1. Cloud Security
The first “C” is cloud security, which focuses on protecting the overall infrastructure—be it a public cloud, private cloud, on-premises data center, or co-located environment. In our demo, the infrastructure hosting the Kubernetes cluster was insufficiently secured, permitting unrestricted access to cluster ports. Without proper network firewalls, remote access from the attacker’s system was easily achieved.Ensure that your cloud infrastructure includes robust network firewalls and proper access controls. This is not only essential for preventing unauthorized access but also for mitigating broader risks that can stem from exposed ports.
2. Cluster Security
The second “C” focuses on securing the Kubernetes cluster itself. In the demo, the attacker compromised the system by exploiting a publicly accessible Docker daemon and an unsecured Kubernetes dashboard that lacked proper authentication and authorization measures. To secure your cluster:- Follow best practices to protect the Docker daemon.
- Secure the Kubernetes API by enforcing strong access controls.
- Restrict dashboard access with proper authentication.
- Implement network policies and ingress security for additional safeguard measures.
3. Container Security
The third “C” addresses container security. In the demonstration, the attacker was able to deploy containers without restrictions, including running containers in privileged mode. The absence of constraints on image sources or tags allowed the deployment of potentially harmful containers and unapproved applications. To mitigate these risks:- Enforce policies that allow only images from secure, trusted repositories.
- Disallow privileged mode for containers.
- Use container sandboxing to provide an additional layer of security.
4. Code Security
The final “C” focuses on code security. Although not the main focus of this lesson, securing application code remains critical. Common pitfalls include hard coding credentials, passing sensitive information via environment variables, or transmitting data without TLS encryption. Key recommendations include:- Implement Secrets Management and vault solutions for critical information.
- Enable mTLS encryption to ensure secure communication between pods.
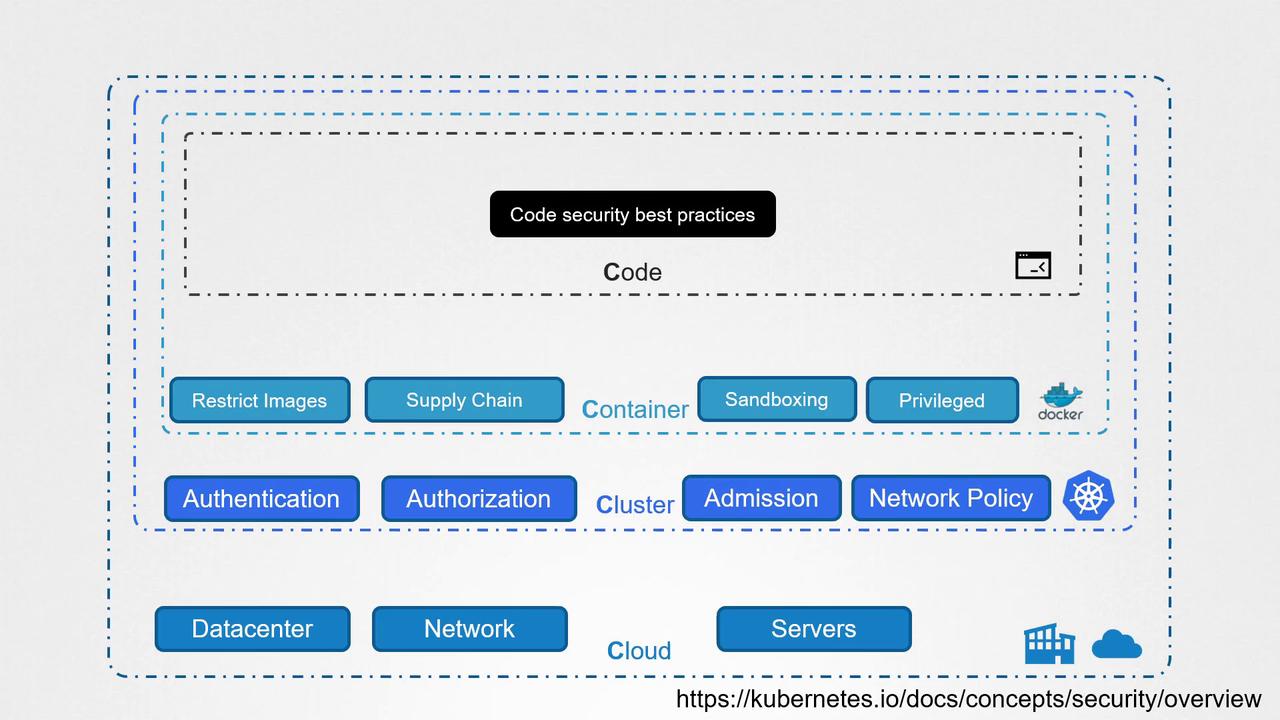
Never overlook the importance of code security. Integrating strong security practices at the code level ensures that vulnerabilities are minimized, complementing other security layers such as container and cluster security.