Stages of a Secure Supply Chain
-
Receiving and Inspection
The process begins with the receipt of raw materials and components from various suppliers. Each component undergoes thorough quality inspections to confirm its compliance with defined standards. Once verified, the components advance to the next stage. -
Assembly and Intermediate Quality Checks
During the assembly phase, components are combined to form the final product. Additional quality and security checks are conducted to ensure that every stage of the build adheres to strict standards. -
Rigorous Quality Assurance Testing
In the third phase, comprehensive quality assurance (QA) testing identifies any defects. Detected issues are either corrected immediately or the affected products are reworked.
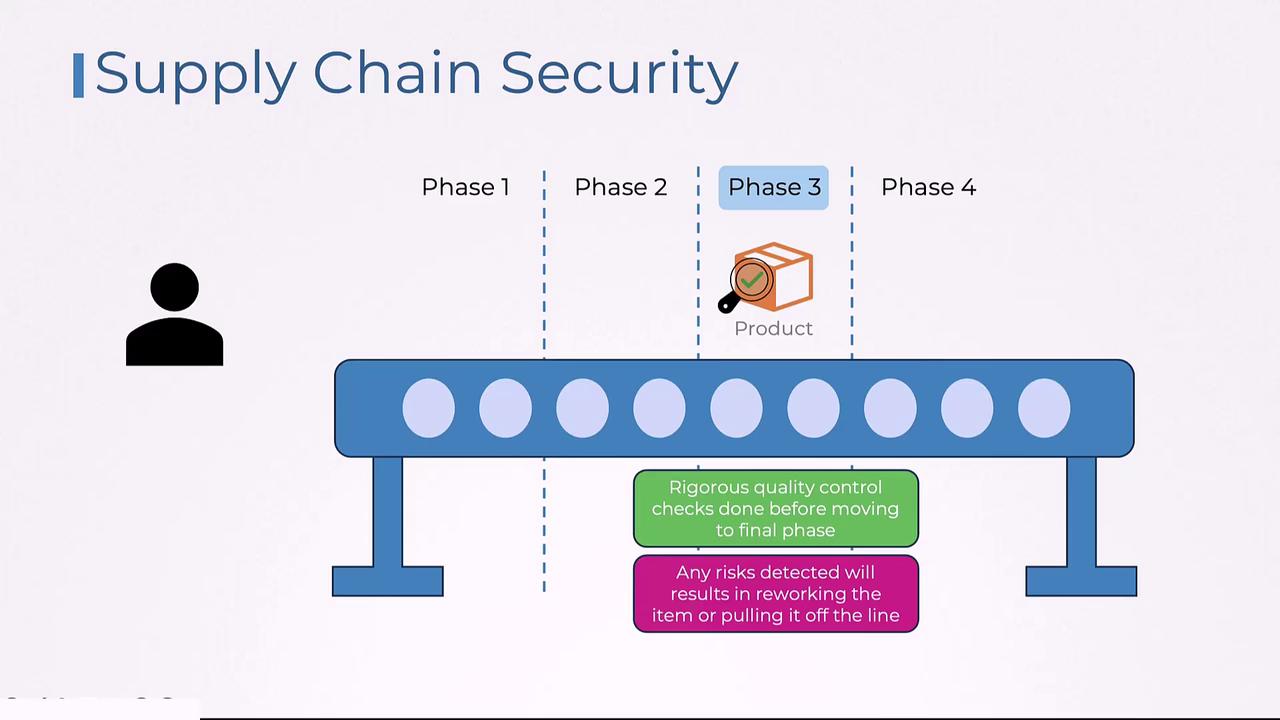
- Packaging and Secure Release
Once the product passes all previous stages, it moves to the final phase: packaging and release. Packaged products are shipped securely, ensuring they reach customers without being tampered with. This process serves as a strong analogy for a secure supply chain in software development.
Just as raw materials are inspected in a factory, developers work in secure environments where source code is written and tested. Securing the supply chain in software involves multiple stages, from development to deployment.
Securing the Software Development Life Cycle
In a secure software development process, the source code is initially crafted and tested by developers in a trusted environment. Following this, the code enters the build phase—where it is compiled and prepared for deployment. It is crucial to ensure the integrity of the build process by isolating environments, keeping dependencies up-to-date, and scanning for vulnerabilities using tools like OWASP Dependency-Check and Snyk. Before deployment, container images are scanned thoroughly to detect any vulnerabilities. Tools such as Clair and Trivy are commonly used for this process. This stage is analogous to the careful logistics required to deliver a finished product safely to the end user.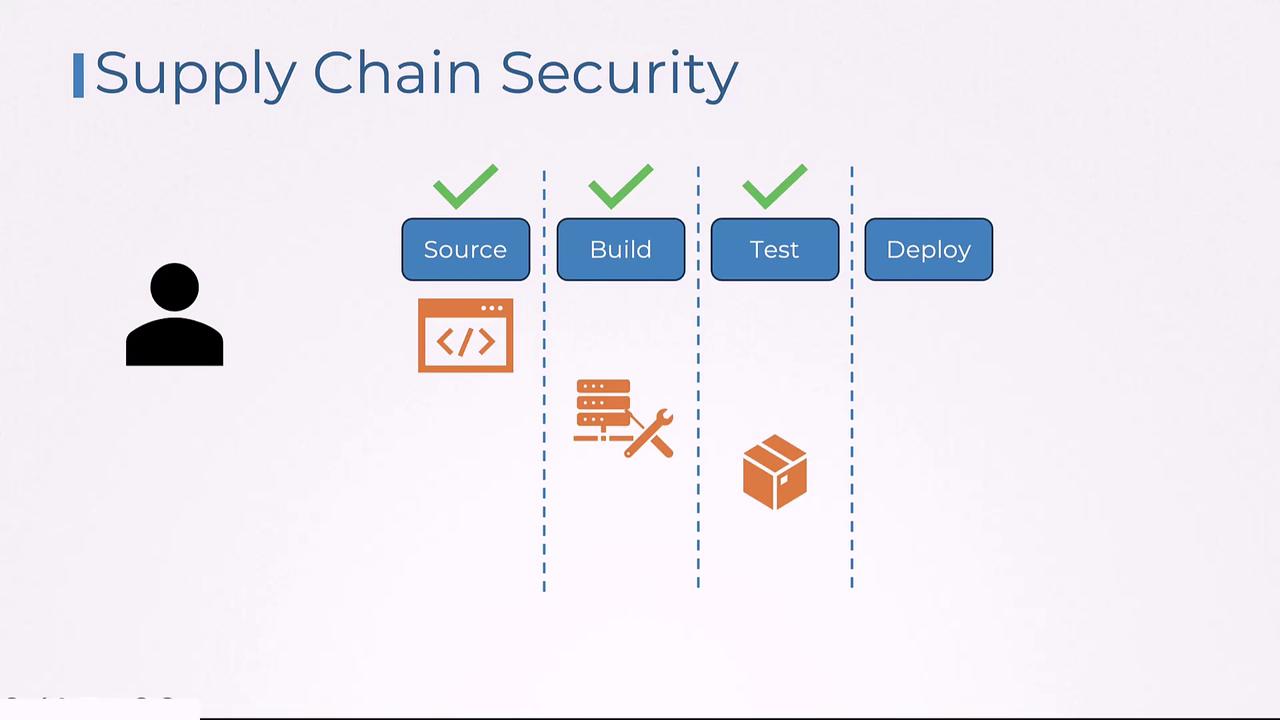
Enhancing Deployment Security
Deployment is the final and critical stage in ensuring software integrity. It involves implementing robust security measures to safeguard production environments from unauthorized access or modifications. Techniques such as Pod Security Policies, network policies, and role-based access controls (RBAC) help secure Kubernetes resources during deployment.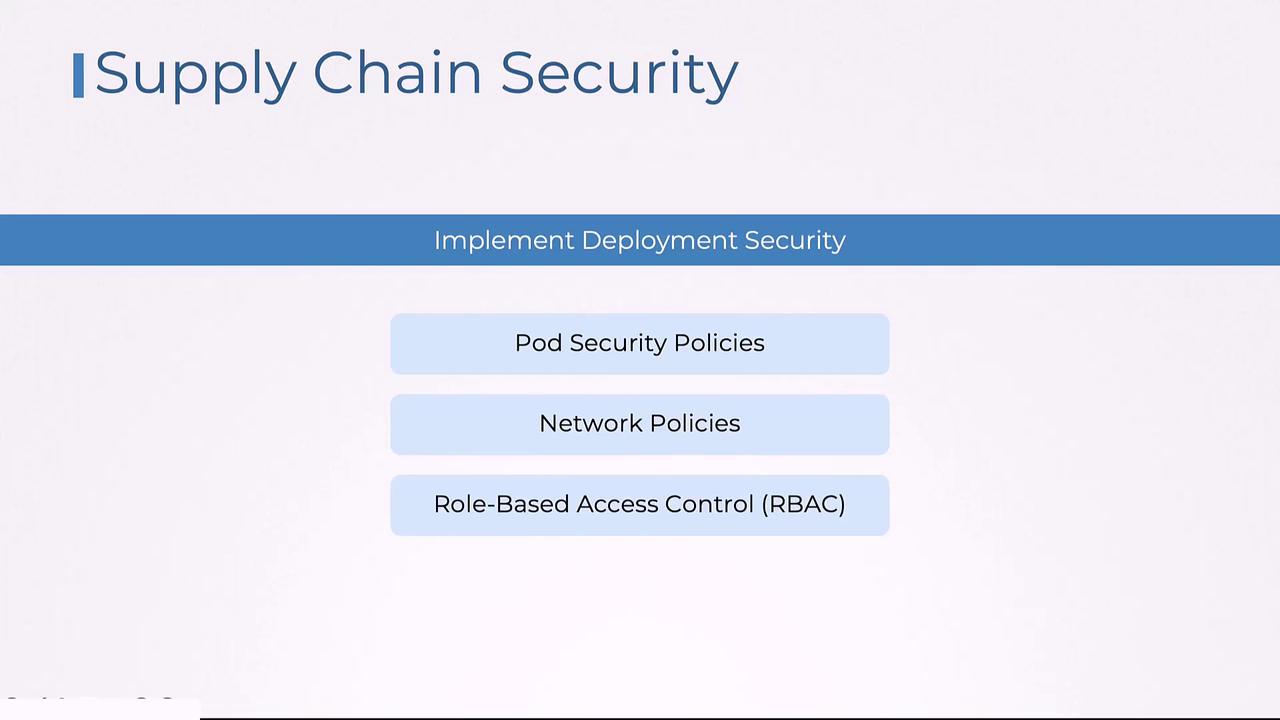
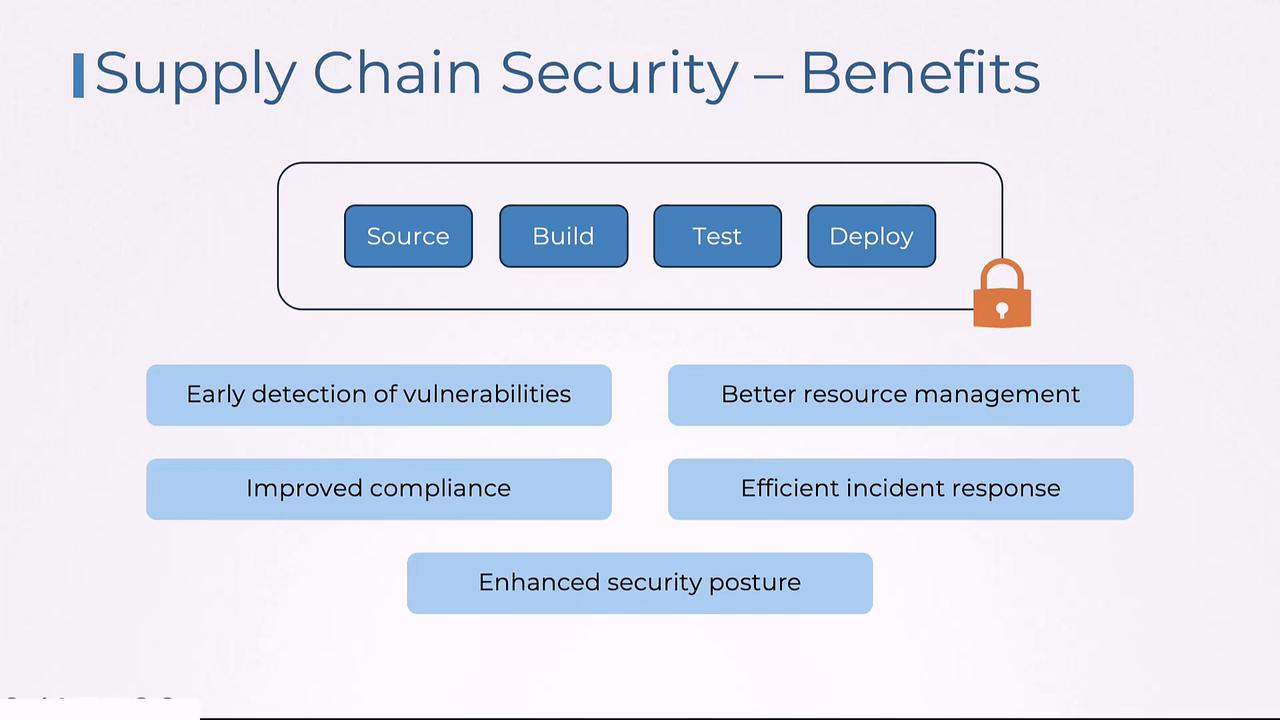
The Benefits of Robust Supply Chain Security
Implementing a secure supply chain process offers numerous advantages:- Early Vulnerability Detection: Issues are identified during early stages, allowing for swift remediation.
- Optimized Resource Management: Continuous inspections prevent security incidents from disrupting production.
- Improved Compliance: Adhering to stringent security standards helps organizations meet industry regulations.
- Efficient Incident Response: Streamlined processes minimize damage in the event of a breach.
- Enhanced Overall Security Posture: A secure supply chain reinforces the integrity of every stage—from development to deployment.
Neglecting any stage of the supply chain security process can expose your systems to risks and potential breaches. Always ensure that security measures are enforced at every phase to protect both your digital and physical products.