Certified Kubernetes Security Specialist (CKS)
Minimize Microservice Vulnerabilities
Implement pod to pod encryption by use of mTLS
In this guide, we explore how to secure pod-to-pod communication within a Kubernetes cluster by leveraging mutual TLS (mTLS) encryption. By implementing mTLS, you ensure that data exchanged between pods remains confidential and tamper-proof.

The Need for Encryption in Kubernetes
Kubernetes clusters often span multiple nodes with numerous pods communicating with each other. By default, these inter-pod communications are unencrypted, which poses a risk if sensitive data—such as customer phone numbers or addresses—is transmitted in plain text. mTLS provides a robust solution by authenticating and encrypting communications between pods, thereby reducing the risks of data breaches and unauthorized access.
Note
Using mTLS in a Kubernetes environment ensures that every pod verifies its communication counterpart, leading to significantly enhanced security across your cluster.
How mTLS Works Between Pods
The process of establishing a secure connection between two pods involves several steps:
- Certificate Request:
Pod A initiates communication by requesting Pod B’s certificate. - Certificate Exchange:
Pod B responds with its certificate and simultaneously requests Pod A’s certificate. - Certificate Validation and Key Exchange:
After validating Pod B's certificate, Pod A sends its public certificate along with a symmetric encryption key. - Secure Communication:
Once Pod B validates Pod A’s certificate, both pods switch to using the symmetric key to encrypt all further communications.
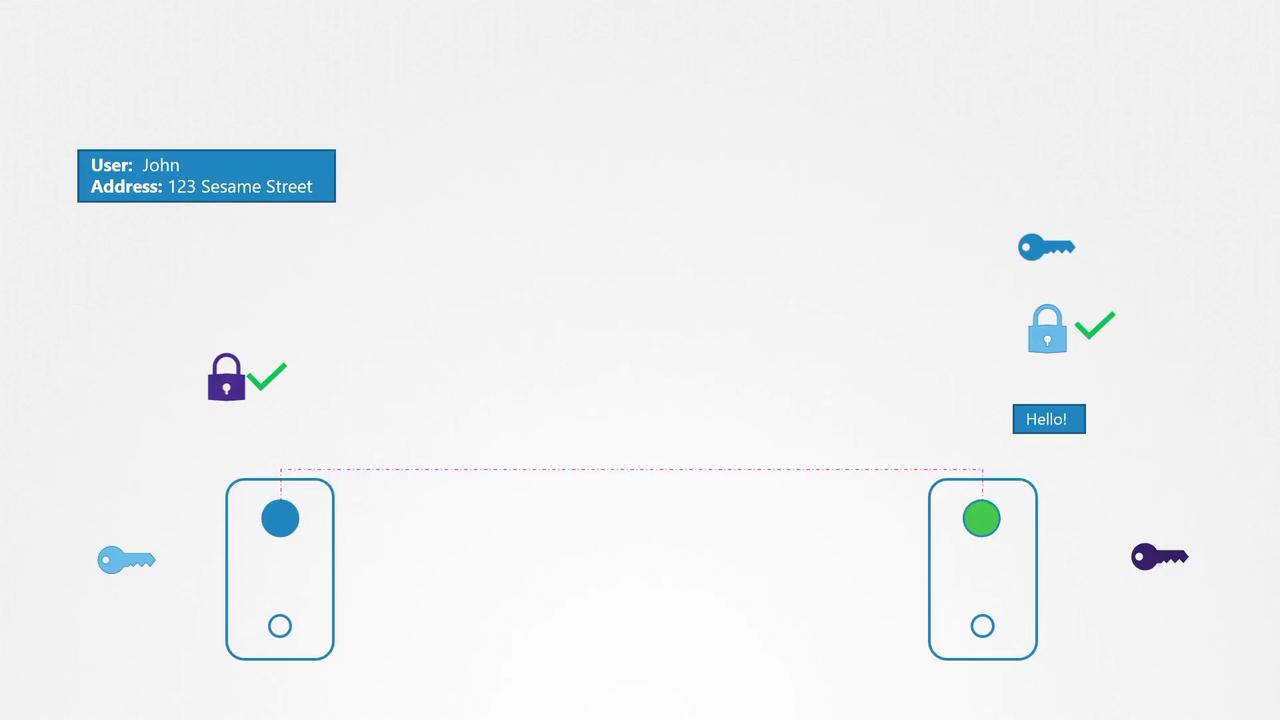
This mutual authentication and encryption ensure that each pod's identity is verified, preventing attackers from introducing fake data or commands.
Managing Encryption Across a Cluster
One might wonder how to manage secure communication when hundreds of pods across several nodes must interact. While some applications, like MySQL, offer built-in encryption, relying solely on individual applications can lead to inconsistencies. Different encryption algorithms may be used, adding complexity and potential security gaps.
A more efficient strategy is to implement mTLS using dedicated service mesh tools. This approach abstracts encryption responsibilities from the application layer to the network layer.
Service Mesh Tools for mTLS
Popular tools such as Istio and Linkerd enable mTLS at the network level, ensuring seamless and consistent encryption for service-to-service communication. These tools:
- Offload encryption tasks from application code.
- Provide centralized management of encryption policies.
- Ensure consistent security across heterogeneous applications.
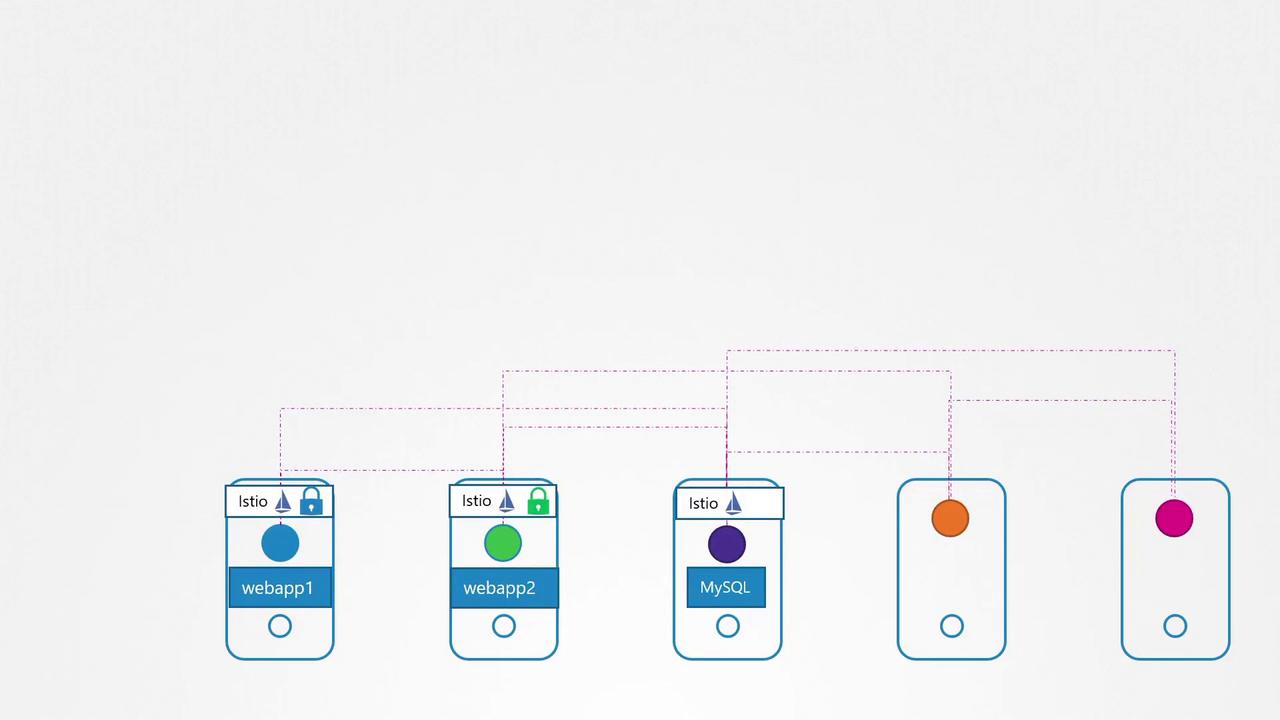
Among these, Istio is widely adopted for its ability to automatically deploy sidecar containers alongside application pods.
Istio and Its Modes of Operation
Istio enhances cluster security by automatically intercepting pod communications. When a web application pod communicates with a MySQL pod, the Istio sidecar attached to each pod encrypts and decrypts messages seamlessly.
Istio supports two primary encryption modes:
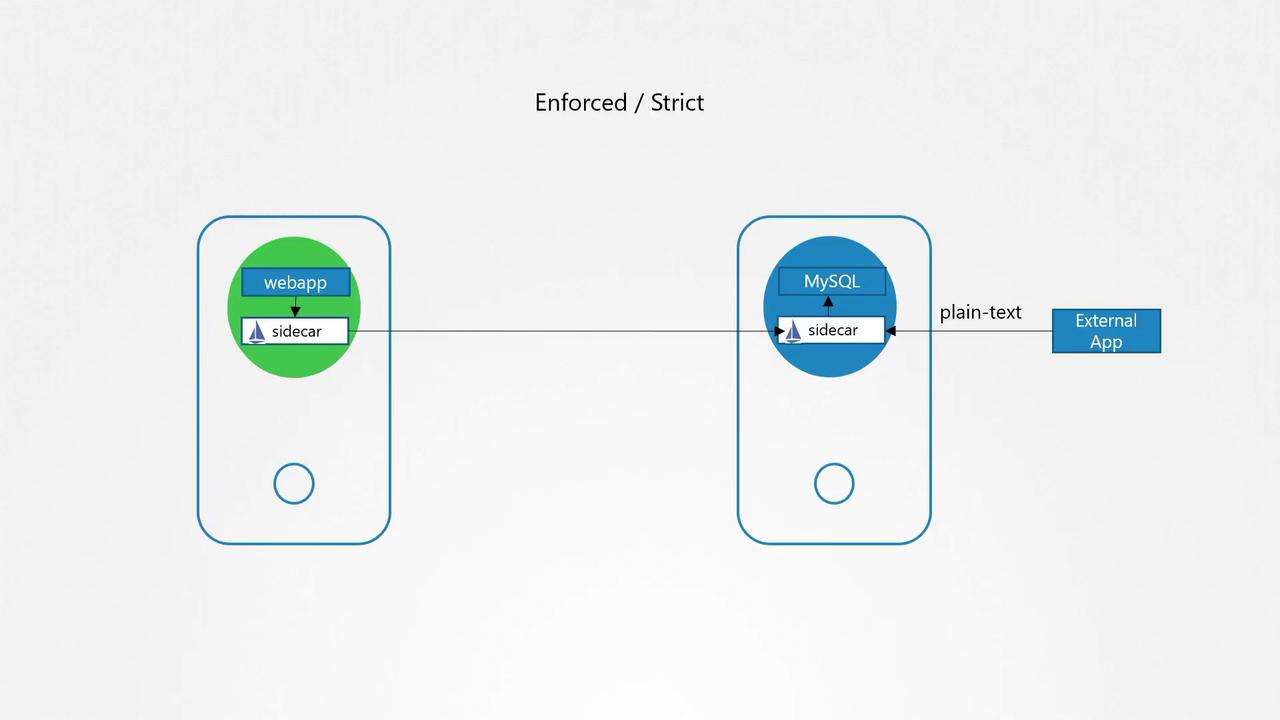
- Permissive (Opportunistic) Mode:
Traffic is encrypted when possible, but unencrypted communication is allowed for interactions with external services or non-mTLS-compatible applications. - Strict (Enforced) Mode:
All traffic must be encrypted using mTLS. Although this maximizes security, it requires all communicating services to support mTLS.
Warning
Before enabling strict mTLS mode, ensure all your services are mTLS-compatible to avoid connectivity issues.
How Istio Implements mTLS
When communication is initiated, Istio’s sidecar intercepts and encrypts outbound messages. On the receiving end, the corresponding sidecar decrypts the message before passing it on to the application. This approach not only secures the traffic but also simplifies the process for developers, as encryption is handled externally.
Conclusion
By integrating mTLS with service mesh technologies like Istio, you can achieve a high level of security within your Kubernetes clusters. This setup ensures that:
- Each pod is mutually authenticated.
- All data in transit is encrypted.
- The encryption overhead is managed independently of the application, contributing to a streamlined and secure infrastructure.
Implementing pod-to-pod encryption using mTLS is a critical step in safeguarding your Kubernetes environment from potential security breaches. For more detailed information on Kubernetes security practices, visit the Kubernetes Documentation.
That concludes our guide on implementing pod-to-pod encryption using mTLS.
Watch Video
Watch video content