Certified Kubernetes Security Specialist (CKS)
Minimize Microservice Vulnerabilities
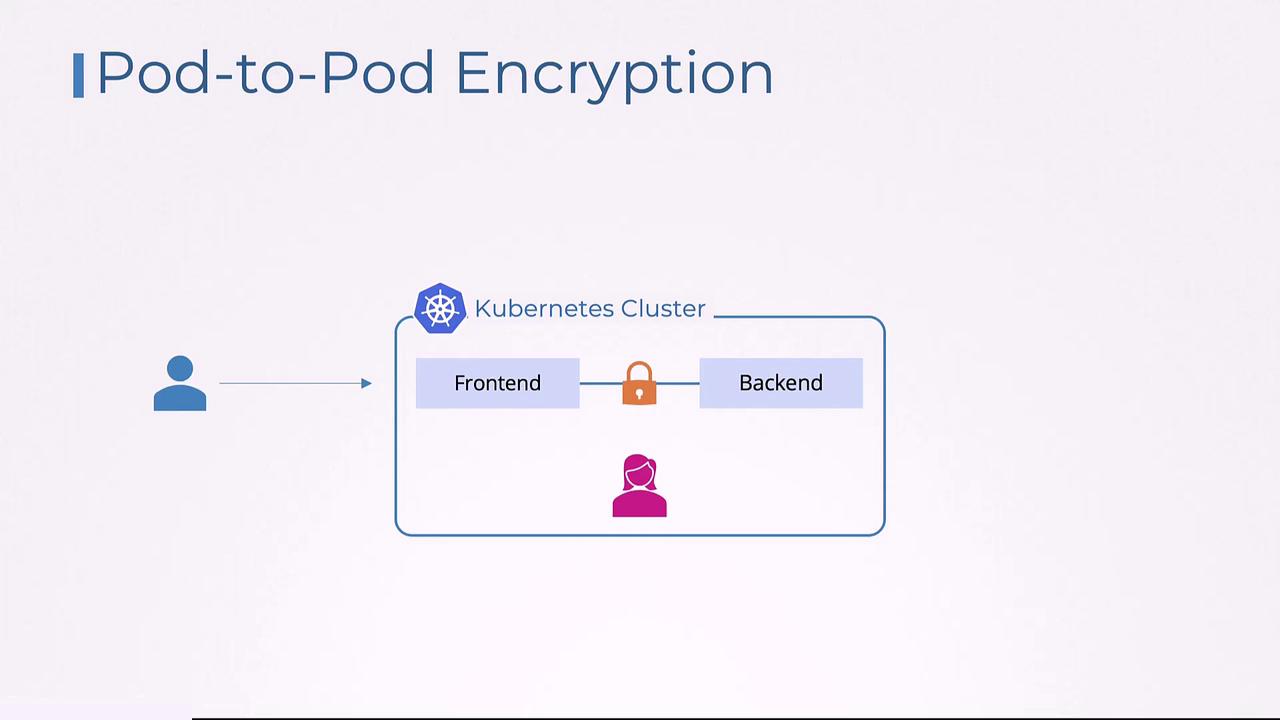
Pod to Pod Encryption
Pod-to-pod encryption is a critical security measure in Kubernetes clusters. It ensures that communication between pods—whether within the same namespace or across different namespaces—is encrypted, maintaining the confidentiality and integrity of transmitted data. This security mechanism is especially vital in multi-tenant environments where sensitive data flows between services.
Imagine an e-commerce application deployed on Kubernetes with two main components: a front-end pod that manages customer orders and a back-end pod that processes payment information. When a customer places an order, the front-end pod sends sensitive payment details, including credit card information, to the back-end pod. Without encryption, an attacker could intercept this communication during a man-in-the-middle attack, leading to a potential data breach.
Key Benefit
Enabling pod-to-pod encryption ensures that even if data is intercepted, it remains unreadable and tamper-proof because it is securely encrypted.
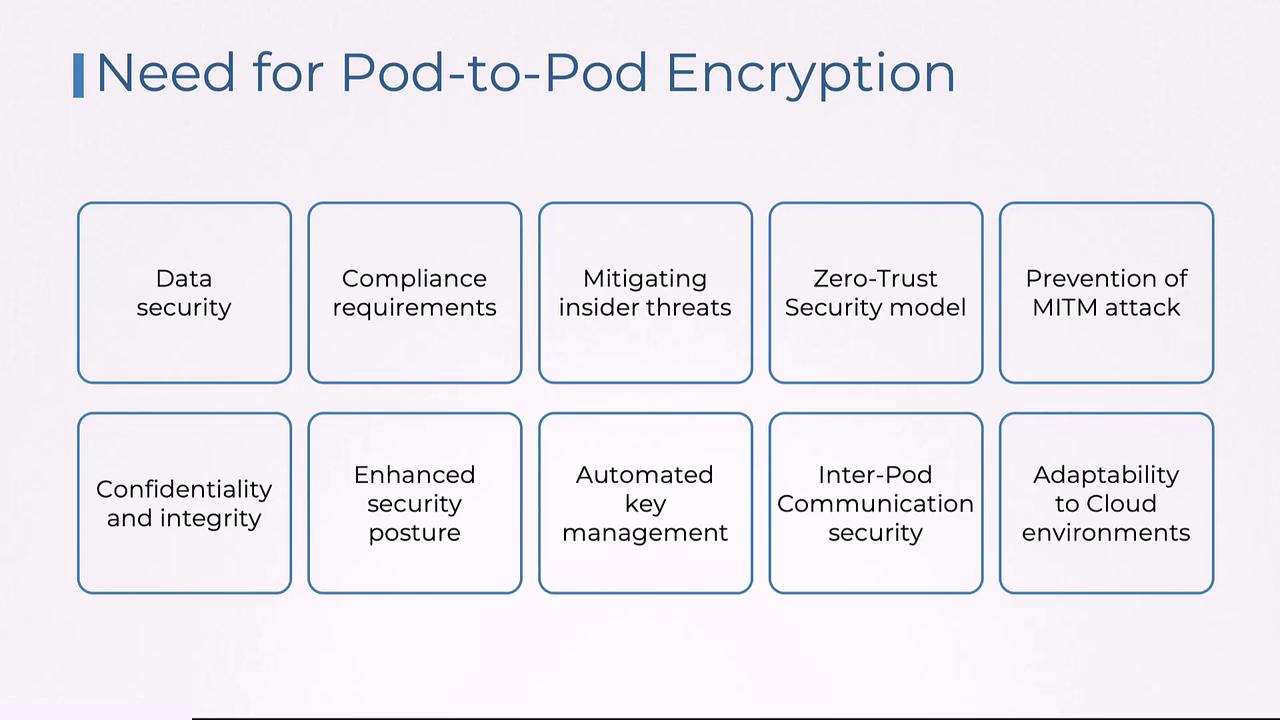
Encrypting data in transit not only protects against eavesdropping and interception but also helps organizations meet compliance standards such as GDPR and HIPAA. This encryption mitigates insider threats by securing internal communications and supports the zero-trust security model—where every connection is considered untrusted until verified. In this way, pod-to-pod encryption reinforces the overall security posture of your Kubernetes cluster without introducing significant operational complexity.
Automated key management provided by Kubernetes-native tools further simplifies the encryption process. This ease of management is crucial in multi-tenant environments where numerous tenants may share the same network infrastructure. In cloud-native scenarios, where traditional network boundaries are blurred, pod-to-pod encryption becomes indispensable for securing communications.
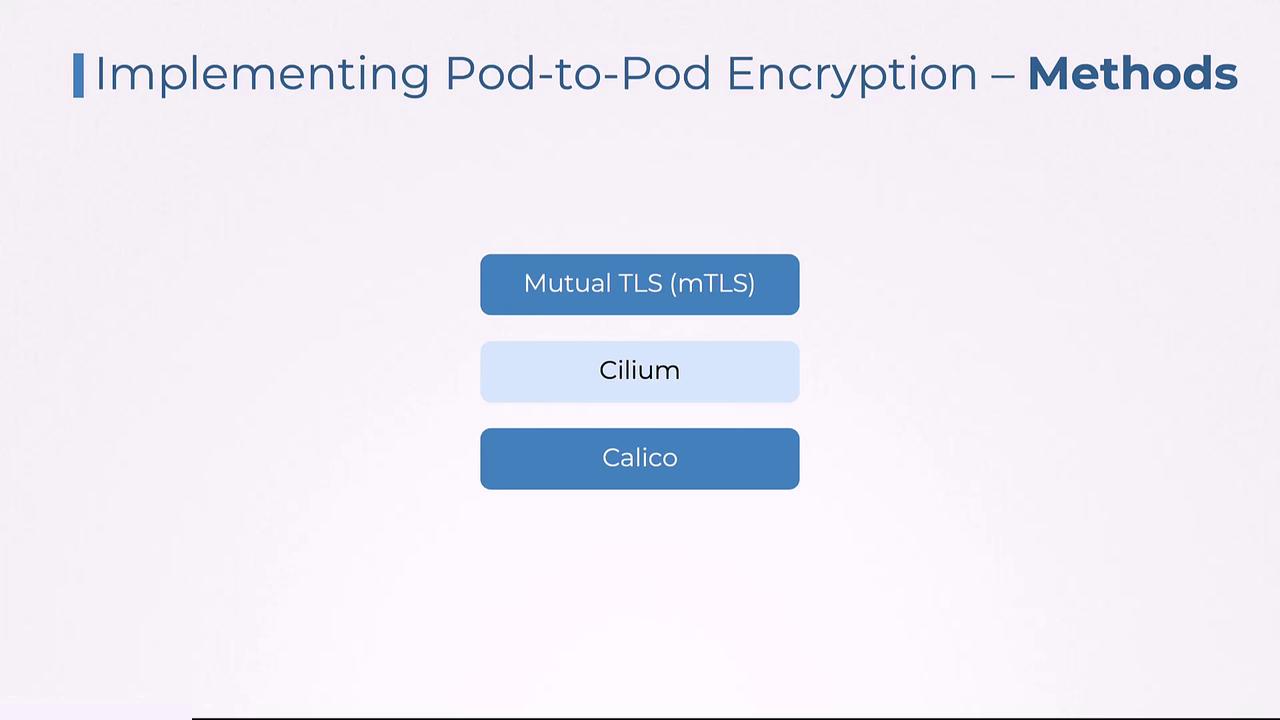
There are several methods to implement pod-to-pod encryption:
- Mutual TLS (mTLS): Commonly implemented via service meshes like Istio or Linkerd.
- Cilium Encryption: Utilizes IPsec or WireGuard protocols.
- Calico Encryption: Leverages IPsec for secure communication.
Each method offers its own advantages depending on the specific requirements of your environment. Detailed discussions, especially regarding Cilium encryption, highlight the flexibility and robustness of these solutions.
Security Best Practice
Implementing pod-to-pod encryption is a key best practice for securing Kubernetes deployments. It not only safeguards sensitive data against external attacks but also reinforces trust in internal communications.
Watch Video
Watch video content