Certified Kubernetes Security Specialist (CKS)
Cluster Setup and Hardening
Kubernetes Security Primitives
Welcome to our comprehensive guide on Kubernetes security primitives. As Kubernetes has become the industry standard for hosting production-grade applications, ensuring robust security practices is more important than ever. This article provides a high-level overview of critical security measures in Kubernetes, with detailed explorations to follow in subsequent posts.
Securing the Cluster Hosts
Before diving into the intricacies of Kubernetes security, it is essential to secure the underlying infrastructure. Ensure that all hosts in your Kubernetes cluster are protected by:
- Disabling root access and password-based authentication.
- Enabling SSH key-based authentication.
- Implementing additional security measures to protect the physical or virtual infrastructure hosting Kubernetes.
Infrastructure Security Reminder
If the underlying infrastructure is compromised, the security of the entire Kubernetes cluster is at risk.
Kubernetes API Server: The Entry Point
At the core of Kubernetes operations lies the kube API server. Users interact with the cluster through the kubectl utility or direct API calls. This interaction is crucial because it governs nearly all cluster operations. Therefore, two fundamental questions arise:
- Who can access the cluster?
- What actions can they perform?
Authentication
Access to the API server is regulated by robust authentication mechanisms. Kubernetes supports multiple methods, including:
- Static files with user IDs and passwords
- Tokens
- Certificates
- Integrations with external providers such as LDAP
- Service accounts for machine-to-machine communications
These diverse approaches ensure that every connection is verified, offering flexibility and security simultaneously.

Authorization
Once users or services are authenticated, authorization mechanisms determine their permitted actions on the cluster. Kubernetes primarily uses Role-Based Access Control (RBAC) to map users to groups with specific permissions. Other authorization modules available include:
- Attribute-Based Access Control (ABAC)
- Node Authorization
- Webhook-based authorization
These systems work together to ensure that every action within the cluster is scrutinized and allowed only if it aligns with the defined permissions.

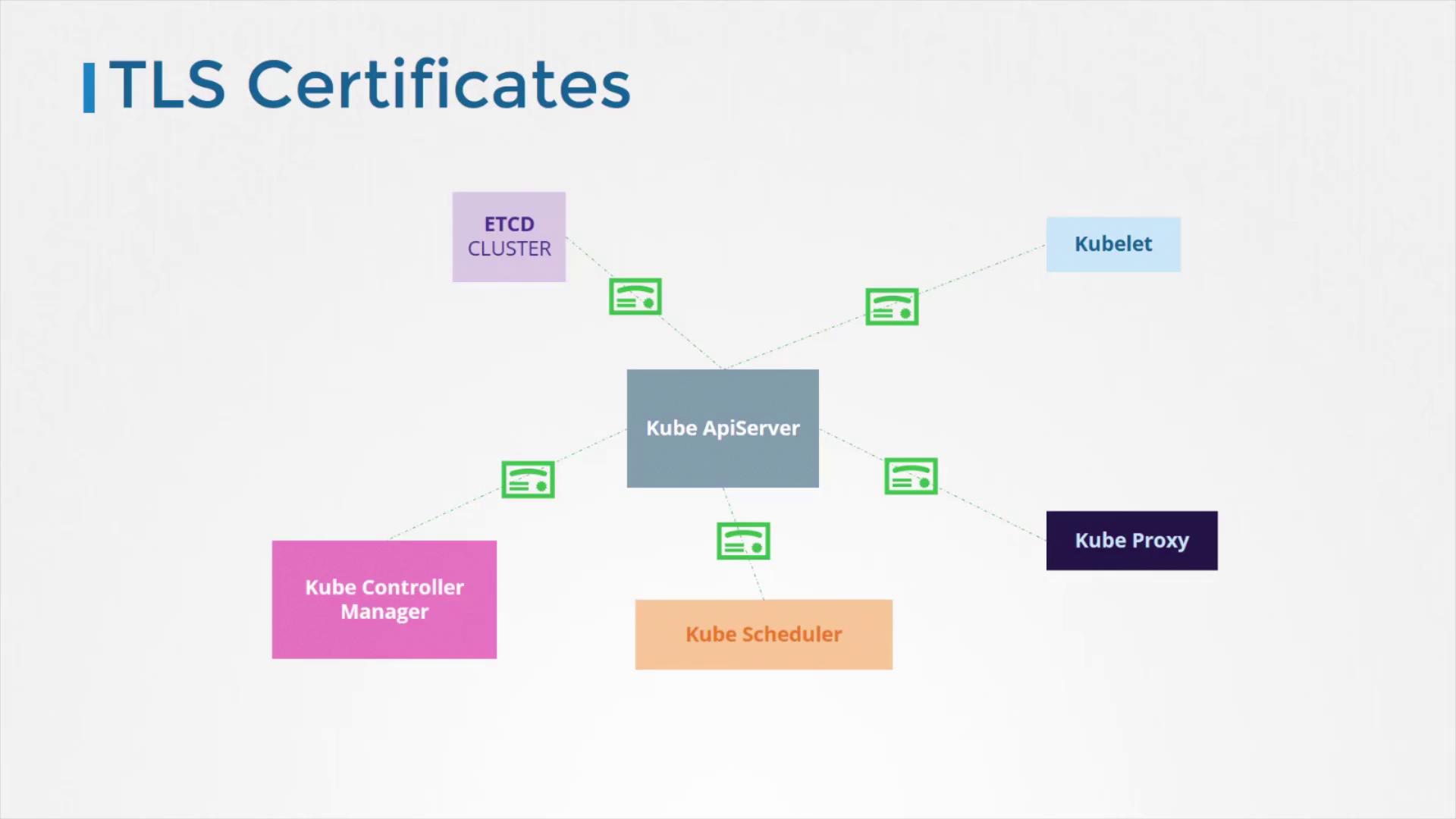
Securing Intra-Cluster Communications
A critical element of Kubernetes security involves securing communications between various cluster components. All interactions between components—such as the etcd cluster, kube controller manager, scheduler, API server, and worker node components (including kubelet and kube-proxy)—are protected using TLS encryption.
TLS Security Implementation
Detailed instructions on setting up certificates for secure communications will be provided in a dedicated section.
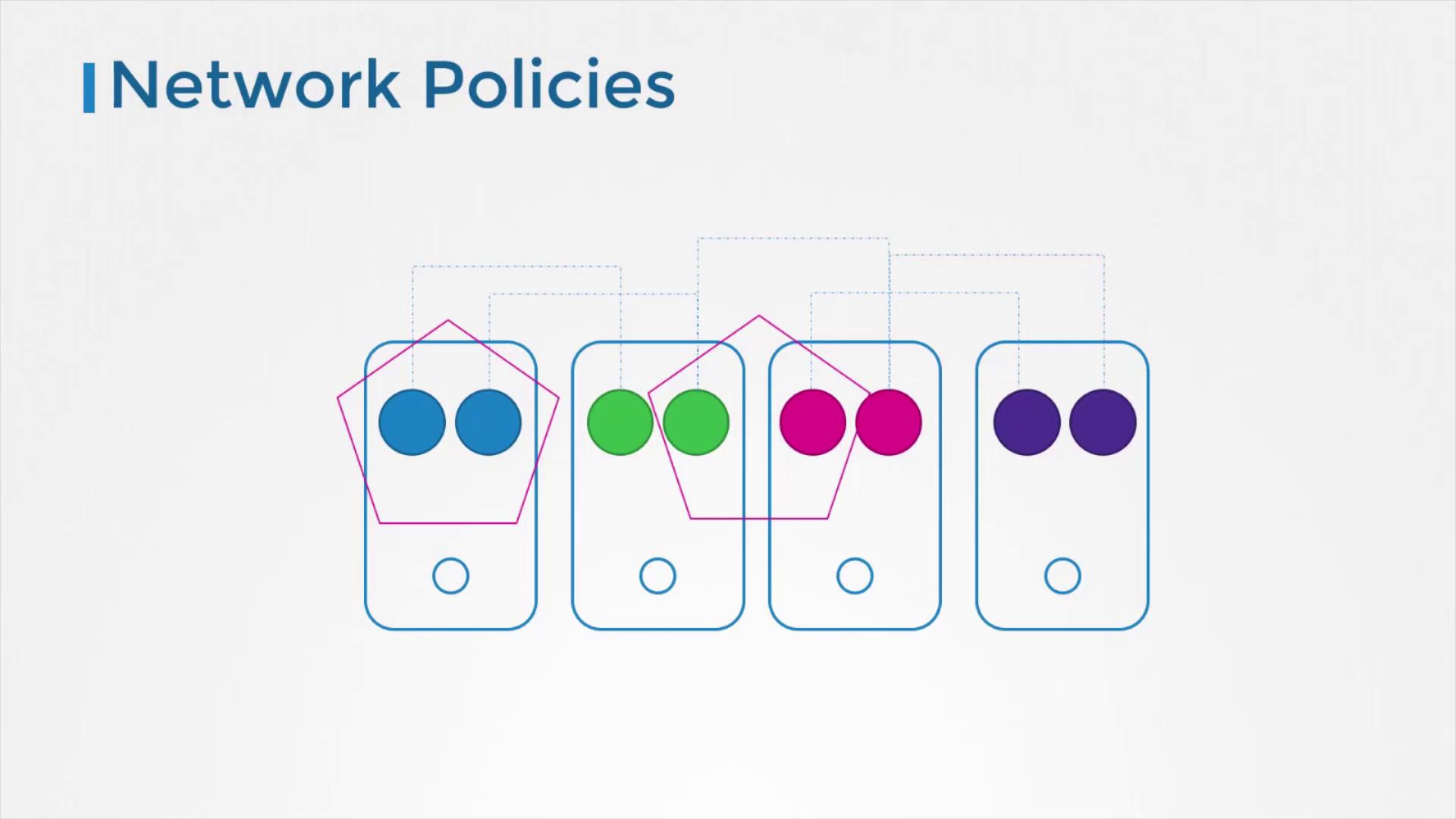
Network Policies Within the Cluster
By default, pods within a Kubernetes cluster can communicate freely with one another. To restrict unwanted access and tighten security, network policies can be implemented. These policies enable you to control traffic flow between pods and are an integral part of securing inter-application communications within the cluster.
In Summary
This article has provided an overview of the key security primitives in Kubernetes:
- Securing cluster hosts
- Strong authentication and authorization methods for the API server
- Using TLS encryption for intra-cluster communications
- Implementing network policies for pod-to-pod communication
We will explore these topics in much greater detail in upcoming articles. Stay tuned as we dive deeper into each security aspect to help you ensure that your Kubernetes environment remains secure and resilient.
For more Kubernetes best practices and security tips, continue following our in-depth guides and tutorials.
Watch Video
Watch video content