Question 1: OSINT Sources
Which of the following is not considered an OSINT source?- Government databases
- News websites
- Social media platforms
- Encrypted private communications
Question 2: Identifying OSINT Tools
Which tool is commonly used for OSINT investigations?Although Nmap excels in network discovery by identifying active IP addresses and open ports, it is not primarily an OSINT tool. Similarly, Wireshark is tailored for network packet analysis and Metasploit is intended for penetration testing. The correct answer is Shodan, a tool specifically designed to search for internet-connected devices.
Question 3: Objective of OSINT
What is the primary objective of OSINT?While options might include launching social engineering attacks, hacking private systems, or defending against malware, the real goal of OSINT is to gather information from public sources.
Question 4: OSINT Framework Developer
Which organization is known for developing the OSINT framework?Among the provided options, the Meta Corporation is recognized for its contributions to open source intelligence.
Question 5: Understanding Maltego
What is Maltego?Your options are: a data mining tool used for OSINT, firewall software, a penetration testing tool, or a network scanning tool. Maltego is a data mining tool specifically designed for OSINT, not for network scanning, penetration testing, or firewall purposes.
Question 6: People Search OSINT Tool
Which OSINT tool specializes in searching for people across multiple social networks?The correct answer is SpiderFoot, which is engineered to gather information about individuals from various online sources.
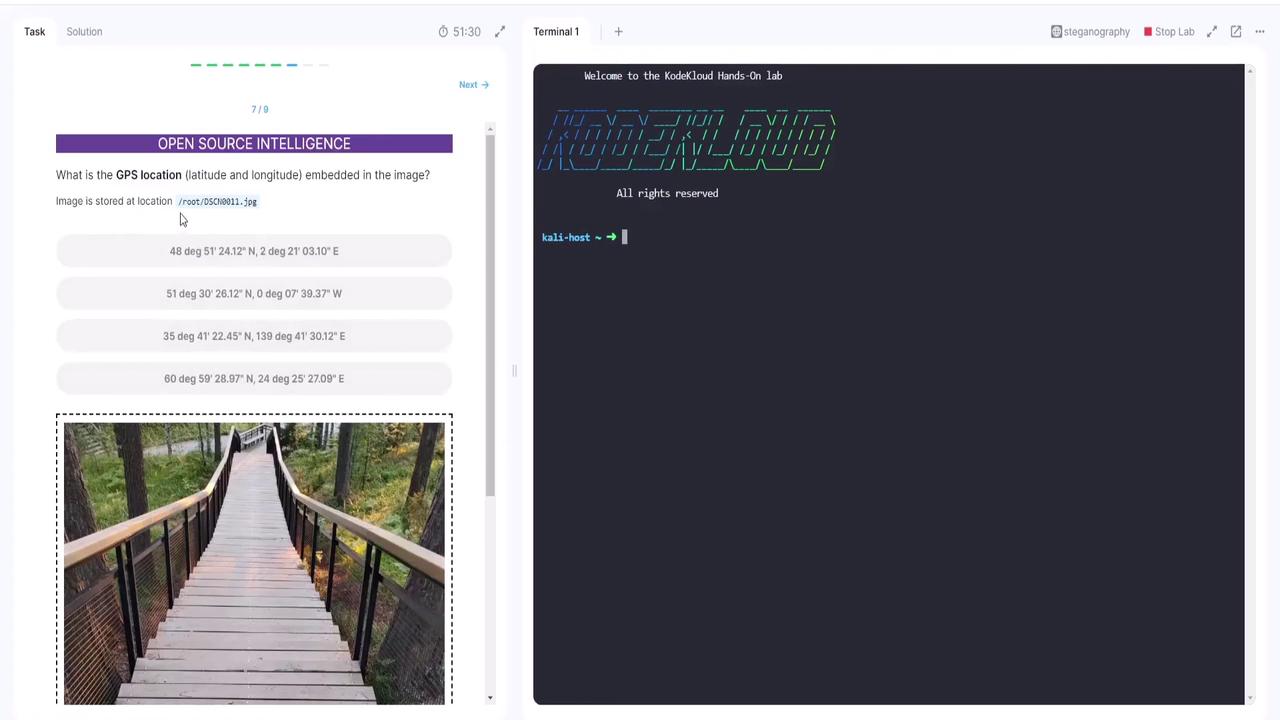
Hands-On Practice with EXIF Data
Now let’s put theory into practice. In this exercise, you will extract the GPS location (latitude and longitude) from an image file. Although the image appears to show a simple wooden walkway in a forest, its metadata holds valuable information.