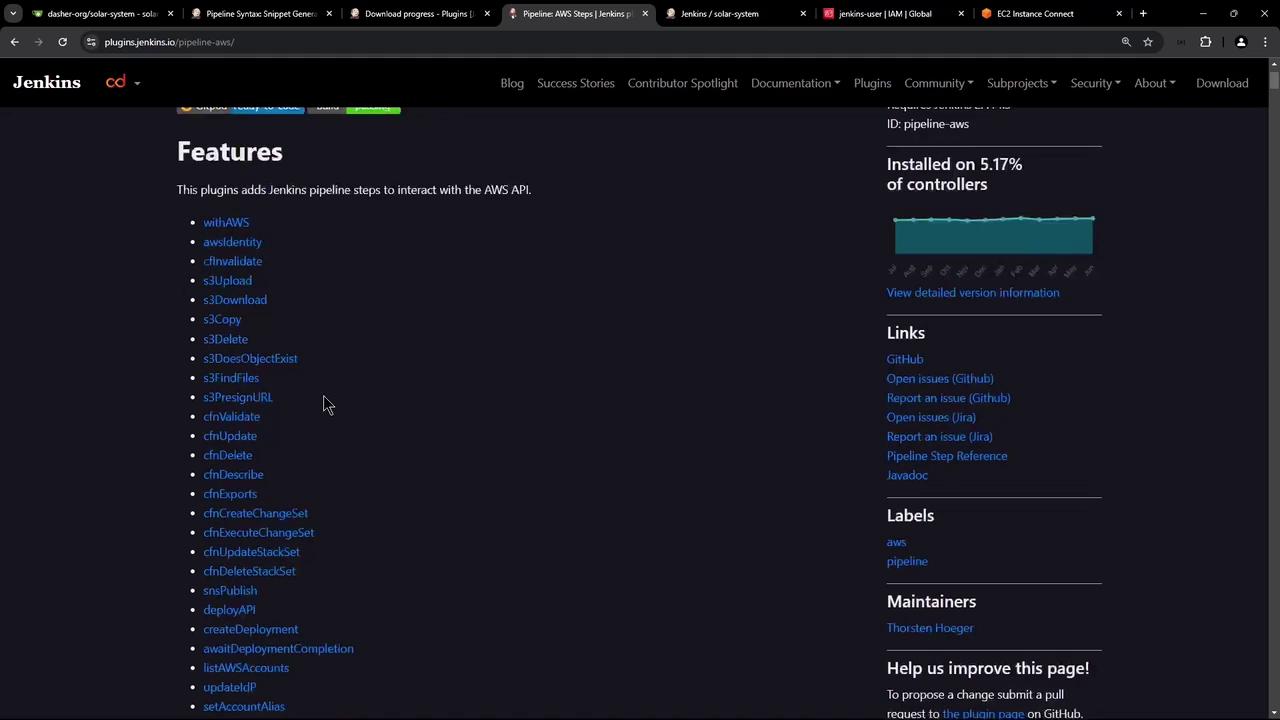
Here are a few example steps you can use in your Jenkinsfile:
| Step | Description | Example |
|---|---|---|
| s3DoesObjectExist | Check if an object exists in a bucket | exists = s3DoesObjectExist(bucket: 'my-bucket', path: 'file.txt') |
| s3FindFiles | List files in an S3 bucket | files = s3FindFiles(bucket: 'my-bucket', glob: 'path/to/*.ext') |
Note
After plugin installation, always restart Jenkins to load new pipeline steps.
Configuring AWS Credentials in Jenkins
Next, store your IAM keys in Jenkins:
- Go to Manage Jenkins → Manage Credentials → (global) → Add Credentials.
- Select Kind: AWS Credentials.
- Enter an ID (e.g.,
aws-s3-ec2-lambda), paste your Access Key ID and Secret Access Key, then save.
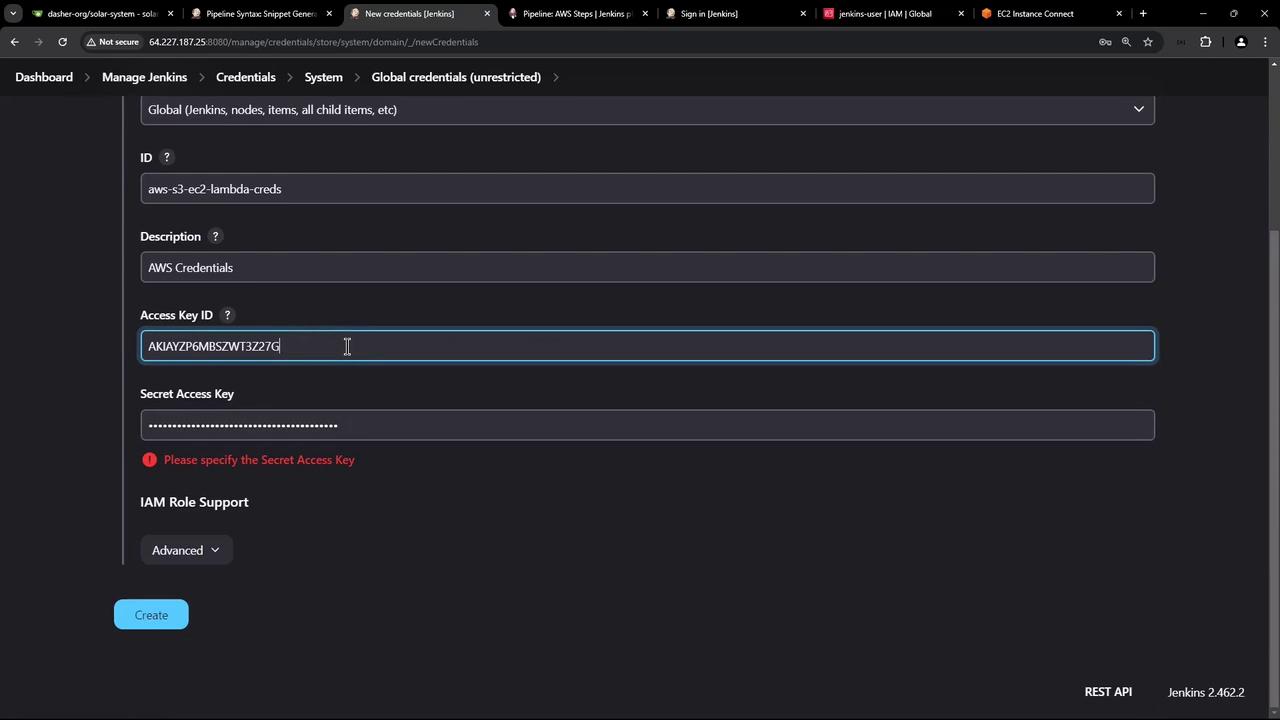
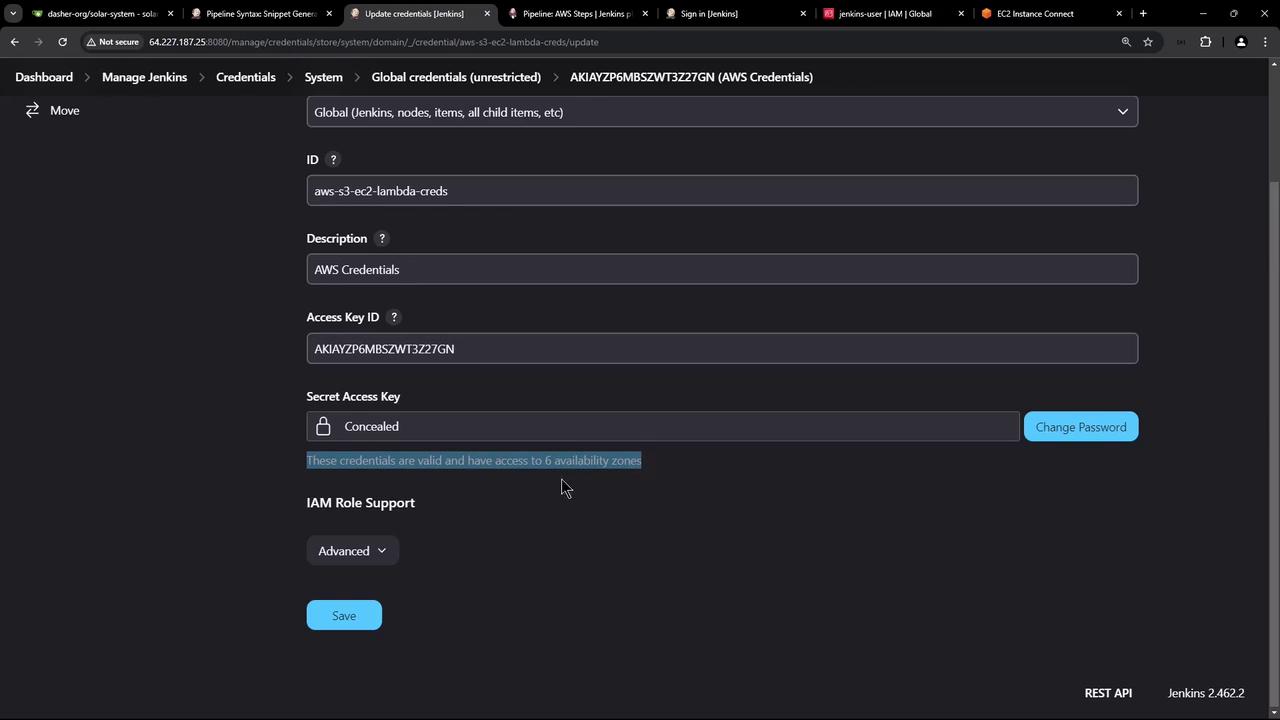
Jenkins will validate these credentials automatically:
Adding SSH Credentials for EC2
To deploy Docker images over SSH, install the SSH Agent plugin:
- Go to Manage Jenkins → Manage Plugins → Available.
- Search for SSH Agent and install.
Then add your EC2 key:
- Navigate to Manage Jenkins → Manage Credentials → (global) → Add Credentials.
- Choose SSH Username with private key.
- Specify an ID (e.g.,
aws-devops-deploy-ec2), Username (ubuntu), and paste your private key. - Save.
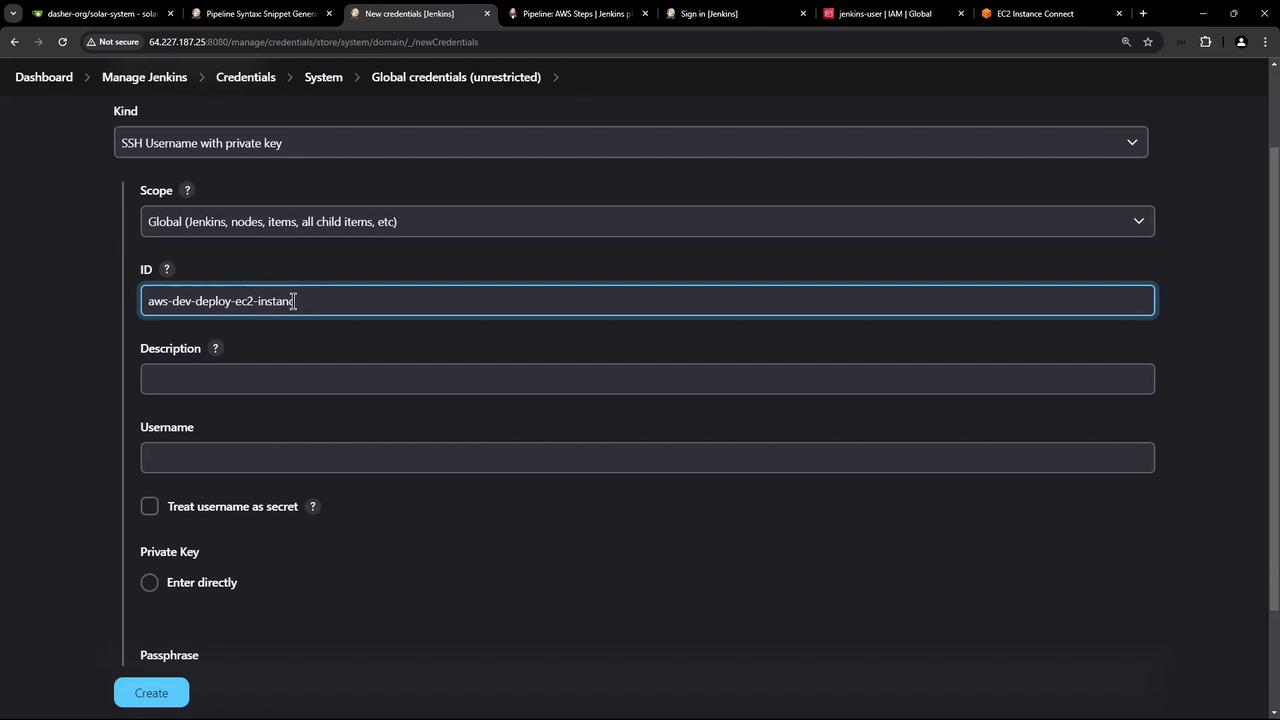
With AWS Steps and SSH Agent plugins installed, AWS IAM and SSH credentials configured, you’re ready to add a pipeline stage that connects to your EC2 instance and deploys Docker images.
Links and References
Watch Video
Watch video content