Unpatched Vulnerabilities Leading to Major Data Breaches
Neglecting known vulnerabilities in software components can create an opening for attackers. For instance, if a company overlooks a critical vulnerability, it might lead to exploitation that exposes millions of records. Such an incident can trigger extensive financial losses, regulatory fines, and irreversible damage to customer trust.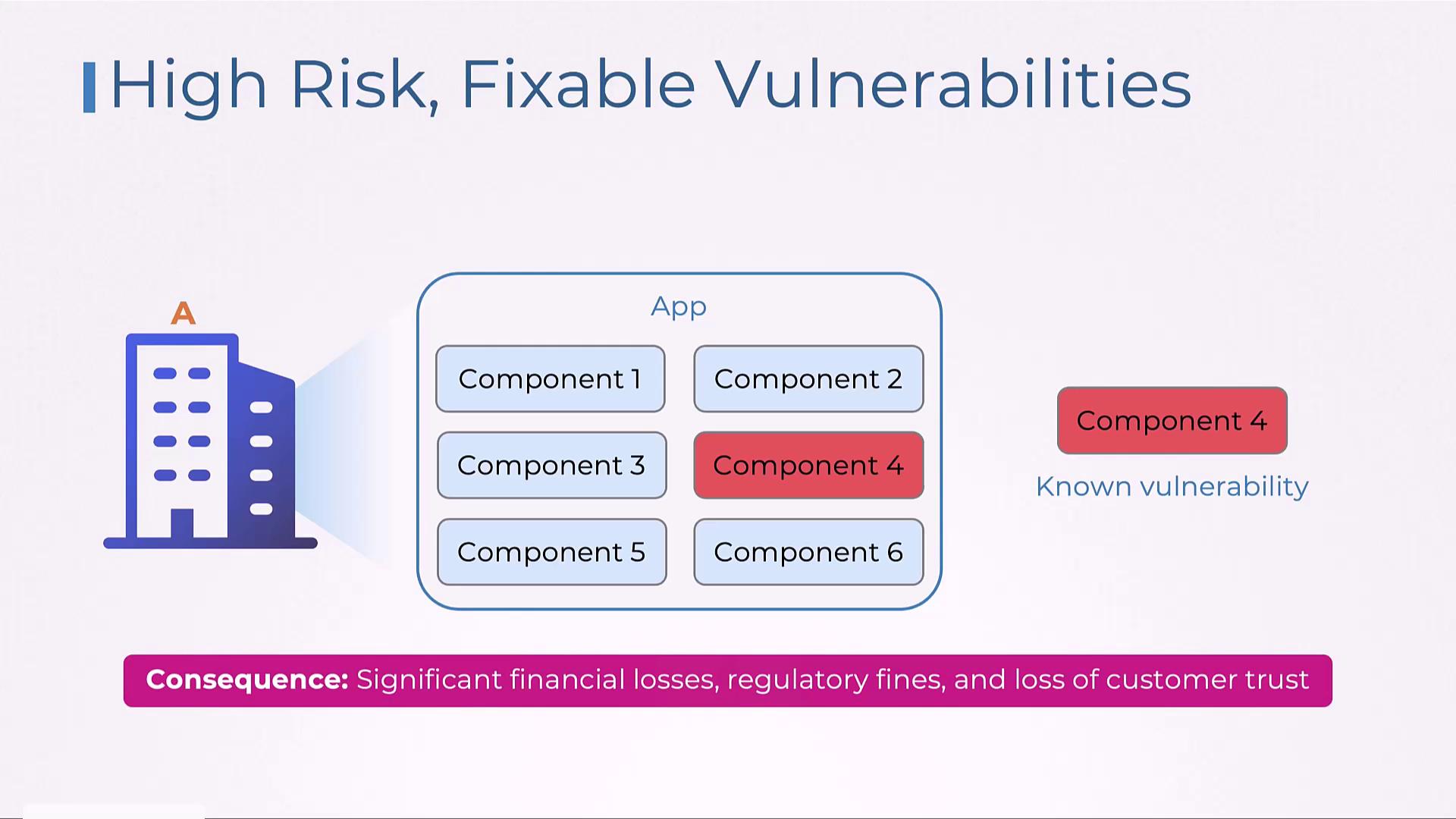
Risks from Untrusted Third-Party Components
Integrating unverified software components from third-party vendors may introduce hidden malware. Attackers could use these components as a backdoor to infiltrate the network, compromising overall security. This vulnerability not only disrupts operations but also results in expensive incident response and remediation efforts.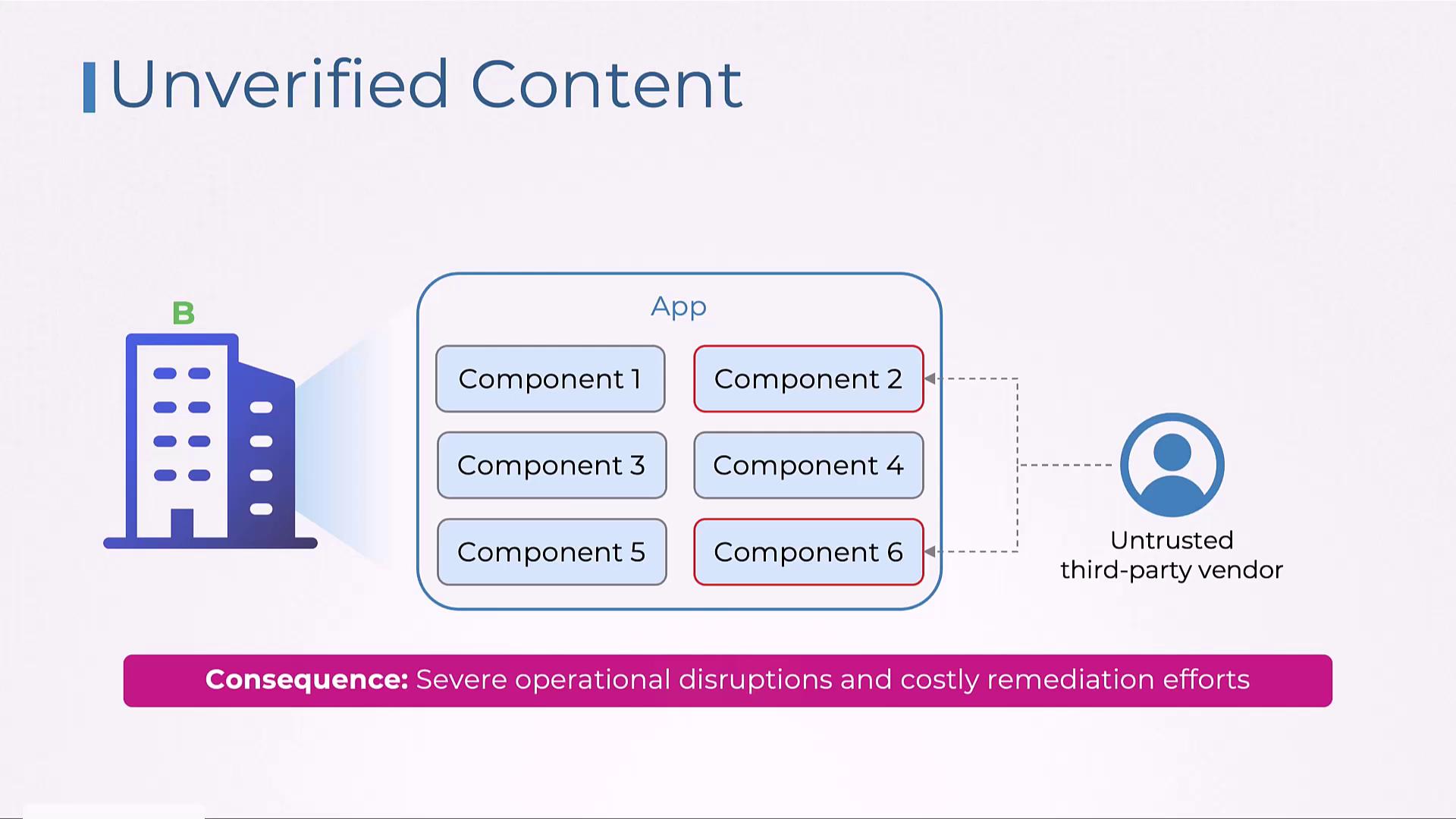
Exposure Through Inadequate Credential Security
Storing sensitive credentials without proper encryption leaves them vulnerable. When unencrypted credentials are compromised, attackers gain easy access to critical customer data, potentially leading to severe data breaches and a loss of customer confidence.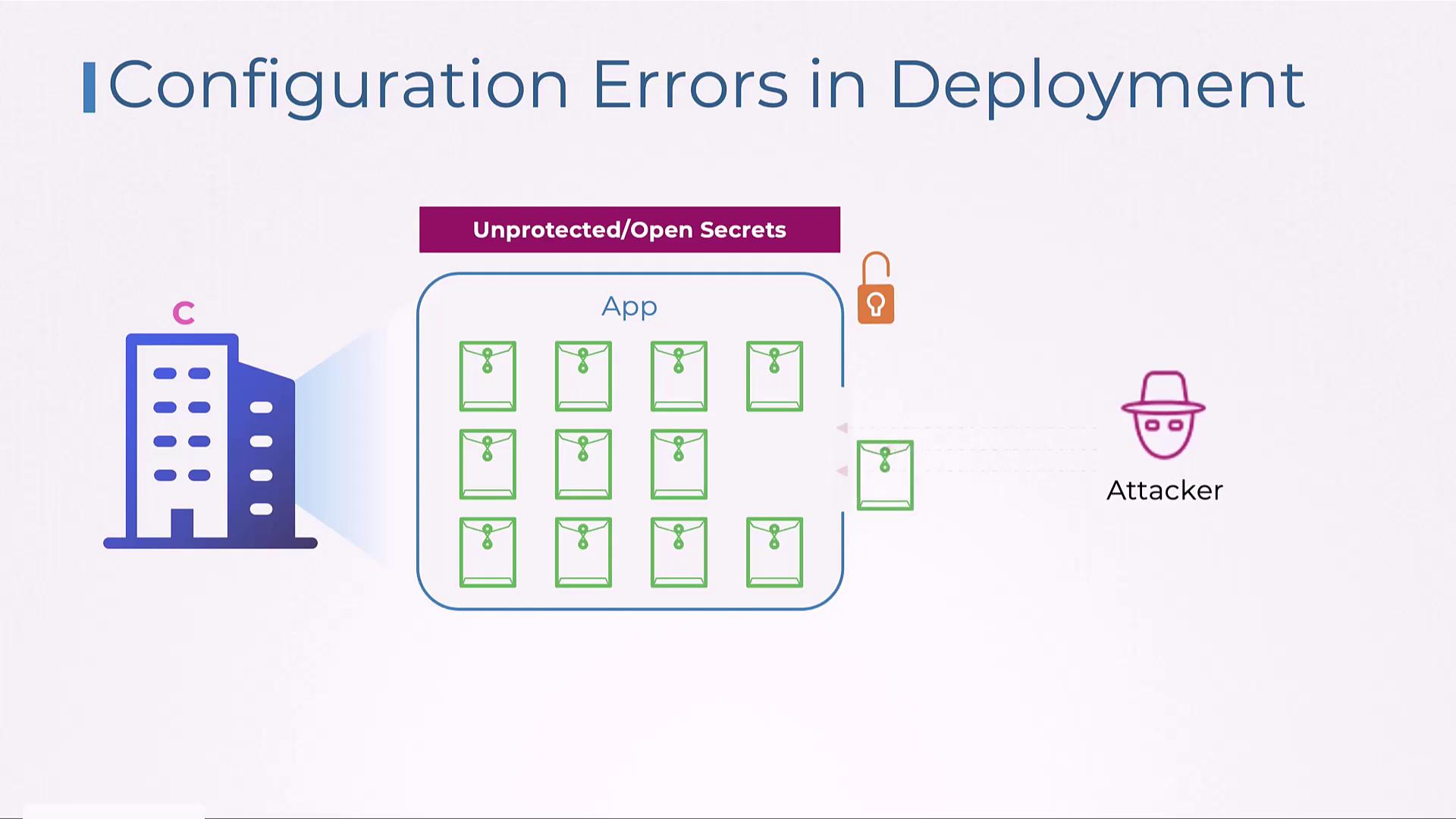
Ensuring that credentials are always encrypted and stored securely is essential to prevent unauthorized access.
Vulnerabilities from Overly Permissive Configuration Settings
Improperly configured access controls can provide attackers with an easy gateway to critical systems. Overly permissive settings, such as lax network policies or missing role-based access controls (RBAC) in Kubernetes clusters, enable attackers to infiltrate vulnerable pods and exploit network weaknesses.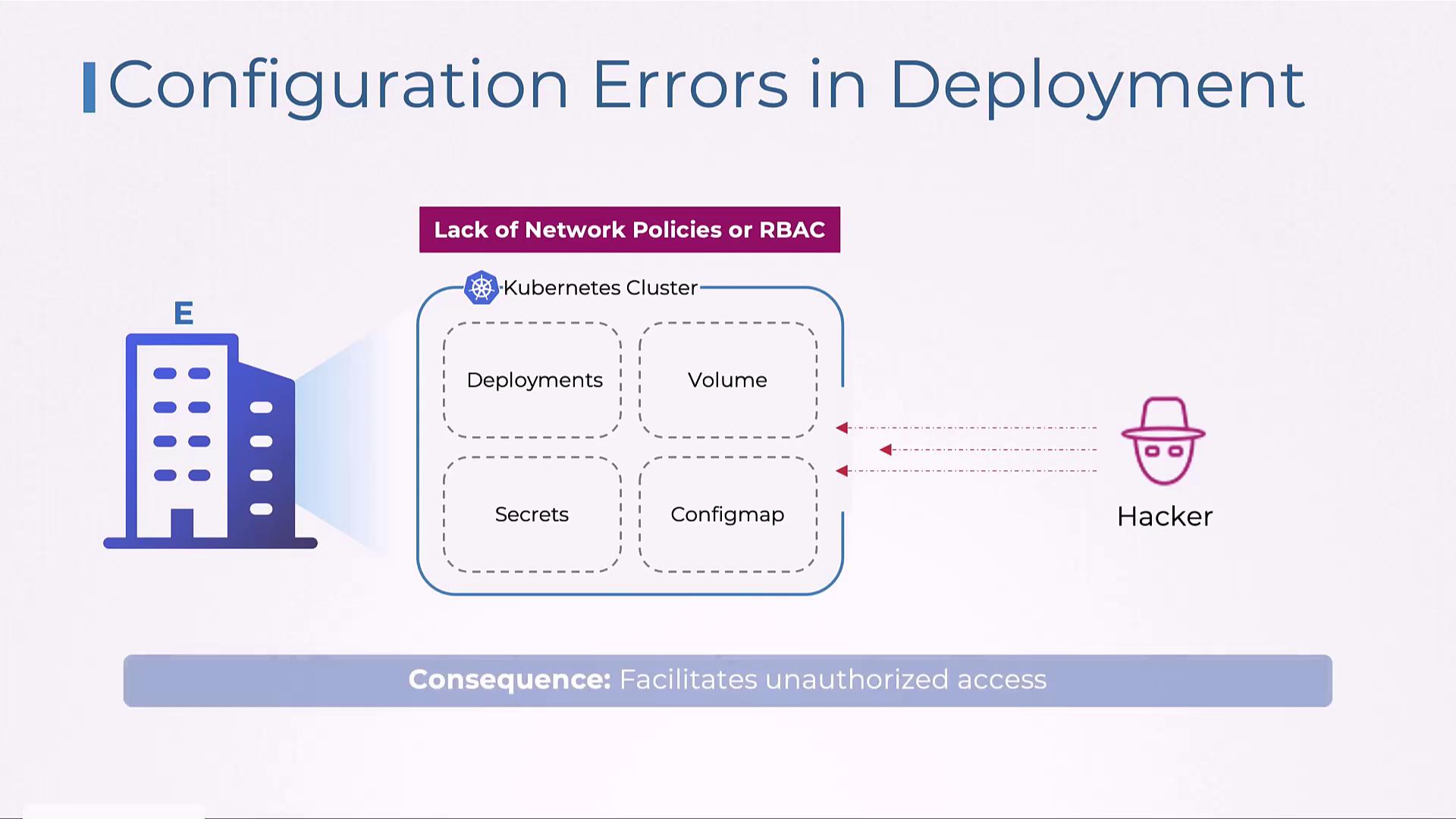
Container Security Misconfigurations and Host Compromise
Improper container security configurations pose a serious risk. If containers are not set up correctly, attackers may break out of the container environment and tamper with the underlying host system. This breach can lead to data theft, manipulation of system operations, and complete host control.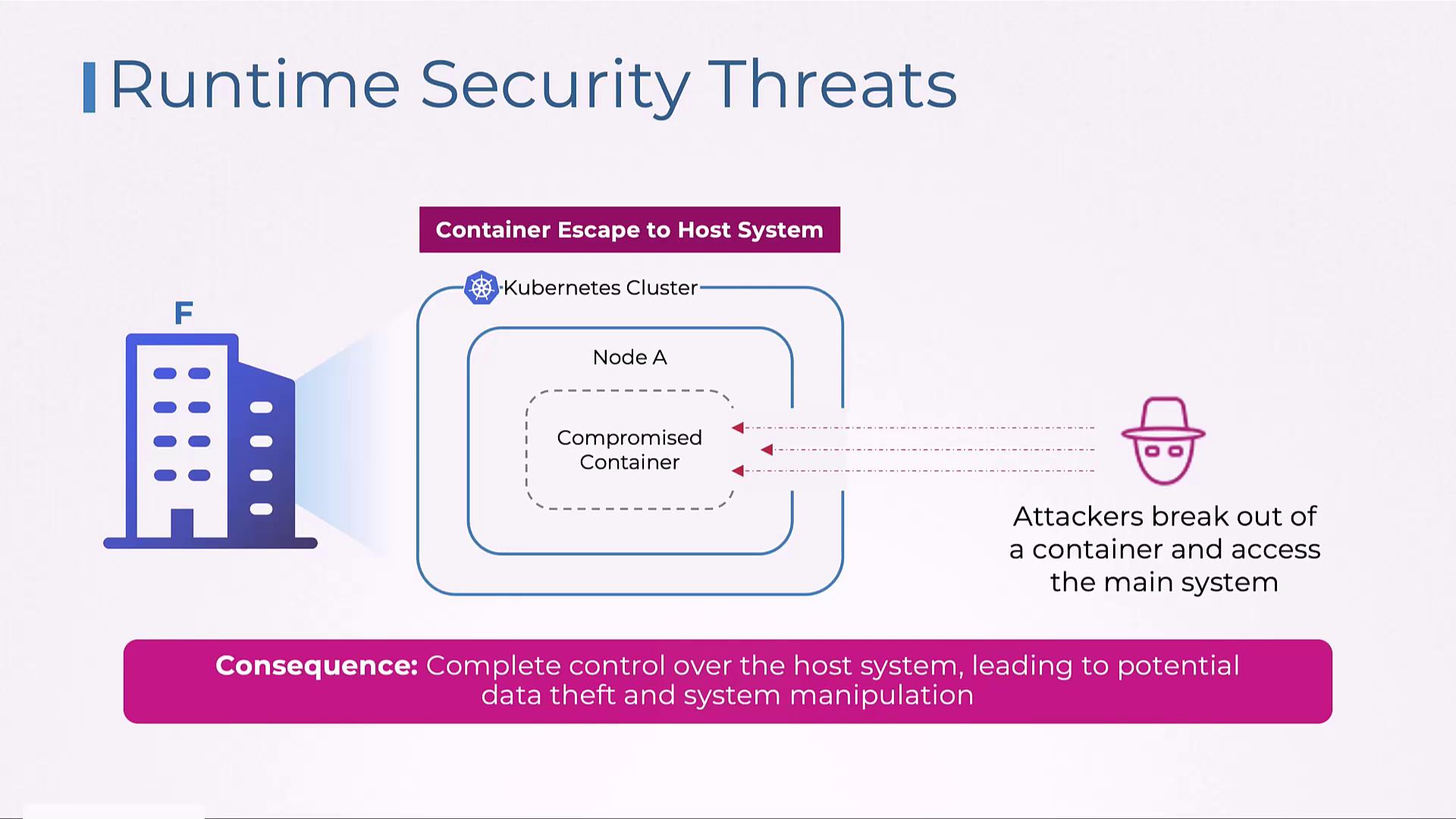
Regular security assessments, proper container isolation, and adherence to best practices in container configuration are crucial to safeguard the host environment.
Summary of Supply Chain Vulnerabilities
The cumulative risks of inadequate supply chain management can pave the way for cyber attacks, operational disruptions, financial losses, regulatory or legal actions, and a competitive disadvantage in the marketplace. It is vital to continuously monitor and update security practices to mitigate these risks effectively.