Certified Kubernetes Security Specialist (CKS)
Minimize Microservice Vulnerabilities
Introduction to Cilium
In this lesson, we explore how to leverage Cilium for robust Pod-to-Pod encryption. Cilium is an open-source solution that secures network connectivity between containerized applications. Built for modern microservices architectures, it utilizes extended eBPF (Extended Berkeley Packet Filter) to enforce advanced network security policies. Among its many features, pod-to-pod encryption stands out as a key benefit.
Cilium's Approach to Pod-to-Pod Encryption
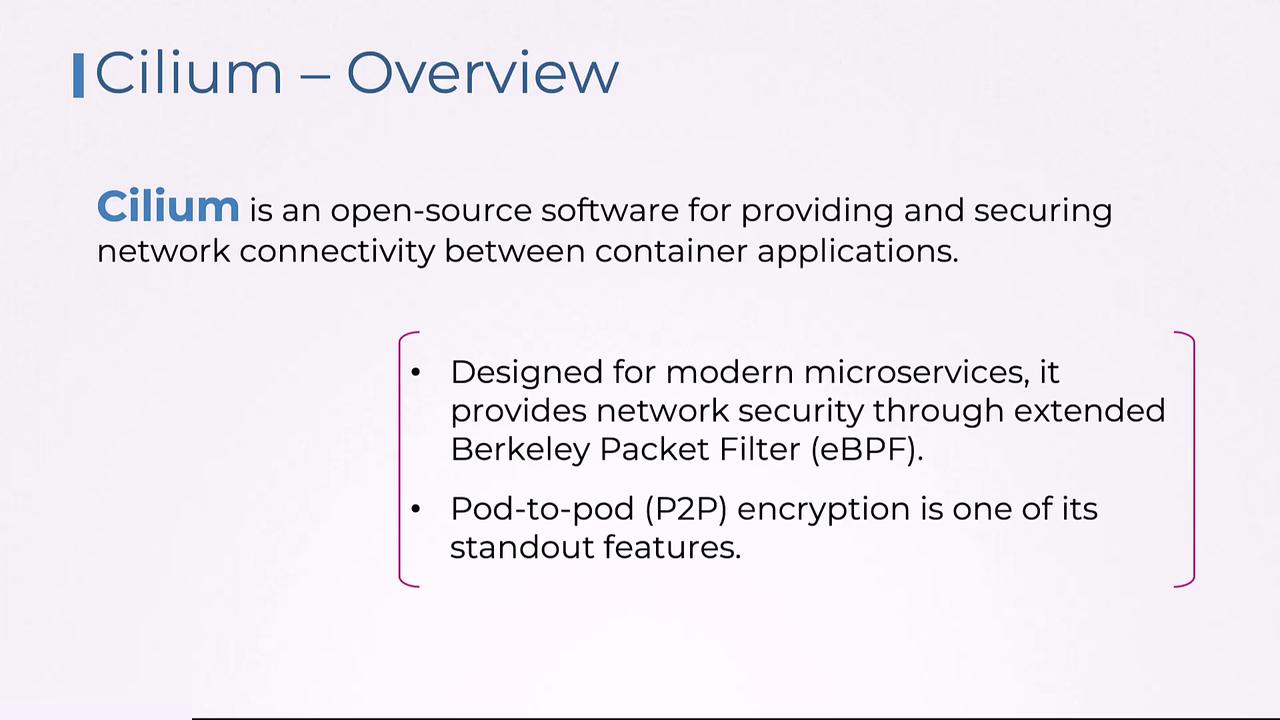
Cilium leverages eBPF for highly efficient data processing, enabling encryption with minimal performance overhead. Encryption is applied transparently, meaning your application code remains unchanged and unaware of the security processes in the background.
Key features include:
- Flexible Encryption Options: Multiple encryption algorithms to suit different use cases.
- End-to-End Security: Continuous encryption ensures data remains secure throughout its network journey.
- Policy-Driven Control: Customizable encryption policies allow precise management of security across the cluster.
Setting Up Cilium
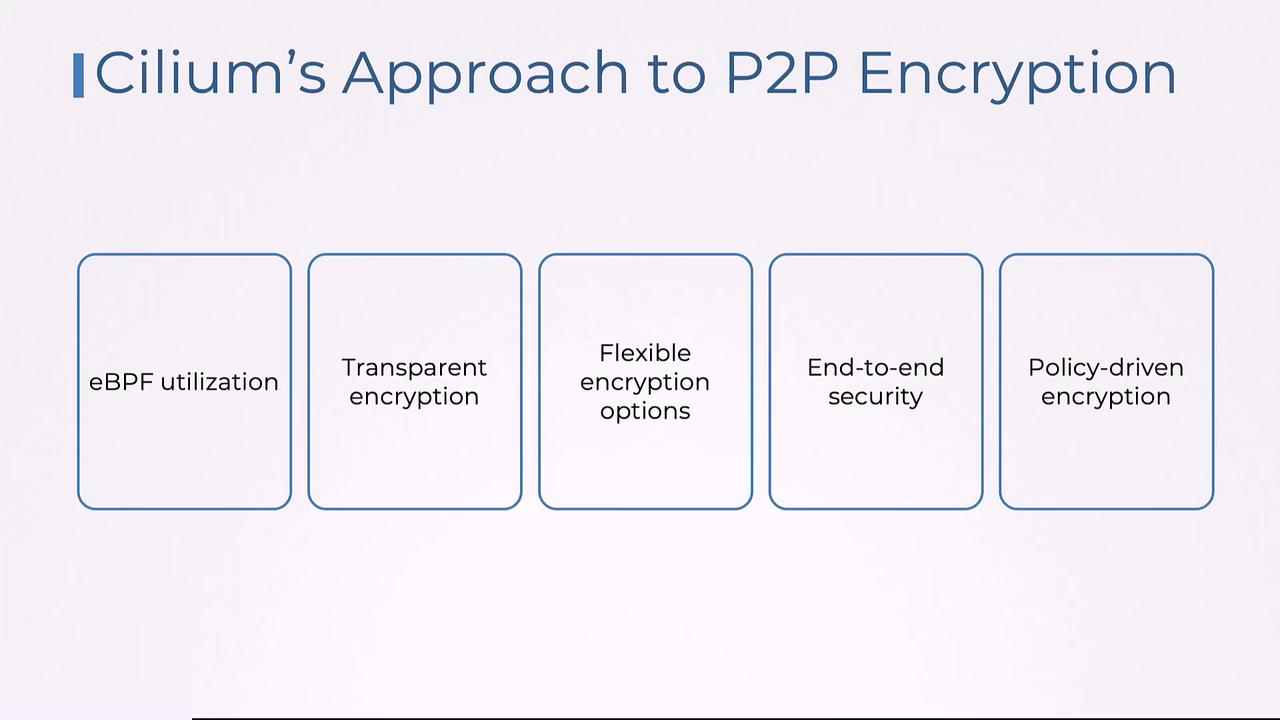
Setting up Cilium for encryption involves several high-level steps:
Installation:
Deploy Cilium on your Kubernetes cluster via Helm or standard manifests, depending on your preferred method.Configuration:
Enable the encryption features explicitly after installation to secure pod-to-pod communications.Key Management:
Utilize Cilium’s native key management system, or integrate it with your existing infrastructure for managing encryption keys.Policy Definition:
Create specific encryption policies based on namespaces or labels to control exactly where and when encryption is applied.
Note
For detailed installation and configuration instructions, refer to the official Cilium documentation.
Monitoring and Performance Benefits
Continuous monitoring is vital to verify that encryption is consistently active and that all inter-pod traffic remains secure. Thanks to its efficient eBPF implementation, Cilium introduces minimal performance overhead while executing encryption and other security tasks. Its robust features include:
- Encryption: Secure data transmission between pods.
- Identity Management: Effective tracking and control of application identities.
- Policy Enforcement: Streamlined application of security policies across your cluster.
These features collectively contribute to making your Kubernetes cluster both secure and easily manageable.
Community Support
Cilium is backed by a vibrant community, including contributions from open-source enthusiasts and enterprise-level organizations, ensuring continuous improvement and support.
Watch Video
Watch video content
Practice Lab
Practice lab